Introduction
It’s been a little over four years since our first Hardware Router Need to Know and while a lot has changed, a lot has stayed the same. On the change side, prices have come down to the point where there’s no excuse for not having a router if you have a broadband connection. You can even find some products in “blister-pack” form hanging near checkout lanes to encourage impulse buying. And while some vendors like UMax and Nexland have left the business, there have been plenty of new entrants such as Trendnet, Zonet, CNet (is there a trend here?) to take their places.
On the “stay the same” side, router buyers are still plauged by routers that frequently drop connection, reboot mysteriously, overheat and generally make owners regret their purchase. Official vendor support is still a hit-or-miss proposition, with many users taking their problems to fellow users in online forums, rather than endure hour-long waits to end up speaking with someone who is barely understandable.
In spite of these hassles, there is still no better way to share a broadband (or even dialup) Internet connection than by using a hardware router. Today’s consumer-grade routers continue to provide a lot of bang for the buck, and both enable more than one computer to use a single Internet connection, while protecting those computers from some of the dangers of a full-time direct Internet connection.
This article will help you understand the features of these beasties, untangle some of the confusing terminology that some manufacturers use, and figure out what the “must-have” features are for your situation.
Let’s get started!
Tip: If you already know the ins and outs of hardware routers, then hop over to our Hardware Router Chart to see how products compare with multiple benchmark tests.
Choosing a Router
Many people choose a router from a friend or colleague’s recommendation or simply buy what’s touted as the most popular product by the shopping website that they like to use. If your needs are simple, you’ll probably do just fine with this method. But if you use the Internet in more advanced ways, you’ll need to do some homework in order to end up with a product that you’ll be happy with.
Many of the problems with routers are due to conflicts between the technology that routers use to work their magic and the web-based applications that people use. Some applications have no problems running through a router. Others have problems that can be solved by changing the settings on the router. But some applications just won’t work at all, or will have their features so crippled by the router that they are essentially unusable.
Tip: The “magic” that most hardware routers use is called Network Address Translation or NAT. See this Wikipedia article for an understandable explanation of NAT.
The basic rule of thumb is that if you (or your software) starts an interaction with the Internet, your router will be happy and things will work just fine. But ff someone on the Internet tries to connect with a computer on your LAN that is behind your router’s firewall, they won’t get through unless the router is configured (and is configurable!) to let them through. This behavior is due to the basic firewall function that all NAT routers provide.
NOTE: “Firewall” is one of the most frequently used, but least understood networking terms. I’ll attempt to clarify it shortly.
Which Router for Me?
Let’s look at some profiles of different types of Internet use and the features that a router needs to be able to handle them.
Web Browsing, Email, File Downloading, Instant Messaging:
These activities are pretty much the simplest thing that a user can do on the Internet. Since all these activities require that the user initiate a request to a server on the Internet to load a web page, check email, etc., the router’s firewall will not cause problems. Assuming you can get the router connected successfully, you probably won’t encounter problems with it thereafter.
Recommendations: Most any router will work. Make your decision on price, warranty, and quality of the manufacturer’s support.
Remote office worker / Telecommuter:
These users will usually need to have a secure Virtual Private Network (VPN) based connection back to their company network. Most routers support some sort of VPN client pass-through connection, but that may not be enough, depending on the needs of the VPN server that you’re trying to connect to.
If you fall into this category, you’ll probably also use some sort of Internet conferencing (WebEx, GoToMeeting, etc.) and/or telephony (Skype, Gizmo, Vonage, etc.) application. Fortunately, these applications have become a lot smarter about working around NAT firewalls and you generally shouldn’t have problems using them.
Recommendations: The world has changed a lot in four years for telecommuters. Corporations are generally much more fussy about what they let connect to their networks. The good news is that if you work for a large company, your IT department will probably be able to set you up and help you debug any problems that you might have with the company VPN.
So first check with your company’s IT department to see if they recommend a particular product. If your company doesn’t have any specific router recommendations, then ask around to see what other people are using.
If you are self-employed or work for a smaller company, you’ll probably be on your own to figure out a VPN solution. Fortunately, there are a number of products available with VPN endpoints built-in that can take some of the pain out of making a secure remote connection.
Gaming and P2P
Gamers are one of the two user types that have the most difficult time with routers. The problems stem from the conflict between the way games connect to and use the Internet and the way that NAT-based routers work. Add in the fact that there are few generally accepted standards (although Microsoft might argue with this) for how Internet based games communicate, and you may have a difficult time with online game play. And if you want to host a game server, there will be some additional hoops for you to jump through.
One thing you don’t need to worrry about in gaming router selection is ping time. Any router you buy today is going to have a ping time lower than the 1 mS that ping can measure. Ping performance is always dominated by network traffic, both on your LAN and on the Internet. Quality of Service (QoS) technologies like Ubicom’s Streamengine, which is used in D-Link’s DGL-4100/4300 “Gaming” routers, can only prioritize traffic on your LAN.
So if you like to game and have a Bittorrent download going, QoS can help, as long as you don’t try to use more bandwidth than your ISP provides. But once the packets hit the WAN side of your router, there is nothing you can do to affect the time it take for them to reach their destination.
Recommendation: The key to online gaming success is a router’s flexibility in letting you open holes (ports) in its firewall. Get a product that supports as many mapped or forwarded port ranges as possible. Also look for models that support triggered mappings (this is also sometimes referred to as “Special Applications”). I also recommend you do a Google web and Google Groups search, or ask around in your favorite newsgroup or game website forum to see what works for other people.
You’ll also want to choose a router that can support the large number of simultaneous connections (sessions) that are used when a game tries to find the available game servers. Unfortunately, manufacturers generally don’t provide this information, so once again, you’ll need to Google and ask around in gaming forums. You can also check Which Router Reigns Supreme for P2P? to see how many simultaneous connections some popular routers can handle.
Finally, make sure that your router can put one computer completely outside its firewall (called “DMZ” or “Exposed computer”). Strange as this may seem, there are some products that won’t allow this, because of the security risk. But it is a helpful troubleshooting tool to see if closed ports are what is causing your online gaming problems.
NOTE: Putting your gaming machine is not where I recommend you start in order to get your game working, because this exposes the computer directly to all of the extremely nasty attacks that constantly occur on the Internet. It used to take minutes for an unprotected computer directly connected to the Internet to be compromised. But this article describes an unprotected computer being hit by the Sasser worm in eight seconds! So use this feature only as a troubleshooting tool and be sure to have up-to-date antivirus software running on any machine you put in DMZ!
File Swapping / Peer to Peer (P2P)
These folks join gamers as the most likely to not succeed in getting their favorite application to work with a router, or at least have problems in getting it work work reliably. The first reason is that P2P applications can use a large number of simultaneous connections, just as gaming apps do.
But instead of just using them for a short time while locating game servers, P2P apps use a large number of upload and download connections for long periods of time. This heavy usage can cause some routers to overheat or trigger obscure bugs in firmware, leading to flaky problems that are hard to pin down and fix.
Another problem with P2P is that it tends to be a bandwidth hog, which ISPs generally frown on. So if you are a constant P2P user and don’t make any effort to limit the bandwidth you use, you can be pretty certain that your ISP will crank down your bandwidth for you.
ISPs usually don’t even bother to tell you that they’re doing this, or the methods of bandwidth control they are using. So you may think that something is wrong with your router when your torrents seem to slow to a crawl occasionally or even stop altogether. But in reality, it’s just your ISP trying to keep you in line with their bandwidth usage policies.
Recommendation: The recommendations made for Gamers also hold for this category. But P2P users are also advised to use the bandwidth usage controls in their P2P application to stay within their ISP’s bandwidth usage guidelines. You can also check Which Router Reigns Supreme for P2P? to see how many simultaneous connections some popular routers can handle. Check our Hardware Router Chart, too, so that you can choose one of the speedier products.
That’s it for the overview. Now lets move on to understanding router terminology and features.
What is a Firewall, anyway?
As I said earlier, the term “firewall” is thrown around a lot in router marketing literature and is intended to give you a warm, comfy feeling that if you just use one, then you’ll be protected from whatever evils exist on the big, bad Internet. But, of course, real life is a bit more complicated.
All consumer grade routers use Network Address Translation. This is the technology that lets you have multiple computers on your LAN (which each have their own IP address) communicate with the Internet through the single IP address that your Internet Service Provider / Broadband Service Provider (ISP / BSP) assigns to you.
NAT also enforces a simple security policy that lets any device on its LAN (Local Area Network) side freely communicate with devices on its WAN (Wide Area Network) / Internet side, as long as the LAN-connected device initiates the communication request. The NAT security policy also blocks any devices on the Internet from communicating with any devices on the LAN, if the LAN device did not request the communication. These two policies together make up the router firewall function.
So why isn’t this firewall all that you need to keep you safe from the Internet’s harms? Let’s look at the simplest way around the firewall: email. Since retreiving email meets the firewall criteria of a request initiated by a LAN device, i.e, you press the “Get Mail” icon on your email program, anything harmful either embedded in the email itself, or in an attachment comes right on through. Once the harmful code is safely past the firewall, unless you have taken any other precautions, it is free to do whatever it was designed to do. The prevalence of email-borne nasties is one of the reasons why most anti-virus programs now have built-in email scanners that check mail as it is being received and sent.
But email isn’t the only way that harmful programs can get past a firewall. Websites are now full of all sorts of executable code,such as Active X controls, Java applets, javascript, flash animation, etc. that are downloaded as part of fetching a requested web page. Once again, your router’s firewall isn’t going to stop any of it, since, after all, you did click on a link or enter a URL to download that page, didn’t you?
So it should be clear by now that your router’s NAT firewall isn’t going to be enough to keep all of the Internet’s bad stuff off of your LAN. So how about the Stateful Packet Inspection (SPI) that your router’s firewall is supposed to have. That sounds like it can be a big help, right?
Unfortunately, the SPI that’s included in consumer routers doesn’t really make you more secure, and in fact, can mess up some applications that you purposely open ports for. The SPI you would want is something that would check each incoming packet for all of the bad stuff I mentioned above.
But all most consumer SPI does is protect against malformed packet exploits and things that you’d only need to be concerned about if you were running certain types of servers and had ports opened to them. And the denial of service (DoS) attack protection that is always mentioned as an SPI feature? Not much help either, since if your LAN were the target of a DoS attack, your Internet connection would be so flooded by traffic that it wouldn’t matter if your router were running or not.
Fortunately, SPI is now included for no extra charge in most consumer routers, so you don’t even need to worry about it.
WAN Port Features
With the firewall discussion out of the way, we can turn our attention to more practical matters… like how you get your router connected to the Internet!
NOTE: We use “broadband modem” to refer to the device that is used to connect your computer to whatever method of broadband delivery you subscribe to. This can be cable modem, DSL (whatever flavor), satellite, fixed wireless, etc.
Connection Type
Most routers now have a 10/100 Ethernet WAN port to accomodate the higher connection speeds provided by ADSL2, ADSL2+ and fiber-based connections. There are still routers with only a 10 Mbps WAN port, which should be fine for any Internet connection with 10 Mbps or lower download throughput. But if you have higher-speed Internet service, be sure that your router has a 10/100 Mbps WAN port.
For the most part, it’s difficult to find serial WAN ports that can be used for dialup or ISDN connection, simply because those methods are so seldom used for a shared Internet connection. The most notable exception is the WiFlyer from Always On Wireless, which is a compact, portable router with a built-in telephone modem. It can also be used with a broadband modem via its Ethernet WAN port and supports both 802.11b wireless and Ethernet LAN connections.
Obtaining your IP address information
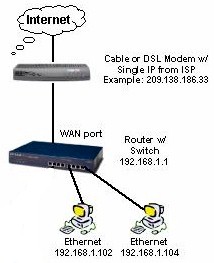
Once you have a router with the correct physical connection, you’ll need to make sure that it can handle the various methods of obtaining IP address information and connection authentication that ISPs use. Let’s first run down the two methods for setting up your router’s IP address information that all routers provide, then review authentication methods.
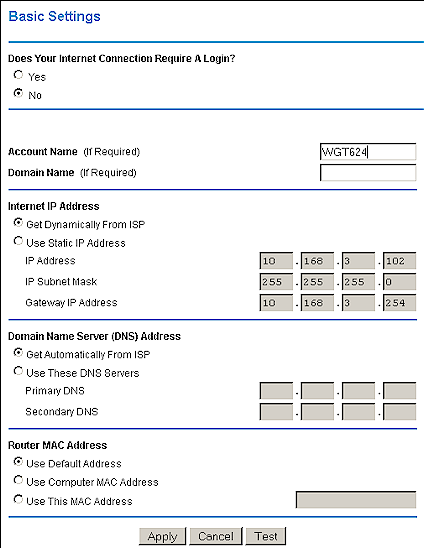
Figure 1: WAN Connections
Dynamic IP
In this method, which is sometimes referred to as “DHCP client”, your router is set to obtain its IP, Gateway, and DNS server addresses automatically. It’s a common method because is gives your ISP a lot of flexibility in configuring their network. Figure 1 shows a router configured for dynamic IP.
The downside is that since your IP address can change, any application that is looking for a server or application at a specific IP address will not find you when your IP address changes. Fortunately there are Dynamic DNS providers, such as TZO, who can make sure that folks can reach you no matter what your IP address is.
Static IP
This is the method of choice for folks who want to run servers and don’t want to bother with using Dynamic DNS providers. It requires that you manually enter the IP, Gateway, and DNS address information that your ISP gives you. This choice is not always available, and if it is, you may have to pay extra for it. In Figure 1, all you’d need to do is click the Use Static IP Address radio button and enter the information.
Discard WAN ping / “Stealth” mode
One of the basic things that any port scanning program does is to ping your IP address and see if any answer comes back. This feature makes sure that your router doesn’t make a peep if it’s hit with a ping, so that the port scanner thinks that nobody’s home at your IP address and doesn’t mark you for further investigation. Definitely a good feature to have, and most routers now have it, and enable it by default!
ISP Authentication – PPPoE
Your ISP uses a number of methods to make sure that only valid users connect to their systems. We’ll next review the common ones.
Point-to-Point Protocol over Ethernet, or PPPoE has become very widely used, driven into the market by DSL BSP’s. It requires a user name and password, but uses a protocol that allows the authentication, monitoring, and control of multiple virtual connections. This means that it if your BSP uses this protocol, they could eventually keep track of and charge separately for multiple users. But since they could do this only if you purchased multiple IP addresses from them, this charge-per-user option hasn’t been widely implemented, since most users install a router when they want to share the connection.
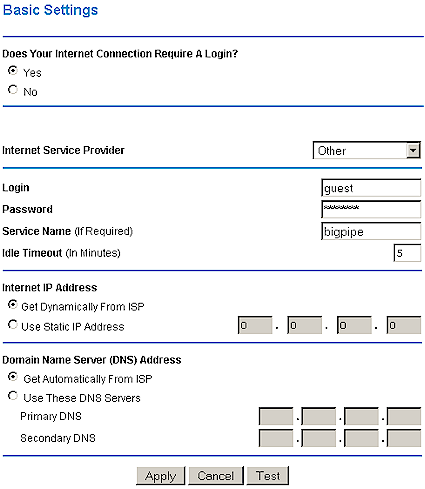
Figure 2: PPPoE Connection Options
PPPoE is now standard on all routers, but the quality of implementation, i.e. how well it works, varies greatly. Some of the PPPoE related problems are due to buggy router firmware, and some are due to the wide variety of PPPoE implementations used by BSPs. If your BSP uses PPPoE, look for routers that support it, and also that have these other features (refer to Figure 2):
Connection Controls
These include a number of different features, intended to give you control over how long a connection is maintained when there is no network activity and what is done if you are disconnected. Most routers default to automatically connecting when Internet related network activity is detected, but the Linksys routers put this under the control of a “Connect on Demand” setting. “Maximum Idle Time” settings control the time that the router waits to drop the connection when there is no Internet related network activity. An “Auto-Reconnect” feature automatically tries to restore the connection when it’s dropped.
Keep Alive
One of the very common problems with PPPoE connections is that the connection is frequently dropped. Some BSPs do this intentionally, much as a dialup ISP will drop your connection after a certain period of inactivity, but others just don’t have their PPPoE servers set up properly. A “Keep Alive” feature will try to keep the connection up by forcing a short burst of Internet activity after a programmable period of time.
Other PPPoE needs
Depending on your BSP, your Router’s PPPoE client may have to provide a Static IP address, and/or Service Name. Make sure your router has these controls if you need them. If you need PPPoE with Static IP, don’t assume that your router supports this, since many don’t.
Also, check to see if your router supports adjustment of its MTU (Maximum Transmission Unit) value. A PPPoE connection has a lower MTU than a normal Ethernet connection, and can cause problems with some ISPs and/or applications. PPPoE and VPN are a particularly troublesome combination, but there are other cases in which the ability to tweak your router’s MTU will come in handy. Note that you may have to hunt through many router admin screens to find the MTU adjustment, since manufacturers are not consistent in where they place it.
ISP Authentication – Other Methods
MAC Address
Anything that has an IP address will have a MAC (Media Access Control) address. MAC addresses are unique to each piece of networking equipment (at least they’re supposed to be… more below) and are used in the IP address assignment process. The MAC address (also known as an “Adapter” or “Ethernet” address) is composed of twelve hexadecimal characters. To avoid address duplication, ranges of addresses are assigned to network equipment manufacturers, who are charged with setting up the proper systems to ensure that address assignments are not duplicated.
NOTE: MAC addresses are represented in three common ways. Here’s how you would write the same MAC address in those three ways:
- 00fe3c812eab
- 00-fe-3c-81-2e-ab
- 00:fe:3c:81:2e:ab.
MAC addresses are not case sensitive, so the letters that are used (A-F) can be either upper or lower case.
MAC address authentication used to be very commonly used. But routers evolved to allow setting the WAN MAC address to whatever you wanted either by automatically “cloning” the MAC address of a computer that’s attached to it, or letting you manually enter the MAC address. This greatly reduced the effectiveness of this authentication method.
Host Name
The Host Name method was used primarily by the now defunct BSP @Home. It requires that the Host Name (Windows calls this the “Computer Name”) of the connected computer be set to a specific, long name. Many routers continue to include the ability to set the Host Name, even though @Home has long since gone.
PPTP
Known more as Microsoft’s VPN protocol, PPTP authentication is used by some ISPs instead of PPPoE. The setup screens and parameters look very similar to PPPoE.
Telstra Bigpond
Another username / password authentication system used by the large Australian BSP.
DHCP Server
All routers include this capability, which can automatically provide your LAN clients with the TCP/IP information they need to successfully establish an Internet connection. The TCP/IP information will also allow File and Print Sharing to work, but you’ll usually need to take some extra steps to get those services working. Not all router DHCP servers have the same feature set, so here’s what to look for:
Address Range control
This lets you control the range of addresses that the server hands out. Some routers allow you to only set the starting address of the range. Others allow you to directly set the starting and ending addresses of the range. This feature is handy for making sure that the DHCP server issued addresses don’t collide with any fixed IP addresses that you may need to assign to LAN clients. Refer to the lower portion of Figure 3.
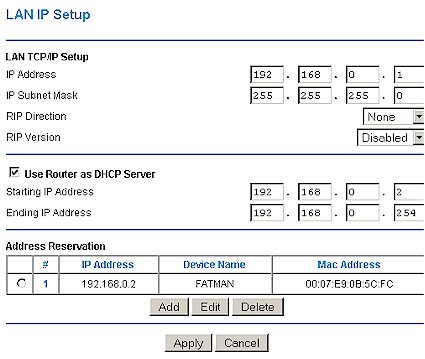
Figure 3: DHCP server and LAN IP setup
IP reservation
This allows you to assign a given IP address to a specific LAN client, or prevent blocks of addresses from being handed out. Figure 3 shows a reservation for the computer FATMAN.
Domain Name
The DHCP server always hands out the IP addresses of your ISP’s DNS servers, but this feature allows you to set a domain name that will also be handed out. If your ISP does not use Fully Qualified Domain Names (FQDN) for its servers (@Home was notorious for this), you may need this feature to allow your LAN clients to successfully receive and send email and browse newsgroups.
NOTE: FQDNs contain host, domain, and top-level domain information, i.e. www.home.com, or mail.home.com. Non-FQDNs typically just have a host name, i.e. mail, news, POP3.
Enable/Disable
This lets you shut off the DHCP server. Can be a useful feature for wireless routers, or if you already have a DHCP server on your network.
Client Listing
Sometimes it’s handy to see what’s connected to your LAN. This feature at minimum shows you the IP address and MAC address of clients that have a DHCP “lease” (assignment). Sometimes the control to invoke this feature is conveniently located on the DHCP server page. But other times, such as in Figure 3, it isn’t.
Lease time
This is more an enterprise or business feature and not commonly found in consumer routers. It allows you to set how often clients must renew their DHCP lease.
Finally, some products also let you see the Host name of the client, force a lease renewal, or disconnect a client.
Port Mapping (Forwarding, Virtual Server)
This feature goes by many names, but they all allow you to open holes (ports) in your firewall. You’ll need to do this for most any Internet applications that depend on the ability of someone on the WAN (Internet) side of your router to send a data request to a computer on your LAN.
There are a few ways that manufacturers implement port mapping, and what you need will depend on what sort of applications you use. Let’s take a look at the different types of port mapping features.
Tip: “Port” in this case, refers to a logical communication connection, not a physical socket. You can think of ports as channels, with certain protocols using particular channels. An example is that the HTTP protocol used for WWW traffic uses Port 80.
Static Single Ports
Figure 4 shows an example of the simplest form of port mapping. You must map each port used by an application to the IP address of the computer that the application is running on. Some routers allow you to specify either the protocol used for the mapping (TCP or UDP). Others automatically map the port for both protocols.
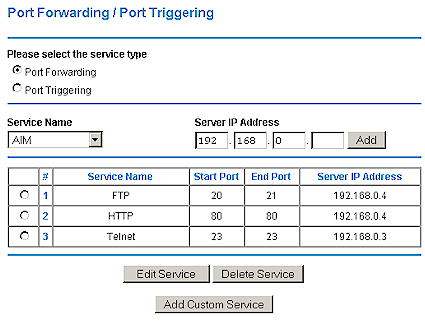
Figure 4: Port Forwarding Example
NOTE: You can statically map a specific port to only one IP address. This means that if you have multiple users who want to use the same application, or multiple servers of the same type, each copy of the application or server would need to use a different port. Some applications allow this to be done, and others don’t.
If you have only a few applications and they use only one or two ports each (i.e. running a web or FTP server) this method should be fine. Although the number of single port maps vary from manufacturer to manufacturer, you’ll typically get somewhere around ten mappings.
Static Port Ranges
Similar to single port mapping, this option lets you map a range of ports in each mapping. Each mapping still applies to only one IP address, however. This option gives you the ability to handle applications that use a lot of ports such as games and audio/video conferencing. Again, the number of mappings varies from product to product, with ten or so being typically offered.
Dynamic (“Triggered”) Mapping
Sometimes called “Special Applications”, this feature attempts to bypass the “one map per IP” limitation of static port mapping. You typically set up a port mapping as you would for a static mapping, but then specify a “trigger” port (and sometimes, protocol). The router then watches the outbound data stream, i.e. data from computers on your LAN headed to the Internet, for the trigger criteria.
When it sees the trigger, it remembers the IP address of the computer that sent the trigger data. When data that matches the trigger request tries to come back into your LAN, the mapping that the trigger is tied to is enabled, and the data is allowed through the firewall. The router then disables the mapping as soon as the transfer is finished so that another computer can use the same mapping. This gives the illusion of multiple computers simultaneously using the same mapping, but, of course, only one computer can use the mapping at a time.
NOTE: Since the trigger event must come from a computer on the LAN, triggered maps can’t be used to allow access to multiple servers on your LAN that use the same port. So if you’re running two webservers, you’ll still need to set up static mappings for two different ports, and configure the webservers accordingly.
NOTE: Triggered maps are best used for quick data requests / transfers because it depends on the mapping being available when another computer triggers it. If you have an application that uses a continuous data stream (i.e. streaming audio or video, Internet phones, etc.), that ties up a port for a long time, a triggered map isn’t going to help you.
UPnP
Universal Plug and Play is a feature that router manufacturers were pretty much forced into by Microsoft. As a result, it has taken a long time for it to be implemented in a large number of routers and the features that are implemented vary widely. One of UPnP’s key tricks is its NAT Traversal feature, which automatically opens ports in a UPnP-enabled router’s firewall for applications that know how to speak UPnP.
My main objection to this “feature” is that it opens these ports without either asking the user’s permission or even providing an indication that it has done so. Since NAT Traversal depends on the application that requests the ports to be opened to also request that they be closed, it’s possible for the ports to be left open if the application crashes or otherwise abnormally exits before issuing the request.
Fortunately, NAT Traversal didn’t catch on much outside of Microsoft and as a result only Microsoft Messenger, Remote Assistance and Remote Desktop know how to automatically open ports on UPnP-equipped routers. My advice is to find the control on your router and disable UPnP if you don’t use these applications.
DMZ (“Exposed Server”)
This is the ability to virtually place one computer outside your router’s firewall. Note that we say “virtually” because the target machine is still physically connected to the LAN side of your router. What this option actually does is map ALL ports through to the IP address that you specify.
When a computer is placed in DMZ, however, it is for all intents and purposes, directly exposed to the Internet. So make sure that any computer placed in DMZ is running up-to-date antivirus software and has no sensitive data on it.
Because DMZ depends on the router’s firmware to do the job, you can have problems with some routers that have buggy implementations of this feature and still not be able to use a desired application even if you place the target computer in “DMZ”.
Mapped Server “Loopback”
If you have forwarded or mapped servers on your router’s LAN side, you would normally reach them by using the private IP address assigned to the computer that the server is running on if your computer were also on the LAN side of the router. On the other hand, users on the WAN side of the router would reach the server via the router’s WAN IP address.
“Loopback” is the ability for LAN-side users to reach a forwarded server via the router’s WAN IP address (or assigned Domain Name if it has one and the proper DNS services are in place). This is a desirable feature that allows users on the same LAN subnet as the server don’t have to hassle with remembering special addresses and can reach a server just like anyone else does. Manufacturers typically don’t specify whether loopback is supported, so do some Googling before you buy if you really need this feature.
Service and Content Filtering
Some users may need to control which users can access Internet services, or restrict access to only specific things like email and web browsing. For this, most all routers provide some sort of service access control (also known as “port filtering”). It works by having you first create groups of users (you actually make groups of IP addresses). For each group, you select specific Internet services (using their port numbers) that you want to control for that group.
Different routers allow different degrees of control, but you’ll usually be able to limit Internet access to a programmed group of services (ports) only, or allow access to all services except a named group. When a user tries to use a filtered service, say AOL Instant Messenger, in most cases the service just won’t work. This can be frustrating for the user and prompt unnecessary calls to tech support (or Mom or Dad) if the router administrator hasn’t told the users about the filters.
A growing number of routers, however, display a message telling the user that their access is being blocked when they trigger a filter. Figure 5 shows a filter that blocks all users from accessing any RealAudio content.
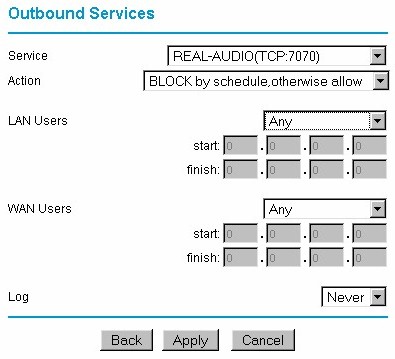
Figure 5: Service Access Control
The average number of port filtering groupings is about four, and the number of ports that can be filtered per grouping varies. Some routers allow you to mix single ports and port ranges in the filter, while others allow only lists of single ports.
In most cases, the filters are either on or off, but some routers allow you to program a schedule for enabling and disabling the filters. The filters can also in some cases be set to make a log entry when they are triggered. The schedule programming allowed is usually not very flexible, usually limited to one time period and the ability to control the days of the week that the time period is used.
Content Control (Content filtering)
Content Controls basically are intended to control which websites your LAN users can access. This feature is similar in function to programs like Cybersitter, SurfControl, etc., but is usually much more limited in function. Some products just allow you to enter the URLs or IP addresses of websites and allow you to restrict access to just those sites, or block the sites. Other routers implement list based filtering and allow you to purchase a subscription to a filter list maintained by a third party. You also might or might not get Time of Day controls for the filtering.
Note that most content filtering features that are included in consumer routers aren’t worth the space they take in firmware. The thirty or so keywords or websites you get aren’t nearly enough to provide effective control over the websites your children or employees visit. And in many cases the filters are easily bypassed by entering the IP address of the desired website instead of its URL. And, of course, there are always anonymous proxy services available for most any content a user is determined to access.
If you’re really serious about controlling the content and web services that your Internet users can access, you should expect to pay for a subscription-based service. One router that we have found to have decent content controls is the ZyXEL HomeSafe Parental Control Gateway.
VPN (Virtual Private Networking)
With the increased focus on network security, this feature is becoming more important to people who need to connect to their office from home or while traveling. Many businesses are allowing connection to their internal networks only through these encrypted connections, and the router makers are responding by improving the VPN features of their offerings. Router VPN features do vary, however, so it’s important to know what type of VPN support you need.
Protocols
The two most commonly used VPN protocols are PPTP and IPsec. PPTP (used by Microsoft’s Virtual Private Networking feature) is the most commonly supported, although most routers now also support IPsec as well. A third protocol, L2TP, is not very widely supported, so if your VPN uses it, check your prospective router’s specs carefully.
Pass-Through
The simplest form of VPN support is pass-throuth. A router supporting this mode will simply allow VPN data packets to pass through its firewall unmolested. It’s then up to the client computers on the LAN to run appropriate VPN client software in order to complete the VPN “tunnel” and successfully connect to the remote VPN server.
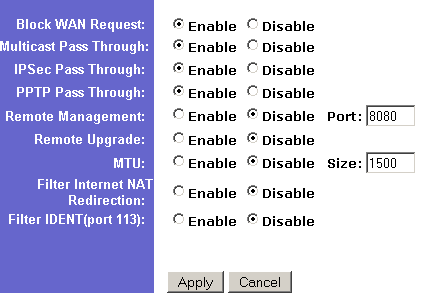
Figure 6: VPN Passthrough and other controls
Most router manufacturers say their products support VPN pass-through, but your actual experience may be different. Problems are sometimes due to buggy router firmware, but can also be due to the fact that some VPN configurations won’t work through a NAT firewall. You also may need to specifically enable VPN pass-through, as indicated in Figure 6.
Tip: The following VPN configurations will not work through a router’s NAT firewall:
• IPsec using Header Authentication
• IPsec and unencapsulated FMZ encryption
Routers also differ in the number of pass-through connections they handle. Although not important for a lone telecommuter, this spec is important to small businesses trying to run VPN connections among multiple locations. Some products handle only one pass-through client at a time, while others will handle multiple clients. However, some routers require that all the pass-thru sessions go to the same VPN server. In the small business example above, this limitation would not let two users at the same location each connect to a different remote location. You won’t be able to find this level of detail in any manufacturer’s spec, but fortunately, we do include this information in most of our product reviews.
One more potential “gotcha” is the ability of the router to support VPN servers behind it. You’ll of course have to map the appropriate ports, or put the VPN server in DMZ, but unless the router knows how to handle the specially constructed VPN data packets, your VPN clients won’t be able to connect. So if you need to have a VPN server behind your router, make sure it supports PPTP or IPsec server pass-through.
End-Point
This VPN feature is also called “VPN Edge”, and it’s the ability of the router to either originate or terminate a VPN tunnel. This allows the router to handle the VPN chores, and free LAN clients from having to run VPN client software. It also allows you to use two similarly-equipped routers to set up a VPN tunnel between two locations, without using any other VPN software or hardware.
This feature used to be available only in products above $500, but there are now alternatives such as Buffalo’s WZR-RS-G54 125* High Speed Mode Wireless Remote Secure Gateway and Netgear’s FVS318 ProSafe VPN Firewall that can get the job done for around $100.
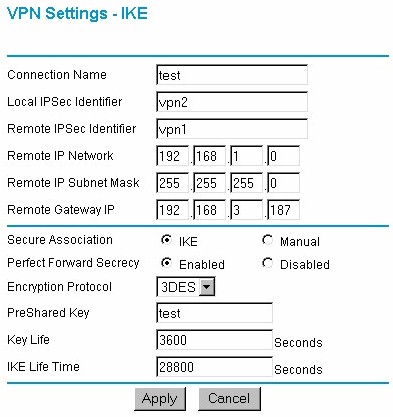
Figure 7: Setting up an IPsec connection
Figure 7 shows, however, that VPN setup can still be a daunting task and unfortunately, consumer router manufacturers aren’t much help if you run into trouble.
If you’re shopping for routers with this feature, make sure you check whether PPTP is supported if you need it (some products support just IPsec in the End-point and pass-thru only for PPTP). And if you’re planning to access your network while traveling, see if they either bundle in VPN client software, or offer a discount toward the purchase of a suitable client.
Logging
Logging is your router’s way of telling you what it’s been up to, and more importantly what the folks using it have been doing. Most consumer-class routers have fairly simple logging features and little or no way to “drill down” into the data to look at a particular user’s activity. Logs entries tend to be pretty cryptic and in many cases, indeciperable to non-technical users (Figure 8).
Figure 8: A not-so-helpful log
Other products do a better job of formatting log information and translating it into something that non-geeks at least have a chance of understanding (Figure 9).
Figure 9: You might be able to understand this log
The three main types of data that are logged are administrative, “hack attempts”, and user traffic. Administrative activity includes things like router startup, shutdown, and reboots. You’ll also find admin interface logins, too. “Hack attempt” logs usually include any attempt to access your router from a machine on the WAN or Internet side of the router. These attempts are usually not aimed at your router specifically, but result from broad network (or subnet) wide port scans from any number of sources.
Routers can usually interpret and log more potentially damaging attacks such as Denial of Service (DoS), fragmented packet, and other nasty stuff. Finally, user traffic logs keep track of the website, FTP, and other data requests that users make for Internet services.
As mentioned earlier, many routers provide a simple log interface, usually consisting of a page in the admin interface where you can just view a raw list of the logged activities. Some routers allow you to clear and/or save the list to a file, while others just keep a certain number of logged events, discarding the oldest ones as new events are added.
Another kind of simple log is a URL or web traffic log, which may just show the number of visits to a specific web domain, without keeping track of the specific pages visited. If you’re interested in keeping track of what a specific user is doing, or need other cuts at the logged data, you should look for products that support external logging.
There are two methods used for external logging. Syslog support lets you specify the IP address of a machine on your LAN that runs a syslog daemon or server. This handy service originated in the unix community and can be added to a Windows or MacOS systems by installing one of the programs that are available. Once installed, it allows your router to send it a copy of its logging information, which can be then be manipulated in various ways.
The other popular external logging method is the SNMP trap, which is the method primarily used by some Linksys routers.
Finally, some routers support Email alerts and reports. These features allow the router to send an email when it detects certain access (“hack”) attempts from the router’s Internet side, or email a copy of selected log reports on a scheduled basis. Nice features to have if, like most of us, you don’t have the discipline to regularly check your logs!
Routing and QoS
Some routers have non-NAT routing features. This means that instead of manipulating data so that many computers can share a single IP address, the router can properly direct traffic among all computers on networks that use more than one range of IP addresses. One of the key functions performed is making sure that all computers know the IP addresses of the various network gateways and DNS servers and where to send data that’s intended for computers that are on different subnets.
Note that this feature does not solve the problem of getting Microsoft File and Printer sharing to work so that all machines on all subnets can see and communicate with each other. That requires a Domain controller, which you get by either adding a Microsoft-based server or machine running SAMBA.
There are two kinds of additional routing features. Static routing requires that you manually enter subnet information into the router. Dynamic routing uses RIP (Routing Information Protocol) to allow RIP-aware devices to share network routing information automatically.
If this explanation isn’t that clear to you, don’t worry too much. If your network were complicated enough to require these functions, you probably already know more about them than we do!
Quality of Service (Qos)
QoS is the ability of the router to prioritize the handling of some packets over others. This is most useful for applications requiring “real-time” response, such as gaming, VoIP, and multimedia streaming. It also holds the promise of being able to allow control of the bandwidth allocated to specific users and/or applications. But as I write this in late spring 2006, QoS is still in its infancy as far as most consumer routers are concerned and inconsistently supported.
For example, some of the most expensive MIMO routers such as Netgear’s RangeMax 240 have no QoS features at all, while less expensive products such as D-Link’s Gaming routers have Ubicom’s sophisticated automatic StreamEngine QoS technology (D-Link calls this “GameFuel”. But while StreamEngine is slick and works well, it works for upstream traffic only. This makes it useless for keeping little Susie’s music downloading habit from dominating the home Internet connection. And as Figure 10 shows, QoS controls have a way to go in order to be user-friendly.
Figure 10: D-Link GameFuel QoS settings
The good news is that the emphasis on web-based multimedia applications should push manufacturers in the direction of implementing QoS more consistently and across their product lines. In the meantime, however, don’t assume that your router has QoS features.
Other Features
This final section will attempt to capture all the rest of the features that you’re likely to find in NAT routers that don’t really fit neatly into any of the previous headings.
Remote Administration
This feature allows you to access the admin screens of your router from the WAN (Internet) side. Very handy if you travel frequently and need to adjust a setting on your router, or if you’re responsible for keeping routers at customer sites up and running. Since this feature can potentially allow anyone to gain control of your network if it’s not properly secured, you need to look for products that have ways to make it harder for anyone besides you to control the router.
At minimum, you should be able to restrict Remote Admin access to specific IP addresses or range of addresses. Better yet, but harder to find, is the ability to specify the port number that you use to access the Admin HTTP server. This means that someone would not only have to know your router’s WAN IP address, but also the port number that you’ve assigned.
Finally, although they are hard to find, a router that supports secure HTTP (HTTPS) is an even better choice if you need to administrate a router remotely. Fortunately, Linksys seems to have added this capability to their popular WRT54G wireless routers.
Print Server
This feature was made popular by SMC’s original Barricade line of routers. It allows you to connect a printer to the router instead of a networked computer and offload the printer sharing tasks to it. This means that printing doesn’t depend on a particular computer being up and running, and can also allow you to move your printer to a more centrally located spot.
But it’s much more difficult to find routers with built-in print servers today. Instead this feature looks like it has moved to being more frequently included in Networked Storage (NAS) products.
When you do find routers with print servers, they’re more likely to support USB instead of parallel-port printers. In addition, most router-embedded print servers don’t have much memory (limiting the size of files that can be printed), may not handle printing from MacOS computers, and don’t support bi-directional printer features.
But if you must have this feature, check out the Netgear FR114P, FWG114P or Trendnet TW100BRF114U.
Dynamic DNS (DDNS)
Most of us have Internet service that uses a dynamic IP address that changes on a periodic basis. This doesn’t bother most Internet users, but is a problem if you need to connect back to your LAN from across the Internet. You’d need to do this if you were making a VPN connection back to your home office, for example, or trying to monitor a “nanny-cam” to check up on what’s happening at home.
Fortunately, dynamic DNS services can come to the rescue. These services let you register a domain name and use a client running on one of your LAN computers that tells the service when your assigned IP addresss has changed. So when you want to “phone home”, you just use your domain name, which the dynamic DNS service keeps pointed at the proper IP address.
Since the router is the actual device that holds the WAN IP address, it makes sense to run the dynamic DNS client there instead of on a LAN computer. Many routers now come with built-in dynamic DNS clients that support at least dyndns.org and more frequently services such as TZO.com.
Take me to the Hardware Router Chart
