Introduction
Last time, you got a general introduction to "smart" / managed switches (NETGEAR’s GS108T in particular) and a walkthrough its port-manipulation features. This time, I’ll show how to use a smart switch to enhance your LAN’s security.
But first, an SNB forum reader asked that I check to see if enabling port mirroring caused a throughput hit in the GS108T. So I fired up IxChariot and sent TCP/IP traffic between two machines connected by the GS108T. While the traffic was running, I enabled port mirroring on one of the in-use-ports and mirrored it to first an unused port, then to the other port that was being used by the test. In neither case could I see any affect on the traffic being sent. Now back to our program.
The GS108T’s security-related features are grouped under its Security tab. Some of the features, like Port Authentication, require a companion RADIUS server and I’ll come back to those shortly. But other features can help you tighten up your small network’s security without wrassling with RADIUS.
Port Security
The simplest function is Port Security. While you wouldn’t know if from the description in the GS108T user manual, this feature lets you lock down switch ports. Figure 1 shows me locking down Port 4 using the Discard action, which configures the port so that traffic from any other device physically connected to the port other than the "learned" one will be discarded.
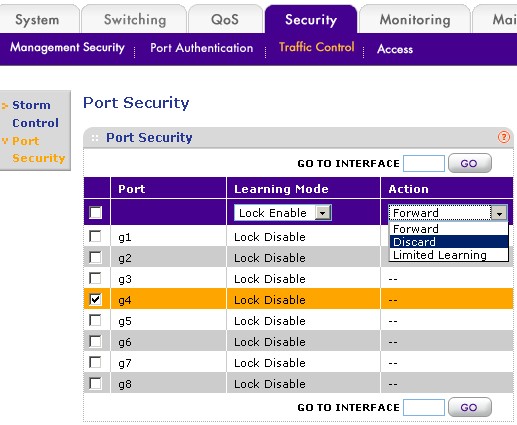
Figure 1: Configuring Port Security
Forward is kind of the reverse of Discard in that if you move the "learned" device to any other port, it will be locked out. But data from any other device plugged into the "locked" port will be sent (or received) normally. The last option, Limited Learning, is handy if you have another small switch uplinked to the "locked" port. It will allow traffic to and from 16 MAC addresses, but then block traffic from anything else.
The other feature on the Traffic Control tab—Storm Control—probably won’t find much use in a small LAN. It is there to protect against network "storms" or floods of network traffic that are sometimes caused in large multiswitch networks. You have seen a network storm if you accidently connected two ports together on a switch and then saw the link / activity lights flash wildly.
But what if you’d like to have the equivalent of the MAC Address filtering that you find on wireless routers? You can find that in the Security > Access menu’s Trusted MAC function (Figure 2). Unfortunately, the feature in the GS108T isn’t very user friendly. There is no pick list of currently-learned MAC addresses to use in creating your list of trusted addresses.
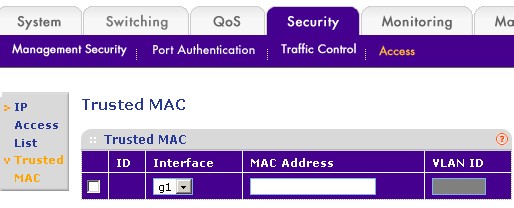
Figure 2: Trusted MAC address
But the bigger uh-oh creator is that as soon as you enter the first trusted address, all others are disabled. So make sure that the first address that you enter is the one for the computer (and the port that it is connected to) that you are using to administer the switch! Or you’ll end up having to do a paperclip reset to defaults (and redo all of your other settings or reload a saved config file) to get back into the switch admin!
Port Authentication
Another way to control LAN access is to have users actually log in or authenticate. Smart / managed switches usually support this option and so does the GS108T. But the GS108T requires a RADIUS server somewhere on the network to store the user credentials and perform the authentication.
Figure 3 shows the GS108T’s Port Authentication controls, which include the ability to allow access if the RADIUS server is not available and the ability via the Guest VLAN setting to send anyone failing authentication to a particular VLAN. This technique effectively puts unknown users on a separate network from authenticated users and perhaps given only Internet access.
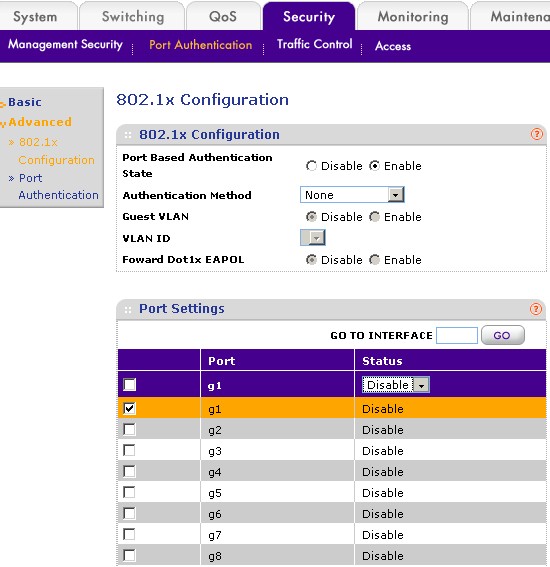
Figure 3: Port Authentication
Setting up a RADIUS server is beyond the scope of this article. But you might get some clues from How To: Setting up FreeRADIUS for WPA & WPA2 Enterprise – Part 2. Another trick is to purchase a wireless AP/router that has a mini-RADIUS server built in. Zyxel has a few, including the NWA-3160. For about $140/$150 you could save yourself a whole lot of hassle!
VLAN
VLANs or Virtual LANs are another way of implementing network security by controlling broadcast traffic. Since network broadcasts are used by ARP to match up MAC and IP addresses, if you control broadcast traffic, you control the ability of devices to communicate.
Most smart switches allow you to set up VLANs either based on physical ports or using the 802.1Q protocol. Using 802.1Q adds VLAN information to packets so that VLANs can be created across multiple switches and even subnets. For single-switch LANs, you can use port-based VLANs, as shown in Figure 4. Note that VLANs don’t create multiple subnets, so all devices will still be on whatever subnet that your router’s DHCP server assigns.
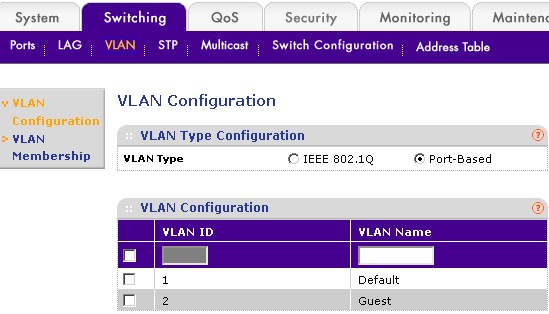
Figure 4: Settting up port-based VLANs
Using port-based VLANs, it’s simple to set up a "Guest" VLAN that allows Internet access, but no access to other LAN clients. Unfortunately, the GS108T’s GUI shows VLAN membership for only one VLAN ID at a time. So Figure 5 is actually a composite that I created from two screenshots.
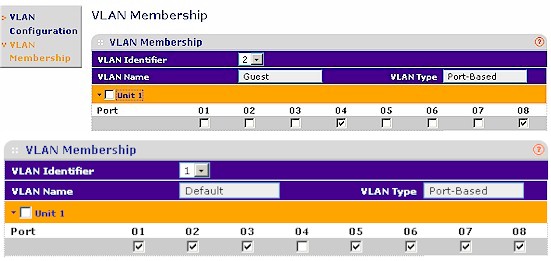
Figure 5: Guest VLAN port assignment
The "Guest" port 4 and the switch uplink port 8 (which connects out to my LAN’s router) are assigned to VLAN 2 and port 4 is also removed from VLAN 1. Since the uplink port is a member of both VLANs, the computer connected to port 4 can connect out to the Internet, but can’t connect to any devices connected to the other GS108T switch ports.
That’s it for this time. The next and last installment will show you how to use a smart switch to control client bandwidth use.
