This article is sponsored by Luma.
The recent Mirai attack showed how hacked IoT (Internet of Things) devices can be used to take down websites and services we rely on. With IoT devices projected to number in the tens of billions by 2020, possibilities of future attacks will increase. This makes it all the more important to keep your home network safe from malicious hackers.

The Mirai attack was a wake-up call
Hacked IoT devices aren’t the only problem. Stolen passwords, weak security settings, unpatched vulnerabilities and social engineering can make your network an easy target for hackers and scammers. Home networks become the soft targets predators are looking for and your router is often the vulnerable entry point.
Luma recently analyzed hundreds of thousands of computers and connected devices across tens of thousands of home networks and found 2 out of 3 homes have malware on their home network and 1 out of 6 IoT devices have a security problem.
Luma’s Surround WiFi System has always focused on strong network security, with built in features that competing systems lack.
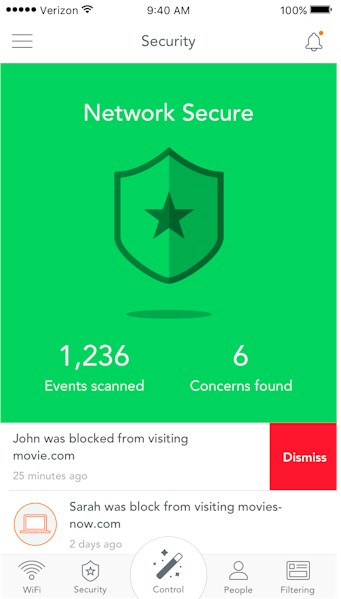
Luma can detect and automatically block bad stuff
Luma security starts with a comprehensive view of what’s on your network. Devices can be assigned to users so that access rules and parental controls can easily be applied.
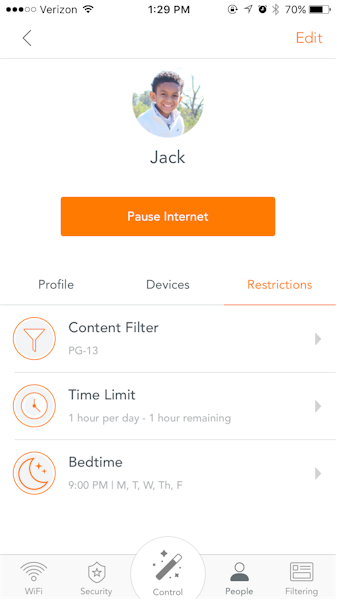
Luma makes parental controls easy
If an unknown device is found on the network, Luma can send a notification through the app, alerting the owner of the unidentified device.
Using a combination of Luma’s own and third-party databases, Luma identifies harmful activity such as ad fraud, botnets, malware, spyware, spam and phishing. Luma uses these databases to continuously watch for hacks, malware, and other related infections that put your security at risk.

Luma watches for viruses
Luma detects traffic destined for known malicious/dangerous websites both locally and with policy queries to Luma’s cloud as needed. Luma can understand if a client inside the network is infected with malicious software causing a botnet "phone home", for example, and send an alert. Even better, a recent update now provides the option of automatically detecting and blocking malicious activity.![]()
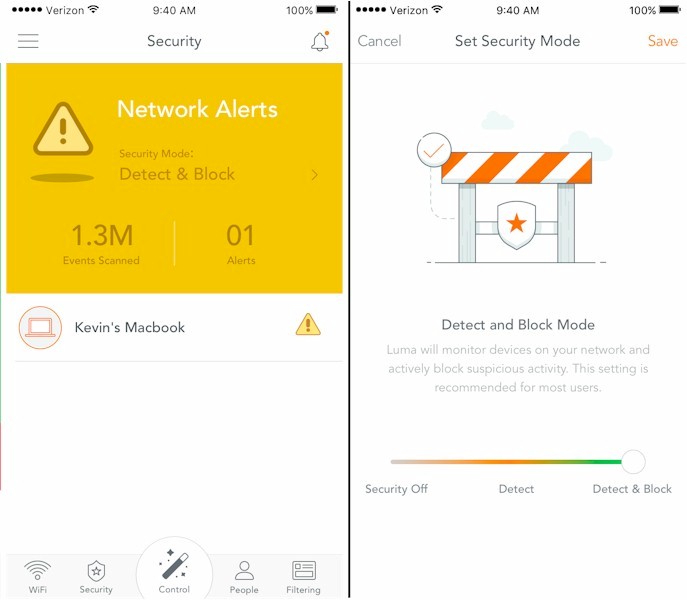
Luma can detect and automatically block bad stuff
Of course, Luma’s Surround WiFi also uses WPA2-AES, the most advanced WiFi security available. Coupled with a strong WiFi password, this Wi-Fi Alliance certified standard uses advanced cryptographic algorithms to protect data in transit from prying eyes.![]()
WPA2-AES is also used on Luma’s guest network, which allows visitors to access your internet connection, but keeps them separated from other devices on your network.![]()
To sum up, Luma protects you from the constant barrage of hackers and malicious software trying to access your home network and compromise your security. And Luma constantly updates its cloud and devices to protect you. ![]()
The rise of IoT devices is just beginning. So as your home becomes smarter and more of your devices become Internet-connected, it has never been more urgent to have a safe, secure home network. Luma is the only WiFi system that provides great WiFi and best-in-class home network security. Learn more at getluma.com.![]()

 Read more about Luma.
Read more about Luma.