Introduction
| OvisLink eLive Multimedia Server / VPN Router | |
|---|---|
| Summary | Multi-talented router supporting IPsec and PPTP VPN & 4 USB ports. Has integrated webcam and FTP servers & supports up to 4 USB printers. |
| Update | 18 November 2005 – Corrected Flash and RAM info 4 August 2004 – Updated PPTP and IPsec info |
| Pros | • Many features not usually found in SOHO routers • Bandwidth control by application or IP address |
| Cons | • Jack of all trades, master of none • Low IPsec tunnel bandwidth • Bandwidth control applies to upstream traffic only |

OvisLink is a company better known in Europe and Asia than in the U.S., but it’s been in business over a decade and has a broad line of wired and wireless products. Our on-going quest for unique networking products recently discovered its MU-9000VPN eLive Multimedia Server / VPN Router, which has a number of features that set it apart from the pack.
The 9000VPN is also available as the WMU-9000VPN, which adds 802.11g wireless capability via a Conexant PRISM-based mini-PCI card. All features in the 9000VPN are also contained in the WMU-9000VPN.
Basic Info
The 9000VPN is packaged in an attactive light blue plastic case that has the footprint of a typical hardcover novel and stands about 1.25 inches (30mm) tall. The enclosure has wall-mounting screw slots on the bottom, and isn’t designed to be stood vertically on its side.
All indicators are on the front of the box, are bright and easily viewable from a wide angle. You get Link / Activity and 10/100 lights for each of the single WAN and four LAN ports, plus indicators for Power and Status and PPPoE. There are also two E-mail lights, whose function I’ll explain later.
The rear of the 9000VPN is where things get a little interesting. In addition to the expected four 10/100 LAN ports, one 10/100 WAN port, power jack and Reset / Reset-to-factory-defaults switch you’ll also find four USB 2.0 ports and a 6 pin DIN-style HDD Power connector. Note that all LAN ports are auto MDI / MDI-X, though OvisLink doesn’t spec or mention this.
Internal Details
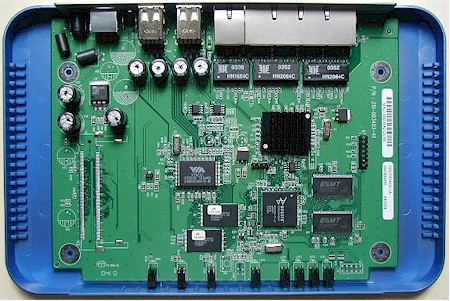
Figure 1 shows that the 9000VPN is powered by a Brecis MSP2006 Multi-Service Processor clocked at 170MHz. The MSP2006 is a MIPS-based microcontroller designed for access points and wireless routers which includes two 10/100 Ethernet PHYs and a PCI bus interface. It doesn’t however, contain a hardware encryption co-processor, which you’ll see later affects its performance as an IPsec endpoint.
Figure 1: MU-9000VPN board
(click on the image for a full-sized view)
Both the WAN and LAN ports appear to be handled by a switch chip whose identity hides under the heatsink that you can see in the board photo. The USB 2.0 ports are courtesy of a VIA Vectro VT6212 USB 2.0 Host Controller and 8MB of flash and 32MB of RAM perform the memory chores.
Note that the same board, loaded with a mini-PCI connector and equipped with a FiWin WM680-110 PRISM-based radio, becomes a WMU-9000VPN. The connector mounts in the spot at the lower left of the photo where you see the empty connector pads.
Setup and Administration
TIP: You can check out the 9000VPN’s Admin interface yourself by using OvisLink’s on-line demo.
The 9000VPN comes set to 192.168.1.254as its factory default, its built-in DHCP server enabled and WAN connection type set to Static. Once you enter the default password, you’ll be sent to the Quick Setup page (Figure 2).

Figure 2: Quick Setup page
The router supports a number of WAN connection types, including common and not-so-common ones:
- Static
- DHCP (with Host Name option)
- PPTP – DHCP and Static
- Big Pond Cable
- L2TP – DHCP and Static
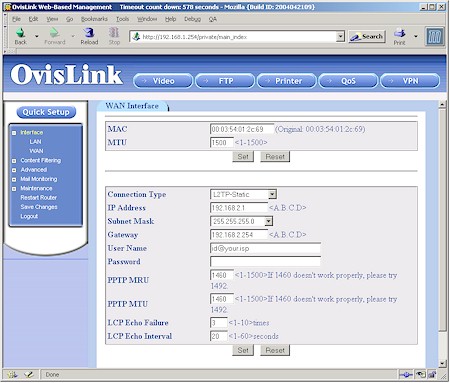
Figure 3: L2TP WAN setup
Since the L2TP option isn’t so common, Figure 3 shows you what the setup is like – pretty much the same as a PPTP connection. Note that MTU adjustment and changing the WAN MAC address are supported for all connection types. I used the DHCP option for my testing and had no problems with the router acquiring IP address info from my LAN’s main DHCP server.
The browser interface is pretty responsive and saving changes made on each page is relatively quick. But there isn’t a prompt to remind you to click the Save Changes menu link to store the changes to non-volatile RAM. So it took me awhile to figure out why my changes would go away each time I power-cycled or rebooted the router.
I had no problems using either IE or Mozilla (OvisLink lists Mozilla 1.0, Netscape 7.0 and IE 6.0 as supported right on the log in page) but you’ll need to enable cookies and Javascript.
Multiple admin logins are allowed, with no warning given when more than one admin logs on. Once you’re logged in, you’ll be automatically logged out after a 10 minute timeout, which you can adjust from 3-35791 (!) minutes on the Maintenance > System Management Setting page. You can also use the logout button or simply close your browser when you’re done.
The System Management Setting page also has controls for changing the Admin server’s port from the default of 80 and enabling secure (HTTPS) management. I feel the latter feature should be supported on any product that provides web-based administration, so OvisLink gets points for including it. The 9000VPN also lets you create a list of single IP addresses or address ranges that are allowed or denied remote administration privileges.
Rather than bury them in the usual set of nested menus, OvisLink chose to put buttons for its unique “multimedia” features in a button bar that sits at the top of every Admin server page. I’ll attempt to hit the highlights of each of the Video, FTP, Printer, QoS and VPN buttons next.
Video Server
The Video Server feature supports a wide variety of USB cameras and turns them into web-enabled cameras, supporting both live streaming and motion-triggered features. Unfortunately, I didn’t have a compatible camera handy, so couldn’t give this feature an actual workout.
TIP: The 9000VPN supports cameras using OmniVision and Philips chipsets. See this OvisLink page for a list of supported USB devices.
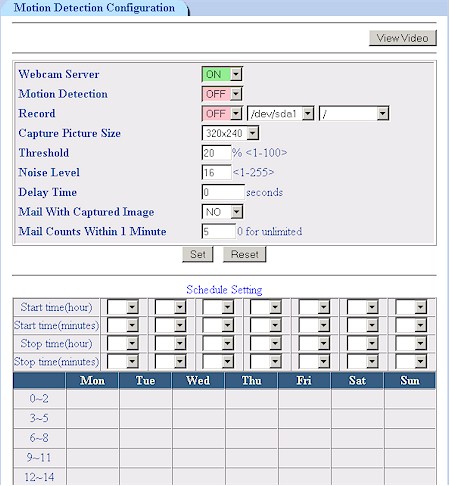
Figure 4: Video Server controls
Figure 4 shows all the controls you get except for the two email addresses where you can send motion-triggered snapshots. Captured picture sizes can be set to the 320 x 240 shown or a smaller 176 X 144 size. Images can also be recorded in AVI format on any USB drives that you have attached to the system. Recordings will last as long as motion is detected and OvisLink says their next firmware will add a setting to control the time between no motion being detected and the end of recording.
FTP Server
Since OvisLink says they didn’t have room to implement a SAMBA server to provide complete Networked Storage features, they opted instead to include a decent FTP server. To check this feature out, I plugged in the 160GB One-Touch USB 2.0 drive that Maxtor loaned me for my review of Linksys’ NSLU2 Networked Storage Adapter and a 32MB Flash drive I had lying around.
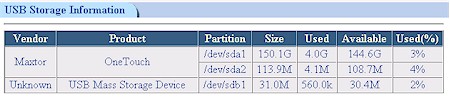
Figure 5: FTP volume information
Both drives were recognized without muss or fuss and Figure 5 shows how they appeared when I clicked on the Show USB Storage button on the FTP Server Configuration page. I liked that the server recognized both drives, even though the OneTouch was formatted for ext3 and the USB Flash drive FAT formatted.

Figure 6: FTP Server configuration
Figure 6 shows you get a pretty good set of controls including port, active / passive mode (including setting the passive mode data transfer port range) and maximum number of clients to name a few. Following good security practice, the FTP server is disabled by default and even when enabled defaults to being available to LAN clients only.

Figure 7: FTP User Account setup
Figure 7 shows the user account settings, which include the ability to limit maximum upload and download speed and limit user access to specific IP addresses or ranges. I set up both Anonymous and normal accounts and logged in using an FTP client and IE and Mozilla browsers without problems. I also successfully made file transfers in both directions using both my FTP client and drag-and-drop with IE.
I would have liked to see a simple disable for FTP user accounts, though you can accomplish (almost) the same thing by changing a user’s password to a different, strong one.
Print Server
As is the case with many print servers integrated into routing products, you don’t get any controls to twiddle. So if your printer meets the requirements of supporting standard TCP/IP printing using the RAW protocol and it still doesn’t work, your only recourse is to double-check your settings.
The admin interface Printer button either shows you the status successfully connected printers or steps you through an on-line copy of essentially the same setup information for WinXP/2000 or Linux OSes that’s in the User Manual. If you’re running Win98 or Me, the on-line help and User Manual directs you to install a little program from Axis, which should get you hooked up for those OSes.
The only USB printer I had was an Epson Stylus C80, which installed and ran without a hitch. OvisLink says that the 9000VPN will handle up to four USB printers (if you have nothing else connected) assigning each one to its own port (9100, 9101, etc.)
QoS / Bandwidth Control
Regular SmallNetBuilder readers know that I think that Bandwidth control is a very desirable feature to have on SOHO routers. Implemented correctly, it can keep kids (or employees) from sucking up the bulk of your bandwidth for music and video downloads, or any other undesirable activity. So I was looking forward to seeing how this feature checked out in the 9000VPN.
But my enthusiasm quickly cooled once I realized that the 9000VPN’s QoS feature allows upstream bandwidth only to be capped to programmable values. This means that it will help if someone on your LAN is running a server that uses up a lot of bandwidth, but it will have no effect for over-active downloaders.
At any rate, bandwidth can be limited by IP address (Figure 8) or Application / Port (Figure 9).
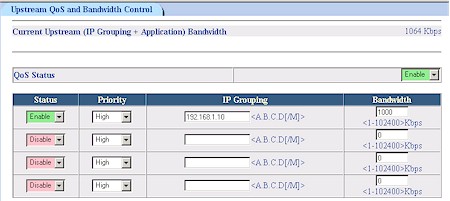
Figure 8: QoS by IP
This implementation is more flexible than the physical port method used by the Draytek Vigor 2900G [reviewed here], but I feel the upstream-only control seriously limits its usefulness.
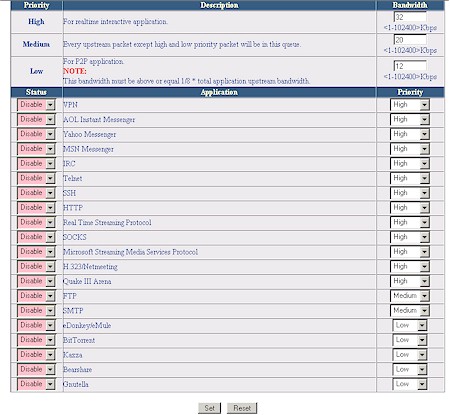
Figure 9: QoS by Application
I used Qcheck to run a simple throughput test using the IP Grouping settings shown in Figure 8. I confirmed that the bandwidth cap was in effect for the LAN to WAN direction only, and found that a setting of 1000kbps yielded a measured throughput of about 440kbps, less than half the programmed value.
I also was confused by the Priority selector in the IP Grouping section, since the High, Medium and Low Priority settings are used for Application QoS. But OvisLink assured me that the IP Grouping setting would take priority over the Application level setting. If that is the case, I think OvisLink should remove the Priority selectors from the IP Grouping section.
VPN
The last button in the 9000VPN’s bag of special tricks brings up its VPN functions. Both PPTP (Figure 10) and IPsec servers (Figure 11) are supported, with 10 connections allowed for PPTP and, theoretically, up 100 IPsec tunnels.
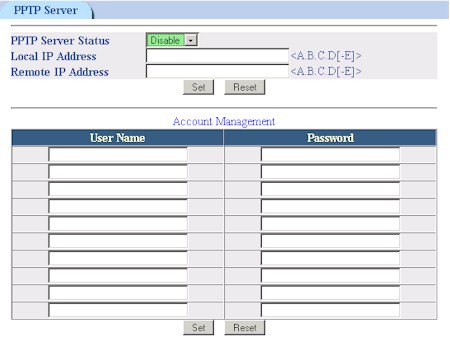
Figure 10: PPTP server setup
I provide the “theoretically” caveat because my test of an IPsec router-to-router tunnel using a MU-9000VPN and its WMU-9000VPN wireless sibling yielded the disappointing results shown in the table below.
IPsec VPN Performance test results
|
Firmware Version: |
1.01.039 Mon Jun 7 15:14:11 CST 2004 |
|
Test Description |
Transfer Rate (Mbps) [1MByte data size] |
Response Time (msec) |
UDP stream |
|
|
(Actual throughput- kbps) |
(Lost data- %) |
|||
|
Local to Remote |
0.736 |
5 (avg) |
221 |
52 % |
|
Remote to Local |
0.613 |
10 (avg) |
128 |
71 % |
[Details of how we test can be found here.]
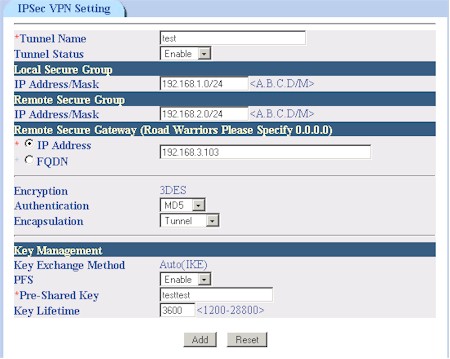
Figure 11: IPsec server setup
This result isn’t surprising, given that the Brecis processor that powers both 9000VPN’s doesn’t include an encryption co-processor.
The IPsec configuration parameters are minimal, though adequate for setting up a tunnel between two 9000VPNs as I did. Only 3DES encryption is supported, but you get a choice of MD5 or SHA1 for Authentication. Key Management is limited to IKE only, but you can enable Perfect Forward Secrecy (PFS) and set the key lifetime.
Updated 4 August 2004 OvisLink will be adding support for AES tunnel encryption in their version.41 firmware.
I should also note that the 9000VPN doesn’t provide tunnel setup logging. You can only check the SPI (Security Parameters Index) information via the Show IPsec SPI Information button after setup to see whether anything appears. If the information is blank, however, you’ll have no clue as to what is wrong with your setup.
Updated 4 August 2004
I retested the PPTP server portion of the 9000VPN using correct configuration information that OvisLink has incorporated into a stand-alone VPN Setup Guide (PDF), which also contains IPsec tunnel setup information. This time I was able to both establish a PPTP connection and run a set of Qcheck tests whose results are shown in the table below.
PPTP VPN Performance test results
|
Firmware Version: |
1.01.039 Mon Jun 7 15:14:11 CST 2004 |
|
Test Description |
Transfer Rate (Mbps) [1MByte data size] |
Response Time (msec) |
UDP stream |
|
|
(Actual throughput- kbps) |
(Lost data- %) |
|||
|
Local to Remote |
3.6 |
4 (avg) |
499 |
0 % |
|
Remote to Local |
3.1 |
5 (avg) |
195 |
61 % |
[Details of how we test can be found here.]
Throughput is significantly higher than what I obtained in my IPsec tunnel tests, primarily because the 9000VPN PPTP server uses encryption only for the login process and does not encrypt data traffic.
Fortunately, if you can’t, or don’t want to, use either the IPsec or PPTP servers, you can instead use VPN pass through with IPsec, PPTP or L2TP client applications. And if you want to run a different IPsec, PPTP or L2TP server on the 9000VPN’s LAN side, OvisLink says the firewall will handle those protocols when you configure a firewall rule to expose the server.
Firewall Features
The 9000VPN’s firewall has the ability to expose LAN side servers to the Internet (Virtual Servers) and establish firewall rules for inbound and outbound traffic (also known as port filtering). Figure 12 shows the Virtual Server controls, which contain a few controls not typically found.
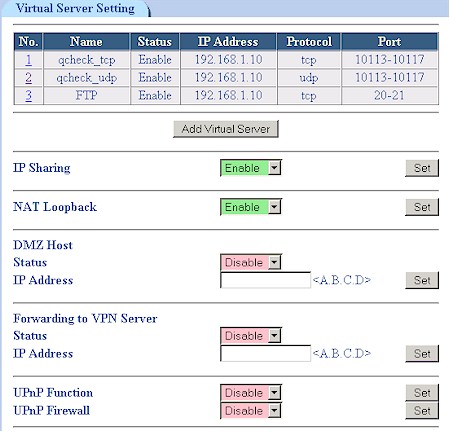
Figure 12: Virtual Servers
The IP Sharing control can be used to disable the NAT (Internet sharing) function, which would make the 9000VPN function as a normal router. NAT Loopback lets LAN-side users reach Internet accessible servers via their public IP addresses or domain names, instead of having to use local IP addresses. This desirable feature is found on competitive products, but the 9000VPN is the first time I’ve seen it under user control.
The Forwarding to VPN Server control isn’t described in OvisLink’s documentation, but I found out that it is essentially a special Virtual Server enable in case you want to have your own PPTP server running on the router’s LAN side instead of the built-in server. I liked that UPnP defaults to being turned off and that you can separately disable the NAT Traversal function that lets UPnP automatically open holes in your firewall.
Both the Virtual Server and Firewall (port filtering) features use a pre-defined list of Services (Figure 13), to which you can add your own. You can specify a single port or range and select from TCP, UDP and ICMP protocols. Note that you can’t edit defined service, but can delete them.

Figure 13: Services
Speaking of the Firewall, Figure 14 shows a rule that I set to block Web access. This is as good a time as any to highlight OvisLink’s use of “slash” or CIDR Notation. While its use may be more natural to networking professionals, I feel it’s not appropriate for use in a SOHO product – especially when there is no explanation of how to use it in the User Manual.
In the case of setting firewall rules, it makes setting a rule that applies to a list of IP addresses difficult, if not impossible – forcing a user to use up multiple rules to achieve the desired effect.
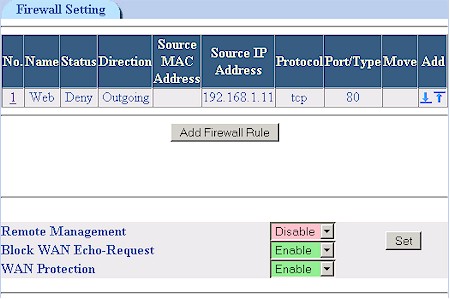
Figure 14: Firewall Rules
Note that neither Virtual Servers or Firewall rules can be scheduled, i.e.enabled by day and time. There are also no firewall controls to block cookies, Java and Active X applets or Web Proxies.
Content Filtering
The 9000VPN contains the most robust and complete set of Content Filters that I’ve seen. Where as most of the URL filters found on SOHO routers are easily bypassed by entering the IP address for the website of interest, that trick won’t get you by this router’s URL Blocking feature.
Competing “keyword” filters usually just screen for the keyword in the website’s URL, but the 9000VPN’s Keyword Filtering (Figure 15) actually parses webpage content for the offending string, which can also be a regular expression! Other unique options for this feature include the ability to apply the filter to gzipped content and make the search case insensitive.
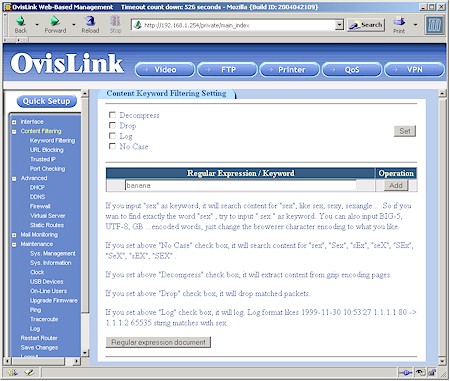
Figure 15: Keyword Filtering
You get 20 entries each for URL and Keyword filters and when they kick in, the user’s browser just hangs.
For those users who can take everything the web has to dish out, you can use the Trusted IP feature to define IP and port ranges that will bypass the content filters. Finally, the Content Filter Port Checking page lets you specify the ports – in addition to the default 80 / HTTP – that that the filtering features are applied to.
Logging and Other Features
Many events of interest are logged (Figure 16), and the 9000VPN’s interface give you the ability to show All, System, Incoming, Outgoing, Firewall and Content Filter events. Web traffic is logged via the Outgoing log, but reverse DNS isn’t supported so you’ll have to figure out where Junior is browsing by looking up the logged IP addresses yourself.
Negatives are that neither email alerts or periodic emailing of logs are supported and new events are added to the end of the log, forcing you to click through multiple pages to see the latest happenings. That syslog enable you see in the screenshot below is also tempting, but it currently doesn’t work since it doesn’t allow you to specify the IP to send the logs to.
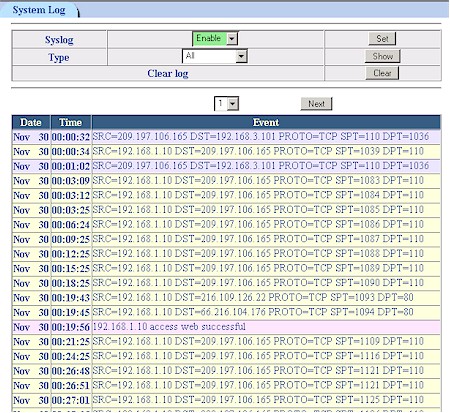
Figure 16: The Log
There are a number of other features to be found among the 9000VPN’s admin pages, which I’ve summarized below for your convenience:
- The Mail Monitoring feature lets you define six groups of six users each that can be on six secure or unsecure POP3 and IMAP servers. Two lights on the 9000VPN’s front panel can be set to various combinations of on, off and blink to indicate when incoming mail has been processed for any of the defined users.
- You can view assorted LAN and WAN traffic statistics
- Dynamic DNS is supported for DynDNS.org and ODS.org
- DHCP server that allows you to set lease and maximum lease times, reserve IP addresses by client MAC address and specify boot files and TFTP server IP
- You can display static routes, ARP and Host Name tables and add entries to each (see this OvisLink FAQ)
- Built-in ping and traceroute utilities
- The USB Device Information page shows serial #, speed, USB version, Vendor ID, Product ID, Revision Number and Device Type for attached devices.
Routing Performance
Even though the 9000VPN’s VPN performance isn’t anything to write home about, its normal routing is fine, clocking in between 24 and 26Mbps. No complaints on response times and UDP streaming performance either.
Testing Notes:
• All tests were run with Qcheck TCP and UDP ports 10113 – 10117 set as Virtual Servers
Routing Performance Test Results
| Test Description | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
|---|---|---|---|---|
| Throughput (kbps) | Lost data (%) | |||
| WAN – LAN | 24.6 | 1 (avg) 1 (max) |
500 | 0 |
| LAN – WAN | 26.7 | 1 (avg) 2 (max) |
500 | 0 |
| Firmware Version | 1.01.039 Mon Jun 7 15:14:11 CST 2004 | |||
See details of how we test.
Conclusion
There’s a lot packed into the 9000VPN’s bursting-at-the-seams flash memory, but some features are better implemented than others. The FTP server , Print server and Content Filtering are strong points in my mind, although users may find the 20 keywords for the Filtering to not be sufficient.
The weaker features include the VPN functions, which will be suitable primarily for folks who buy two 9000VPNs to set up a router-to-router link and who don’t plan to push much traffic through the IPsec tunnel. I also think that buyers who don’t realize that the Bandwidth Management features apply to outbound (upload) traffic only, may be disappointed in their purchase.
With its relatively high price and limited availability (at least in the U.S.), the MU-9000VPN and its WMU-9000VPN wireless sibling will be appealing to a relatively limited group of purchasers who “just gotta have” their unique combination of features. For me, however, the quest for the right SOHO router with built-in bandwidth management continues.