Introduction
Updated August 16, 2005
Pretty Good Privacy (PGP) has had quite a history since Phil Zimmermann released the first version in 1991. Government lawsuits, acquisitions, revisions, and finally a massive buyback of assets from erstwhile owner Network Associates in 2002 all befell the little piece of software initially used to help users securely post to Bulletin Board Systems.

But throughout all of this, the encryption itself has remained unbroken – in spite of claims ranging from lonely teenagers breaking it to the US government forcing Zimmermann to implant backdoors into the software. Along with S/MIME, PGP has been given the honor of being one of only two email encryption systems approved for use by the National Institute of Standards and Technology.
And yet, despite all of these accomplishments and praises, many users and organizations still refrain from using PGP or other encryption mechanisms to secure their email.
Why is this? A combination of different factors have deterred both the average Joe Internet and not-so-average Bob Company from buying into the world of email encryption. Chief among these is complexity. Encryption is seen as just too difficult to set up, for a home user and especially for the workplace. And terms such as “public key”, “private key”, and “digital signature” are viewed as concepts best left to the experts.
PGP Corporation – the company that owns and distributes PGP – has taken this to heart and crafted a solution to help companies both big and small encrypt everyday email, without having to go through the hassle of generating public and private keys or even consciously clicking an ‘encrypt’ button before sending a message. The solution is PGP Universal, which is a set of encryption tools that help an organization’s users encrypt everything from email, to instant messages, or even entire hard drives, without having to invest in multiple products.
This article is the first of two reviewing PGP Universal, and will serve to set the scene and introduce the reader to both the product and PGP in general. The second article will deal with PGP Universal’s technical details, and examine how the product functions in the business environment.
Let’s start with a brief look at how far PGP has come since those early days of BBSes, cypherpunks, and the government lawsuits that love them.
Pretty Good History
Version 1.0 of PGP was written in 1991 by Philip Zimmermann. The politically-conscious Zimmermann wanted to devise a solution to allow users to post to the early Bulletin Board Systems and store files without being snooped on. To this end, he created the cross between public-key and symmetric key encryption known as of Pretty Good Privacy that remains publicly unbroken to this day.
PGP works like this: Alice wants to send an encrypted message to Bob. Alice locates Bob’s public key (one half of Bob’s key pair, publicly available for all to see and download) through a keyserver, Bob’s website, or any other method, and uses it to encrypt her message. The message is then sent using normal delivery methods to Bob, who uses his private key (the other half of Bob’s key pair, only visible and usable by him) to decrypt the message. Since no one but Bob knows his private key, no one but Bob can decrypt the message, and it is thus safe from prying eyes at all steps of the delivery process.
This method of keeping messages safe from electronic voyeurs did not escape the attention of the United States Government, and in 1993 a criminal investigation was undertaken into Zimmermann and PGP due to cryptography-related export regulations. Under US export laws, ciphers longer than 40 bits were considered munitions and thus illegal to export, and a three-year legal battle ensued between Zimmermann and his legal team – many of whom worked free of charge on the case – and the US government. This ended in victory for Zimmermann’s team in February of 1996 after the government dropped all charges.
In the wake of this victory, Zimmermann founded PGP, Inc. to market his encryption solutions. The company was quickly bought in 1997 by Network Associates International (NAI), the makers of the McAfee Anti-Virus family of software, and a number of new features were added to PGP. Four years later, in 2001, NAI ceased the development of PGP and put the company’s assets up for sale. A group of investors – including the current management team – soon purchased these assets, and thus was formed the PGP Corporation.
Since it achieved its independence from NAI, PGP Corp. has busied itself with the task of improving PGP and integrating it into a variety of security solutions for both the home and business user. This brings us back to the current day, with PGP Universal 2.0 – PGP Corp.’s integrated solution to allow organizations to satisfy their user’s security and encryption demands from the network level.
About PGP Universal
PGP Universal is a standalone server product that can be installed on any x86 computer. Due to potential hardware incompatibilities, PGP Corp. does not provide precise hardware specifications, though they do provide a list of supported machines.
PGP Corp. also recommends that systems running PGP Universal be relatively similar to the systems running the organization’s email server, so as to to keep up with the mail demands of users.
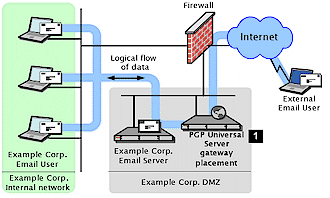
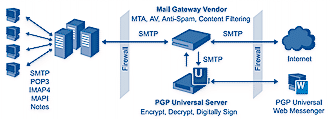
Figure 1: PGP Universal gateway set up in front of mail server
The product uses Fedora Core 2 running the Linux 2.6 kernel as its basis, and is set up to run at the border of an organization’s network, either logically in front of (Figure 1 ) or behind (Figure 2) a mail server.
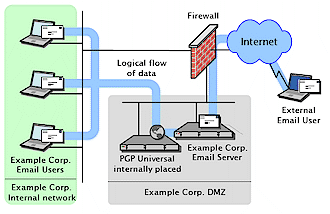
Figure 2: PGP Universal internal set up behind mail server
According to the product specifications, PGP Universal supports Service Pack 1 of Microsoft Exchange Server 2003, Service Pack 3 of Microsoft Exchange Server 2000, Lotus Domino Server 6.5 and Domino Server 5.0.11, and Stalker CommuniGate 4.2. However, our tests showed that any mail server could be used with the product, so long as it implements the product-supported protocols of SMTP, POP, IMAP, MAPI, or Lotus Notes.
PGP Universal is currently being deployed on networks with anywhere from 20 users to nearly 100,000 users, and has the ability to be clustered with other Universal servers to provide for even more users. It is not without competition in the encryption market, however, as business-level encryption has become a hot item in the wake of privacy laws like HIPAA and the Sarbanes-Oxley Act.
Voltage Security and Tumbleweed Communications both provide server-based email encryption solutions, while PostX provides encrypted delivery for bank statements, invoices, and other sensitive business material. But these products either cover only a few of the pieces of the security puzzle that PGP Universal covers, or rely on unproven, proprietary encryption techniques that have not been scrutinized by the security community.
How it Works
PGP Universal works like this: Alice wants to send an email containing sensitive business information to Bob. Alice works for Company A, which runs PGP Universal, while Bob works for Company B, which does not run PGP Universal. Alice sends an email to Bob, which is routed through the PGP Universal server on Company A’s network.
The server sees that Alice is sending an email to a user from Company B, a company that people from Company A have done business with in the past, and proceeds to locate Bob’s public key to encrypt the email with on a public keyserver that the server knows about. The server then encrypts the outgoing email with Bob’s public key, and Bob decrypts the message with his private key upon receipt.
Figure 3: PGP Universal in action
(Click image for more detail)
The product even allows users without PGP keys to send and receive mail. Continuing with the previous example, if Bob wants to receive encrypted mail from Alice, but does not have a PGP key or other encryption mechanism at his disposal, Alice can send him a message with Universal’s WebMessenger. This informs Bob that a message is waiting for him on the WebMessenger server (securing the exchange with SSL) and allows him to register a username and password to receive the message and send future messages to Alice or anyone else.
As an added measure of security, Alice can create a passphrase or code to make sure that Bob is who he says he is when signing up for the WebMessenger service. This is given to Bob independent of email – over the phone, in person, written in invisible ink on a slip of paper inside of a briefcase that is handcuffed to an operative sent to Bob’s workplace via submarine, etc.
PGP Universal relies mainly on the OpenPGP standard of encryption (outlined in RFC 2440 and 3156). But it also has built-in functionality for the other encryption standard recognized by the National Institute of Standards and Technology – Secure Multipurpose Internet Mail Extensions, or S/MIME.
S/MIME is similar to PGP in that it makes use of the public key / private key system of encryption. However, it is an incompatible standard – so someone using a PGP key cannot communicate with someone who has an S/MIME key. PGP Universal includes the capacity to automatically generate S/MIME keys and X.509 certificates for users, so that organizations using Universal are not automatically excluded from communicating with organizations that only use S/MIME as their encryption standard.
Product Line
What makes PGP Universal unique is its all-inclusive nature. At its core, PGP Universal is an email encryption server that allows employees of an organization to have their email automatically encrypted without having any knowledge of how PGP and public-key encryption works. But the software goes beyond this, allowing the Universal server to interact with clients running PGP Desktop (a standalone desktop-level encryption program for individual users), and even run automatic virus scans on incoming mail.
There are three different PGP Universal products that have different feature sets (Figure 4), allowing an organization to choose the security that best fits its needs.
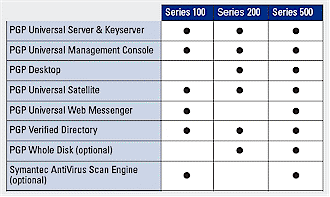
Figure 4: Product and Feature matrix
Updated August 16, 2005
Series 100 is the basic PGP Universal package, including the server software for Universal itself. It also includes PGP Universal WebMessenger and Satellite, which are used to communicate with users that do not have any PGP product or other encryption solution available. Series 100 also has an option for licensing Symantec’s AntiVirus Scan Engine to scan incoming and outgoing messages for worms and viruses. Pricing starts at $59 per license, with a 25 license minimum purchase for $1475. Quantity discounts are available with, for example, a one year subscription for 100 clients coming in at $4800.
Series 200 includes the PGP Desktop program, and performs all key generation and management from the desktop level instead of from the server itself. PGP Desktop is a client-side program that allows for even more security capabilities. It allows individual users to encrypt email themselves, which is useful for employees in the field on laptops connecting from unsecured wireless access points or Internet cafes. It also allows individuals to encrypt their entire hard drive (or portions of it), and even encrypt AOL Instant Messenger conversations provided the user on the other end is also running PGP Desktop. Pricing starts at $110 per desktop, with a 25 license minimum purchase for $2750 and a one year subscription for 100 clients coming in at $9000.
At the top of the line is Series 500, which combines the features of both Series 100 and 200. This series is meant for organizations that want the capacity to encrypt every aspect of their business, from email to hard drives to instant messages. Since it contains all of Universal’s features, Series 500 is what I used to put the product through its paces. Pricing starts at $2950 for a 25 user, 1-year license ($9600 for 100 clients).
Setup
Due to its server-oriented nature, testing PGP Universal required a unique test set up. I configured two networks: Arpstorm and Foobar. The Arpstorm network was the network that the product was deployed on, while the Foobar network was the external network that messages would be sent to.
Both networks ran Windows Server 2003 Enterprise Edition, which managed their mail and DNS servers, and hosts on both networks ran Windows XP Professional. In order to eliminate any unforeseen variables such as hardware or network difficulties, and since my goal was a functional review of the product and not any performance benchmarking, I set up both of these networks on a machine running VMWare Workstation.
It is important to note that the above Windows clients and servers were chosen because they are supported by PGP Corp. While my experience with the product leads me to believe that Open Source applications would be able to manage an installation of PGP Universal, with the exception of the Thunderbird mail client, there are no Open Source applications that are supported at this time.
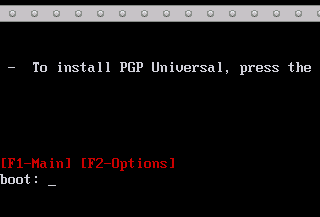
Figure 5: Initial setup screen for PGP Universal
(Click image for more detail)
As previously noted, PGP Universal is installed on a dedicated host on an organization’s network. The product can be set up in one of two configurations – gateway placement, or internal placement.
In gateway placement, the host sits logically outside of the mail server (and outside the network’s firewall) and encrypts outbound mail after it is sent from the server.
In internal placement, the host sits logically behind a company firewall and between clients and the mail server. In this configuration, Universal encrypts outbound email before it hits the server, where it sits queued in encrypted form before being sent on its way.
Since MX records and DNS names must be updated differently for each of these configurations, the placement decision must be made before starting installation. Something else that needs to be considered when choosing the installation configuration is the protocols that will be used for email. POP or IMAP may only be utilized with the internal server placement, while SMTP may be used with both placement methods.
Figure 6: Linux packages being unpacked onto the system
(Click image for more detail.)
I chose an internal placement and started to set up the server. Booting the dedicated (virtual) machine – since Universal will wipe the hard drive of whatever you put it on – with install CD in place briefly displayed a loading screen followed by a prompt where we could enter any options for installation. Since I was ok with the default network IP addressing used (Universal assigns itself an IP of 192.168.1.100), I didn’t need to use the customnet argument and simply hit Enter.
The program then pretty much installed itself, unpacking and installing all of the necessary Linux packages such as Java and Tomcat, and then restarted.
Figure 7: The PGP Universal setup page welcomes you in seven different languages
When the dust had cleared from the restart, I was able to log into the PGP Universal Server via a web browser from another machine on the network and configure it. This was an easy enough process, and after entering information about my test network such as DNS and mail servers and assigning the Universal box its own name, the system restarted once more. (Note that I had to to update our DNS server’s host records to allow other machines on the network to access it via name.)
In the next and final part of this review I’ll dive deeper into PGP Universal to see if it lives up to its claim of effectively implementing automatic email encryption for an entire organization.