Introduction

| At a Glance | |
|---|---|
| Product | Sonicwall SSL-VPN 200 Appliance (SSL-VPN 200) |
| Summary | Entry level SSL VPN gateway supporting SSL proxy and IPsec tunnel connections |
| Pros | • Works with both IE and Firefox • No per-use licensing • Vista support for VPN client |
| Cons | • Unequal local > remote and remote > local throughput • Support plan ($) required for firmware updates after 90 days |
We previously looked at rolling your own SSL VPN and Netgear’s SSL-312 as affordable ways for SOHO / SMB users to explore the SSL alternative to IPsec VPN gateways. This time, I’ll look at Sonicwall’s entry-level SSL-VPN 200 appliance.
The 200 is Sonicwall’s entry-level SSL gateway with ten recommended maximum concurrent users. Also available are the 2000 and 4000 models that have recommended maximum concurrent users of 50 and 200 users respectively. In a departure from Sonicwall’s usual per-user license model, all the SSL VPN’s come with unrestricted users licenses. So if you want to try loading them beyond the recommended maximums you can have at it. But as you’ll see later, the recommendations are probably reasonable, if not a bit optimistic.
The 200 provides secure remote access via two main methods. Proxies are provided for HTTP, HTTPS, FTP, SSH (V1 or V2), Telnet, RDP (via ActiveX control or Java applet), VNC and Windows File Sharing (Windows SMB/CIFS). The proxies provide remote access to these services via IE or Firefox running on any OS. For other TCP/IP-based applications, you use what Sonicwall calls NetExtender. I’ll let Sonicwall explain:
NetExtender is a SonicWALL SSL-VPN client for Windows that allows users to run TCP/IP-based applications securely on the company’s network. NetExtender is downloaded transparently and uses a Point-to-Point Protocol (PPP) adapter instance to negotiate ActiveX controls.
NetExtender first queries whether the ActiveX component is present, and if not, allows the user todownload and install it. When installed, NetExtender allows users to tunnel to the remote network and virtually join the remote network in order to mount drives, upload and download files, and access resources in the same way as if they were on the local network.
The 200’s silver and blue metal enclosure is designed for utility and has mounting screw slots on the bottom and plenty of vent holes on each side. The indicators and connectors are shown in Figure 1 below.

Figure 1: SSL-VPN 200 Front and Rear Panels
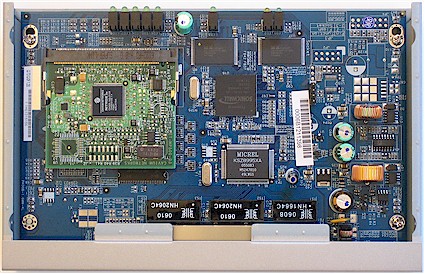
Figure 2 shows that the 200 is based on a proprietary Sonicwall CPU joined with a Cavium XL Security Acceleration Board (PDF link). The Cavium spec sheet rates the board at 200 Mbps "IPsec performance" and 1750 (1024 bit exp) SSL TPS (Transactions Per Second). While this sounds impressive, we’ll see later that actual performance doesn’t have numbers that large.
The 200’s Status page reports 128 MB of RAM and 16 MB of Flash, which is the same as contained in Netgear’s SSL-312. All five 10/100 Ethernet ports are handled by the Micrel KSZ8995XA switch chip. Note the absence of heatsinks, which didn’t seem to be needed for cool operation.
Figure 2: Inside the VPN 200
Installation / Configuration
The 200 is basically set up in a "one armed" connection (Figure 3). Unlike a router that has separate WAN and LAN ports, traffic flows in and out of the single X0 port, which you just plug into your LAN’s switch. The four X1 ports are there mainly because the same chassis is used for Sonicwall’s TZ150 firewall. But it also possible to establish a separate subnet behind the 200 using these ports and put clients there that will only be able to be accessed via the appliance.
The 200 comes set to 192.168.200.1, so you’ll need to change the IP address of the computer that you use to access its built-in secure (HTTPS) web admin interface.
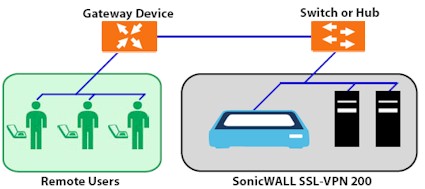
Figure 3: VPN 200 connection
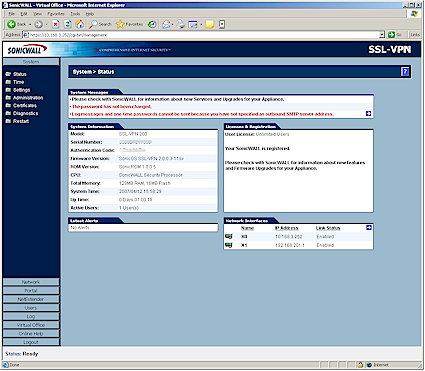
Upon login, you’ll be presented with the System > Status screen (Figure 4). A browse through the other System menus will find options for NTP server (Time), saving and restoring system settings and upgrading firmware (Settings), failed login attempt lockout (Administration), generating and managing security certificates (Certificates), various Diagnostics and Restarting the 200.
Figure 4: System Status screen
One of your first stops will be the Network > Interfaces screen, where you’ll change the IP address of the X0 port to match your LAN, as I did in Figure 5.
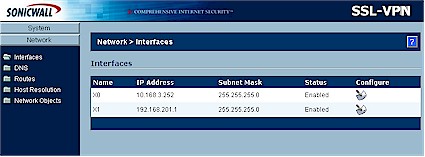
Figure 5: Network Interfaces screen
I also stopped at the DNS and Routes screens to enter my LAN’s DNS server and Gateway IP addresses. I didn’t bother defining any Hosts in Host Resolution, so it held only the default “sslvpn” for the 200 itself. The Network Objects screen lets you define combinations of services and IP addresses that are handy to have when defining access policies later. Since my needs were simple I made no entries there.
Now we’re ready to add a user to the 200 via the Users > Local Users page (Figure 6). There is a wealth of options available for controlling what users can see and do via the 200 and also how and from where they can log in. Options include idle timeout, ability to add, edit and delete "Bookmarks" (explained shortly) and permit/deny policies based on user, IP address, IP range and more.
Note that the same configuration options are available for Groups and both User and Groups have Global Policies, too. Note that policies can be edited and deleted, but not temporarily disabled.
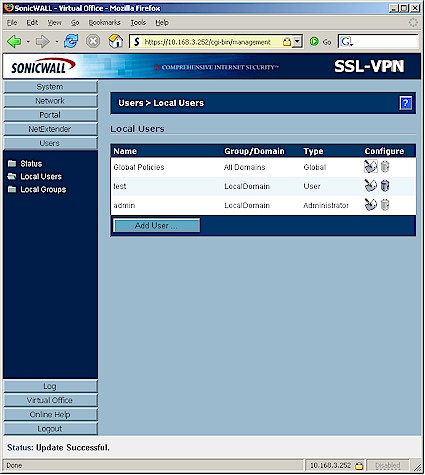
Figure 6: Users > Local Users screen
![]() Check out the slideshow for more 200 configuration options
Check out the slideshow for more 200 configuration options
Once you’ve finished defining a user, you’re ready to see the 200 in action. But in order to access the 200 from outside your LAN, you’ll need to forward port 443 (HTTPS) through your router to the 200’s IP address—as you would for any server that you access from the Internet. If you want to have automatic redirection from HTTP to HTTPs, then also forward port 80 (HTTP). Contrary to the description in the Administrator’s Guide, neither of these ports can be changed for the 200.
In Use – Proxy Mode
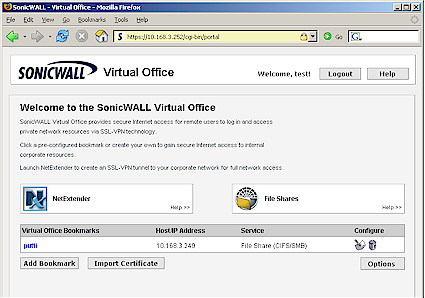
Log out of the 200 (doing so will close your browser window, which I found annoying) and log back in using the user account. If all goes well, you are presented with the "Virtual Office" landing page (Figure 7). Virtual Office is a portal that users access in order to create and access bookmarks, file shares and NetExtender sessions.
Figure 7: Virtual Office home page
Both the login and Virtual Office landing pages can be customized with an uploaded logo and text of your choice. You can also control what appears on the Virtual Office landing page including the File Share proxy, bookmarks and even the Net Extender link.
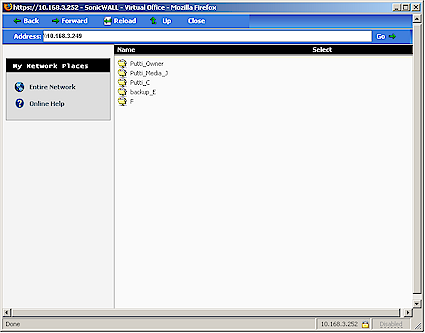
Most proxy services are accessed via "Bookmarks" that have been created by admins or that users can create themselves (or not, depending on the Policies that have been created). The "putti" bookmark seen in Figure 7 consists of the IP address of one of my LAN’s systems and the File Share (SMB/CIFS) service proxy. Clicking it opens the screen shown in Figure 8 that shows all of the shares on that machine.
Figure 8: Virtual Office ‘putti’ bookmark
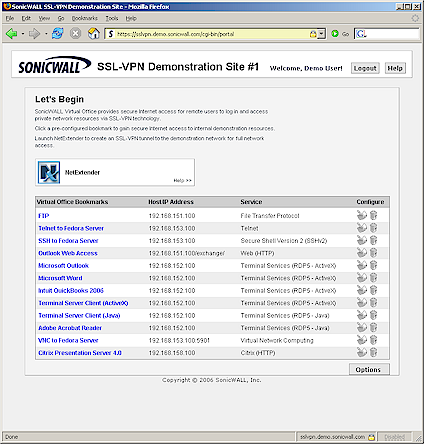
If you want to see a better example of what you can do with bookmarks, check out Sonicwall’s SSL-VPN demo site (Figure 9). Be patient because some of the bookmarks take some time to load. I had better luck with the demo site using IE than with Firefox, which seemed to hang on many bookmarks. Also note that the Citrix option isn’t available on the 200.
Figure 9: Demo site
Net Extender and Other Features
If your secure remote access needs aren’t met by the proxies, and you’re running Windows 2000 Professional, XP Home or Professional or 2000 / 2003 Server, you can use the NetExtender feature. Sonicwall says that NetExtender will also work with Vista if you use IE 7 and are logged in as Administrator for a 200 that has the current 2.0.X firmware. When 2.1 firmware is released for the 200 sometime in 2Q 07, then even non-Administrators will be able to install NetExtender. More Vista info is available in these FAQ.
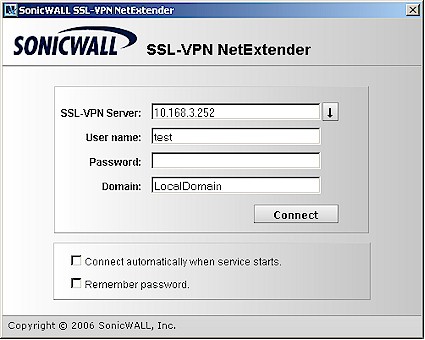
Figure 10: NetExtender client
Once you connect to the 200 via NetExtender, your client is assigned IP address and route information from values that you enter in the 200’s NetExtender section. So, for all intents and purposes, the remote client is securely connected to the 200’s LAN, just as it would be via a normal IPsec or PPTP tunnel. Note that you can see the active NetExtender sessions on the 200’s NetExtender > Status screen but you can’t manually terminate sessions.
Since Sonicwall highlighted the 200’s "one time password" feature in the reviewer material they sent, I thought I’d check it out. I was stopped in my tracks however, when I went to enter my SMTP server info. I was disappointed that I had to enter the server’s IP address instead of its name. But the real show-stopper was the lack of any authentication feature. Since most email servers require some sort of authentication these days, this is a major omission. I also would have liked to see a "test email" feature like other products have.
The only other major feature that I haven’t covered are the Log and Online Help features. Log info is pretty much limited to user log ins and outs and activations of the built-in proxies and NetExtender. New entries are added at the top of the log page and you can send the log to a syslog server or email the logs (assuming you can get around the SMTP server authentication issue). I put an example of the log screen in the slideshow. The Online Help is context-sensitive and comprehensive, but requires connection to help.sonicwall.com.
Performance and Closing Thoughts
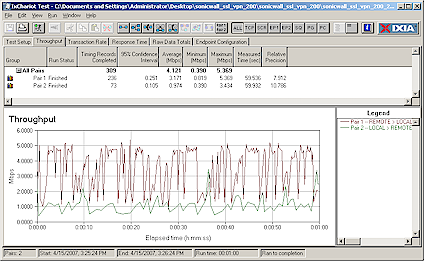
I used IxChariot to measure the 200’s throughput. Since IxChariot wasn’t handled by any of the 200’s proxies, I had to make the measurements using NetExtender. I tested in the recommended "one arm" mode with the 200’s x0 port plugged into my LAN switch and one client connected via NetExtender.
Since the NetExtender client gets a different IP address assigned than its normal LAN address, I was able to ensure that I was measuring performance through the 200 and not just directly from client to client. Figure 11 shows the results for simultaneous Local > Remote and Remote > Local tests.
Figure 11: SSL-VPN 200 throughput – NetExtender
I tested using the IxChariot throughput.scr script using TCP/IP and its default 100,000 Byte file size and throughput appears to vary quite a bit with a total average of 4.1 Mbps measured. I also ran each direction separately and found similar results. I thought it odd that there was such a large difference between throughput in each direction. So I also ran a test with the "Local" client plugged into one of the 200’s x1 ports, but obtained similar results and next checked with Sonicwall. Although they didn’t have IxChariot at their disposal, the FTP method they used also found a noticeable difference in throughput for the two directions.
Note that the Netgear SSL312 had better throughput around 6 Mbps. But more significantly, the SSL312 had just about equal throughput in both directions.
Summing up, I had expected to find that the 200 and Netgear SSL312 were more similar than different. And while both products do support proxy and VPN-like secure remote connections, each has different strengths and weaknesses. Sonicwall has an edge in that its NetExtender client can be downloaded via Mozilla, Firefox, Opera and Safari in addition to IE, where the Netgear download works with IE only. The Sonicwall is also in better shape than Netgear with respect to Vista, if that’s on your must-have checklist.
But the 200’s unbalanced throughput, higher cost and requirement to purchase support after the first 90 days could tip the scales back in Netgear’s (or other vendors’) favor for buyers who aren’t yet ready for Vista and who don’t mind using IE to launch a VPN tunnel when needed. ("Dynamic 8×5" support will run you $105 for 1 year.) Neither product has it all, so your selection of either will depend on which compromises you’re willing to make.
![]() Check out the slideshow
Check out the slideshow