Introduction

| At a glance | |
|---|---|
| Product | Zyxel Gigabit VPN Firewall Gateway (VFG6005) [Website] |
| Summary | Inexpensive, Gigabit port PPTP / IPsec router with 3G failover |
| Pros | • 3G WAN support • High routing and VPN bandwidth • Up and downlink bandwidth control |
| Cons | • No IPv6 • No L2TP • Poor documentation |
Typical Price: $0 Buy From Amazon
The ZyXEL VFG6005 was introduced by ZyXEL last year. But since I recently reviewed TRENDnet’s TW100-BRV214—another inexpensive 4 port VPN router—I figured the VFG6005 would make for a good alternative review. As we’ll see, however, the VFG has some key advantages.
Take a look at the diagram from ZyXEL in Figure 1, showing key features and use models. As with the TW100, the VFG is a wired-only router. ZyXEL also offers the VFG6005N, which adds an 802.11bgn access point.
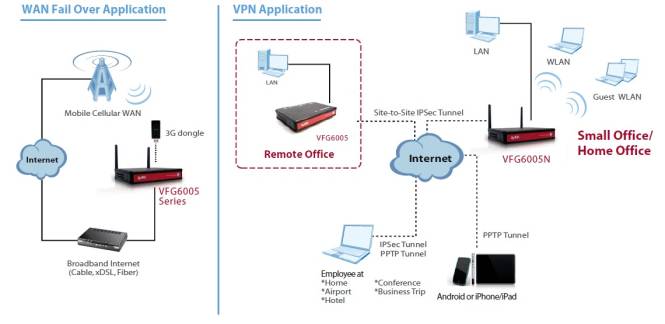
Figure 1: VFG6005 use overview
Two key differences between the VFG and TW100 are immediately apparent.. First, the VFG has Gigabit LAN (4) and WAN (1) ports vs. the TW100’s 10/100 ports. (Note, the LAN ports on the VFG are limited to an MTU size of 1500 bytes, thus jumbo frames are not supported.) Second, the VFG has a USB port that supports 3G wireless dongles, making it a dual WAN router.
With that said to whet your appetite, let’s first cover the basics. The VFG’s black plastic case measures 6.2" X 4.2" X by 1". It has a red front panel with indicator lights on the top, near the front edge of the device. You can see the indicator lights in the picture at the beginning of this article. The front is displayed below.
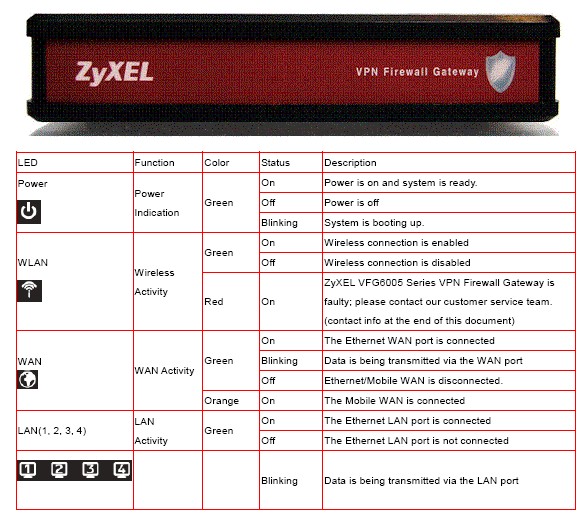
Figure 2: Front view
The WAN, USB WWAN and LAN ports on the back, as well as the power connector. There is no on/off button or switch on the VFG. The VFG has an external power brick at the end of the power cable, is passively cooled and runs silent.
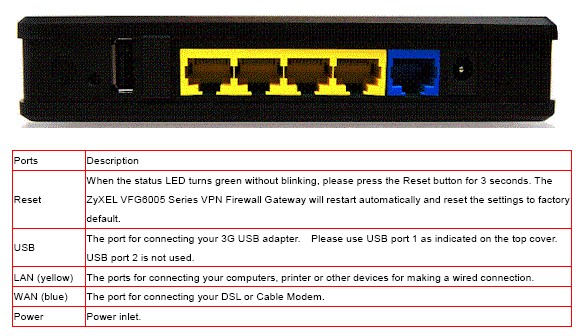
Figure 3: Rear view
Inside
Under the covers is the mainboard, housing a MIPS24K CPU clocked at 384 MHz with 16 MB of flash, 64 MB of SDRAM and an Atheros AR8316 Gigabit switch. As Figure 4 shows, both CPU and switch have ceramic heat spreaders attached.
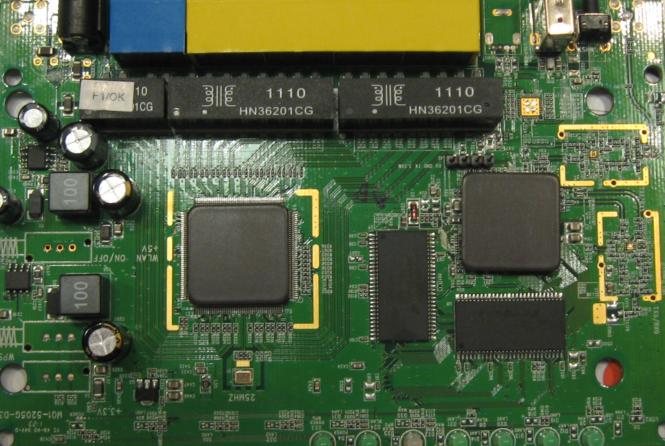
Figure 4: VFG6005 board
Configuration
I found the menus straightforward and responsive. The menu bar (Figure 5) is available on the top right in all configuration screens, making it easy to navigate from one option to another. On the other hand, the manual is a bit sparse, lacking clear explanation and examples on configuration options.
![]()
Figure 5: VFG6005 menu bar
Each menu item has two to eight submenus. I’ve laid out the configuration options in Figure 6.
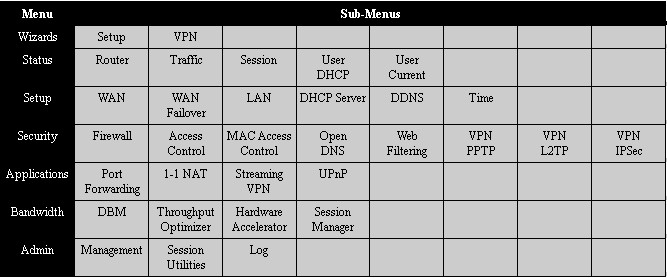
Figure 6: VFG6005 admin menu summary
Missing from the configuration options is support for IPv6. As I mentioned in my review of the TW100, we in the U.S. may not need IPv6 in our small networks today, but it will likely be needed in the next couple of years.
There are two wizards, one for basic setup, the other for VPN setup. The basic setup wizard simplifies configuration of the admin password, WAN and WWAN, and time settings. With that said, let’s dive into the VFG, starting with VPN capability.
VPN Features
The VFG is a surprisingly capable VPN router, considering its low price. It supports IPsec and PPTP site-to-site and remote access (client-to-gateway) tunnels. ZyXEL provides a simple wizard for configuring each. All the typical IPsec encryption and authentication options are supported, as shown in the configuration screen below.
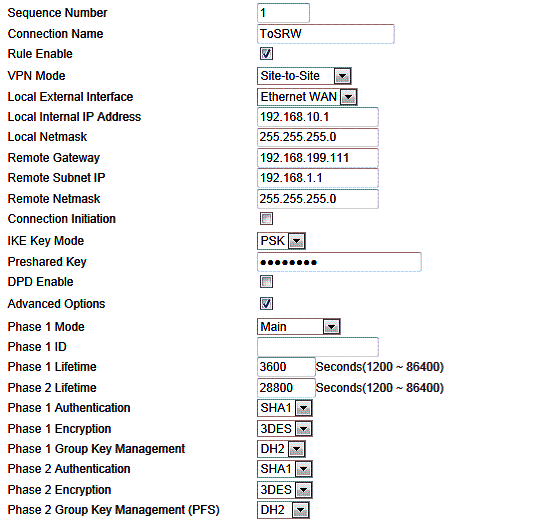
Figure 7: VFG6005 IPsec settings
To test IPsec, I set up an IPsec tunnel using 3DES and SHA-1 between the VFG and my standard site-to-site test partner, a NETGEAR SRX5308 high performance VPN router. I used the wizard on both the ZyXEL and NETGEAR to configure the tunnel options, then manually tweaked the ZyXEL options to enable 3DES encryption. Once configured, the tunnel established right away. I also found I was able to simultaneously establish a PPTP tunnel and an IPsec tunnel. Figure 8 shows the established IPsec connection to the NETGEAR.
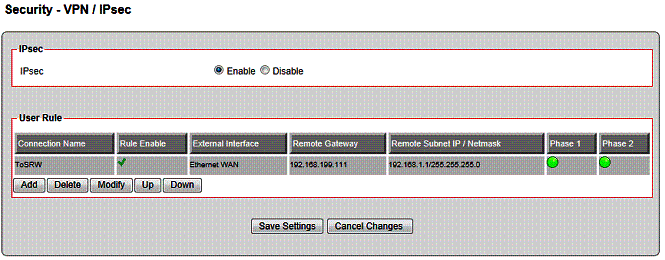
Figure 8: IPsec tunnel status
Remote client access to the VFG LAN can be achieved through an IPsec or PPTP tunnel, but ZyXEL doesn’t provide IPsec client software. So users without IPsec software are left with the PPTP option. I find this solution reasonable, as PPTP is included in Windows 7.
I tested remote client VPN access to the VFG with PPTP using a Window 7 64 bit PC. The VFG also provides a wizard for the PPTP configuration, but I chose to set it up manually, which was quite simple. Configuring the VFG as a server for PPTP requires enabling the server, and adding a user name and password. I also had to disable the VFG’s Hardware Accelerator (more on this later.) Figure 9 shows my PPTP server configuration.
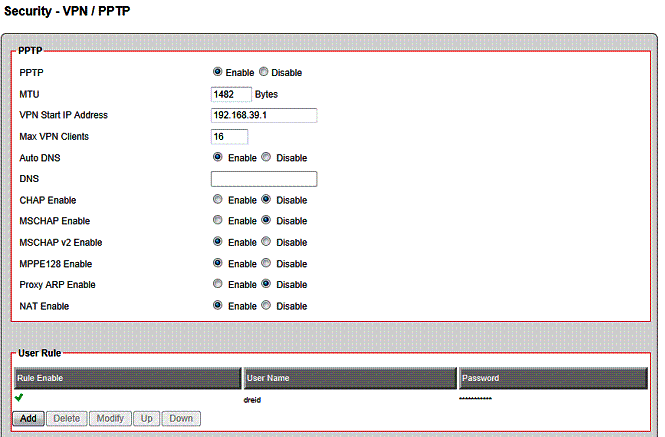
Figure 9: PPTP settings
As discussed in previous VPN router reviews, configuring Windows’ PPTP client is point and click. Here’s the quick setup if you need it:
- From the Network and Sharing Center in the Control Panel, select Set up a new connection or network,
- Select Connect to a workplace
- Select No, create a new connection
- Select Use my Internet connection
- Enter the IP or dynamic DNS name you’ve assigned to the router
- Select Don’t connect now, just set it up so I can connect later
- At the next screen, enter the user name and password you created on the VFG.
These steps will create the new VPN connection on your PC. Once created, right-click on that connection and select Properties. In the security tab, select PPTP. Save your changes, right-click the connection again and click connect.
With the settings above and an enabled PPTP interface on my PC, I had no problems remotely connecting to the VFG. In fact, I tested PPTP connections to the VFG while on a recent business trip and was able to successfully connect to the VFG from an airport as well as from a hotel in Europe.
Note, the VFG doesn’t provide a status screen or indicator that there is an active PPTP connection, other than a log message saying PPTP Server: client [192.168.199.110] local [192.168.39.1] connected [OK].
If you look back at Figure 1, you’ll see ZyXEL shows an Android or iPhone/iPad connecting to the VFG via a PPTP tunnel. I recently picked up an iPad2 and I didn’t even realize it supported VPNs. So I had to try this out. I found it easier to configure PPTP on the iPad than on my Windows PC!
From the iPad’s General-Network menu, I added a configuration in the VPN menu under the PPTP tab by keying in the VFG’s WAN IP and my PPTP user name and password. When I turned the VPN connection on, I was connected to the VFG within seconds via a PPTP tunnel from my iPad and able to browse the VFG’s configuration menus. Notice the VPN icon on the top left of Figure 10, showing an active PPTP VPN connection.
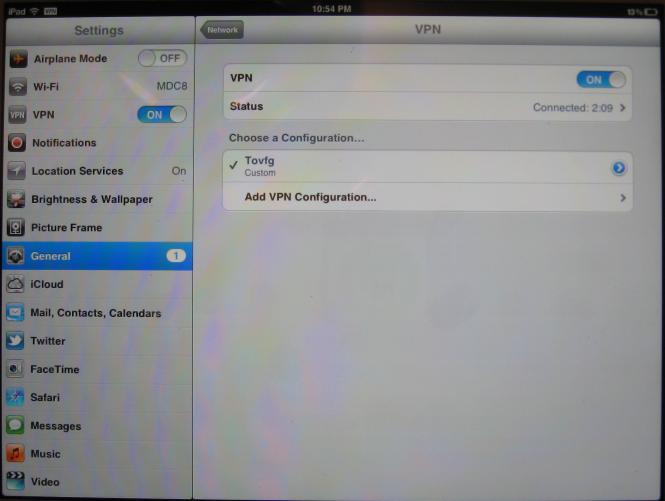
Figure 10: iPad connected via PPTP
The VFG has a menu option for L2TP tunnels, but I’m not sure it is meant to be there. L2TP is not listed in the VFG’s product specs, on the product packaging, or in the product data sheet, leading me to believe L2TP may be an unsupported menu option.
I tested L2TP on the VFG anyway and couldn’t get it to work, regardless of the configuration options. I did a packet capture on my PC and on the VFG’s WAN connection while attempting to set up an L2TP connection and could see the VFG was not even responding to L2TP setup requests, indicating the problem wasn’t a setting mismatch.
VPN Performance
I tested the VFG’s VPN client-to-gateway performance with iperf using default TCP settings, with a TCP window size of 8 KB and no other options. I ran iperf on two PCs running 64-bit Windows 7 with their software firewalls disabled. (Running a simple iperf throughput test between two PCs uses the command iperf -s on one PC and iperf -c (ip) on the other PC.)
Note, I typically measure IPsec throughput using 3DES encryption. But in this case, I measured both 3DES and AES on the VFG, as ZyXEL lists the VFG as capable of 11 Mbps IPsec throughput with AES encryption. As you can see in Tables 1 and 2, clearly the VFG is optimized for AES encryption over 3DES encryption.
The tables show my VPN throughput measurements over the three tunnel types on the VFG. It also shows my VPN throughput measurements from four other wired VPN routers I’ve reviewed, the TrendNet TW100, Draytek 2920, NETGEAR FVS318G and the Cisco RV042v3.
| Test Description | Throughput – (Mbps) | ||||
|---|---|---|---|---|---|
| VGF6005 | TRENDnet TW100-BRV214 |
Draytek 2920 |
NETGEAR FVS318G |
Cisco RV042v3 |
|
| IPsec (AES) | 12.1 | – | – | – | – |
| IPsec (3DES) | 5.9 | 3.32 | 17.8 | 2.72 | 37.1 |
| PPTP | 10.8 | 8.95 | 19.9 | – | 10.8 |
Table 1: VPN Performance comparison – client to gateway
Note that IPsec throughput was not affected by the VFG’s hardware accelerator. PPTP throughput was measured with the VFG’s hardware accelerator disabled, which is required to enable PPTP. I’ll touch on the hardware accelerator more in the features section of this review.
| Test Description | Throughput – (Mbps) | ||||
|---|---|---|---|---|---|
| VGF6005 | TRENDnet TW100-BRV214 |
Draytek 2920 |
NETGEAR FVS318G |
Cisco RV042v3 |
|
| IPsec (AES) | 10.9 | – | – | – | – |
| IPsec (3DES) | 5.6 | 2.85 | 17.8 | 2.72 | 47.5 |
| PPTP | 6.5 | 7.61 | 19.9 | – | 9.7 |
Table 2: VPN Performance comparison – gateway to client
As you can see from the results, the VFG’s AES client-to-gateway throughput of 12.1 Mbps and gateway-to-client throughput of 10.9 Mbps validates ZyXEL’s rating of 11 Mbps. This is impressive! Most of the time, manufacturer claims don’t match the iperf test results.
Clearly, AES throughput on the VFG is faster than its 3DES throughput of 5.9 Mbps / 5.6 Mbps. Further, AES and 3DES throughput on the VFG are faster than the 3DES throughput numbers of both the TW100 (3.32 Mbps / 2.85 Mbps) and the FVS318G (2.72 Mbps / 2.72 Mbps ). But the VFG is no match for the 3DES throughput of the Draytek 2920 (17.8 Mbps both directions) or the Cisco RV042v3 (37.1 Mbps client-to-gateway and 47.5 Mbps gateway-to-client).
The VFG’s PPTP throughput of 10.8 / 6.54 Mbps is pretty close to the TW100’s 8.95 / 7.61 Mbps and Cisco’s 10.8 / 9.7 Mbps, but well below the Draytek’s 19.9 Mbps. The FVS318G does not support PPTP.
To wrap up, ZyXEL lists the VFG as capable of supporting up to 32 IPsec and 16 PPTP tunnels. While I didn’t try this many, I had no problem running both flavors simultaneously. Further, I like the fact that AES is faster on the VFG than 3DES because AES is more secure. As long as the other endpoint or your client software supports AES, using AES for IPsec encryption is a good thing.
Routing Features
The VFG has three groups of routing features. First, traffic can be filtered based on rules or MAC address. Second, web traffic can be controlled via Open DNS and keyword filtering. Third, the VFG supports standard firewall functionality such as a DMZ, Port Forwarding, and permitting specific traffic types such as RTSP, MMS, H.323, IPsec, PPTP and UPnP. Within this third group, the VFG also has menu options to enable/disable the firewall, as well as enable/disable DoS and ICMP protection.
Firewall rules on the VFG are constructed based on exit interface (WAN or WWAN), source and destination IP range, layer 4 protocol (TCP or UDP), and destination port range. Traffic matching a rule can be either allowed or denied. Below is a simple rule I created to block all web traffic.
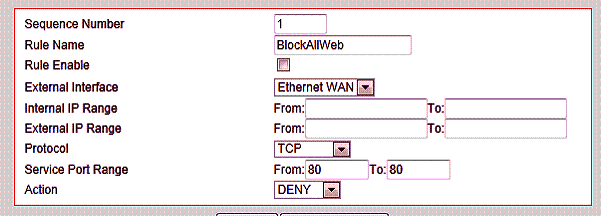
Figure 11: Block all traffic firewall rule
The rule worked, I could not surf the web with it enabled. However, the VFG doesn’t present an error message telling users why their traffic is being blocked. It would be better if a simple message was presented on blocked traffic, such as “This traffic is blocked, please contact your network administrator.”
Integrating Open DNS into the VFG is quite useful. Open DNS filters web traffic by preventing resolution of web sites that are objectionable to your network. Open DNS offers both basic free accounts and subscription-based home and business level accounts, depending on the features you need. I tested the VFG with a free account by simply adding my Open DNS user name and password into the VFG. Once enabled and saved, I was presented with the message below, indicating Open DNS was enabled.
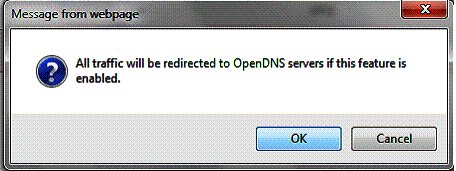
Figure 12: OpenDNS enabled
I like Open DNS as a web filtering service. It enables routers to perform effective web filtering without negatively impacting throughput. With Open DNS enabled on the VFG, I was presented with the web page in Figure 13 when trying to browse to xxx.com.
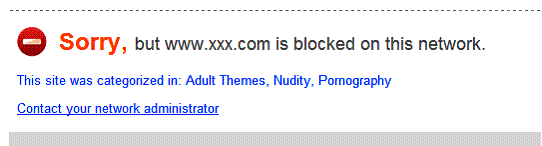
Figure 13: OpenDNS block message
Below the block message shown above, there were a few advertisements, which is how Open DNS is able to offer free web filtering. Nevertheless, seeing a few ads is a small price to pay for the value that Open DNS delivers.
To augment the VFG’s web filtering, keyword filtering can also be applied if you wish to block specific content or websites. Below, I created a keyword filter to block access to facebook.com. This rule worked in the same manner as my simple rule to block all web traffic, but again did not present an error message telling the user why their desired web page was blocked.
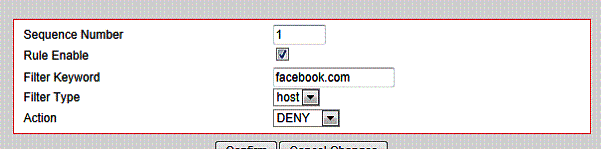
Figure 14: Keyword filter
Overall, the VFG’s firewall is functional and easy to use. Support for Open DNS is a nice touch. Other than that, the VFG’s firewall is pretty standard.
The VFG offers some interesting features that help it stand out from other VPN firewall routers. First, it supports 3G WWAN adapters via a USB 2.0 port. Second, the VFG has multiple options for enhancing or limiting bandwidth utilization.
The VFG doesn’t have the kind of 3G WWAN support you’d find in a Cradlepoint router. But it does support adapters from major providers of North American 3G WWAN services. Figure 15 shows a list of supported 3G adapters from ZyXEL’s product page.
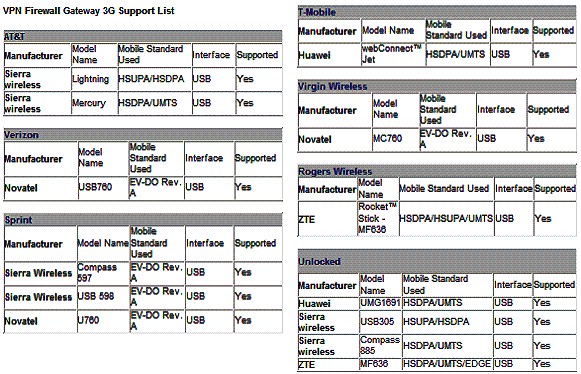
Figure 15: Supported 3G modems
In my experience, the last thing a busy network can tolerate is having its Internet connection go down. 3G WWAN connections provide a high degree of Internet redundancy due to their independence from physical wires. Thus, even the wires going to your house or building are cut, the 3G WWAN service will still be available.
Failover can be enabled from the WAN to WWAN interface so the 3G connection will only be used in the event of your primary Internet connection going down. Further, rules for the firewall, Open DNS, DMZ, Port Forwarding, and 1-1 NAT can all be configured differently for the WAN and WWAN interfaces. Note that only failover is supported for WWAN; bandwidth aggregation and bonding is not.
A second interesting feature of the VFG is its multiple bandwidth management options. The VFG offers Dynamic Bandwidth Management (DBM), a Throughput Optimizer, Hardware Accelerator and a Session Manager.
DBM configurations can be applied dynamically or statically. Dynamically, bandwidth utilization can be controlled on both the WAN and WWAN interfaces. I measured my Internet service (using speedtest.net) at 12 Mbps download and.65 Mbps upload, and then created a DBM rule on the WAN interface to limit my speed to 10 Mbps download and.384 Mbps upload. After enabling this new rule, I measured my Internet service at 9.94 Mbps download and.37 Mbps upload, closely matching my rule and validating bandwidth functionality on the VFG.
Static bandwidth utilization rules can be applied to specific hosts on your network, preventing a host or end user from consuming too much bandwidth or slowing the network. Below is an example of a rule to limit bandwidth use for a host at 192.168.10.20 to 3 Mbps download and.3 Mbps upload. Note that service port range can also be specified.
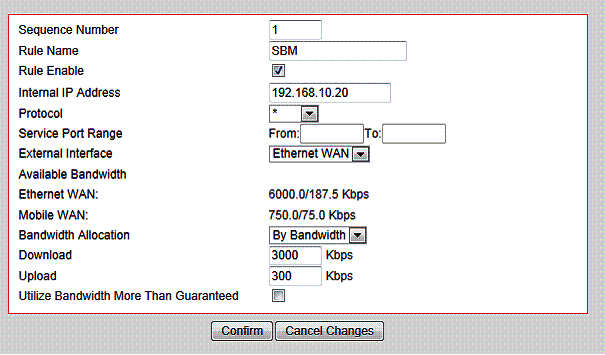
Figure 16: Bandwidth control
With the above static rule applied, I ran another speed test and got the results in Figure 17, validating the accuracy of the VFG’s static bandwidth controls.

Figure 17: Speed test result with bandwidth control
The Throughput Optimizer on the VFG enables prioritizing TCP, ICMP, DNS, SSH, and Telnet traffic, allowing any of these traffic types priority over other traffic on your network. Missing is an option to prioritize UDP traffic for VoIP.
The Hardware Accelerator is an interesting feature on the VFG. When enabled, it increases WAN throughput significantly, which I’ll cover at the end of this review. The downside is the Hardware Accelerator must be disabled to use keyword filtering, DBM, or PPTP. This is disappointing. It is nice to have the higher performance with the Accelerator enabled, but the tradeoff of disabling PPTP takes away one of the router’s key features.
The VFG has a Session Manager feature, with options for fast (recommended), regular, and slow. ZyXEL indicates this feature can improve the VFG’s P2P performance by recycling connections faster. ZyXEL rates the VFG as capable of up to 60,000 NAT sessions.
Finally, here are a few other things to note about the VFG’s routing features:
- Port forwarding supports separate external and internal ports
- 1-to-1 NAT (allows mapping an external Public IP address to an internal LAN IP address; useful if you have multiple WAN IP addresses from your ISP)
- HTTPs administration is not supported
- Remote admin can be enabled and port set, but can’t limit access by IP
- DHCP server – can set least time, but can’t reserve addresses
- MAC address ACL is supported
- Dynamic DNS for DynDNS.org, TZO.com, ZoneEdit.com
- Schedules are not supported for any firewall features
- Triggered port forwarding is not supported
Routing Performance
Routing performance for the VFG using our standard test method and 2.07(VFE.2)B0_20110804 firmware is summarized in Table 3. Downlink speed of 636 Mbps is pretty impressive, but uplink at 150 Mbps is significantly lower. The VFG maxed out our simultaneous connection test at 34,925 sessions, however.
| Test Description | VFG6005 Throughput – (Mbps) |
|---|---|
| WAN – LAN | 636 |
| LAN – WAN | 150 |
| Total Simultaneous | 304 |
| Maximum Simultaneous Connections | 34,925 (test limit) |
| Firmware Version | 2.07(VFE.2)B0_20110804 |
Table 3: VFG6005 Routing throughput summary
The composite IxChariot plot in Figure 18 of the three routing tests below shows a good amount of WAN-LAN throughput variation. Although it’s hard to see in the composite plot, WAN-LAN variation still remains high in the simultaneous WAN-LAN / LAN-WAN test.
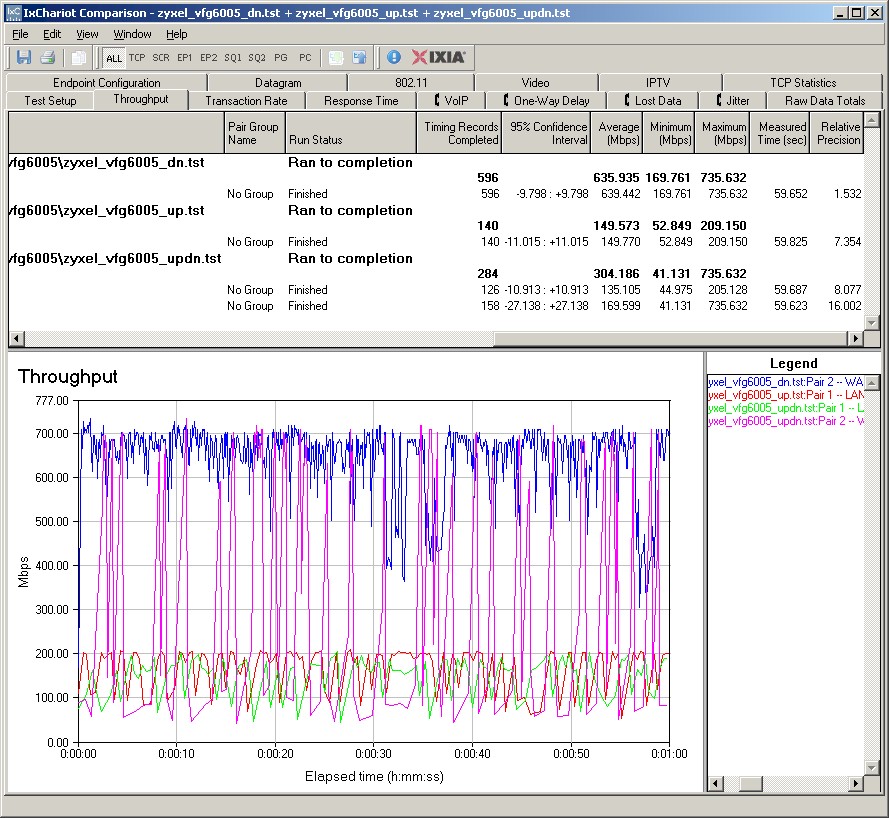
Figure 18: VFG6005 routing throughput
Note that, as is our standard practice, the tests were run with all defaults except to put the LAN-side IxChariot client in DMZ. So this means that the Hardware Accelerator was enabled for these tests and could be causing the high variation.
To investigate this theory, I ran my own set of throughput tests using iperf. I got 206 Mbps WAN-LAN and 159 Mbps LAN-WAN with the VFG’s hardware accelerator enabled. The WAN-LAN result isn’t as high as the IxChariot 636 Mbps result. But that’s probably because iperf’s measurement resolution isn’t as high as IxChariot’s and the averaging effect brought down the result. The LAN-WAN number is more closely matched, because its variation is nowhere near as high as downlink.
Switching off hardware acceleration yielded 133 Mbps WAN-LAN and 135 Mbps LAN-WAN. These more equal throughput numbers seem to indicate that high WAN-LAN throughput variation is caused by the hardware accelerator.
Use the Router Charts to run more comparisons.
Closing Thoughts
ZyXEL positions the VFG against the Dlink DIR-130 and the NETGEAR FVS318. We haven’t reviewed the DIR-130, so I’ve excluded it from Table 4. But I did include the other four routers compared in the VPN section of this review.
| Product | # IPsec tunnels | GRE | SSL | PPTP | L2TP |
|---|---|---|---|---|---|
| ZyXEL VFG6005 | 32 | N | N | Y | N |
| TRENDnet TW100-BRV214 | 80 | Y | N | Y | Y |
| NETGEAR FVS318G | 5 | N | N | N | N |
| Cisco RV042v3 | 50 | N | N | Y | Y |
| Draytek 2920 | 40 | N | N | Y | Y |
Table 4: VPN feature comparison
The ZyXEL falls toward the low end for the number of supported IPsec tunnels, but 32 is a respectable number nontheless.
Table 5 provides overall comparisons, including throughput and maximum connections taken from the Router Charts.
| Product | WAN ports | LAN ports | Gigabit | WAN-LAN Throughput (Mbps) | LAN-WAN Throughput (Mbps) | Max Simultaneous Connections | Price |
|---|---|---|---|---|---|---|---|
| ZyXEL VFG6005 | 2* | 4 | Y | 636 | 150 | 34925 | &83 |
| TRENDnet TW100-BRV214 | 1 | 4 | N | 93 | 93 | 34925 | $68 |
| NETGEAR FVS318G | 1 | 8 | Y | 23 | 23 | 200 | $118 |
| Cisco RV042v3 | 2 | 4 | N | 91 | 90 | 34925 | $146 |
| Draytek 2920 | 2* | 4 | Y | 148 | 137 | 34925 | $245 |
Table 5: Router summary comparison
The single asterisk next to the ZyXEL and Draytek’s WAN ports indicate these two routers support 3G WWAN connections via a USB interface, which is not supported by any of the other routers.
ZyXEL rates the VFG at 300 Mbps throughput. Looking at the IxChariot test results would seem to back this up. But they also reveal high downlink throughput variation with hardware acceleration kicked in, which it is by default.
With hardware acceleration enabled or disabled, the VFG stands out when you consider its price/performance. A check of the price links below, as I write this, shows lowest prices in the $80 range. With hardware acceleration enabled, the VFG is the fastest and least expensive VPN router in this group. Even with its hardware acceleration disabled, routing throughput of the VFG is second only to the more expensive Draytek router and more than adequate for the service bandwidths it is likely to be connected to.
In all, I found the VFG6005 stable and easy to use. The IPsec and PPTP VPN options work as advertised and it has Gigabit ports, fast throughput, 3G failover and a nice low price. For these qualities, I rate the VFG6005 a winner!
