Introduction

| At a Glance | |
|---|---|
| Product | Copfilter for IpCop |
| Summary | Open source network traffic filtering and anti-virus add-on for IPCop |
| Pros | • Power compilation of multiple open source tools • Centralized anti-virus and anti-spam filtering • Web based GUI for configuration |
| Cons | • Requires some Linux ability to install and manage • No content filtering |
Network security is a significant issue for virtually all networks, both personal and business. As we increase our use of the Internet and network enabled devices, our private information, communication, and network devices are more and more exposed to uninvited parties.
Larger networks typically have significant investments in network security and filtering tools to protect information and control inbound and outbound communications. Fortunately, there are also solutions for small networks, ranging from software to hardware-based appliances. A few examples of hardware-based appliances include the recently reviewed Zyxel USG100, as well as the SonicWall TZ190W and D-Link DFLCPG310.
All three of these solutions integrate a physical router, firewall, and subscription-based network filtering tools. These three solutions range in price from $110-$735 to purchase the hardware, plus an additional $166-$418 in annual subscription fees.
For the technically adventurous, there are sound and "free" options that can be implemented with older computing hardware and open source software. I say "free" in quotes because although the software may be openly available, an investment in time and effort is required, which also has value.
"Free" options also generally have no warranties or support. So initiative and ingenuity are required to fully leverage and manage their capabilities. In this review, I’m going to cover one of those "free" options, Copfilter, which is an add-on to the open source firewall solution called IPCop.
One of the neat aspects of the IPCop and Copfilter solution is it centralizes traffic filtering and doesn’t require software to be installed on each network client. Indeed, Copfilter could be used instead of software on individual PCs. Although an organization may prefer the enhanced security of both centralized and distributed security solutions, the reduced cost and computing overhead provided by a centralized Copfilter solution is a compelling proposition.
Copfilter filters network traffic such as email, web surfing and downloads, looking for viruses, spam and other exploits. It does not, however, provide web content filtering.
Copfilter includes an anti-virus engine called ClamAV. To scan email for viruses with two anti-virus engines, Copfilter also offers the option of adding the Linux version of F-Prot’s anti-virus software. F-Prot is an anti-virus client similar to the more well-known Norton and McAfee applications. Note that the free version of F-Prot is designed for workstation based filtering, not centralized filtering as we’re doing with Copfilter. To use F-Prot’s server-based version, a subscription is required.
Installation
Copfilter is an add-on to IPCop, so you need IPCop up and running first. IPCop runs on standard PC components and I used a 3.2 GHz P4 CPU with 2 GB of RAM and a pair of Intel gigabit NICs. We reviewed IPCop awhile back and covered hardware, installation and uses, so I’ll just focus on installing Copfilter.
Many open source solutions lack good documentation and require significant technical skill. Installing Copfilter does require some Linux knowledge, but there is a well written 46 page guide (README.pdf) available on Copfilter’s website that I found very useful for installing and evaluating this tool.
The Copfilter guide is relatively user-friendly and doesn’t presume advanced Linux skills. And it has directions for installing and administering Copfilter from both Linux and Windows machines. There are several Linux commands that have to be entered at the command line in IPCop, but each is listed in the guide. I was pleased to find the installation instructions worked as written.
To install Copfilter from a Windows machine, you’ll need an SSH client like Putty and an SCP client like WinSCP on your Windows machine. SSH and SCP are included in many Linux distributions, so I used a Linux workstation behind my IPCop firewall to install and configure Copfilter. I found the installation boils down to 5 steps; each is pretty straightforward.
Step 1: Enable SSH and Web Proxy on IPCop
As with most other small network firewall/routers, IPCop is managed via a web based GUI. IPCop’s web GUI is point and click, so enabling the SSH and Web Proxy features are a matter of clicking check boxes on a web page.
Step 2: Download Copfilter and F-Prot to a PC in IPCop’s "Green" LAN
IPCop calls the network connected to its LAN interface "Green" and the network connected to its WAN interface "Red" as illustrated in Figure 1. Other interfaces can be installed in IPCop, each designated by a different color.
Figure 1: IpCop interfaces
Installing Copfilter is typically done from a PC connected to IPCop’s “Green” or LAN interface. I used the Firefox browser on a Linux workstation connected to the “Green” interface of my IPCop to download both Copfilter (filename = copfilter-0.84beta3a.tgz) and F-Prot (filename = fp-Linux-i686-ws.tar.gz).
Step 3: Copy Copfilter and F-Prot to IPCop
After downloading the files, I copied them from my Linux workstation to my IPCop machine. From a terminal session on my Linux workstation, I typed the commands below.
 Note: 192.168.188.3 is the IP address of the Green interface on my IPCop machine; your IP may be different. SCP stands for secure copy, a protocol for secure transmission of files.
Note: 192.168.188.3 is the IP address of the Green interface on my IPCop machine; your IP may be different. SCP stands for secure copy, a protocol for secure transmission of files.scp -P 222 copfilter-0.84beta3a.tgz [email protected]:/root scp -P 222 fp-Linux-i686-ws.tar.gz [email protected]:/root
Step 4: SSH to IPCop
I used SSH to log in to the command line of my IPCop via 192.168.188.3. SSH (secure shell) is a secure network protocol for command line access from one machine to another. It works just like Telnet, but the traffic sent between the two machines is encrypted, preventing someone from capturing and reading the data transmitted.
Note that you use port 222 instead of the standard port 22 for SSH access to IPCop, as shown below.
ssh -P 222 [email protected]
Step 5: Expand and install Copfilter and F-Prot
It took seconds for each to complete, and once done, the Copfilter menu was created in the IPCop GUI and available for configuration without a reboot, although I rebooted anyway.
cd /root tar xzvf copfilter-0.84beta3a.tgz cd copfilter-0.84beta3a ./install cp /root/fp-Linux-i686-ws.tar.gz /root/copfilter/ cd /root/copfilter./setup_util -f fp-Linux-i686-ws.tar.gz
With installation complete, the IPCop GUI shows an additional tab named Copfilter. This tab has the configuration options for the various traffic filters now incorporated into your IPCop Firewall, shown in Figure 2.
Figure 2: CopFilter tab
Notice in Figure 2 that there are configuration menus for POP3, SMTP, HTTP, FTP, AntiSpam and AntiVirus. You have to go into each of these menus and turn on the options in order for each type of traffic filtering to be enabled. It’s point and click, so it isn’t a big deal, but obviously an important step.
Traffic Filtering
Copfilter is primarily a traffic filtering tool. Traffic types that are filtered include inbound and outbound email, web and file downloads via HTTP and FTP. Traffic is filtered for spam, viruses and various network security risks such as executable files. Lists can be built to block specific traffic sources or locations, as well as allow or block email traffic from specific domains.
A useful feature of Copfilter is that it can be configured to email notifications and reports to an administrator. Specify the email address to send to, plus an SMTP server address and user id/password if authentication is required in the email configuration page, and Copfilter will send email notifications of status and issues.
Email notifications are a useful feature for a small network without the resources to continuously monitor servers and network traffic. For example, I received email from Copfilter with notifications when it successfully updating the anti-virus database.
Email Anti-Spam
POP3 traffic, which is inbound email to PCs on the LAN, is filtered for viruses and spam. To see that Copfilter is doing its job, text messages can be inserted into the email header showing that Copfilter detected and scanned that message, as well as into the email body itself. If IPCop and Copfilter are your first foray into open source network tools, having a message in your emails showing the system is functioning is nice feedback.
Turning on these text messages is done by selecting on from a drop down in the web GUI for the two features shown in Figure 3.
Figure 3: Enabling email alerts and header, body inserts
Adding Copfilter Comments to an email header, as shown in the first line of Figure 3, puts text into the message source information of each email. This text (example below) can be seen in Microsoft Outlook by opening an email and clicking on View-Options, or in Mozilla Thunderbird by opening an email and clicking on View-Message Source.
X-Copfilter: Client is part of local network, skipped Spamassassin
X-Copfilter: Sender is in whitelist, skipped SpamAssassin
X-Filtered-With-Copfilter: Version 0.84beta3a (ProxSMTP 1.6)
Adding a disclaimer to each email, as shown in the second line of Figure 3, is an even more obvious notification that the received email has been scanned. If enabled, all incoming mail will have a line at the end similar to “Scanned with Copfilter Version 0.84beta3a (P3Scan 2.2.1)”, confirming that Copfilter’s anti-virus scanner is on line.
The “X-Copfilter: Sender is in whitelist, skipped SpamAssassin” message header mentioned above points to the spam filtering functionality in Copfilter. Copfilter uses whitelist/blacklist spam filtering for defining acceptable and unacceptable email sources and destinations. Note that email from addresses in Copfilter’s whitelist will not be scanned for spam, but will be scanned for viruses. Email from addresses in the Copfilter’s blacklist will be rejected.
The whitelist / blacklist functionality has both an automatic and manual capability. If a client on the LAN side of IPCop sends an email to a destination email address and then receives a reply, the original destination email address will automatically be added to the whitelist.
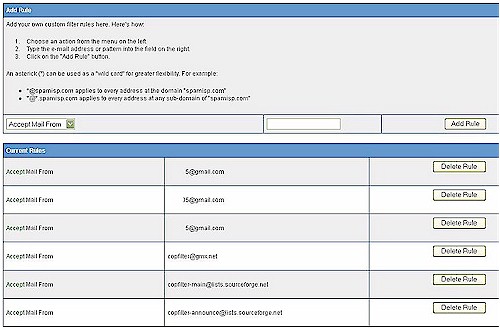
Copfilter’s whitelist / blacklist is a single list. It can be manually updated by clicking on the Whitelist keyword shown in the bottom right of Figure 3 and adding either entire email addresses, or just domain names.
The * wild card can also be used in the whitelist / blacklist for greater flexibility. Selecting Accept or Discard for each email address or domain defines whether the email will be passed (whitelist) or rejected (blacklist), as illustrated in Figure 4 below.
Figure 4: Whitelist / blacklist
Beyond the simple automatic and manual email spam whitelist / blacklist, Copfilter checks email for various conditions defined by the open source anti-spam engine SpamAssassin. SpamAssassin is a Perl program comprised of multiple algorithms and rules performing various header, text and character analyses to detect spam.
SpamAssassin can also be configured to check incoming emails against the Razor and DCC external spam databases, in addition to its own. SpamAssassin can also be enabled to check incoming emails against up to eight different DNS Black Lists (DNSBLs).
Copfilter’s configuration page warns that enabling the Razor, DCC, and DNSBL functionality “improves recognition, decreases performance.” But the nice thing about Copfilter is that you control processing power. Improving processor power on an off-the-shelf router is typically not an option. But since IPCop / Copfilter runs on a PC platform, upgrading the processor and memory is simple.
Messages matching conditions in a SpamAssassin algorithm, one of the external databases, or from an email address found in a DNSBLs can be quarantined or tagged with a message. The default tag of ***SPAM*** is added to the subject line of emails as shown in the email in Figure 5. Most email clients have the ability to construct a rule to look for a specific tag and move tagged emails to a folder or delete them.
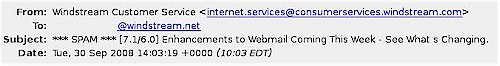
Figure 5: Email with subject line SPAM tag added
Email Anti-Virus
Another key element to incoming mail filtering is virus control. Copfilter leverages the open source ClamAV anti-virus engine along with the open source P3Scan tool to filter POP3 traffic on both port 110 and 995. This is a strength over subscription-based products that filter traffic only on port 110. With the P3Scan tool enabled in the Copfilter-POP3 Filter menu, the ClamAV and F-Prot anti-virus engines will be applied to incoming email.
Copfilter includes a nice test tool to check that the anti-virus functionality is running. Under the Tests & Logs menu, there is a button to Send Test Virus Email. Clicking this button will send an email with an innocuous virus to the address entered in the Copfilter email configuration page. I tried this and received the test email shown in Figure 6.
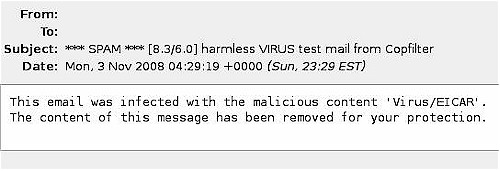
Figure 6: Email virus test result
In addition to filtering inbound email, Copfilter filters outbound email. I enabled the disclaimer option on outgoing email as I did for incoming email, which adds “Scanned with Copfilter Version 0.84beta3a (ProxSMTP 1.6)” to each email sent. I always appreciate seeing messages like this on received email.
Web and Download Filtering
In addition to email filtering, Copfilter has an array of open source tools for filtering web surfing and downloading to further ensure that evil files are kept out of your network. Web filtering is done with the open source tools HAVP and Privoxy. HAVP uses the ClamAV engine to filter traffic to port 80 for virus signatures, while Privoxy filters ads. Another open source tool, frox, filters FTP downloads.
The Copfilter manual provides a link to an innocuous virus test file that when downloaded, should be caught by an anti-virus engine. I downloaded the test file from this page from a PC with a commercial anti-virus product, as well as with Copfilter. Both products caught the virus and stopped the download, with Copfilter providing the message in Figure 7.
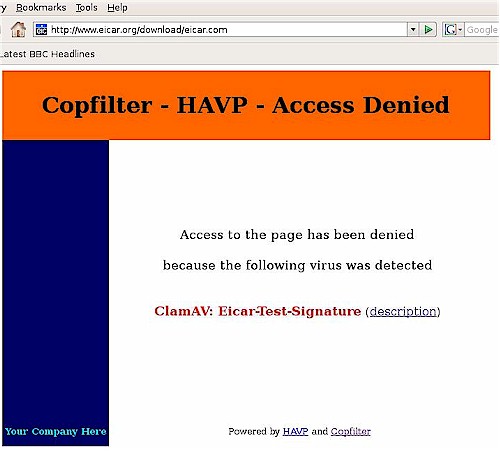
Figure 7: Downloaded virus test result
Privoxy will manage cookies to protect privacy, as well as filter ads, pop ups, and other “Internet junk.” But I found that Privoxy left blank spaces in web pages where there were normally advertisements. Although I’m not a big fan of advertisements, my eyes usually just ignore them. Blocking the advertisements, though, made web pages look odd to me.
Figure 8 shows a screen shot from espn.com. Notice the empty white space at the top indicated by arrows that I added. This empty white space is the work of Privoxy. I have to admit, I guess I prefer the ads, but Copfilter at least provides an alternative.
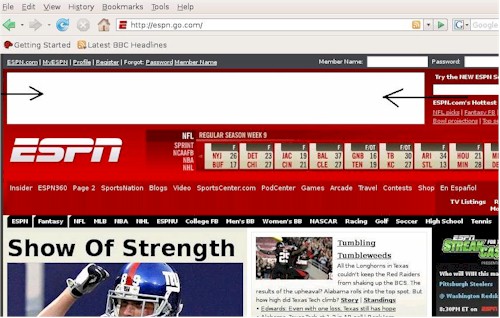
Figure 8: Privoxy ad blocking
Closing Thoughts
The biggest omission from Copfilter is web content filtering. It’s hard to complain about a free tool, especially one with as many features and capabilities as Copfilter, but content filtering would really round out this offering as an alternative for subscription-based traffic filters and expensive UTM (Unified Threat Management) appliances.
The leader in free open source based web content filtering is DansGuardian, which used to be able to be made to work with IPCop. But since DansGuardian’s author became technical director of SmoothWall, that became the DansGuardian primary platform.
Nevertheless, Copfilter is really a nice add-on to IPCop, conveniently bundling quite a few solid open source filtering tools. If you’re already using IPCop as your firewall, installing Copfilter is a no-brainer and each individual component can be enabled as you choose.
The Copfilter web configuration pages carefully credit and link each tool and their source, making it completely clear where the tools come from. Copfilter doesn’t take credit for any of its features, but deserves credit for putting them together. My hat is off to Markus Madlener for bringing all these tools together in a usable package. If you try Copfilter and like it, be sure to send a donation his way!