Introduction
VLANs are a common source of discussion in our forums. How to configure and deploy VLANs in a small network can be challenging. I recently put together an article on how to deploy VLANs on a small network using a smart switch supporting port-based and 802.1Q VLANs. In this article, I’m going to focus on how to use 802.1Q (tagged) VLANs with both a router and switch, as well as how to use 802.1Q VLANs to segment a wireless network.
802.1Q is a VLAN standard, supported by many different device manufacturers. The 802.1Q standard says a VLAN trunk can carry traffic for multiple VLANs. To differentiate traffic, each frame on a VLAN trunk is tagged with a VLAN ID, except frames associated with the trunk’s PVID (native VLAN). Frames associated with the trunk’s PVID are not tagged with a VLAN ID.
VLAN trunks can be connected to 802.1Q capable routers, switches, access points, servers and any other device compliant with the 802.1Q standard. Here are two configuration examples demonstrating VLAN trunking.
Example 1
Let’s say I want to deploy five VLANs in my network. VLAN 1 will be a common wired VLAN, VLAN 2 will be for secure wired devices, VLAN 3 will be for VoIP devices, VLAN 4 will be for general Wi-Fi devices, and VLAN 5 will be for guest Wi-Fi devices.
I’m going to use a Linksys LRT224 router, ZyXEL GS1900-8HP switch, and Cisco WAP321 access point for this example. The first step is to configure the router. In the below screenshot, I’ve added VLANs 2-5 to the LRT224.
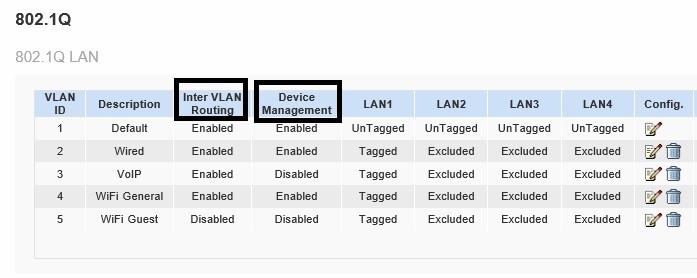
Create VLANs on Linksys Router
I highlighted two options in the above screen. The LRT224 has a couple of useful options for controlling inter-VLAN traffic. I can enable or disable inter-VLAN routing, as well as enable or disable device management from each VLAN. Other routers may not have these specific options, but you can likely implement similar functionality with firewall rules.
A common practice with multiple VLANs is that devices in each VLAN should be given unique IP address ranges, or subnets. The LRT224 automatically creates a DHCP server for each VLAN. VLAN 1 uses the 192.168.1.0/24 subnet, VLAN 2 uses the 192.168.2.0/24 subnet, VLAN 3 uses the 192.168.3.0/24 subnet, shown below, and so on. Using different IP ranges per VLAN allows you to write firewall rules to filter traffic between subnets, as well as create QoS rules to prioritize traffic from a specific subnet. Below is a screenshot of the DHCP server on the LRT224 automatically created when I added VLAN 3.
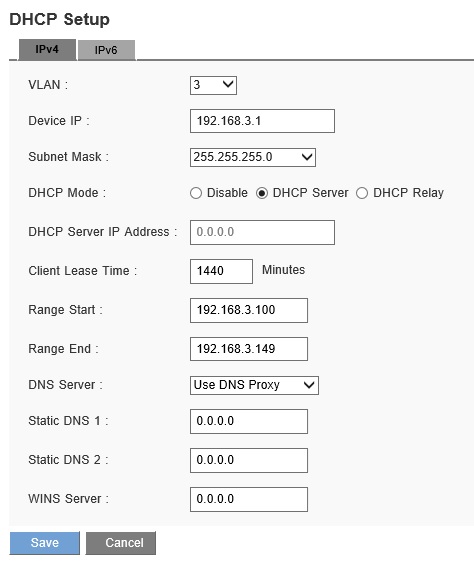
DHCP Server
Once I’ve configured the router, the next step is to configure the ZyXEL GS1900-8HP switch. VLANs 1-5 need to be created, as shown below.
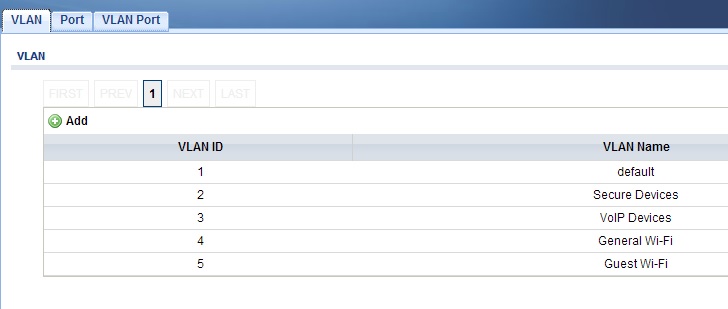
Create VLANs on ZyXEL Switch
Next, I need to configure VLAN membership on the switch. I’ve configured port 1 on the ZyXEL GS1900-8HP as an untagged member of VLAN 1 and as a tagged member of VLANs 2-5. On the GS1900-8HP, this involves clicking the tagged option on VLANs 2-5 for port 1. Below, I’ve set port 1 as a tagged member of VLAN 2, which I repeated for VLANs 3-5.
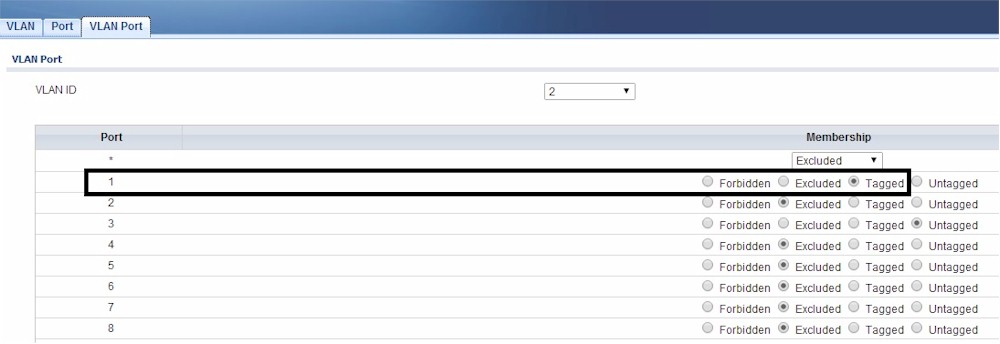
Tagged VLAN
To connect PCs or other end devices to any of the VLANs, configure a port on the GS1900-8HP as an untagged member of the desired VLAN. Note, VLAN 1 is the default port setting on the GS1900-8HP, so I don’t have to change port settings if I want my devices on VLAN 1.
If I plan to connect a VoIP device to VLAN 3, for example, I need to assign that port a PVID of 3 and make that port an untagged member of VLAN 3. As shown below, I’ve given port 4 a PVID of 3.
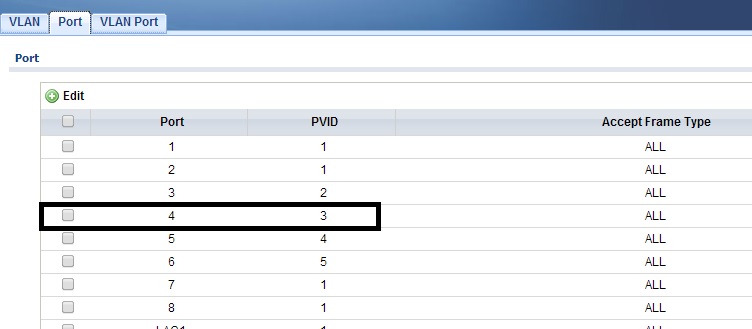
VLAN PVID
In the next image, I’ve made port 4 an untagged member of VLAN 3. My VoIP device connected to port 4 is now on VLAN 3 and gets an IP address in the 192.168.3.0/24 subnet.
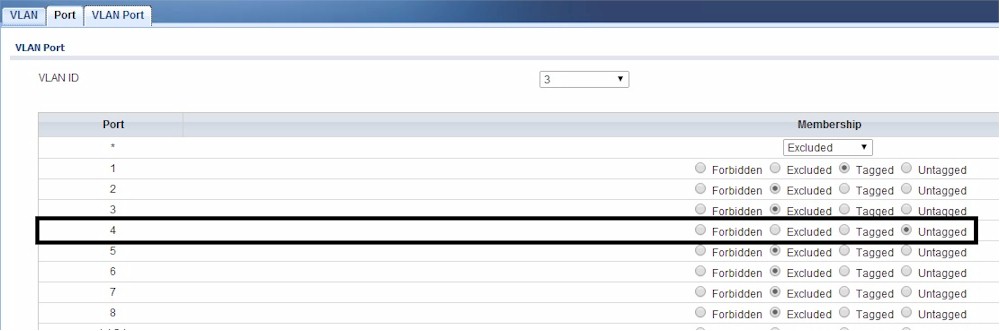
VLAN Assignment
To connect another device that will carry multiple VLANs, I need to create another trunk on the switch. In this case, I’m going to create a trunk on port 8 of the GS1900-8HP that will connect to the Cisco WAP321 access point. Note, the Cisco WAP321 is an 802.1Q aware access point. Many Wi-Fi access points support 802.1Q, but not all.
I’m going to configure port 8 on the GS1900-8HP switch to be an untagged member of VLAN 1 and a tagged member of VLAN 4 and 5. I followed the same steps with port 8 that I used at the beginning with port 1.
Now I’m going to configure the WAP321 access point. The management interface on the WAP321 is already on VLAN 1, so I just need to configure the Wi-Fi networks. I’ll configure two SSIDs and assign them to my desired VLANs. In the below screenshot, I’ve created an SSID called GeneralWi-Fi and assigned it to VLAN 4, and I’ve created an SSID called GuestWi-Fi and assigned it to VLAN 5.
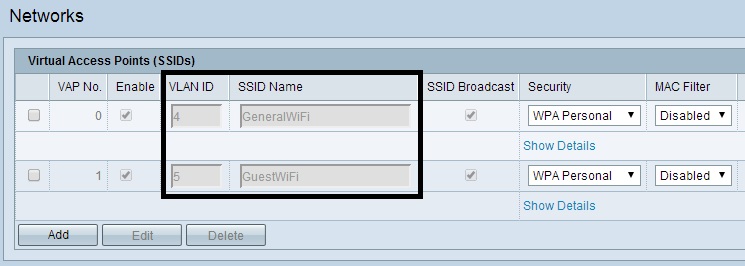
Wi-Fi VLANs
With these configurations in place, Wi-Fi devices that connect to the SSID called GeneralWi-Fi will be on VLAN 4 and get an IP address in the 192.168.4.0/24 subnet. Wi-Fi devices that connect to the SSID called GuestWi-Fi will be on VLAN 5 and get an IP address in the 192.168.5.0/24 subnet.
With these configurations implemented, my LRT224 router, ZyXEL GS1900-8HP switch,and Cisco WAP321 access point are passing VLAN tags. The router is the central device, providing a DHCP server to each VLAN and routing between VLANs.
The LRT224 router is trunked to the GS1900-8HP switch. Configurations applied to the GS1900-8HP switch ports define which ports are in which VLANs.
The WAP321 access point is also trunked to the switch. By mapping SSIDs to VLANs, wireless devices end up in the desired VLAN based on the SSID they connect to.
Configuration options vary by manufacturer, but the concepts remain the same. To use multiple VLANs between multiple devices, they all need to support 802.1Q. Further, a VLAN trunk needs to be configured between devices. The trunk needs to be an untagged member of one VLAN, and tagged member of the remaining VLANs. VLAN tagging configurations should match on each end of the trunk.
Example 2
In this example, I’m going to use a ZyXEL ZyWALL 110 router, Cisco SG200-26 switch, and NETGEAR GS108T switch. I am using two switches in this example to demonstrate an inter-switch 802.1Q trunk.
The ZyWALL 110 has two LAN interfaces, both of which can support multiple VLANs. In this example, I’m configuring the ZyWALL’s LAN2 interface with VLANs 10, 11, and 12, as shown below. This means the LAN2 interface is supporting four VLANs: LAN2’s PVID or native VLAN, plus the three VLANs I created.
I’ve also configured a DHCP server on each VLAN. LAN2’s native VLAN uses the 172.23.2.0/24 subnet. For VLANs 10-12, I created DHCP servers to use the 172.23.10.0/24, 172.23.11.0/24, and 172.23.12.0/24 subnets.
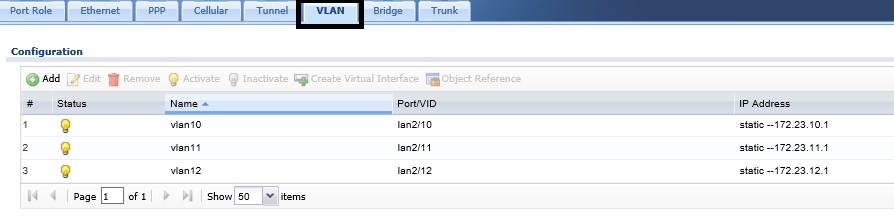
Create VLANs on ZyXEL Router
I’m connecting the ZyWALL’s LAN2 interface to the Cisco SG200-26 switch. I’ve created VLANs 2, 10, 11, and 12 on the SG200-26 and made ports 17 and 18 trunks. Port 17 will be my trunk from the ZyWALL to the Cisco switch, and port 18 will be my trunk from the Cisco switch to the NETGEAR switch. The PVID, or native VLAN, or ports 17 and 18 is VLAN 2. Ports 17 and 18 are untagged members of VLAN 2, have a PVID of VLAN 2, and are tagged members of VLANs 10,11, and 12, shown below.
Any port on the Cisco switch that I configure as an access port and untagged member of VLAN 2, 10, 11, or 12 will place the device connected to that port in the assigned VLAN. As you can see below, I’ve configured port 9 as a member of VLAN 2, port 10 a member of VLAN 10, port 11 a member of VLAN 11 and port 12 a member of VLAN 12. Access ports will have a PVID equal to their VLAN assignment.
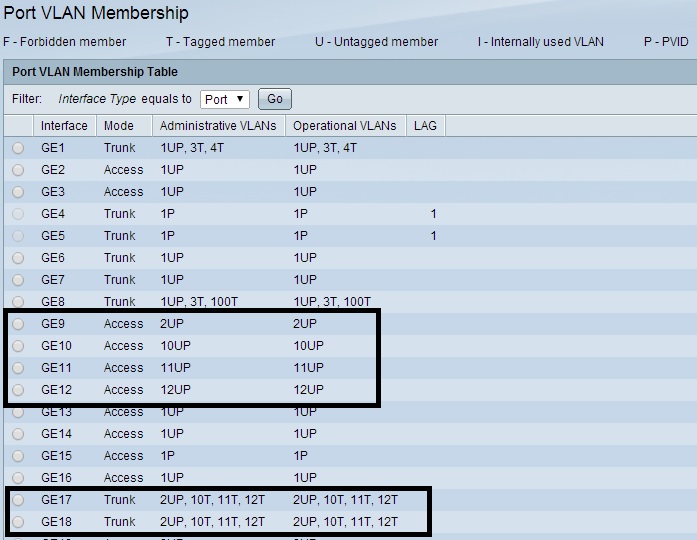
VLANs on Cisco Switch
To extend my VLANs from the Cisco Switch, I’ll connect port 18 on the Cisco switch to a similarly configured port on the NETGEAR GS108T switch. On the NETGEAR, I’ve configured port 4 as my trunk, making port 4 an untagged member of VLAN 2 and a tagged member of VLANs 10-12. My trunk port will have a PVID = 2. I’ve also configured the GS108T’s port 5 as an untagged member of VLAN 2, port 6 as an untagged member of VLAN 10, port 7 as an untagged member of VLAN 11, and port 8 as an untagged member of VLAN 12.
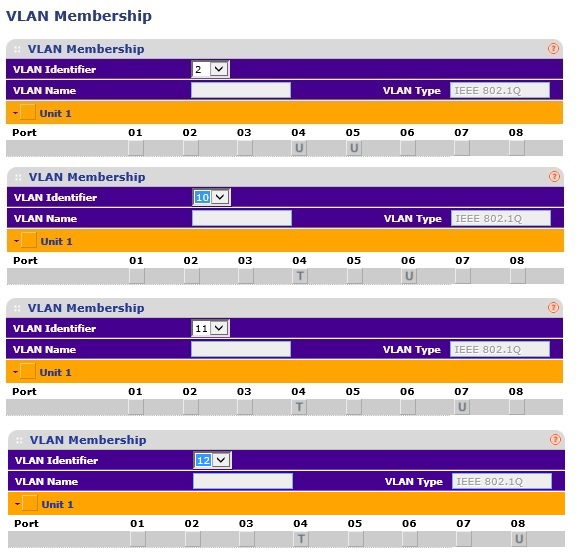
VLAN Tagging on NETGEAR Switch
The image above, which is a combination of four screenshots from the GS108T, shows my tagging configurations on the NETGEAR switch by VLAN and port. The image below shows my PVID assignments by port.
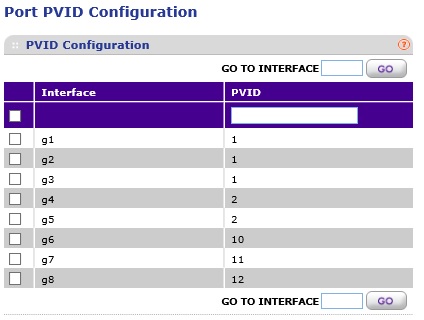
VLAN PVIDs on NETGEAR Switch
With these configurations, port 9 on the Cisco switch and port 5 on the NETGEAR switch are on VLAN 2, port 10 on the Cisco switch and port 6 on the NETGEAR switch are on VLAN 10, port 11 on the Cisco switch and port 7 on the NETGEAR switch are on VLAN 11, and port 12 on the Cisco switch and port 8 on the NETGEAR switch are on VLAN 12. Since I’ve configured DHCP settings to align with VLANs, I can tell which VLAN a PC is on by checking its IP address.
Conclusion
Some devices, such as the Cisco SG200-26 used in this example, allow you to configure port type as access, general, or trunk. Access ports can only be members of one untagged VLAN and should be used for ports connected to PCs. General ports can be members of multiple untagged VLANs. General ports are useful when configuring port-based VLANs on an 802.1Q devices, as discussed in my previous article. Trunk ports can be members of one untagged VLAN and multiple tagged VLANs, and should be used for ports connecting to other 802.1Q VLAN aware devices, such as the devices used in the above examples.
In these two examples, I’ve set up 802.1Q VLAN tagging between a router and a switch, between a switch and an access point and between two switches. The first key is making sure your VLAN assignments match on each end of a trunk. Specifically, the untagged PVID (native VLAN) should match on each end of a trunk and you need to specify the remaining tagged VLANs on each end of the trunk. The second key is making sure your device ports have the correct VLAN assignment and a matching PVID. I found it helps to write down a chart of VLANs, ports, and tagging assignments before you start configuring.
802.1Q VLAN tagging allows segmentation of network traffic by VLAN and by subnet. With this segmentation in place, security and QoS rules can be created on one or more devices to filter traffic between VLANs and/or subnet and to prioritize traffic by VLANs and/or subnet. In a future article, I’ll put together a few examples of filtering and prioritization to do just that.
