
Wake on LAN
Introduction
I posted an article about Wake on LAN (WoL) about seven years ago, which has since generated a good amount of discussion in our forums. It seems this is a technology of interest and why wouldn’t it be? Wake on LAN is a useful tool to turn on a computer over a network. It allows you to leave your computer off for security, power saving or other reasons, yet turn it on without physically pressing the button on the device.
In this follow-on article, I’m going to discuss the details of the magic packet a bit more, as well as discuss how the magic packet may turn on a remote device over both wired and Wi-Fi networks.
WoL
As a brief review of my last article, WoL uses a “magic packet” containing the broadcast MAC address ff:ff:ff:ff:ff:ff followed by sixteen iterations of the target device’s MAC address. A network interface card (NIC) and PC configured to monitor for the magic packet will turn itself on when it sees it.
To understand the magic packet better, it is useful to look at the packet itself. When the packet is sent over a LAN, it is simply sent as a Layer 2 frame, with the sending PC’s MAC address as the source address and either the target PC’s MAC addresss or the broadcast MAC address as the destination address.
You can examine these details by generating a magic packet with Wireshark running on your PC. A free command line utility I’ve successfully tested that generates a magic packet is Matcode’s mc-wol executable, available here. Simply typing mc-wol [target computer MAC address] will send the magic packet over the LAN. For example, to wake up a PC on a LAN with a MAC address of 00:1C:23:01:02:2D, you would type mc-wol 00:1C:23:01:02:2D from the command line (CLI).
You’ll see in Wireshark screenshot below, that the MC-WOL utility created a magic packet with my running PC’s MAC as the source address and the broadcast MAC address as the destination address. You can also see the contents of the packet, with “ff ff ff ff ff ff” followed by sixteen iterations of the target PC’s MAC (00 1c 23 01 02 2d).
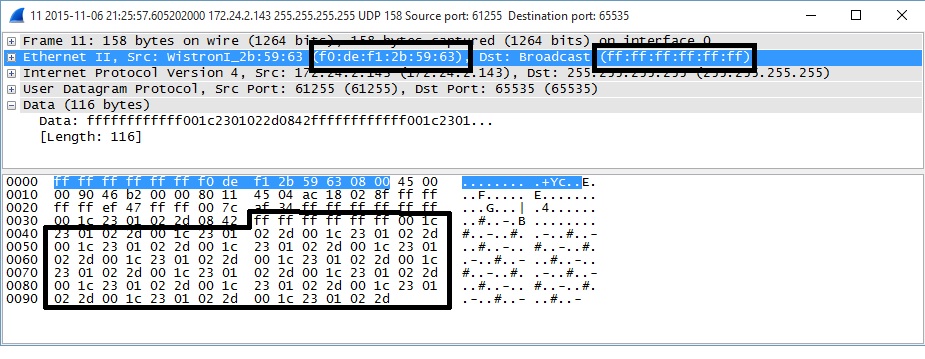
Magic Packet
A key step for this to work is enabling WoL in both your BIOS and Operating System, as shown in the below screenshots taken from a Windows 7 PC. The first screenshot shows the WoL options from my PC’s BIOS. As you can see, I’ve enabled WoL for both my LAN and WLAN interfaces.
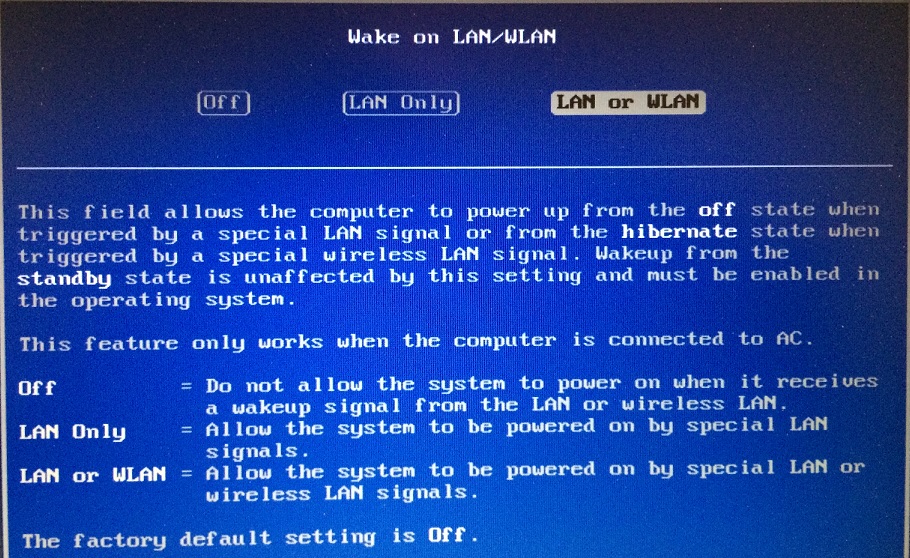
Enable WoL in BIOS
In the screenshot below, I’ve enabled my laptop’s Ethernet port for Wake Up Capabilities in the left window and enabled the wake up functionality in the Ethernet port’s Power Management menu on the right.
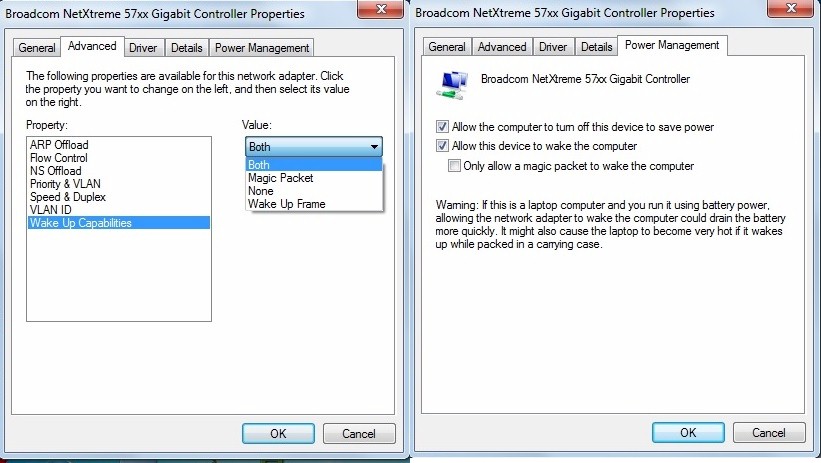
Enable WoL in OS
It’s easy to tell if your PC will support WoL. Before you enable WoL on the target PC, turn the PC off and look at the Ethernet port on the target PC and the Ethernet port on the router/switch it is connected to. If WoL is disabled, there will be no lights on the ports. Once you enable WoL in the BIOS and OS, you should see the link light ON on the Ethernet port on the target PC and the Ethernet port on the router/switch. For WoL to function, the NIC on your PC will stay on in a low power state, monitoring for a magic packet.
Below is an image of the Ethernet port on my laptop. The laptop is completely powered off, but notice the light on the Ethernet port next to the cable. (Note also that a laptop has to be plugged into power for WoL to work. WoL will not work while on battery power.)

Link Light is ON
This is a make or break step, but it doesn’t always work. On one of my PCs, enabling WoL in both the BIOS and OS results in the NIC staying on, even when the PC is turned off. This PC successfully responds to a magic packet. I can consistently power on that PC with a magic packet from anywhere on my LAN.
On another PC, enabling WoL in both the BIOS and OS does not result in the NIC staying on. Subsequently, this PC does not respond to a magic packet. I suspect an issue on my second PC with either the BIOS or device drivers. No matter what the culprit is, the result is the same: no WOL!
Remote WoL
An important point of my previous article was to point out that it is possible to send a magic packet from one network to another. It’s great to be able to turn on a PC remotely on your LAN. But even better if you can do so remotely over the Internet! Sending a magic packet over the Internet is a bit more challenging, though, as now the magic packet has to be encapsulated in a Layer 3 packet and get forwarded properly by your router to the target PC.
It’s simple to encapsulate the magic packet in a Layer 3 packet using the Matcode utility or another utility, such as Solar Winds’ Wake on LAN. The next step is to examine that packet via Wireshark to see what Layer 4 protocol and port are being used. For example, to use the Matcode utility to send the magic packet over the Internet to a target PC with MAC = 00:01:02:55:77:B3, type mc-wol 00:01:02:55:77:B3 /a [IP address]. The IP address you’d use is your router’s WAN IP address.
If my router’s WAN IP address is 72.22.33.44, I’d enter mc-wol 00:01:02:55:77:B3 /a 72.22.33.44. Examining the packet in Wireshark shows me that Matcode uses UDP as the Layer 4 protocol with a target port = 65535.
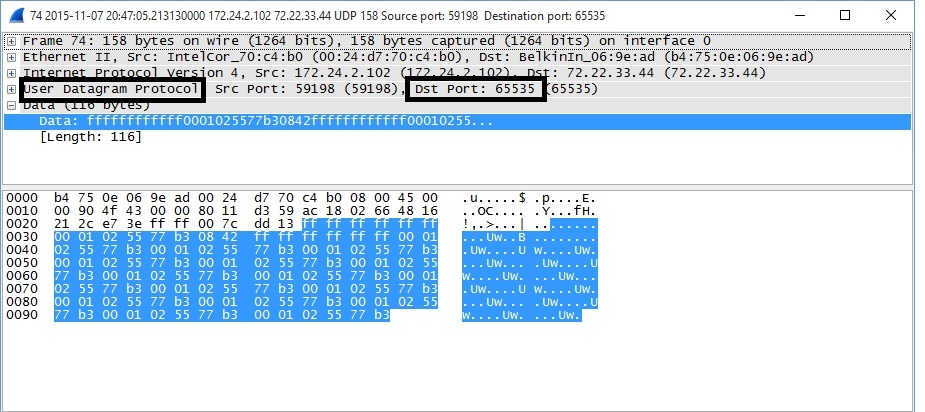
Matcode WoL Utility Layer 4 Protocol and Port
Examining the Solarwinds utility with Wireshark shows this utility also uses UDP as the Layer 4 protocol with a target port = 7. In the below example, the target PC MAC = 00:1C:23:01:02:2D and destination WAN IP = 10.10.10.100.
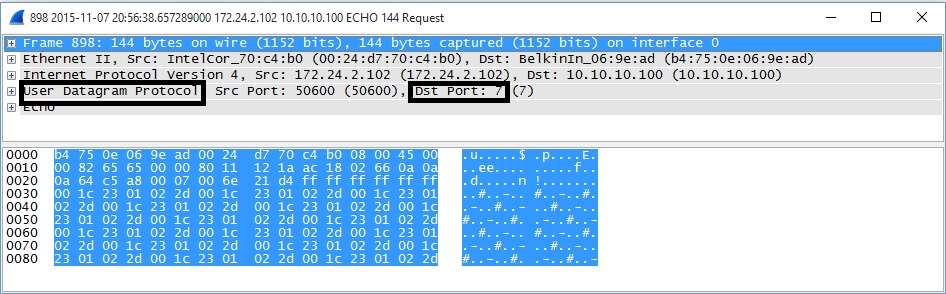
Solarwinds WoL Utility Layer 4 Protocol and Port
With this knowledge of the Matcode (and Solarwinds) software, I could set up a port forwarding rule in my router to send all UDP packets destined for port 65535 (or port 7 if I’m using Solarwinds) to my target PC.
In my experience, this can be hit or miss. The UDP packet can get dropped over the Internet, which is out of your control, or your router may not properly de-encapsulate the Layer 3 packet and correctly forward the Layer 2 magic packet it to the target PC’s MAC or broadcast MAC. Sometimes putting your target PC in the router’s DMZ can work, with the risk that you’re reducing your router’s firewall protection for the target PC.
Instead of trying to send a magic packet to your router and relying on your router to forward it properly to the target PC, there are several other solutions. First, you can use a router that has WoL technology built in. For example, routers running DDWRT, Tomato, or PfSense firmware have a built in WoL client. If you’re using a router with WoL built-in, all you do is remotely access the router and use the router’s WoL client to send a magic packet over the LAN.
Two, a VPN tunnel is another possible means to forward a magic packet over the Internet. In this case, you’d use the target PC’s IP address as the IP instead of your router’s WAN IP. I recommend you assign a static IP on your LAN to the target PC.
If my target PC with MAC = 00:01:02:55:77:B3 has a static IP on my LAN of 192.168.1.111, I’d use the command mc-wol 00:01:02:55:77:B3 /a 192.168.1.111 from my remote PC that is connected to the VPN. Once the magic packet is sent over the VPN tunnel, your VPN router then must decrypt and de-encapsulate the magic packet and then send it to the target PC’s MAC or broadcast MAC.
WoWLAN
Wake on Wireless LAN may also work on computers with the right motherboard and Wi-Fi chipset. For example, laptops powered by the Intel Centrino Process Technology (or newer) support Wake on Wireless LAN (WoWLAN). Intel posted an interesting brief on WoWLAN here. According to Intel, WoWLAN requires the target Windows system to be in sleep state, not hibernate or off.
For WoWLAN to function, the Wi-Fi adapter has to be in a lower power state and examining signals from the associated Wi-Fi network, scanning for the presence of the magic packet. Similar to Wake on LAN, essentially the Wi-Fi NIC has to be in an on state for WoWLAN.
The steps to enable WoWLAN are basically the same as with WoL; enable it on the Wi-Fi NIC and in the BIOS. With WoWLAN already enabled in the BIOS, shown previously, I just had to enable WoWLAN on the Wi-Fi adapter in Windows. In the screenshot below, I’ve enabled the wake up functionality in the Wi-Fi adapter’s Power Management menu.
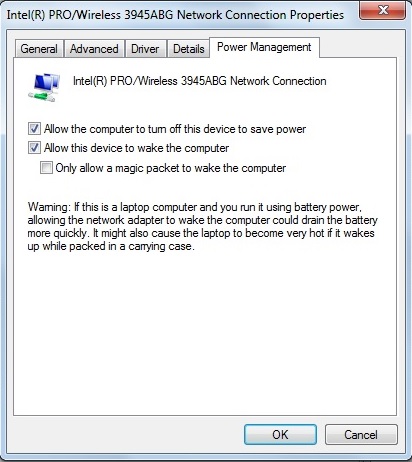
Enable Wi-Fi Adapter WoWLAN in OS
With that said, I have not been able to get WoWLAN to work on two different Windows systems, each with the required Intel technology. Using my Windows 7 system (with an Intel Centrino chipset) that supports WoL over a wired connection, I was not able to trigger WoWLAN with the system in sleep or hibernate mode, let alone from a completely powered-down state.
Conclusion
My experience with WoL is it is reliable over a wired LAN, but is not reliable remotely or via Wi-Fi. The magic packet is a simple Layer 2 frame, but it ultimately has to be placed on the LAN as a broadcast packet to ensure it gets to the target PC. Encapsulating this broadcast frame and sending it over the Internet and through a NAT firewall / router may not always work. Further, I have not had success with WoWLAN, leading me to conclude that although WoWLAN may work in some circumstances, it is also not very reliable.
