Introduction

| Sonicwall SOHO TZW | |
|---|---|
| Summary | Feature-rich firewall appliance with Sonicwall’s usual high quality. Built-in IPsec VPN endpoint and bundled VPN client for IPsec-secured wireless connections. |
| Update | None |
| Pros | • Simultaneous support of IPsec VPN and normal wireless traffic • Can control wireless and wired bridging and wireless client-to-client communication • Bandwidth • Consistent wireless performance vs. range |
| Cons | • 33% wireless throughput reduction with IPsec-based encryption • Low throughput with draft-11g clients • Support contract ($) required for firmware updates, and email / phone support |
Sonicwall is well known and regarded for their powerful, yet easy-to-use line of security appliances aimed at the small to medium business buyer, who can presumably afford the premium that Sonicwall commands for its products.
With their first foray into wireless security appliances, it appears that Sonicwall decided to bypass all the LEAP, PEAP, and other WLAN security alphabet soup and base the TZW on tried and true IPsec VPN technology. What they hoped to produce was something as easy to use, robust, and secure as their wired products, but with 802.11b wireless users now brought under their security umbrella. Did they succeed? That’s what I set out to discover…
Features and Design Details
The TZW comes in an attractive blue and silver plastic enclosure that has the footprint and height of a typical hardcover novel. All indicator lights are on the front of the box and are bright and viewable from a wide angle. You get Link, 100, and Activity for both the WAN and single Ethernet LAN ports, and On, WiFiSec, and Activity lights for the Wireless LAN. Power and Test lights round out the indicators.
All connectors are on the rear panel, including one each WAN and LAN 10/100 LAN ports, power jack, Command Line Interface (CLI) DB-9M serial port, and two RP-TNC connectors for the antennas. A nice touch is that you can force speed and mode for each port via the admin interface (default is autonegotiate), but on the negative side there’s no Normal / Uplink capability for the LAN port – although Sonicwall thoughtfully includes both normal and crossover UTP cables. Note also that there’s no documentation included for the CLI on the CD that comes with the TZW or anywhere I looked on Sonicwall’s website.
Two minor negatives are that one of the antenna connectors is very close to the power jack and there is no hardware reset switch. You can, however, reset the box from the admin interface.
Internal details
The TZW is powered by a Toshiba TMPR3927 RISC-based processor clocked at 133MHz. Although there’s also a Sonicwall custom ASIC, Sonicwall says that the TZW does not include a hardware IPsec coprocessor.
Figure 1: TZW internal view
(click on the image for a full-sized view)
Figure 1 shows the TZW’s innards, including the Intersil PRISM-based 802.11b mini-PCI radio, which looks to be a Senao SL-2511MP. The radio is cabled to two RP-TNC style connectors that have two moveable, jointed 5dBi dipole antennas attached.
I should note that Sonicwall says that they don’t plan to make the TZW’s radio field upgradeable. Their reasoning is that since the IPsec processing power is matched to 802.11b’s 5Mbps or so best-case throughput, adding an 802.11a or 11g higher-bandwidth radio would also entail adding more juice to the VPN processing. So if 802.11b isn’t your thing, you’ll need to wait until Sonicwall comes out with a TZW model that has the radio you’re looking for.
That’s it for the internal exam. Let’s move on to the setup.
Setup and Administration
There are so many features in the TZW that if I were to write about them all, it would make this review about as long as its 283 page Administrator’s guide! So in the interest of my finishing this review sometime this month, I’ll try to hit the TZW’s more unique highlights.
The TZW comes set to 192.168.168.168 but with its built-in DHCP servers (there are two – one each for the LAN and WLAN network segments) disabled. So you’ll need to set the computer to an address in the same subnet in order to connect (Sonicwall suggests 192.168.168.200). All this is outlined in the printed Quick Start Guide that comes in the TZW’s box.
TIP: After you complete initial setup, remember to change your client’s settings to match the IP addressing method you choose! I forgot to set my client back to being a DHCP client after enabling the TZW’s DHCP server. I had trouble browsing the web until I figured out that my client didn’t have the right DNS info! Guess I should have read the Quick Start Guide, which clearly describes the proper steps…
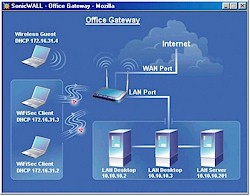
Once you get connected, a setup wizard automatically launches to step you through the initial setup. The toughest part here is deciding which of the three scenarios matches your needs, but, even then, Sonicwall provides handy diagrams of each one to help you decide (see Figure 2).
Figure 2: Office Gateway Setup Scenario
(click on the image for a full-sized view)
I found the Admin interface logically arranged and generally responsive, although I experienced a noticeable lag when accessing it from one of my slower machines. Setting changes take about 5 seconds to save and I didn’t really run into any situations that required a restart – which was a good thing since restarts and cold boots take about 90 seconds!
In keeping with the security focus of the product, both HTTP and HTTPS connections are supported for the admin interface, with the default method for administration from wireless clients set to HTTPS. Depending on your browser’s settings you may get some popups warning you about security certificate acceptance, but if you just tell the browser to accept the certificates permanently, you shouldn’t be bothered with them again.
Remote management can also be done via HTTP or HTTPS, and you can set the port used for each service, restrict management to a single IP address or address range, and set the admin interface idle auto-logout time and login lockout after a settable number of failed attempts.
The TZW handles the usual static, dynamic and PPPoE WAN types, but also includes the not-so-common options of PPTP and L2TP authentication, supporting static or dynamic IP addressing for each. MAC address cloning and host name authentication are also supported, but not domain-based authentication.
Manage that Bandwidth
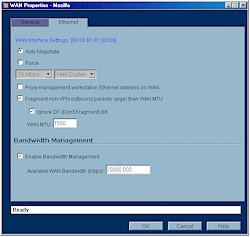
The feature that could really make potential buyers take a second look at the TZW is its bandwidth management features shown in Figures 3 and 4.
Figure 3: Bandwidth Management Enable
(click on the image for a full-sized view)
You can set both the total bandwidth used by the TZW and control the bandwidth of each service, i.e. FTP, HTTP, etc. You can also set the bandwidth allocated to VPN use.
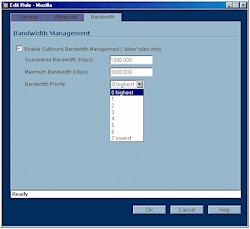
Figure 4: Bandwidth Management Setting
(click on the image for a full-sized view)
Unfortunately, you can’t control bandwidth by user or LAN type (Ethernet or wireless) and the controls apply to outbound traffic only. Still, given that bandwidth control generally isn’t available in this class of router, I applaud Sonicwall for taking these first steps and hope that the bandwidth management features – especially control of individual users – will be enhanced in future firmware revisions.
Firewall Features
The TZW uses a Rules and Services firewall programming model, which, thanks to its use on some models of inexpensive consumer routers, may be more familiar than it was a few years ago. Services define the ports and protocols (TCP, UDP, and ICMP can be specified) that will be used to control packet forwarding, and Rules define the data source and destination and IP address(es) that are used to control access to a specified service. The TZW comes with some pre-defined Rules and Services, and you can add 100 more of each.
Together, Rules and Services provide Port Forwarding (the ability to reach LAN-based services from the WAN side of the TZW), and Port Filtering / Access Control (the ability to control the Internet services that users can access) features.
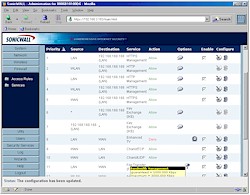
Figure 5: Firewall Rules
(click on the image for a full-sized view)
Figure 5 shows a portion of the Access Rules screen, which provides an excellent view into the flexibility of the TZW’s firewall controls. Temporarily disabling, editing and deleting rules is a snap, and icons are used to indicate important rule features, such as time-of-day enabling, and whether bandwidth control is in use.
The screenshot also shows how “tool tip” types of pop-ups are used to provide details represented by the icons, saving the need to edit the rule in order to view that information. Note that you can also change how long the ports for idle TCP-based services stay open from their 5 minute default timeout and whether fragmented packets are allowed to pass.
Consumer router users considering a step up to the TZW should be aware of two things. The first is that there isn’t a “DMZ” function per se. If you want to put a computer outside the TZW’s firewall, you’ll just need to implement an Access Rule opening all WAN services to a specific LAN machine’s IP address. The second issue may put a crimp in the ability to run certain gaming and multimedia applications that dynamically allocate ports since the TZW doesn’t support outbound port triggers. It does, however, have special “dynamic port” support for ORACLE SQL.net, Windows Messenger, and H.323-based conferencing applications such as NetMeeting.
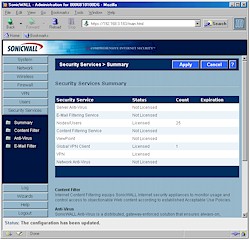
In addition to the Rules and Services firewall functions, the TZW also has other security muscles it can flex via a visit to the Security Services admin page shown in Figure 6.
Figure 6: Security Services
(click on the image for a full-sized view)
Unfortunately, most of what you see here will cost you extra to keep after their free 30 day trials expire. But it’s nice to know that Email and Content filtering and McAfee-based Anti-Virus services are available if you need them.
Content Filtering runs in the TZW, costs over $300 for a one year subscription, and allows you to choose among a Sonicwall Content Filter List, or filtering by N2H2, or Websense. But even if you don’t spring for the paid service, you can still enable blocking of Web Proxies, ActiveX, Java, and Cookies and Known Fraudulent Security Certificates to help protect your clients from harm.
The Anti-Virus Service (about $30 per protected client per year) runs anti-virus and email filtering software on each client, but uses the TZW to make sure that an up-to-date anti-virus application with the latest virus data files is running on a client before it allows it Internet access. The service handles the anti-virus application and virus data updating process for all protected clients, too.
VPN
With all the TZW’s other features, it’s easy to forget that it includes a full-featured IPsec VPN endpoint that supports up to 10 WAN-based VPN tunnels, with no limit on the number of users (up to the TZW’s maximum of 25 licensed users) per tunnel. Sonicwall appears that they’re really trying to reduce the VPN licensing hassle since they even include one client license that will work from the TZW’s WAN side so that at least one road-warrior will be able to tunnel into home base without having to cough up about $45 for a Global VPN client license.
Figure 7: VPN Setup
(click on the image for a full-sized view)
The endpoint has just about any IPsec feature you’d want and can work with both static and dynamic WAN IP addresses as long as the TZW with the dynamic address initiates the tunnel. There are so many configuration options available (Figure 7 is only the tip of the iceberg) I suggest you download the TZW’s Administrator’s guide if you want the full story, but I’ll give you a little taste here:
- Site-to-site, hub-and-spoke, and mesh tunnel configurations supported
- Separate control of Phase 1 and 2 proposals
- Allows selection of Diffie-Hellman Group 1,2, and 5 key exchange
- DES and 3DES encryption and SHA1 and MD5 authentication supported
- Support for MS Networking NetBIOS broadcast (disabled by default)
- Ability to hide remote tunnel end LAN behind the TZW’s NAT and firewall
- Built-in L2TP server
If all this doesn’t suit you, the TZW also supports VPN pass through for multiple connections with PPTP, IPsec and L2TP protocols. This comes in handy since your company may require the use of a specific VPN client or protocol not supported by the TZW’s endpoint.
VPN Performance
Since I didn’t ask Sonicwall for two TZW’s, I did my VPN throughput testing using my Dell Inspiron 4100 laptop running Sonicwall’s Global VPN client. I used my laptop’s 10/100 Ethernet port running at 100Mbps full duplex and plugged it into one of the switch ports in my network’s main router. This connected me to the TZW’s WAN port which was plugged into another of the router’s ports. I then added a new VPN connection using the Global Client’s wizard and I connected up on the first try. The test results are shown in Table 1.
Table 1: IPsec VPN Performance test results
|
Firmware Version: |
1.0.0.1 |
|
Test Description |
Transfer Rate (Mbps) |
Response Time (msec) |
UDP stream |
|
|
(Actual throughput- kbps) |
(Lost data- %) |
|||
|
Local to Remote |
6.9 |
3 (avg) |
499 |
0 % |
|
Remote to Local |
6.9 |
3 (avg) |
499 |
0 % |
This is great performance and more than needed for most SOHO and SME broadband connections. But since the same endpoint is used for the encrypted WiFiSec wireless connections, Sonicwall has wisely designed the TZW with enough VPN headroom to handle that load, too. If more performance tuning is needed, remember that you can enable the VPN bandwidth control to balance off wired and wireless VPN performance.
Logging
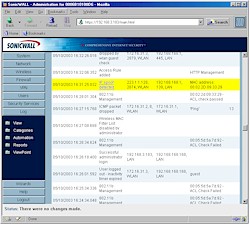
The TZW’s logging features are a pleasure to use, mainly because you get information and not just data. A look at Figure 8 shows you what I mean.
Figure 8: Log report
(click on the image for a full-sized view)
When you compare this with the gobbledygook you typically get with less expensive routers, it really looks like it’s a case of you get what you pay for. The log entries are constructed so well that even I can understand what’s going on without hitting Google to look up some port number or other cryptic log result. You can clear the log from the admin interface, and also email it or demand or have it sent via email daily, weekly, or when it fills up. You also get emailed alerts – choosing from attacks, system errors, blocked websites and VPN tunnel status – and can sent the log to multiple syslog servers.
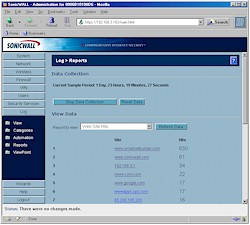
Data traffic reports are also available, one of which is shown in Figure 9.
Figure 9: Web site report
(click on the image for a full-sized view)
You can also get Bandwidth usage reports by user IP address and type of web service. These reports can’t be saved, but you can clear out data and stop and start its collection.
Other Features
The TZW has some features that will be helpful to folks with more advanced networking needs. For example, if you have more than one IP address from your ISP, you can define 64 different One-to-One NAT groups. Each definition assigns a range of private LAN IP addresses to one of the WAN IP addresses. This would let you, for instance, set up two different web servers, both running on Port 80, but answering to different WAN IP addresses or domains.
You can also establish Static Routes to handle networks with more than one subnet and flush and set the cache timeout for the TZW’s ARP table. But if dynamic routing is your thing, the TZW unfortunately doesn’t give you any control over the handling of RIP or other dynamic routing protocols.
If you have a proxy server on your network, you can move the server to the WAN and enable the Web Proxy Forwarding feature. The TZW then automatically forwards all Web proxy requests to the proxy server without requiring you to change the proxy settings on every machine on your network… a royal pain if you’ve ever had to do it!
I previously mentioned that there are separate DHCP servers for the LAN and WLAN segments. But I neglected to say that you can set the address ranges, and also program specific IP info by MAC address, including segment type, gateway and DNS and WINS server info.
You also get a number of diagnostic tools including the ability to Ping, run traceroute, do a hostname (or reverse) lookup, and run a packet trace on inbound traffic.
I could go on, but it’s time to move on to Performance.
Routing Performance
Testing Notes:
• All tests were run with Qcheck TCP and UDP ports opened from WAN to LAN client running Qcheck console
The results show plenty of routing speed in both directions and are up there with the best of the routers that I’ve tested.
Note that the lack of UDP test results in the LAN to WAN direction isn’t the TZW’s fault, but a problem that Qcheck has with many SPI + NAT routers. I’d expect actual performance to mirror that of the WAN to LAN UDP stream test results.
Routing Performance Test Results
| Test Description | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
|---|---|---|---|---|
| Throughput (kbps) | Lost data (%) | |||
| WAN – LAN | 10.5 | 3 (avg) 4 (max) |
499 | 0 |
| LAN – WAN | 13.6 | 3 (avg) 4 (max) |
||
| Firmware Version | 1.0.0.1 | |||
See details of how we test.
Wireless Features
The TZW provides a very broad set of wireless controls, monitoring features (Figure 10), and of course, security!
Figure 10: Wireless Status
(click on the image for a full-sized view)
It takes a little doing to wrap your brain around all that’s going on in the TZW’s wireless section – especially the security features. There are so many layers and options for your wireless client to get through that I strongly recommend you use the built-in Wireless Wizard when setting up the first time. Read this description from the TZW’s Administrator Guide and you’ll see why.
On the SOHO TZW, wireless clients connect to the Access Point layer of the firewall. Instead of bridging the connection directly to the wired network, wireless traffic is first passed to the Secure Wireless Gateway layer where the client is required to be authenticated via User Level Authentication.
Access to Wireless Guest Services (WGS) and MAC Filter Lists are managed by the SOHO TZW. It is also at this layer that the SOHO TZW has the capability of enforcing WiFiSec, an IPSec-based VPN overlay for wireless networking.
As wireless network traffic successfully passes through these layers, it is then passed to the VPN-NAT-Stateful firewall layer where WiFiSec termination, address translation, and access rules are applied. If all of the security criteria is met, then wireless network traffic can then pass via one of the following Distribution Systems (DS):
•LAN
•WAN
• Wireless Client on the WLAN
• VPN tunnel
Got all that? A diagram would’ve helped a lot, but basically it means that there are three choices for letting wireless clients authenticate with the TZW’s AP:
- Normal – Via the 802.11 ESSID authentication process.
- Guest Services – This is a “hotspot”-like function that lets clients associate, but blocks all traffic until the user fires up a web browser and logs in with a username and password.
- WiFiSec – This mode also allows a client to associate, but requires that the client authenticate and encrypt all traffic via IPsec before allowing data to pass.
Using WiFiSec requires installing a custom version of Sonicwall’s Windows-based Global VPN client on your notebook. No, this doesn’t mean that Sonicwall is now giving away their IPsec client, because although the version that comes on the TZW’s CD will work for any number of wireless connections, it will support only one WAN-based wired tunnel. Although Sonicwall doesn’t limit the number of WiFiSec connections via licensing, it recommends only a maximum of 20-25 simultaneous clients for satisfactory WLAN performance.
This is a very powerful feature set, and I especially like the ability to run both WiFiSec and Guest Service connections at the same time. Note that it’s possible to have multiple clients using the same Guest Service account, so all you have to do is freely post the username and password if you want folks to have open access to the Internet via your TZW, while keeping them safely off your wired LAN. You won’t be able to post this information on the login page, however, since the login message is not customizable. You can, however, set how long your “guests” can stay and how long guest accounts themselves are good for.
Although you can enable Guest Services and WiFiSec independently, turning either one of them on kills the ability to use only plain-vanilla 802.11 ESSID authentication. You can, however, enable 64 or 128 bit WEP in any of the three modes, although why you’d want to run it at all given the TZW’s other security features is a reasonable question. But it’s there if you really want it.
And while I’m on the subject of 802.11-based security, I’ll note that neither 802.1x-based authentication nor WPA enhanced security is supported, nor are they likely to be. Sonicwall’s position is that its IPsec-based security takes the place of all that and does it in a way compatible with the wide number of IPsec client and gateway products that have been around for years.
MAC address association control (MAC Filter) works in addition to the above authentication schemes. Once enabled, the MAC Filter list prevents all clients from even associating with the TZW’s AP until their MAC address is entered into the list. Two negatives on this feature are that you can’t load or save the Filter list and it doesn’t present a pick-list of associated or in-range clients to ease the job of adding clients to the list.
The other thing to note about the MAC Filter list is that it’s automatically brought into play when Guest Services are enabled and is used to control “guest” AP association. But Guest Services clients don’t show up in the MAC Filter list and the MAC Filter isn’t automatically disabled when you disable Guest Services. Since the MAC Filter defaults to blocking all stations that are not entered into its list, you’ll need to remember to shut it off when disabling Guest Services – something that I forgot to do on more than one occasion during my testing!
Once authenticated, clients must then run the TZW’s firewall gauntlet, which is default configured to allow only Internet access to wireless clients. You can set a firewall rule to allow traffic to pass between WLAN and LAN, but it will be ignored for traffic authenticated via Guest Services. The firewall also defaults to not allow wireless client-to-client communication, but this can be turned off.
Other wireless settings of interest are the ability to set transmit power, Beacon and DTIM intervals, and RTS and Fragmentation thresholds. You can also limit the number of client associations (default is 32), authentication timeout, length of association, and terminate an associated client. You can separately limit the number of clients using Guest Services and choose whether to apply the TZW’s firewall filtering to their traffic. And happily, there’s the strongest wireless security feature of all – the ability to shut off the AP entirely!
Wireless Performance
NOTES:
• “Signal Quality” readings were not available
• WiFiSec mode enabled and WEP disabled
• Testing was done with an ORiNOCO 802.11b Gold client card in a WinXP Home Dell Inspiron 4100 laptop
I started out trying to use a NETGEAR WAG511 a/b/g card [reviewed here] for my testing, since it has a good 11b radio and I wanted to give the TZW a fair shot at turning in good performance marks. However, after futzing around with it and other draft-11g based cards for a few hours I found that I couldn’t get any card to go faster than about 1Mbps or so. So I gave up and decided to use an ORiNOCO 802.11g Gold card instead. I later read the following in the release notes for version 1.0.0.1 of the TZW’s firmware:
Some wireless cards, notably Netgear and Linksys 54G cards, have demonstrated compatibility issues when connecting to other manufacturer’s devices. Compatibility issues are further complicated by the use of WEP, or by increasing the beaconing interval beyond its default value. It is strongly recommended that you upgrade to the latest firmware and device drivers available from your wireless client card’s manufacturer, particularly if you are using Netgear or Linksys 54G equipment.
I asked Sonicwall how they were sure that the problem lay with the draft-11g cards and not with the TZW’s radio and basically got a “draft-11g new and unstable, PRISM stable and mature” (I’m paraphrasing) response. But no matter what the cause, I’d have to say that I agree with Sonicwall’s warning and advise not planning on using any 802.11g cards with the TZW until after 11g is ratified and you update your card’s firmware with released 11g code!
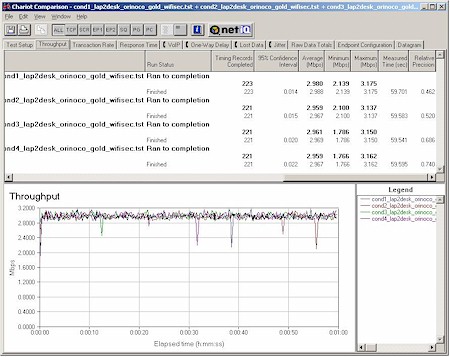
With my test client chosen, I then decided to do my four location throughput test in the WiFiSec mode and without WEP enabled, since I figured most users would be running in that mode. Figure 11 shows the results.
Figure 11: Four Condition Throughput test – WiFiSec mode
(click on the image for a full-sized view)
As you can see, the TZW had consistent throughput in all of my test locations, but with 3Mbps average throughput – significantly lower than the best case throughput of good 802.11b products.
I attribute the consistency to the dual 5dBi antennas and 200mW radio which together produce a stronger signal than the 2.2dBi dipoles and 30mW radio that come with many consumer APs.
The lower throughput, however, came from the use of WiFiSec. Since the TZW has two potential throughput stealers in its WEP and WiFiSec encryption options, I ran some tests to quantify the effects of each.
Figure 12: Security option throughput comparison
(click on the image for a full-sized view)
Figure 12 shows four Chariot “Condition 1” (close range) runs with:
- neither WiFiSec nor WEP enabled
- WiFiSec only enabled
- WEP 128 only enabled
- WiFiSec and WEP 128 both enabled
You can see that the best case wireless throughput is around 4.5Mbps, with WEP taking an almost 20% bite and knocking throughput down to about 3.7Mbps. Choosing the more secure WiFiSec, however, lowers throughput by about 1/3 (33%). Fortunately, the effects of WEP and WiFiSec aren’t additive, since the last run made with both enabled shows the same 33% reduction as with WiFiSec alone.
I found this result surprising, especially considering that my Ethernet-based VPN testing showed about 7Mbps available through a wired tunnel. But there are apparently other factors that come into play with the wireless WiFiSec that result in the reduction that I measured.
So although I give the TZW excellent remarks on throughput vs. range performance, I have to say I’m disappointed with the significant WiFiSec throughput hit. 802.11b’s best-case 5Mbps-or-so throughput is marginal enough for busy wireless LANs, and business users may find the lowered WiFiSec bandwidth insufficient for their needs.
802.11b Wireless Performance Test Results
| Test Conditions
– WEP encryption: DISABLED |
Firmware/Driver Versions
AP f/w: |
||||
|---|---|---|---|---|---|
| Test Description | Signal Quality (%) | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
| Throughput (kbps) | Lost data (%) | ||||
| Client to AP – Condition 1 | 0 | 3 [No WEP] 2.9 [w/ WEP] |
5 (avg) 6 (max) |
404 | 19 |
| Client to AP – Condition 2 | 0 | 3 | 5 (avg) 6 (max) |
404 | 19 |
| Client to AP – Condition 3 | 0 | 3 | 5 (avg) 6 (max) |
402 | 19 |
| Client to AP – Condition 4 | 0 | 3 | 5 (avg) 6 (max) |
403 | 19 |
See details of how we test.
Wrap Up
It’s been awhile since I spent time with a Sonicwall product and I’d forgotten what a pleasure it is to work with SonicOS-based devices. I guess one really can’t expect the feature set of a consumer router to be the comparable to a product costing many times its price. But a few days with the TZW have served as a good reminder of how little the user interfaces of consumer products have improved over the past few years. Sure, the admin screens may have gotten a little more pleasing to look at, but ease-of-use remains just a catchphrase and decent logging and monitoring features still a gleam in some product manager’s eye (somewhere… I hope!) in consumer gateway-land.
On the other hand, the average home user would probably raise holy hell if Linksys, NETGEAR or any of the other guys tried to charge $115 for a one-year “8 X 5” support contract, without which they wouldn’t even be able to download firmware updates, never mind access email or phone-based support!
But all that considered, I think small businesses and even well-heeled consumers may just have had their prayers answered. The TZW provides an easy-to-use way to both securely connect a couple of locations and support bullet-proof wireless client connectivity. And it does it all in a way that doesn’t require a degree in rocket science to set up! But be warned… once you try the TZW, you may never be able to go back to the cheap stuff again!