Introduction
Update 11/19/2007: Various adds from Netgear feedback (Pg 4).
Update 11/15/2007: Slow WAN failover fixed. (Pg 4)

| At a Glance | |
|---|---|
| Product | NETGEAR ProSafe VPN Firewall 200 (FVX538) |
| Summary | Dual WAN IPSec-endpoint router supporting 200 IPSec concurrent tunnels with nine-port switch. |
| Pros | • Dual WAN and Hardware DMZ ports • 200 IPSec Tunnels • Powerful CPU, RAM and Encryption Processor • Nine LAN ports, including one gigabit port |
| Cons | • High VPN latency • Lack of VPN Vista support • Non 3DES VPN instability |
I recently reviewed the NETGEAR FVS124G, so I jumped at the chance to take a look at the FVX538, NETGEAR’s top-of-the-line VPN router.
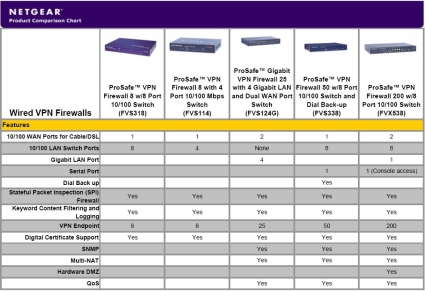
NETGEAR lists seven routers in its wired business class VPN product line. The FVX538 distinguishes itself by offering the combination of dual 10/100 WAN ports, eight 10/100 LAN ports plus one 1000 Mbps LAN port and support for up to 200 IPSec VPN tunnels. Figure 1, from NETGEAR’s product page, summarizes the key features of the line.
Figure 1: Overview of NETGEAR’s wired VPN firewalls
Physically, the FVX538 measures 13″ wide by 8″ deep and 1.75″ high, and can be installed in a standard 19″ rack with the included mounting brackets. The power supply is built in, and there is an on/off switch on the back. We recently posted a slideshow providing some good looks at the FVX’s hardware.
Building the power supply into the device makes for a cleaner installation, and the power switch is a nice convenience over smaller devices that force you to unplug and plug power cords to power-cycle the unit.
On the inside, the FVX has some impressive hardware, including an Intel 533MHz CPU, 64MB RAM, 32MB Flash, and a Cavium Encryption Accelerator, rated for 60+ Mbps of 3DES/SHA-1 encryption throughput. In comparison, its little brother, the FVS124G, has a 200MHz CPU, 16MB RAM, 4MB Flash, and no Encryption Accelerator.
The new CPU is a welcome addition. I noted in my review of the FVS124G that screen response at times was sluggish. Just clicking through the menus of the two devices side by side, it is readily apparent that the FVX is far more responsive.
I liked the FVX’s gigabit LAN port, but wonder why NETGEAR didn’t make all the LAN ports gigabit as they did with the four port FVS124G. Still, the single gigabit port is useful to connect to a gigabit LAN switch, leaving the other eight 10/100 ports for shared 100 Mbps network devices such as printers.
In Use
As you can see in Figure 2, showing the opening menu screen for the NETGEAR FVX538, and Figure 3, showing the opening menu screen for the NETGEAR FVS124G, NETGEAR has a new color scheme and layout. The use of more than two colors and adding some grays and contrast is a nice improvement to the previous basic blue and white color scheme.
Figure 2: Opening menu from the FVX538
Figure 3: Opening menu from the FVS124G
The configuration options on the FVX538 are nearly identical to the options on the FVS124G, with some reorganization and minor modifications. Table 1 provides a matrix of the FVX’s configuration options, which include five main menus, each with 5–7 submenus.
| Main Menus | Submenus | ||||||
|---|---|---|---|---|---|---|---|
| Network | WAN | Protocol Settings | Dynamic DNS | LAN Settings | DMZ Setup | Routing | |
| Security | Services | Schedule | Block Sites | Firewall Rules | Address Filter | Port Triggering | Bandwidth Profile |
| VPN | Policies | VPN Wizard | Certificates | Mode Config | VPN Client | Connection Status | |
| Admin | Remote Mgmt | SNMP | Backup & Upgrade | Password | Time | ||
| Monitoring | Status | Traffic Meter | Diagnostics | Firewall Logs | VPN Logs | ||
Table 1: A matrix of the FVX538’s menu structure
Another nice touch is the sticker on the bottom of the device with the default network address, user name, and password as displayed in Figure 4. Coupled with the manual being fully accessible via a link in the menu, as well as help documentation located throughout the configuration screens, makes it possible to simply fire up the FVX538 and configure it without spending a lot of time searching for information on options and configurations.
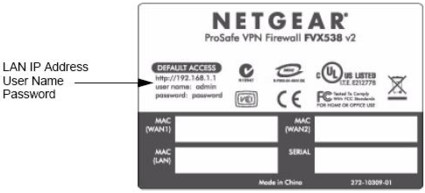
Figure 4: The information sticker on the bottom of the device
LAN Features
NETGEAR has several nice features for managing your LAN devices in its ProSafe line. First, there is the DHCP server, a standard feature on most routers. As part of the DHCP server, NETGEAR uses DNS proxy to assign a DNS IP address to devices that receive their IP addresses from the NETGEAR, an important feature for a Dual WAN router.
Each ISP has its own DNS servers and may not allow access to them from foreign networks. If a router’s DHCP server were to issue DNS IP addresses from one of its WAN connections and then fail over to the other WAN connection, LAN devices may not be able to resolve web addresses. The NETGEAR will issue its own LAN IP address as the DNS IP address to DHCP clients and then forward DNS requests to the DNS IP specific to the WAN connection.
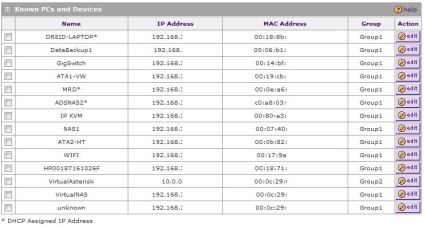
Second, the FVX has what it calls the network database. The FVX builds a database of devices as they connect to the router and are assigned an IP by the DHCP server. Once the device is detected by the FVX, you can assign it to a Group, give it a name, and configure it as a Static IP or Reserved DHCP IP, as you can see in Figure 5.
The advantage of assigning devices to Groups is the ability to apply a single security policy to multiple devices. Up to eight different Groups can be created, and the FVX will support up to 253 devices. In the FVS124G, NETGEAR provided the option to name or number up to eight Groups. With the FVX538, the Groups are simply numbered 1–8.
Figure 5: The network database
I like the network database, as it becomes a central place to find all the devices on your LAN, without having to look up IP addresses or names. A feature the FVX doesn’t have that I’ve seen on some other devices is access to the web utilities of all my network devices. The ability to launch the web configuration utility for a LAN device directly from a router’s network database page would be useful. For example, to access the web utility of my switch, which I named “GigSwitch” in Figure 5, it would be handy to click and launch a browser to that IP.
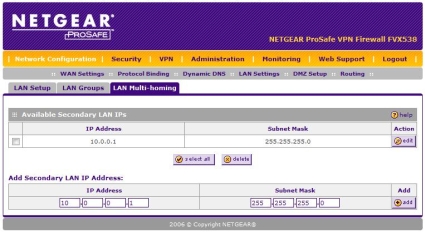
Third, the ProSafe router software has a feature called LAN Multi-homing. This feature enables a network administrator to separate their LAN into multiple subnets, a nice way to organize your devices. It isn’t perfect, as it doesn’t provide a barrier between broadcasts as a VLAN does, and the DHCP server provides IP addresses in only one subnetwork. But this feature can be useful to logically group a couple servers or other devices.
In Figure 6 below, I assigned 10.0.0.1/24 as a secondary LAN IP. Devices connected to any FVX LAN port with static IP addresses in the 10.0.0.0/24 network can access the Internet if assigned a gateway IP of 10.0.0.1, as well as access devices in the other subnetworks on the FVX.
Figure 6: The LAN Multi-homing configuration page
DMZ
In between the LAN and the WAN is the “demilitarized zone”, or DMZ. DMZ functionality on a router allows for maintaining a separate network that can still use your WAN connection, but is intentionally not protected by your firewall. The FVX538 is the only member of NETGEAR’s ProSafe lineup that provides a physical DMZ port, which is the eighth LAN port.
There is a separate indicator light on the front of the FVX that indicates the eighth LAN port is in DMZ mode. An additional DHCP server can be activated to assign IP addresses to devices in the DMZ LAN as desired. In Figure 7 below, I’ve enabled the DMZ option, as well as the DHCP server, creating a separate network outside the FVX’s firewall but still able to utilize my network’s WAN connectivity.
Figure 7: The DMZ Setup page
WAN Features
The FVX538 has two WAN ports, both of which support PPPoE or basic Ethernet connections, with options for DHCP or Static IP addresses. The PPPoE connection, if password and login is required, will automatically log in and establish a connection on power up, reboot, or use, a useful automation.
The value of dual WAN connections is the ability to have continuous connectivity, even through loss of an ISP connection. A dual WAN router should be able to support multiple connections, provide the option of using them in a load balancing or failover mode, send all traffic to the active connection when one fails, and revert back to a desired state when the connections are restored.
I tested the failover on the FVX538 by setting up static Ethernet connections from the FVX538 to two different routers, both with connections to the Internet, using WAN1 as primary and WAN2 as failover. I simulated WAN failure by pulling the plug from WAN1 while running a continuous ping to a public Internet site, and timing how long before those pings were successful. Multiple runs of this test produced a disappointing 2 minute 45 second average. This is slightly improved from the 3 minute average measured on the FVS124G, but still a long time to switch over.
I used the FVX WAN status screen to watch the WAN port status, and it revealed an interesting detail. The FVX538 doesn’t detect the primary WAN connection is down for nearly 2 minutes! Each time I pulled the WAN1 connection, I could see in the NETGEAR status screen that the router considered the WAN1 port “UP,” even though there was nothing plugged in! The physical lights on the port went out the second the cable was removed, yet the software didn’t recognize the interface as down for nearly 2 minutes.
The delay in the interface status detection is obviously a big contributor to the slow failover performance. Since the processor of the FVX538 is more than double the speed of the FVS124G, yet the failover performance is nearly the same, it appears the issue lies in the NETGEAR software.
Update 11/15/2007: In response to a helpful comment from Joe Sutherland, I went back and found the settings in the WAN mode section that allow adjustment of the amount of time before a WAN failure is detected and triggers a rollover.
There are two parameters; Test Period (default = 30sec), and Failover (default=4), representing the number of failed Test Periods before rollover. The Test Period default of 30 seconds is the minimum, the router won’t allow you to set it any lower. However, the default value of 4 in the Failover field can be set to a lower number.
I repeated my test with the defaults, and then adjusted the Failover parameter. I was able to improve rollover time by 30 seconds for each “click” of this control, as would be expected.
BTW, to set up port forwarding in rollover mode when connecting to the secondary WAN port, specify the incoming interface (WAN1 or WAN2), then the port and internal server IP where you are directing the traffic. You need to set up the same rule for both WAN1 and WAN2 directed at the internal server. I tested this and was able to set up port forwarding for Remote Desktop Connection (tcp port 3389) traffic from both WAN interfaces to the same internal server.
NETGEAR Support
NETGEAR links its support page to the menu of the FVX538, so I gave it a try. I submitted separate support requests to NETGEAR, asking about the availability of a Vista VPN client and VLAN support using MultiLAN functionality. Although neither answer was what I wanted to hear, the responses were received within 1-2 business days and were clearly written.
NETGEAR offers multiple support options, as well as a robust warranty for their ProSafe product line. I’ll cover both at the end of this review.
VPNs
I keep a Site-to-Site VPN tunnel going continuously between the two sites a couple of miles apart, using a Linksys RV042 on one end and a SonicWALL TZ190W on the other. I put the FVX538 in my lab and configured it to take the role of the Linksys RV042, and re-established the Site-to-Site VPN tunnel.
But I had some issues getting the tunnel to connect. Duplicating the configurations I had on the RV042 to the NETGEAR, I got the tunnel to work, and left it running overnight. The next morning, though, I couldn’t log into the FVX. It presented the login screen, but didn’t accept my user name and password. I ended up having to completely disconnect the NETGEAR from all connections and power cycle before I could log in again.
NETGEAR’s support site has some useful VPN configuration instructions, and conveniently, a guide for a Site-to-Site VPN between a FVX and a SonicWALL device, here (PDF link). I followed the NETGEAR guide and defaults for a NETGEAR to SonicWALL tunnel, which did work. I had to step down the tunnel encryption from the more secure AES encryption to 3DES encryption, as well as modify several other options. Once the NETGEAR-recommended configurations were entered on both ends, the tunnel came up and was stable.
Update 11/19/2007: Netgear said it will create an application note on setting up a VPN tunnel using AES (versus 3DES).
However, I noticed that ping times changed dramatically from LAN to LAN over the VPN tunnel. To ensure there were no anomalies or errors, I repeated the tests and setup, and verified my results. For some reason, ping latency over the VPN tunnel using the RV042 was 15-25ms better than with the FVX538.
As you can see from Table 2, LAN-to-LAN ping times are significantly higher using the FVX to set up a tunnel to a SonicWALL than a Linksys RV042. The intent here isn’t to compare the NETGEAR and the Linksys, but these results were repeatable and are a clear difference.
The LAN-to-LAN ping times reflect the delay end devices would experience connecting over the VPN. This Site-To-Site VPN tunnel is used to provide off site backup storage, so the added delay will impact data being copied from one site to the other.
| Path | WAN-to-WAN | LAN-to-LAN VPN |
|---|---|---|
| RV042 to TZ190W | 9ms | 11ms |
| TZ190W to RV042 | 16ms | 16ms |
| FVX538 to TZ190W | 9ms | 36ms |
| TZ190W to FVX538 | 16ms | 33ms |
Table 2: Ping times in various configurations
This data is surprising, as the FVX538 is rated to support 200 VPN tunnels, has a more powerful CPU, more RAM, and a separate Cavium Encryption processor. There is obviously some form of encryption / encapsulation delay being introduced by the NETGEAR VPN module.
Update 11/19/2007: Netgear told us that ping response is “one component of a comprehensive traffic mix that can be used to assess performance” and that the 538 wasn’t particularly optimized for ICMP (used by ping).
The FVX538 includes five licenses of NETGEAR’s VPN Client software based on a product called SoftRemote from SafeNet. SoftRemote now supports Vista, yet NETGEAR hasn’t updated its version of the client to support Vista as of this writing. Version 10.7.2 is shipped with the FVX538, a newer release than the 10.7.1 that shipped with the FVS124G.
Update 11/19/2007: Netgear says they will be releasing a Vista VPN client “this quarter”.
As with the site-to-site VPN, NETGEAR provides a useful guide here for configuring both a router and the VPN client for remote VPN connectivity. There are multiple ways to configure VPN Client access, including manually, using the wizard, or with Mode Config.
Mode Config is the more secure method, and this is the means outlined in the NETGEAR guide. Mode Config allows remote VPN clients connecting to your LAN to be assigned an IP address in a different subnet than your LAN, enabling remote access to your LAN, yet providing a logical separation between the remote clients and local clients.
Performance
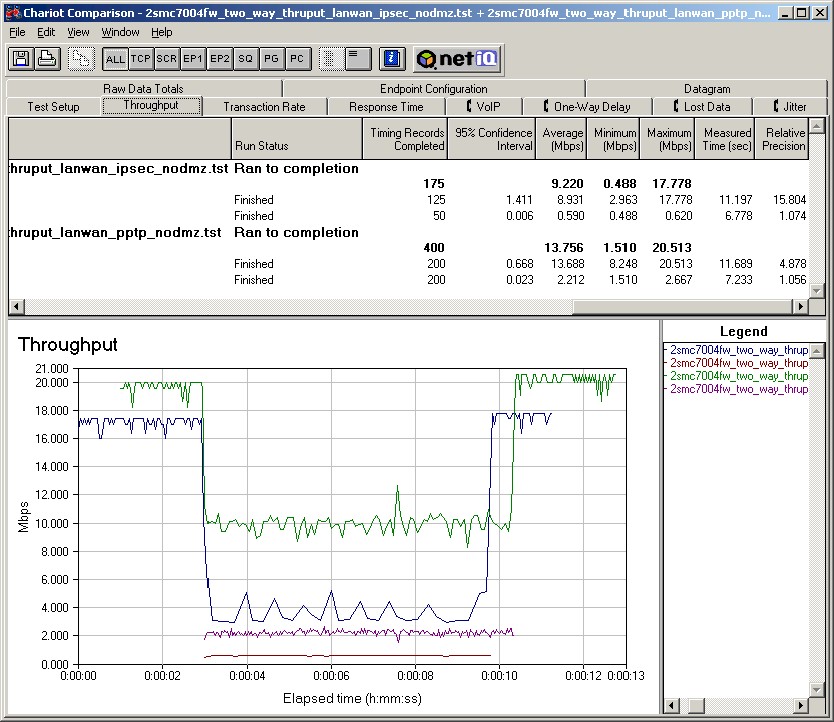
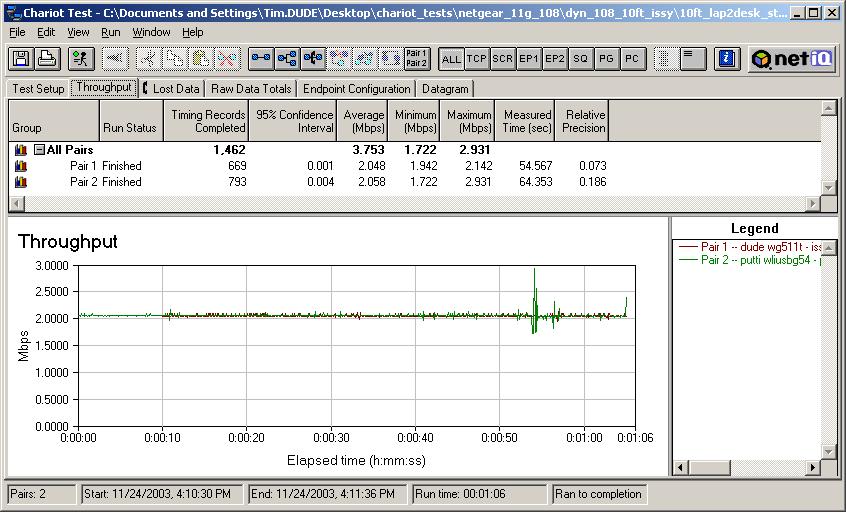
The FVX performs solidly as a network router with the highest measured total simultaneous throughput of any Dual WAN router on our Router charts. With the combined throughput of both inbound and outbound traffic reaching over 80 Mbps as shown below in Figure 8, the FVX has the horsepower to handle a larger LAN with multiple WAN connections.
Figure 8: A test of the FVX538’s throughput
Physically, the FVX538 compares closely to the Linksys RV082, another dual WAN router with eight LAN ports. Linksys’ RV042 is another dual WAN option, with only four ports, but I used it for comparison to utilize more current test data.
Interestingly, both the RV042 and FVX538 utilize Intel IXP CPUs, with the newer FVX using a 533Mhz CPU to the RV042’s 266Mhz CPU. Table 3 shows current performance measurements between the RV042, FVX538, and the FVS124G (as a reference). The FVX is clearly a step up in throughput from the FVS, and it has some performance advantages over the RV042, but not as much as you’d expect for a newer device with this hardware.
| Comparison | FVX538 | FVS124 | RV042 |
|---|---|---|---|
| 3DES WAN-to-LAN | 12.3 | 5.1 | |
| 3DES LAN-to-WAN | 12 | 3.6 | |
| AES256 WAN-to-LAN | 20.7 | 21.9 | |
| AES256 LAN-to-WAN | 26.6 | 32.6 | |
| WAN-to-LAN Throughput | 80 | 13 | 54 |
| LAN-to-WAN Throughput | 78 | 12 | 80 |
| Total Simultaneous Throughput | 82 | 12 | 59 |
| Max Connections | 200 | 196 | 72 |
| Max Tunnels | 200 | 25 | 50 |
Table 3: Device performance measurements and comparisons
Pricing and Conclusion
The FVX538 can currently be found online for as low as $325, while the physically similar Linksys RV082 runs about $258. Dual WAN VPN routers with four LAN ports referenced in this review, the Linksys RV042 and the NETGEAR FVS124G, come in at $157 and $148, respectively. (All prices include shipping as calculated by Pricegrabber.)
Additional licenses for the VPN client are available on NETGEAR’s website for $44.99 each, and 5-packs can be found from various sources online for about $128.
In addition to the purchase price, NETGEAR offers a couple of service options with the FVX538. A three-year express replacement agreement for the FVX538 is $49 and a one-year 24×7 telephone support contract and next business day replacement agreement is $149.99. To increase this level of service to a three-year agreement is $299.99. Keep in mind, the FVX is covered under the Lifetime warranty NETGEAR recently began offering with the ProSafe product line.
But overall, I was disappointed in the FVX538. The FVX performs well as a network router, but I expected more. The hardware specifications, especially of the encryption co-processor, imply the FVX should be a top performer across the board. But there were instability issues with VPN tunnels using encryption other than 3DES and the lack of Vista support is annoying, In addition, the added 15–25ms latency for a site-to-site VPN tunnel is a concern and the slow failover times continue to plague NETGEAR’s dual WAN performance.
At the end of the day, I’ve tested more stable VPN routers that cost less. Other than the DMZ port, the FVX538 has few new features compared to the FVS124G. On the plus side, the FVX538 is a faster router, and I liked its construction, its additional LAN ports, and its updated admin interface. I hope that NETGEAR will work out their issues in future firmware releases, to take advantage of the strong hardware they’ve built into the FVX538.