Introduction
Updated 12/27/2009: Revised performance data
Updated 12/9/2009: Multiple corrections

| At a Glance | |
|---|---|
| Product | NETGEAR ProSecure Unified Threat Management Appliance (UTM10) |
| Summary | UTM appliance with high effectiveness aimed at small business users |
| Pros | • High Virus and Malware effectiveness • Easy to configure • Switch is VLAN enabled • Simple pricing for base box and services |
| Cons | • Laggy admin response • Low network and VPN throughput with UTM enabled • Basic intrusion protection options • No client AV |
NETGEAR’s UTM10 combines the VPN and Firewall strengths of its FVS336G and the FVS318G routers and adds the capabilities of a Unified Threat Management (UTM) device, providing anti-virus, anti-spam, content filtering, malware protection and Intrusion Protection.
NETGEAR has two UTM devices in their ProSecure line, the UTM10 and UTM25. The UTM10 is designed for 1-15 concurrent users and the UTM25 is designed for 10-30 concurrent users.
I used the UTM10 on my network for several weeks while writing this review, and tested as many of the key features as possible. Prior to reviewing the UTM10, I reviewed SonicWall’s TZ100W UTM, so I’ll be referring to my experience with the TZ100W and comparing it to the UTM10. I’ll also refer to my reviews of the FVS336G and FVS318G. With that said, let’s take a look at the UTM10!
Under the Covers
The UTM10 is enclosed in NETGEAR’s business gray metal covering. It’s rack mountable, but the hardware for rack mounting isn’t included. The box is larger than most four port routers I’ve tested, measuring 13” wide x 1.7” high x 8.2” deep. By comparison, NETGEAR’s FVS318G, an 8 port VPN router, is just 7” wide and 5” deep.
12/9/09: RAM size corrected
Figure 1 shows the UTM10’s innards. Under the large passive heatsink on the right is a Cavium CN5010 single core 500Mhz Octeon Plus Secure Communications Processor. Just to the left of the CPU are four RAM chips with four more on the bottom of the board providing a total of 512 MB of PC667 DDR2 RAM. The one WAN and four LAN ports are provided by a Broadcom BCM53115 five port smart Gigabit switch. Data storage on the UTM10 utilizes a 2 GB Apacer Industrial grade compact flash card.
Figure 1: Inside the UTM10
The UTM10’s four Gigabit LAN ports and one Gigabit WAN ports are all on the front of the chassis (Figure 2). There is also a USB port on the front, but it doesn’t do anything at the moment. The NETGEAR manual states this USB port is intended for “future management enhancements.”
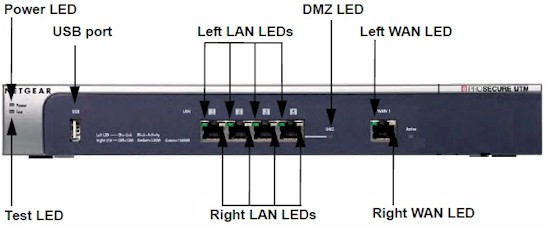
Figure 2: Front view with callouts
The rear of the device (Figure 3) is limited to the serial console port, reset button and power connection. The power supply is built into the device, thus no external power wart, a feature I like. There is an internal cooling fan, which exhausts heat out the side of the chassis. The noise level of the fan is relatively quiet. It’s louder than a laptop fan, but not offensive.

Figure 3: Rear view with callouts
Configuration
Like other UTM devices, NETGEAR’s UTM10 is a complex device with many configuration options. Overall, I found the menus intuitive and easy to work with, more so than other UTM devices I’ve reviewed. For reference, NETGEAR provides a 480 page manual accessible via the menu.
The UTM10’s menus use the same structure as the FVS318G and FVS336G. The menu has nine main sections as listed in the left column of Table 1. Each main section has three to eight subsections. Each subsection has one or more tabbed configuration pages, for a total of over 80 different pages.
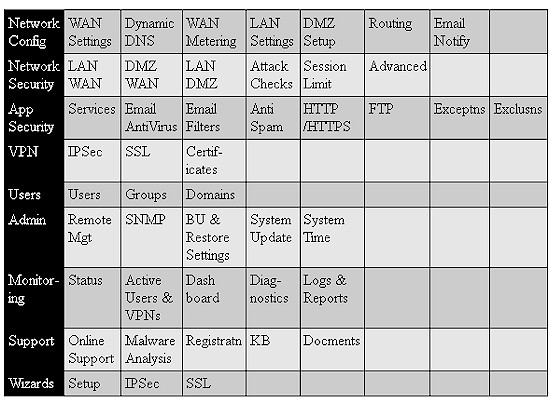
Table 1: Menu summary
At times I found myself waiting for the UTM10 to respond after applying a configuration or selecting a different configuration page. The delay wasn’t significant, but it can be frustrating for a "high performance" network device to have a slow admin interface.
Networking
The LAN and WAN ports on the UTM10 support Gigabit Ethernet so I checked for jumbo frame support. The WAN port MTU value is only adjustable from 1-1500 bytes. Jumbo frames won’t pass over the Internet, thus this feature is used to reduce the WAN MTU if necessary, such as for PPPoE connections.
The LAN ports’ MTU value is not adjustable on the UTM10. I tested for jumbo frame capability anyway, and found the UTM10 will pass frames up to 1962 bytes, the same result I had on the FVS318G. As I stated in my review of the FVS318G, anything larger than 1500 bytes is a jumbo frame, but typical jumbo frame devices use frame sizes of 4000-9000 bytes.
I faulted the FVS318G for not including VLAN support, so I’m glad to see the UTM10 has this covered with 802.1q VLAN capability in the UTM10. Up to 255 different VLANs can be easily configured on the UTM10, and each VLAN can run a separate DHCP server for managing IP addresses on the end devices.
The LAN ports on the UTM10 are assigned by default to VLAN 1. I created VLAN 2 and assigned it to port 2 on the UTM, and set up the DHCP server to assign IP addresses on VLAN 2 in the 192.168.222.0 subnet. To verify my configuration, I connected a PC to port 2, and indeed received an IP address in the 192.168.222.0 subnet instead of the UTM10’s default 192.168.1.0 subnet.
A best practice for VoIP devices is to place them in a separate VLAN. One reason for this practice is to apply Quality of Service (QoS) configurations to the VoIP traffic. In my day job, I’ve found that prioritizing VoIP traffic can have a positive impact on call performance, specifically with problems like dropped calls.
The UTM10 has the ability to apply QoS priorities to VoIP traffic flows. I created a QoS profile called VoIP and gave it high priority. I then created a firewall rule so that all outbound traffic from VLAN 2, which has IP addresses between 192.168.222.1-254, would benefit from the VoIP QoS profile.
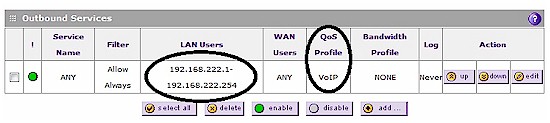
Figure 4: VoIP QoS
VPN
The UTM10 offers three VPN options: SSL Client-to-Site tunnels; IPSec Client-to-Site tunnels; and IPSec Site-to-Site tunnels. I found the UTM10’s VPN functionality and configuration options essentially the same as the VPN functionality in the FVS336G and the FVS318G.
The UTM10 supports up to 5 SSL Client-to-Site tunnels. NETGEAR lists Windows 2000 / XP / Vista (32bit), and Mac OS X 10.4+ as supported operating systems for the SSL VPN Client.
The UTM10’s SSL VPN is nearly identical to the the FVS336G’s, with the exception that the UTM10 is easier due to a new SSL VPN configuration Wizard. With this new wizard, I had no problem setting up an SSL VPN connection with a Windows XP Pro PC.
Unchanged from the FVS336G, but worth repeating, is NETGEAR’s SSL VPN options of Split Tunnel or Full Tunnel mode. Split tunnel mode, the default, means SSL VPN clients will route only the traffic you specify over the VPN Connection based on the subnets on the UTM10 you specify. Full tunnel mode means SSL Clients will route all traffic over the VPN Connection.
Split tunnel mode requires a few more configurations, while Full Tunnel mode can result in slower client web surfing and/or greater bandwidth consumption of the UTM10’s WAN connection. Further, with the addition of VLAN capability to the UTM10, Split Tunnel mode has more utility, since it allows for configuring which VLANs will be accessible to SSL VPN clients.
The UTM10 also supports IPSec Client-to-Site tunnels. I covered NETGEAR’s IPSec client VPN functionality in my review of the FVS318G, and I found the UTM10’s menus and configuration options the same as the FVS318G.
12/9/09: VPN Client correction
Our UTM10 sample wasn’t in retail packaging, so didn’t include a single NETGEAR IPsec client license. But product you buy will come with a single license.
Interestingly, the UTM10 doesn’t include IPSec client software or licenses. Obviously, NETGEAR is steering UTM10 customers toward the SSL client. I agree with this direction, as the SSL client is easier to use and configure than the IPSec client on both the PC and router.
The UTM10 supports up to 10 IPSec Site-to-Site tunnels. As in my reviews of both the FVS336G and FVS318G, I had no problem setting up Site-to-Site tunnels to other NETGEAR devices, as well as to the recently reviewed SonicWall TZ100W, shown in Figure 5. I set up the tunnel using 3DES encryption, but DES, AES-128, AES-192, and AES-256 encryption are also supported.
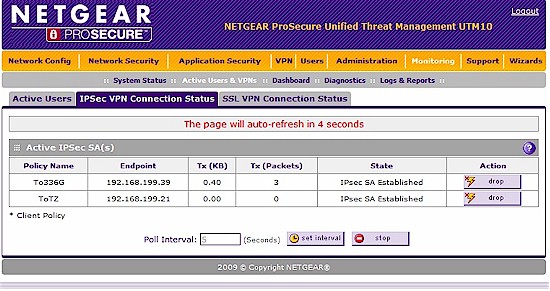
Figure 5: Site-to-site VPN setup
Security – Overview
NETGEAR utilizes what it calls “Stream Scanning Technology” for traffic flow security. This technology allows the router to receive, scan and deliver data via separate threads, similar to multi-tasking in a computer. Instead of waiting for an entire file to be received before scanning, Stream Scanning Technology analyzes data as it enters the router. NETGEAR claims this Stream Scanning Technology enables file scanning at up “five times faster than with traditional anti-virus solutions.” We’ll cover throughput on the UTM10 further on in this review.
Like most other UTM products, NETGEAR’s UTM10 leverages technology from multiple partners. It is refreshing that NETGEAR is forthcoming and proud of these partnerships. Other UTM vendors don’t as readily disclose all their underlying partnerships. NETGEAR lists security partners Commtouch, Sophos, and Mailshell on their ProSecure Technology Partners page with links to each supplier. (Kapersky Labs is also listed as a partner, but their technology is used in the higher end NETGEAR STM devices, not the UTM devices.)
For content filtering, NETGEAR uses an “in the cloud approach” based on technology from Commtouch. This “in the cloud” technology allows NETGEAR to receive data feeds from service providers throughout the world to build a database of millions of classified URLs as depicted in the Figure 6.
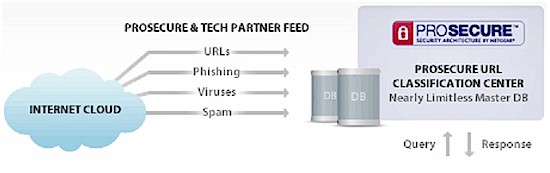
Figure 6: UTM and Partner Feeds
The UTM10’s anti-virus functionality leverages the Sophos engine and signature database containing over 1 million virus signatures. Virus updates are automatically sent from Sophos to NETGEAR’s update servers. By default, the UTM10 polls NETGEAR’s update servers every hour to ensure it can recognize the latest virus signatures.
Unlike the TZ100W, which can enforce PCs to run client anti-virus software, all scanning happens at the UTM10, so PCs are not checked or required to run anti-virus software. But good security practice should still include running anti-virus and anti-malware applications on each LAN client, because not all bad stuff comes from the Internet!
The UTM10’s anti-spam is based on technology from Mailshell. Mailshell also provides the master database of email signatures for spam filtering. In addition to partnerships with Commtouch, Sophos, and Mailshell, the UTM10’s Intrusion Detection and Prevention capability utilizes the open source solution, Snort.
Security – Email
For email traffic to be filtered, the data flow has to be identified as email. Out of the box, the UTM10 monitors SMTP, POP3, and IMAP traffic on the default ports of 25, 110, and 143. Additional ports can be monitored, with the exception of SMTP over SSL using port number 465, POP3 over SSL using port number 995, and IMAP over SSL using port number 993. Of note, Google email uses port 995, which I’ll touch on shortly.
Email filtering on the UTM10 is done by checking to see if it the email is spam, then checking for malware. Even if an email passes the spam checks, it is still checked for malware. (Malware is a general term referring to viruses, worms, trojan horses, spyware, and other malicious and unwanted software.)
Emails are filtered for spam using four separate tools in the following order; whitelists, blacklists, real-time blacklists, and NETGEAR’s Spam Classification Center. This order is important for throughput capability. If an email sender is listed in a whitelist, it will not be checked further for spam, speeding up the filtering process.
Real-time blacklists are third party services who maintain databases that can be queried for known spam senders. The UTM10 comes with the option to check emails against databases maintained by real-time blacklist services from Spamhaus, and spamcop. Additional real-time blacklist providers can also be configured.
If an email passes the the spam whitelist, blacklist, and real-time blacklists, it still has to pass the database at NETGEAR’s Spam Classification Center, which houses the Mailshell technology for identifying spam.
NETGEAR reports that the ProSecure UTM series employs a “hybrid in-the-cloud approach” for spam analysis. This approach looks at both the content and header of emails for spam determination. This is advantageous, as looking only at email headers or relying purely on real-time blacklists may result in false positives/negatives.
Once an email is cleared as not being spam, it is inspected against the Sophos database for the presence of malware, and against any manually configured filters based on keywords in the subject line and by file attachments based on size and/or extension.
Inbound and outbound emails that pass the UTM10’s filters can be tagged with a message indicating they have been scanned and are clean. Inbound and outbound emails that do not pass the UTM10’s filters can be blocked, pass and have the offending attachment deleted, or logged. Further, the sender or receiver or both can be notified by email if the message was blocked or otherwise altered.
As mentioned previously, Google’s Gmail uses port 995 for inbound POP3 email. Most ISPs use port 110 for inbound POP3 email. I tested the UTM10 with my ISP and Google email addresses. Emails to and from my ISP account were tagged with the below message:
“No malware was found: NETGEAR ProSecure Web and Email Threat Manager has scanned this mail and its attachment(s).”
Emails to and from my Gmail account were not tagged, regardless of what ports I enabled on the UTM10. Obviously, the UTM10 does not provide protection for Gmail accounts. On the other hand, my ISP-provided email account was filtered by the UTM10. Thus, it is important to know what ports your email uses to ensure it is being filtered by the UTM10.
How Effective?
It is important to note that verifying the threat mitigation and protection effectiveness of UTMs is difficult and best done by experts in the field. I don’t claim to be such an expert. Even the most basic of tests are relatively useless today. I used to test anti-virus solutions by sending an email with a known virus attachment (eicar.org) from an unprotected computer. However, both my ISP and Gmail accounts now filter the eicar.org malware, defeating this test.
NETGEAR provided us with the following information, from testing they commissioned and paid for. (I paraphrased the below, the full content is available here.)
“Testing by a partnership of AV-Test GmbH and The Tolly Group, premier independent IT test labs, focused on the ability of the solution to stop malware and viruses. The tests measured security effectiveness against 3,583 virus and malware samples from the WildList Organization International’s latest list of viruses “propagating in the wild” and 60,000 zoo malware samples from AV-Test GmbH.”
“The results were as follows:
- ProSecure — blocked 100 percent of WildList samples and 90 percent of zoo malware samples
- Fortinet — blocked 81 percent of WildList samples and 29 percent of zoo malware samples
- SonicWALL — blocked between 75 to 81 percent of WildList samples and 35 to 70 percent of zoo malware samples, depending on model
- Watchguard — blocked 32 percent of WildList samples and 20 percent of zoo malware samples
- More details on the results and the testing methodology can be found here.”
It’s obvious why NETGEAR is proud of this data. They show that NETGEAR’s UTM technology is 90-100% effective on blocking viruses and malware, while their top competitor is only 70-81% effective. But again, you’ll have to take NETGEAR (and Tolly and AV-Test’s) word for it, since I have no way of independently verifying these claims. It should be noted that Sonicwall did not submit its TZ100 to similar testing.
Security – Web
For web traffic to be filtered, the data flow has to be identified as web traffic. Out of the box, the UTM10 monitors HTTP, HTTPS and FTP traffic on the default ports of 80, 443, and 21. Additional ports can be easily added for monitoring.
The UTM10 automatically filters web traffic for malware as it does for email, and has additional configuration options. Basic configurations include whitelist, blacklist and keyword filtering. More detailed configurations include category based filtering, embedded object filtering on sites using ActiveX, Java and Flash, as well as file type filtering.
Whitelists and blacklists can be useful to allow specific sites that are blocked via a category based filter or block specific sites that are allowed via a category based filter. For example, selecting the filtering category to sports will block espn.com. End users will see a web page with a banner as shown in Figure 7 below. If you wish to allow espn.com but block all other sports websites, setting the filtering category = sports and entering espn.com in the whitelist does the trick. The “*” wildcard is available, so a whitelist entry of *espn* would allow all websites with “espn” in the URL.
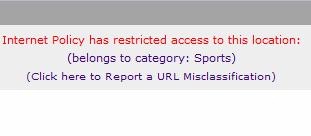
Figure 7: Blocked message
As a side note, sports websites may seem innocuous, but during several times of the year, such as March Madness, web traffic to sports websites can consume excessive resources on a company’s network. Multiple end users streaming video highlights of their favorite college basketball team can consume a lot of bandwidth!
Keyword blocking is also manually configurable. For example, I entered all seven of George Carlin’s famous “Words You Can Never Say on Television” in the keyword blocking section. This was a rather entertaining test, but effective. Once enabled, websites containing any of the listed words in text were blocked by the UTM10.
Category filtering on the UTM10 is hierarchical, with 12 main categories. The main filtering categories are Commerce, Drugs and Violence, Education, Gaming, Inactive Sites, Internet Communication and Search, Leisure and News, Malicious, Politics and Religion, Sexual Content, Technology, and Uncategorized. Each main category has 2 to 14 subcategories, for a total of 64 different category filtering options.
Category filtering blocks websites that have been categorized in the NETGEAR Classification database, depicted back in Figure 6. As with the SonicWall TZ100W and other UTM products I’ve reviewed, category based filters can be easily defeated. With the category pornography selected for content filtering, the UTM10 blocks browsing to adult sites. However, simply typing porn xxx in a search on Google.com and clicking the images option displays adult images which should be blocked.
There is an interesting list of websites known to be infected with malware, located at safeweb.norton.com/dirtysites. So to perform a rudimentary test, I tried to browse several of the websites on the list. Many of them triggered either the content filter or the George Carlin keyword list. But the first one, 17ebook.com, triggered the UTM10’s malware filters which gave me the message in Figure 8.
The Norton page itself is perfectly safe to load.
![]()
Figure 8: Malware message
Additional web security options include filtering embedded ActiveX, Java, or Flash objects within web sites. This option is applied even on whitelisted URLs. I enabled the embedded object filtering option and then tried browsing web sites that utilize Flash.
Stattracker, a handy web page for Yahoo! Fantasy Football is a good test, since it uses Flash technology. With Flash filtering enabled, Stattracker failed to load; only a blank page would come up. Note that, according to NETGEAR, pages that aren’t entirely Flash (or Java or ActiveX) based, will display and just the objects will be blocked.
HTTP file downloads can also be filtered based on extensions, such as.exe for executables and media files like.mpg and.mp3. Additional file extensions are easily added in the content filtering menu.
NETGEAR also provides useful tools for content filter management, including traffic logging, filter scheduling, a lookup tool to determine a URL’s category, and a reporting tool to suggest reclassification of a URL.
To determine a URL’s classification, and thus determine if it would be filtered by the UTM10, simply enter the URL in the web category lookup tool. As shown in Figure 9, smallnetbuilder.com is classified under Computers&Technology, and access to this website would be blocked if this category was selected for filtering.
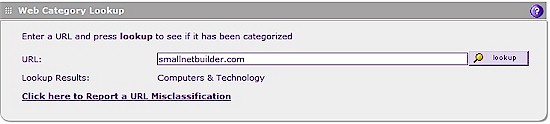
Figure 9: Web Category Lookup
Note the link in Figure 9 labeled “Click here to Report a URL Misclassification.” This link allows for reporting a URL that may be misclassified. I tried this link, reporting a domain which was registering as “Computers & Technology” and recommended it be classified as “Information Security.” I received a message stating “The Web page that you entered is currently under review. It will be analyzed in the next 24 hours and if the classification is found to be incorrect it will be fixed.” I checked back after the recommended 24 hours, but the domain was still listed as “Computers & Technology.”
In addition to Email and Web traffic filtering, the UTM10 can filter FTP traffic for malware, size and extension type. Further, the UTM10 can be configured to pass or block traffic generated by Instant Messenger (IM) and Peer-to-Peer (P2P) traffic services. IM services that are monitored include Google, Yahoo, mIRC, and MSN. Note, however, that Skype traffic can’t be blocked. PSP services that are monitored include BitTorrent, eDonkey, and Gnutella.
Security – Network
In addition to the protection offered by the UTM10’s Email and Web filters, the UTM10 has a full-featured firewall. The functionality of the firewall is very similar to that on the FVS318G and FVS336G, but the Intrusion Protection (IPS) is new. NETGEAR takes a more economical approach for IPS, incorporating technology from the open source solution, Snort.
The UTM10’s IPS functionality is more basic than other UTM devices I’ve reviewed. For example, SonicWall’s TZ100W detects 48 different categories of possible network intrusions, whereas the UTM lists a total of 6. Once detected, intrusions can be either dropped or an alert can be sent.
Although basic, I verified the UTM10 is monitoring activity on the WAN port. I set up my UTM10 to send an alert email on possible Intrusion activity, then deliberately ran a port scan on the WAN interface of the router to generate an Intrusion condition. Almost immediately, I received the following email alert:
At time : 2009-11-22 09:00:03
Intrusion Prevention System of UTM detected : TCP Portscan.
Target host IP : 16.2.18.35
Number of ports which scanned in target host: 1663
The port range scanned in target host : 3:65389
The number of active attack connection : 1700
The attacker IP : 16.8.15.18
Reporting
The UTM10 has a wide array of reporting capabilities including log files, daily and weekly reports and security alerts. I’m going to cover a few of them to give the general idea.
I configured my UTM to send emails on all activity, and I got an email every day containing both the UTM10’s service and system logs. The service logs contained text entries regarding successful security database updates and sending of notifications. The system logs contained text entries generated by traffic that is meant for the UTM, by traffic that is routed or forwarded through the UTM, and by running systems such as NTP and activity on the WAN interface.
I found the Daily and Weekly Reports generated by the UTM10 interesting. The reports are sent in a zip file as an attachment to an email. These reports provide hourly details on Web, Mail and System transactions, broken down by protocol. For example, the Daily Web Report shows the hourly HTTP traffic counts as shown in Figure 10.
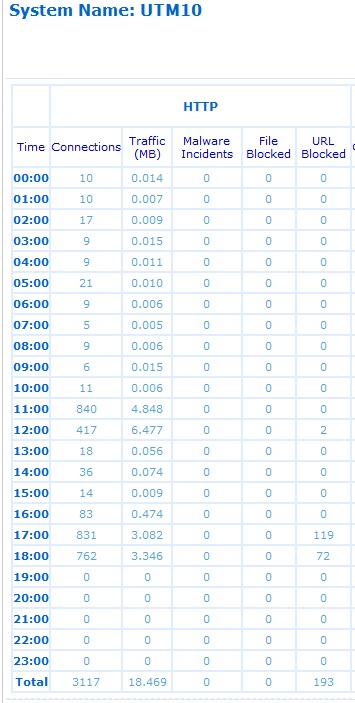
Figure 10: Daily Web Report
In the above report, you can see there were 762 HTTP connections between 18:00 and 19:00, using 3.346 MB of bandwidth. During that same hour, 72 URLs were blocked by the UTM10.
The daily report presents the data numerically and graphically. In addition to the above data, there are graphs for each protocol by hour. The corresponding HTTP graph to Figure 10 is shown in Figure 11. As you can see, the high traffic hours depicted on this graph were 12:00 and 18:00.
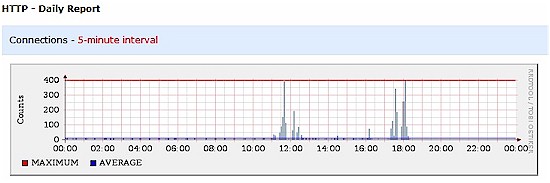
Figure 11: HTTP traffic graph
SMTP and POP3 traffic is reported in the Daily and Weekly Mail reports in similar fashion. An additional statistics report is available to examine highest traffic generating source and destination IP addresses.
Another reporting feature I found useful is the UTM10 is the Status screen. Immediately presented when you log in and continuously available on the Monitoring-System Status menu is a useful dashboard presenting real time CPU, Memory and Disk utilization, the status of the Web and Email protocol monitors, and key licensing information for the security services, shown in Figure 12.
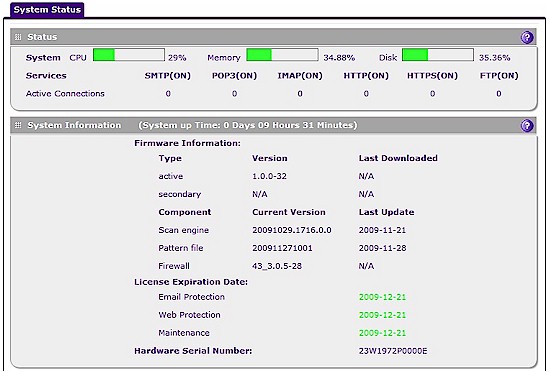
Figure 12: System status
Another nice display within the UTM10 is the real-time security dashboard, updated every 30 seconds, which shows the running total of Email, Web, IM/P2P and Network events. Figure 13 shows the numerical output of this dashboard. This security dashboard on the UTM10 also provides graphical displays of threat types, counts of most recent and top threat types, and detailed statistics on each of the 6 key protocols monitored by the UMT10 (HTTP, HTTPS, FTP, POP3, SMTP, IMAP).
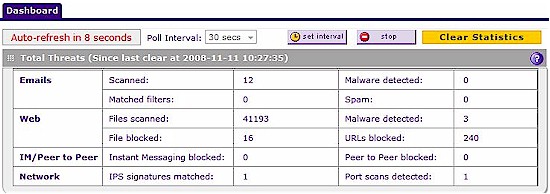
Figure 13: Real-time security dashboard
Lastly, there are five types of security alerts on the UTM10: Failure to Update; Malware Detected; Malware Threshold Exceeded; IPS Detected; and IPS Threshold Exceeded. The Malware and IPS threshold alerts are configurable for the number of violations per time period. The default is two Malware or IPS Attacks within 10 minutes will send an alert. The Alerts are emails indicating the offending condition, such as the IPS Alert I covered in back in the Security – Network section.
Performance
I tested network throughput and VPN throughput on the UTM10 using jperf with its default settings as my TCP/IP throughput measurement tool. I used two physical laptops with a measured minimum throughput of 310 Mbps as my endpoints.
In my original throughput tests, I left IM and P2P features enabled, which negatively impacts the UTM’s throughput. Subsequently, I under-reported the UTM10’s maximum throughput, which you can now see in the revised Table 2 is 76 – 96 Mbps with all filtering disabled.
I tested outbound (LAN-WAN) and inbound (WAN-LAN) network throughput with the UTM10’s traffic filtering enabled and disabled. I took four different throughput measurements: no UTM protection (All Off), just Intrusion Protection (IPS On), just Email/Web protection (Email/Web On), and finally with both Intrusion and Email/Web protection (All On).
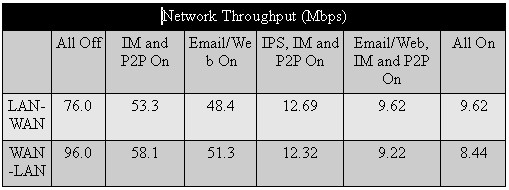
Table 2: Network throughput
Table 2 shows that enabling all of the UTM10’s bells and whistles knocks throughput down around 90%. But the 8 – 10 Mbps of remaining bandwidth should still handle many small business DSL and cable-based Internet connections. However, if you have fiber-based service, the UTM10 would not be a good choice.
I also tested VPN throughput over an IPSec Site-to-Site tunnel and over a SSL Client-to-Site tunnel. I used the 3DES VPN tunnel between the UTM10 and the TZ100W I described earlier. I tested VPN throughput in the same manner I tested network throughput, with no UTM protection (All Off), just Intrusion Protection (IPS On), just Email/Web protection (Email/Web On), and finally with both Intrusion and Email/Web protection (All On). My VPN throughput results are in Table 3.
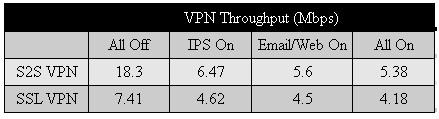
Table 3: VPN throughput
The row labeled S2S VPN in Table 3 shows my throughput results over the IPSec Site-to-Site tunnel. while the row labeled SSL VPN shows my throughput results over the SSL Client-to-Site tunnel.
The results show a 70% throughput reduction in the IPsec tunnel with all UTM features enabled and a 45% drop with an SSL client connection.
What’s the takeaway here? With all security features enabled, expect 8 -10 Mbps throughput to and from the Internet. Further, with all security features enabled, expect about 5 – 6 Mbps throughput over a Site-to-Site IPsec VPN tunnel and about 4 – 5 Mbps throughput over an client SSL VPN tunnel.
Competition and Pricing
NETGEAR considers SonicWall and Fortinet to be competitors in the UTM space. I haven’t reviewed the Fortinet product, so I’ll focus on comparing the UTM10 and SonicWall TZ100W.
Both the NETGEAR and SonicWall use Cavium Networks CPUs, with the UTM10 using a Cavium 500 Mhz Octeon and the TZ100W, a Cavium 300 MHz Octeon. In my testing, it appears that SonicWall got significantly more bang for the buck from their less-powerful CPU.
Table 4 shows that the TZ100W has higher throughput than the UTM10 with all UTM features on. And while enabling all the UTM10’s UTM features takes an ~90% toll on throughput, it reduces the TZ100W’s by only about 60%. But I’m sure NETGEAR would argue that the difference is due to the UTM10’s more comprehensive threat protection.
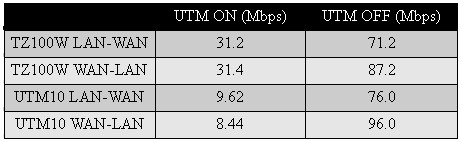
Table 4: UTM Throughput comparison
Clearly, the SonicWall TZ100W has throughput advantages over the NETGEAR UTM10. However, pricing is also a key factor in choosing a network device. NETGEAR makes it easy to figure out your costs on the UTM10. Instead of selling the device and subscriptions separately, the UTM10 is available with a simple all-inclusive bundle list price of $720. Included in the bundle are the router, 1 year subscriptions for Intrusion, Web, and Email protection, along with 24/7 maintenance and support. This UTM10 bundle is available via on line retailers for under $500.
To pull it all together, I’ve listed some of the key attributes of both products in Table 5. Networking strengths for the UTM10 include Gigabit Ethernet ports and VLAN capability, while the TZ100W has dual WAN and wireless capability. Both support up to 5 SSL VPN connections, but the UTM10 has capacity for ten Site-to-Site VPN tunnels compared to the TZ100W’s five.
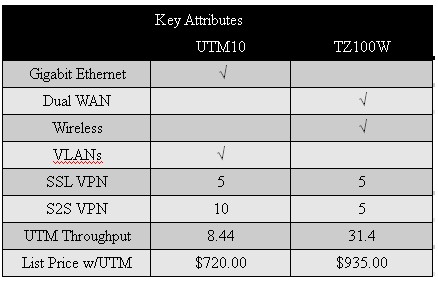
Table 5: Competitive summary
The TZ100W has a significant advantage in speed with all UTM features enabled; 31.4 Mbps to the UTM10’s 8.44 Mbps. And finally, the UTM10 has a list price of $720 vs. $935 for the TZ100W with 1 year subscriptions for all services included with both.
Closing Thoughts
NETGEAR’s UTM10 and SonicWall’s TZ100W can both provide small businesses with security features previously available only to deep-pocketed larger businesses. But each company has chosen its own mix of features that may make your choice a difficult one.
Sonicwall has equipped the TZ100W with more networking features, including dual WAN ports and 802.11n wireless, where NETGEAR has opted for no wireless and a single WAN port. Sonicwall has also focused on providing a higher-throughput product, with almost 4X the speed of the UTM10 with all UTM features enabled. And finally, Sonicwall’s solution includes anti-virus and anti-malware apps for client PCs and ensures that they are running and updated, while NETGEAR has no equivalent client AV / malware solution.
But NETGEAR’s focus is clearly on establishing its bona fides in the area that matters most in a UTM appliance – threat mitigation. Although commissioned and paid for by NETGEAR, the Tolly / AV-Test study shows the UTM10’s superior effectiveness in blocking virus and malware threats. And in the absence of any contradictory data from Sonicwall, those results stand.
As I noted earlier, it’s beyond my ability to adequately judge any product’s UTM effectiveness. But I can judge features and ease of use and I have to say that I was impressed with the UTM10 on both counts.
12/9/09: Clarified conclusion
In the end, I’m a network guy and I consider performance to be very important in product selection. So, if it were my job to select a UTM device to protect my organization’s network from security threats, I’d pick the UTM10 over the Sonicwall TZ100W.

