
| At a glance | |
|---|---|
| Product | PepLink Balance (20) [Website] |
| Summary | Dual WAN router supporting link aggregation, balance and auto-failover. |
| Pros | • Helpful & responsive phone support with no support contract • USB WWAN port with broad modem support • Very quick failover |
| Cons | • Low VPN performance • No VLAN support • Relatively expensive considering its feature set |
Typical Price: $299 Buy From Amazon
Introduction
As you log into the Peplink Balance 20, you are presented with a simple screen requesting a user name and password. In the upper left is the Peplink logo, along with the slogan “Protecting Business Continuity.” This slogan describes Peplink’s intent for its Balance routers.
Businesses rely on continuous connectivity to the Internet. Businesses also rely on continuous connectivity to other locations, often facilitated through VPN tunnels. Peplink has nine multi-WAN VPN routers focused on providing continuous connectivity. The Peplink Balance routers allow you to use multiple Internet connections and VPN tunnels to maintain network connectivity, even if one of your Internet Service Providers goes down.
Below is a chart listing Peplink’s Balance routers and a few basic stats to help identify each model’s target network. The Balance 20 and 30 are targeted at power users and home office users, while the 210/310 are targeted at small business. The 305/380/580 are targeted at mid-size business and the 710/1350 are targeted at large enterprises.
| Model | WAN Ports | Throughput Rating (Mbps) | Recommended Maximum Users |
|---|---|---|---|
| 20 | 2 | 100 | 25 |
| 30 | 3 | 100 | 25 |
| 210 | 2 | 100 | 50 |
| 310 | 3 | 100 | 50 |
| 305 | 3 | 200 | 500 |
| 380 | 3 | 200 | 500 |
| 580 | 5 | 400 | 1000 |
| 710 | 7 | 800 | 2000+ |
| 1350 | 13 | 1500 | 5000+ |
Table 1: Peplink Balance models
Clearly, as the model numbers increase, so do the number of WAN ports, throughput capability and number of recommended maximum users. Supported features also increase with the model numbers. For example, features such as Drop-In Mode, SpeedFusion, RADIUS support, Access Point support, Application Prioritization, advanced bandwidth controls, and content filtering are available only in the higher model numbers. To see which features are available on which model, take a look at the Peplink’s complete Balance model comparison chart.
As a basis for comparison, I last looked at a router from Peplink in my review of the Balance 30 back in 2008.
Inside
The Balance 20 is housed in a black metal case measuring 1.4" x 10" x 5.2". The metal enclosure gives a higher quality impression than the black plastic case I encountered in the old Peplink 30 review. The power supply is external. Cooling is passive so the device is silent.
On the front is one USB 2.0 port, four Gigabit Ethernet LAN ports, two Gigabit Ethernet WAN ports, a reset button, and a status and power LED, all shown below.
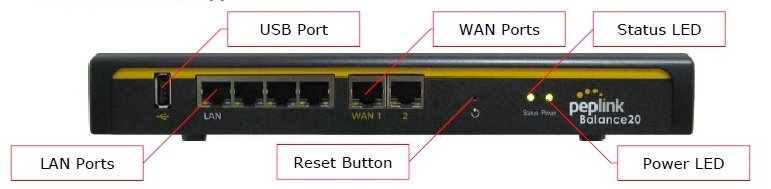
Front
The back of the device has just the power connector and a Kensington security slot to keep the device from growing legs. There is no on/off switch.

Back
The main components in the Balance 20 are an Atheros AR7161 network processor based on a 32-bit MIPS 24K core, 64 MB DDR SDRAM and a Vitesse VSC7395 5+1 port Integrated Gigabit Ethernet Switch with a Realtek RTL8110 Ethernet Controller.
| Balance 20 | Balance 30 (old) | |
|---|---|---|
| CPU | Atheros AR7161 | Micrel KSZ8695P |
| Ethernet | – LAN: Vitesse VSC7395 switch – WAN: Realtek RTL8110 |
LAN: in Micrel WAN: Realtek RTL8139D |
| RAM | 64 MB | 256 MB |
| Flash | 16 MB on board 4 GB on SD card |
64 MB (x2) |
Table 2: Balance 20 and old Balance 30 comparison
Like the old Balance 30, there are two levels of flash, 16 MB on board and 4 GB supplied by an SD card on the circuit side of the board. Here’s a photo of the board topside.
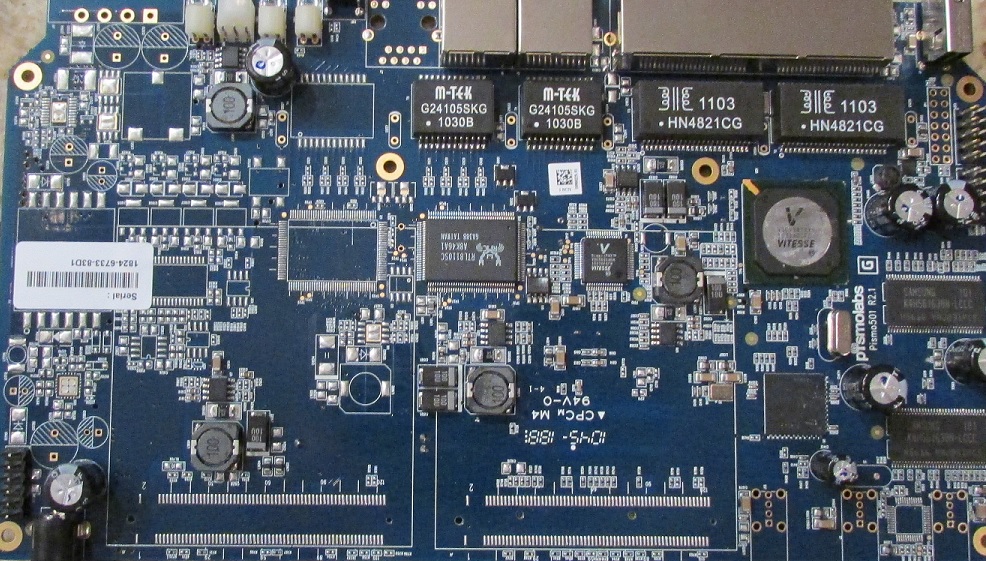
Main Board
Feature Summary
I created the feature summary below from Peplink’s Balance model comparison chart.
- (2) WAN Ports (GbE)
- (1) USB WWAN Port (supports 4G/3G modems)
- (4) LAN Ports (GbE)
- Rated Throughput = 100 Mbps
- WAN Load Balancing and Failover
- NAT/PAT
- Multiple IP Address Support Per WAN interface
- Supports up to 25 LAN Users (recommended)
- Supports up to 3 PPTP users
- Supports up to 2 Site-to-Site VPN Tunnels
- Bandwidth Usage Monitor
- QoS Controls
- SIP, H.323 ALG
- UPnP
- Dynamic DNS
A Peplink Balance feature not available on the Balance 20, but worth mentioning is Peplink’s trademarked SpeedFusion feature, which is available on the Balance 210 and above.
Peplink’s SpeedFusion bonds VPN traffic between Peplink routers over multiple WAN interfaces, effectively increasing the bandwidth available to the VPN connection, as well as increasing reliability. This is unique among multi-WAN routers I’ve tested.
Every other multi-WAN router I’ve tested will run a VPN connection over a single WAN interface that may fail over to a secondary interface if the primary interface goes down. A SpeedFusion VPN tunnel will reportedly use multiple interfaces simultaneously for the VPN tunnel and so will not be interrupted even if an interface fails, as depicted in the below image.
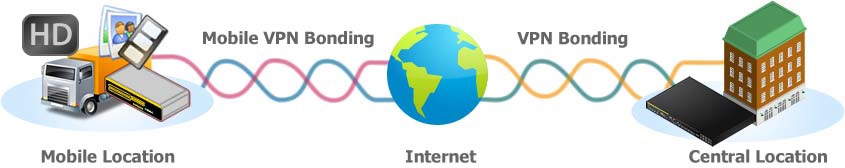
SpeedFusion
Configuration
The menus on the Balance 20 have been updated since I last looked at them in 2008. However, they still use a basic table style layout and appearance. There is a dashboard (shown below) providing a quick status of the router’s interfaces, VPN connection and device info, a setup wizard for configuring WAN interfaces and three main menu options for configuring the router.
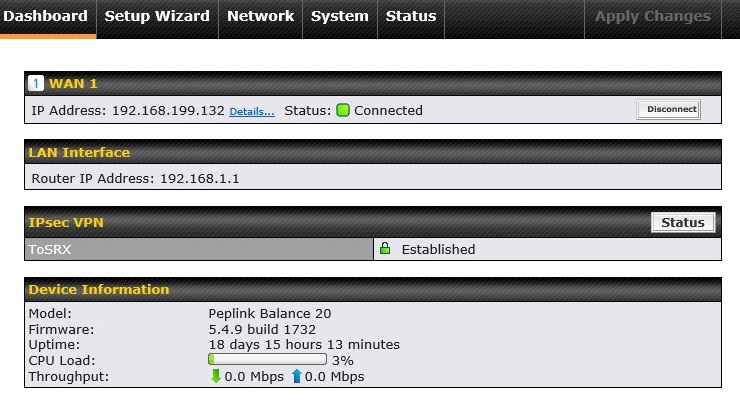
Dashboard
I’ve listed the three main menu options and their sub menus to give an idea of the configuration options available on the Balance 20.
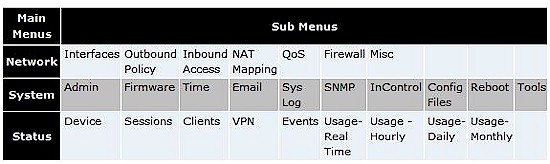
Menu summary
Although basic, the menus on the Peplink are relatively easy to figure out. If you need help, Peplink includes a “?” icon next to most configuration options, which provides instructions or information about a specific option.
Peplink also provides a 199 page manual that covers all models of the Balance product line. In addition, Peplink’s on-line knowledgebase, which directs you to the same location as their How-To section, has numerous configuration examples and explanations.
Here’s the most impressive part of Peplink’s product support. Peplink has a telephone number to call that is prominently listed on their website and answered by humans! I called the number and I only had to make the choice of pressing 1 for sales and 2 for technical support. I pressed 2 for technical support and a human answered! I wasn’t ready to speak as I was prepared to have to make more choices before I could get to a human.
I tried it a second time to ensure the first time wasn’t a fluke and got right through again! I was informed I didn’t need to have a support contract to call this number and if I had a question, they would certainly try to provide an answer. Wow, that is refreshing and unique in today’s world of automated responses!
Dual WAN
Each WAN interface can be configured in NAT or IP Forwarding mode. The IP Forwarding option allows you to use one of the WAN interfaces as a routed interface to another network without NAT, a useful option to connect to another subnet in your network.
Failover options on each WAN interface are Always-on and Backup. Always-on is the recommended setting, which keeps the interface in an up state and allows for load balancing over that interface. At least one WAN Interface should be set to Always-on.
WAN Interfaces on the Balance 20 can also be set to Backup Priority Group 1 or Group 2. A WAN Interface set to Backup Priority Group 1 would be used if the Always-on interface failed and preferred over a USB WWAN Interface configured as Backup Priority Group 2.
I ran a simple test by setting both WAN Interfaces to Always-on and set up a continuous ping to google.com. I simulated WAN outages by disconnecting one of the two WAN interfaces. Failover and fail-back was instant and seamless, there were no dropped packets!
Load balancing on the Balance 20 starts by setting the bandwidth for each WAN Interface. The Peplink manual says to use the values provided by your ISP. Another way to measure your bandwidth on your WAN interface is to run several speed tests, using public speed test sites such as speedtest.net and speakeasy.net. Once the values are entered, the Balance 20 will automatically balance traffic over your Internet connections.
You can customize load balancing by defining how specific traffic types should be balanced over WAN interfaces. Choices are to prioritize traffic types over WAN interfaces using weighted distribution, persistently routing traffic between a specific origin and destination to a specific WAN interface, directing (forcing) specific traffic to a specific WAN interface, prioritizing traffic by WAN interface from WAN 1 to WAN 2 to WWAN and by overflowing traffic to the next WAN interface as an interface reaches capacity.
As a test, I set up a simple rule to direct all web traffic over a specific WAN interface to validate traffic flow, as shown below. I then changed the rule to route web traffic from WAN 1 to WAN 2 and back. The LEDs on the front of the Balance 20 router made it clear the WAN interface I chose in my rule was the one carrying the traffic, validating the effectiveness of my simple test rule.
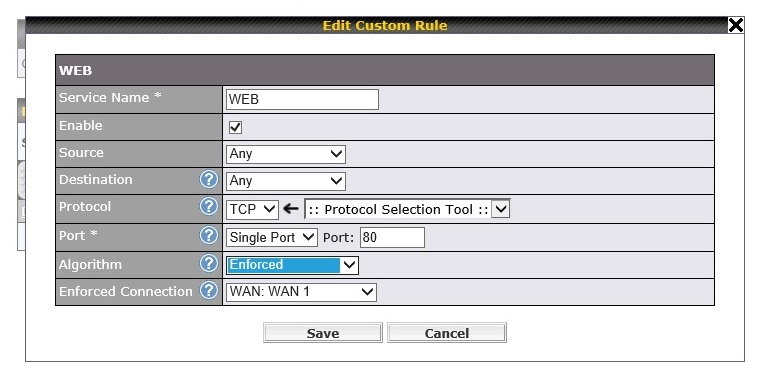
LoadBalancing Rule
WWAN
If you’re using a multi-WAN router, you’re probably doing so to ensure Internet availability. To further ensure Internet availability, Peplink Balance routers also support WWAN (Wireless Wide Area Network) connectivity via a USB 2.0 port.
WWAN connections have the benefit of being highly independent of wired connections. A backhoe or act of nature can take out wired connections. WWAN connections are less reliant on physical infrastructure and provide additional redundancy.
Peplink lists support for 183 modems on its website. Modems from most global manufacturers and carriers are represented in this list. Other than Cradlepoint’s MBR900, I don’t think I’ve tested another router that has as many supported USB modems.

Supported Modems
LAN
LAN options on the Balance 20 are pretty standard. The Balance 20 provides a DHCP server and provides DNS and WINS IP addresses via DHCP. The Balance 20 also supports DHCP reservation, static routing, and DNS Proxy.
However, 802.1q VLANs are not indicated as supported on the Balance 20 LAN interface, nor are they listed in the specs of any of the higher end Balance models, which I find surprising. For my money, I’d like to see 802.1q VLAN support in a business grade router. Peplink tells us, however, that VLAN support is currently in beta and coming in a future firmware update.
VPN
The Balance 20 will support two IPsec site-to-site tunnels and three PPTP tunnels. Peplink’s documentation says it supports VPN site-to-site tunnels to Peplink, Cisco, and Juniper routers. No other brands are listed as supported. Nevertheless, I had no problem setting up an IPsec site-to-site tunnel to a Netgear SRX5308.
Shown below is a screen shot of my IPsec connection from the Balance 20 to the SRX5308. I found Peplink’s VPN configurations pretty straightforward. My guess is an IPsec tunnel could be established with other brands as well.
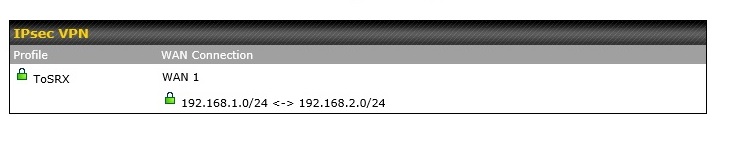
IPsec Status
Interestingly, Balance routers do not support client IPsec tunnels. Thus, the only option for remote client VPN access to a Balance router is via a PPTP tunnel. This approach has pros and cons.
The pro to PPTP tunnels is simplicity. PPTP client software is included in Windows, Mac OS X, iPhones and Android smartphones. PPTP configuration is quite simple. On the Balance 20, all you have to do is enable PPTP and create a user name and password. On the end device, you create a PPTP connection and enter the user name and password.
I had no problem establishing a PPTP connection to the Balance 20 from a Windows 7 and Windows 8 PC, a Mac OSX PC, and an iPhone. Below is a screen shot where I have a Windows PC and an iPhone both connected to the Balance 20 via a PPTP connection.
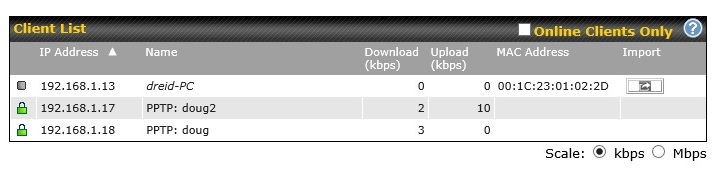
PPTP Status
The con to PPTP tunnels is security. PPTP is considered less secure than IPsec. However, the most secure solution isn’t all that valuable if you can’t get it to work and IPsec client software can be difficult to configure and may not be available across all platforms.
I tested the Balance 20’s VPN performance with iperf using default TCP settings, with a TCP window size of 8KB and no other options. I ran iperf on two PCs, one running 64-bit Windows 7 and the other 64-bit Windows 8 with their software firewall disabled. (Running a simple iperf throughput test between two PCs uses the command iperf -s on one PC and iperf -c (ip) on the other PC.)
I tested IPsec site-to-site VPN performance between the Balance 20 and the NETGEAR SRX5308, a router I typically use for site-to-site IPsec tunnel testing. I measured IPsec throughput with both 3DES and AES-256 encryption. (Peplink advertises their SpeedFusion feature with AES-256 encryption, so my thought is the Balance routers are optimized for AES encryption. The results seem to support that theory.) I tested PPTP VPN performance using my Windows PCs as described above.
| Peplink Balance 20 VPN Throughput Performance (Mbps) | ||
|---|---|---|
| Tunnel Type | WAN-LAN | LAN-WAN |
| PPTP | 13.3 | 13.4 |
| Site to Site IPsec (3DES) | 8.68 | 8.45 |
| Site to Site IPsec (AES-256) | 14.0 | 13.1 |
Table 4: VPN throughput
I was surprised by the Balance 20’s low VPN throughput. Peplink didn’t provide VPN ratings for the Balance 20, yet I thought they’d be higher. As you can see in Table 5 comparing multi-WAN VPN routers, the Balance 20’s VPN performance for both IPsec and PPTP is lower than all other multi-WAN VPN routers I’ve tested.
| IPsec Throughput (Mbps) | PPTP Throughput (Mbps) | |||
|---|---|---|---|---|
| Product | LAN-WAN | WAN-LAN | LAN-WAN | WAN-LAN |
| Peplink Balance 20 | 13.1 | 14.0 | 8.45 | 8.68 |
| TP-LINK TL-ER6020 | 41.9 | 40.0 | 30.0 | 34.6 |
| Cisco RV042 | 37.1 | 47.5 | 10.8 | 9.7 |
| Draytek 2920 | 17.8 | 17.8 | 19.9 | 19.9 |
| NETGEAR SRX5308 | 31.8 | 42.6 | NA | NA |
Table 5: VPN throughput comparison
Firewall
The Balance 20 uses a rule-based firewall with separate inbound and outbound rules. Both directions allow you to specify both source and destination ports and allow / deny as shown in the screenshot below. Inbound rules also allow you to specify the WAN port it applies to.
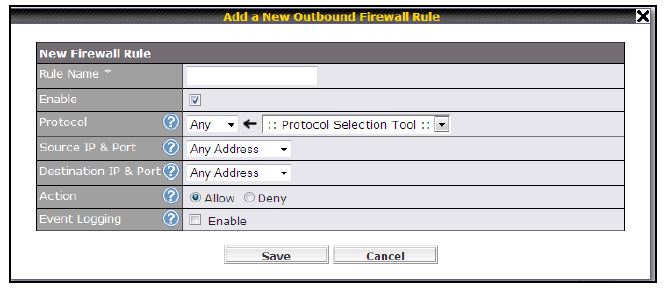
Firewall rule
The Protocol Selection Tool is just Peplink’s way of saying you can choose one of 28 pre-defined different traffic types (shown below). Or you can write your own rule setting TCP / UDP / ICMP / IP and ports.
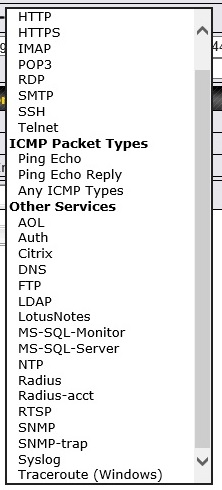
Traffic Types
There is no scheduling of firewall rules. Rule priority is established by drag-and-dropping rule positions.. All Balance models also have a enable for intrusion detection and Denial-of-Service blocking. If you want website (domain) blocking, you’ll need to step up to the Balance 305 or 380+.
QoS
The 20 and most Balance models support three-level priority-based QoS. Priorities are assigned to services as shown below, so apply to all traffic both uplink and downlink.
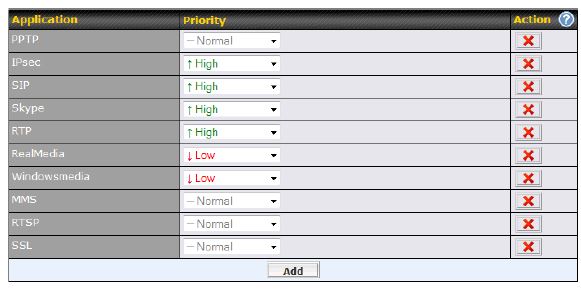
Setting QoS priority
Predefined applications include several types of video streaming (MMS, RealMedia, RTP, RTSP, Windowsmedia), tunneling traffic (IPsec, PPTP, SSL), and VoIP traffic (SIP, Skype). Custom applications can be created by DSCP values or by protocol and port.
If you again step up to a Balance 305 or 380+, you can divide LAN clients among three groups to apply bandwidth-based QoS rules to.
Routing Performance
Routing performance for the Balance 20 loaded with Peplink’s firmware version 5.4.9 and using our standard test method is summarized below. 14,983 simultaneous connections should be more than enough for 25 users!
| Test Description | Peplink Balance 20 |
|---|---|
| WAN-LAN (Mbps) | 103 |
| LAN-WAN (Mbps) | 94 |
| Total Simultaneous Throughput (Mbps) | 102 |
| Maximum Simultaneous Connections | 14,983 |
| Firmware Version | 5.4.9 build 1732 |
Table 6: Routing Performance summary
The IxChariot plot for the routing test shows pretty consistent throughput in the unidirectional tests, shown below.
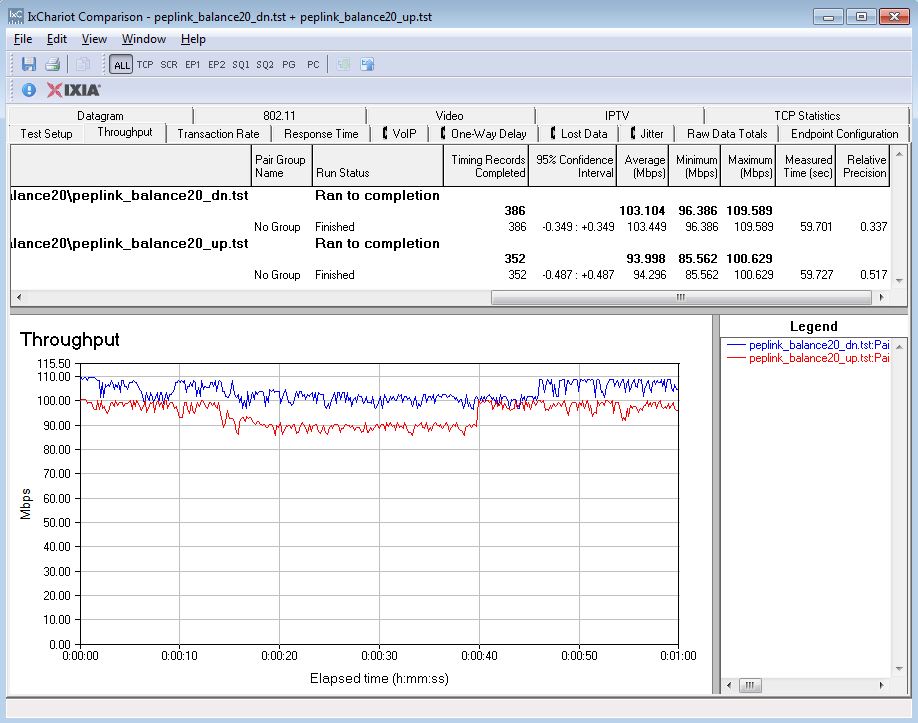
Unidirectional Throughput
Simultaneous up/downlink throughput came in at 102 Mbps. There is some variation in both uplink (45.445) and downlink (56.371) throughput as shown in the IxChariot plot below.
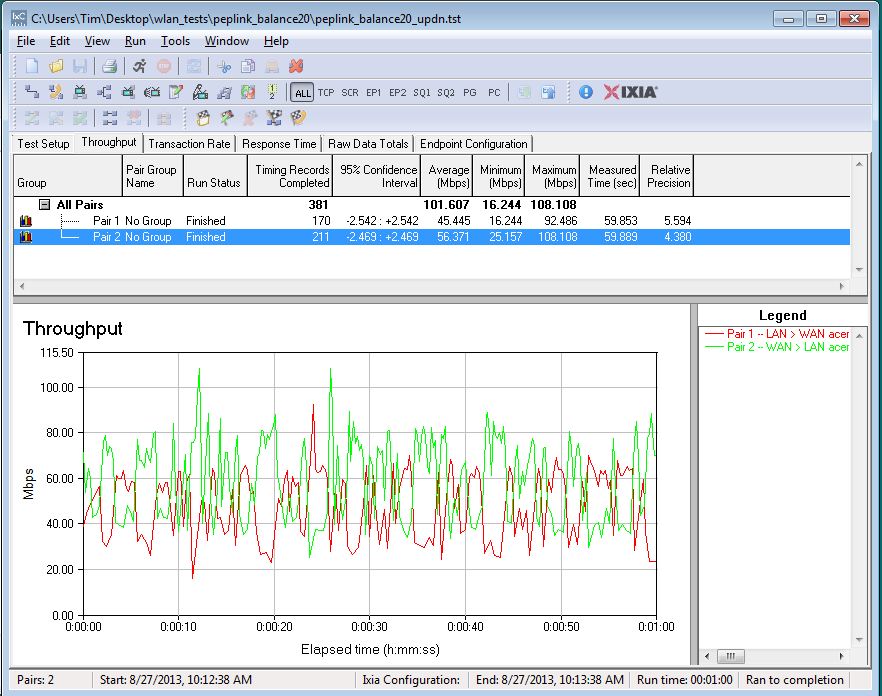
Simultaneous Throughput
Closing Thoughts
As you can see below, the Balance 20 is more expensive than most of the other dual WAN routers I’ve tested and has lower IPsec tunnel capacity. The NETGEAR SRX5308 remains more expensive than the Peplink Balance 20, but the NETGEAR is a quad WAN router. ![]()
| Product | WAN Ports | WWAN Ports | IPsec Tunnels | VLANs | Price |
|---|---|---|---|---|---|
| Peplink Balance 20 | 2 | 1 | 2 | 0 | $268.99 |
| TP-LINK TL-ER6020 | 2 | 0 | 50 | 3 (port based) | $127.67 |
| Cisco RV042 | 2 | 0 | 50 | 0 | $169.99 |
| Draytek 2920 | 2 | 0 | 32 | 0 | $189.00 |
| NETGEAR SRX5308 | 4 | 0 | 125 | 254 | $344.00 |
Table 7: Competitive comparison
Three things going for the Peplink Balance 20 are product support, WWAN support and fast failover/automatic load balancing. Not many network vendors make it as easy as Peplink to get help over the phone. (This could be part of why the Balance 20 is as expensive as it is versus its competitors.)
The Balance 20’s USB WWAN port sets it apart from the competition and provides a degree of redundancy you can’t get with a wired Internet connection.
Finally, Peplink seems to have really optimized its implementation of multi-WAN connections; the Balance 20 is seamless in distributing traffic over multiple Internet connections.
I noted in my review of the Peplink Balance 30 in 2008 that it was a bit pricey for a multi-WAN router without VPN capability. Adding VPN capability to the Balance has certainly sweetened its value proposition. Yet the Peplink Balance 20 still seems a pricey based on features and performance, particularly considering that it doesn’t support client IPsec.
The bottom line is that the Peplink Balance 20 should provide reliable, redundant routing and VPN for your home or small business if you are willing to pay a premium price.
