
| At a glance | |
|---|---|
| Product | Zyxel VPN Firewall (USG20-VPN) [Website] |
| Summary | Multi-WAN Gigabit Firewall/Router supporting IPsec, SSL and L2TP VPN and subscription UTM features |
| Pros | • Supports L2TP, SSL, and IPSec VPNs • Content Filtering and Anti-Spam protection • Zone-based firewall • WWAN USB adapter support |
| Cons | • Could not get IPsec client-to-gateway working • Routing throughput lower than most current generation routers |
Typical Price: $0 Buy From Amazon
Introduction
Update 7/29/16: Client to Site IPsec works
ZyXEL has steadily expanded its security appliance / firewall product lines. But with three different families, buyers can be easily confused.
The “Unified Security Gateways” include the USG20 (reviewed in May 2011) and USG20W. In addition to VPN and Firewall features, the USG20/USG20W also support subscription-based Content Filtering and Anti-Spam UTM (Unified Threat Management) features. The USG20W adds single-band 802.11b/g/n wireless connectivity.
The “Next-Gen Unified Security Gateways” include the USG40 (reviewed in November 2014) and USG40W. In addition to VPN and Firewall features, the USG40/USG40W also support Content Filtering, Anti-Spam, Anti-Virus, and Intrusion Detection/Prevention UTM features. The current USG40 also has an improved multi-core processor. The USG40W adds single-band 802.11b/g/n wireless connectivity.
The “VPN Firewalls” include the USG20-VPN and USG20W-VPN. The USG20-VPN offers many of the same features as the USG20, with improved performance over the USG20. The USG20W-VPN adds dual-band AC1750 802.11aa/b/g/n/ac wireless connectivity.
The key differences between these product lines are summarized in Table 1. Essentially, the USG20-VPN is a faster version of the USG20, with the addition of an SFP port. The USG40 has even higher throughput than the USG20-VPN, an optional RJ45 port that can be used as a second WAN port, plus support for Anti-Virus (AV) and Intrusion Detection and Prevention (IDP).
| USG20 | USG20-VPN | USG40 | |
|---|---|---|---|
| LAN Ports | 4 | 4 | 3 |
| WAN Ports | 1 | 1 | 1 |
| OPT Ports | 0 | 0 | 1 |
| SFP Ports | 0 | 1 | 0 |
| USB Ports | 1 | 1 | 1 |
| Mobile Broadband | Y | Y | Y |
| Firewall Throughput (Mbps) | 175 | 350 | 400 |
| VPN Throughput (Mbps) | 75 | 90 | 100 |
| Max IPsec VPN Tunnels | 5 | 10 | 10 |
| Max SSL VPN Tunnels | 1 | 15 | 15 |
| VLAN Support | Y | Y | Y |
| Anti-Virus | N | N | Y |
| Intrusion Detection and Prevention | N | N | Y |
| Anti-Spam | Y | Y | Y |
| Content Filtering | Y | Y | Y |
| High Availability | N | Y | Y |
| Bandwidth Management | Y | Y | Y |
Table 1: Model comparison
With that out of the way, let’s dig into the USG20-VPN.
The USG20-VPN has the same look as the USG20 and USG40. Its gray metal enclosure with red trim measures 8.5″x5.63″x1.3″. It comes with an external power supply and adhesive rubber feet for desktop use. It is passively cooled, so runs silently. The USG20W-VPN is physically the same, with the addition of three external antennas.
The front of the USG20-VPN has a reset button, power, system, SFP and RJ45 status LEDs and USB 2.0 port. The port supports a small selection of WWAN adapters.
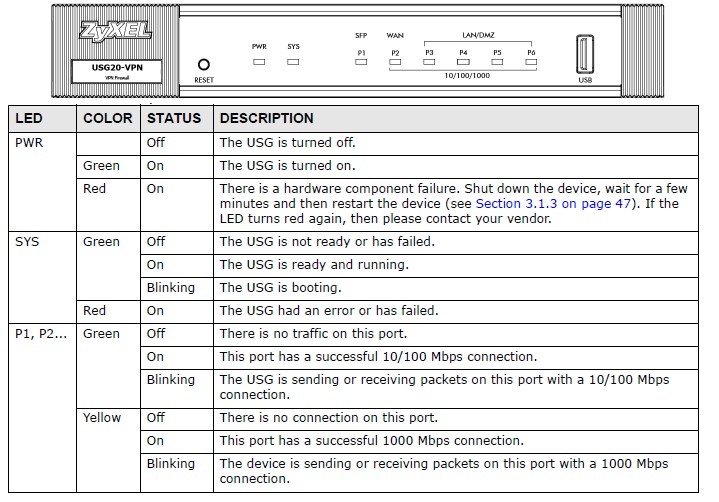
ZyXEL USG20-VPN Front
The rear of the USG20-VPN has the power connection, on/off button, SFP port, console port, and five 10/100/1000 RJ45 ports that can be assigned different roles. I’ll describe this further in the Network section.
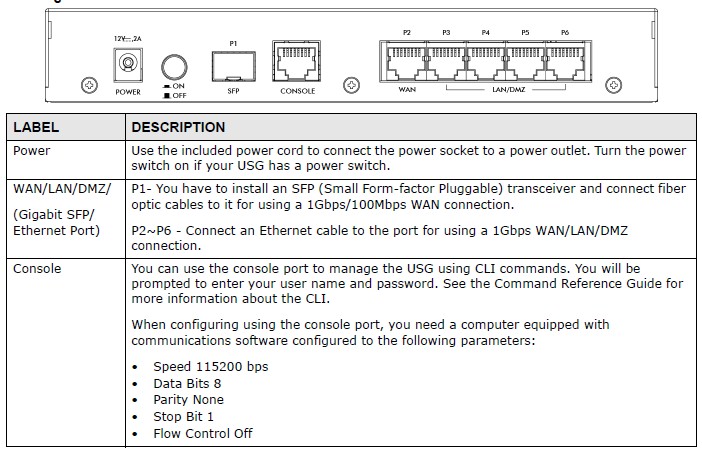
ZyXEL USG20-VPN Rear
Inside
The USG20-VPN runs on an 800MHz Cavium Octeon III CN7010 CPU with 2 GB of RAM and 4 GB of Flash. The Ethernet chipset is a Qualcomm QCA8337 Gigabit switch. Below is a shot of the main board; the CPU is hidden under the large heat sink.
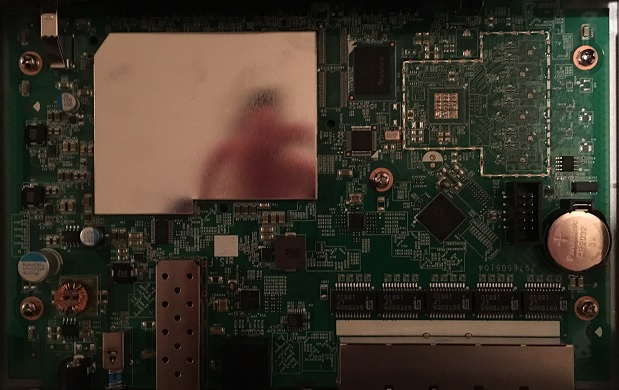
ZyXEL USG20-VPN Main Board
Features
The feature list below was compiled from ZyXEL’s data sheet and website. It’s pretty similar to what we found in the USG20 and USG40.
Hardware
Performance Ratings
Networking
IPv6
IPsec and L2TP VPN
SSL VPN
Firewall
|
Anti-Spam
Content Filtering
Authentication
System Management
Logging and Monitoring
|
Configuration
The USG menu remains very similar to the previous models I reviewed. When you log in, you’re presented with a dashboard showing a graphical image of the front of the device that accurately reflects the current LED status. The dashboard, shown below, provides device information, system status, system resource utilization (CPU, Memory, Flash, USB Storage, and Active Sessions), interface status, security feature status, and content filter statistics.
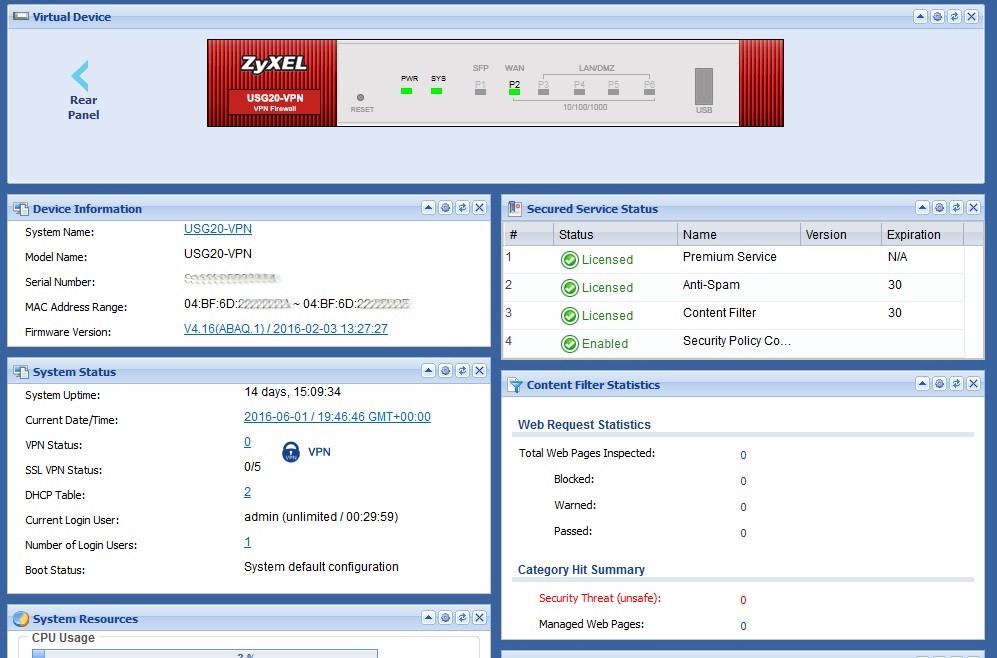
Dashboard
New to the USG configuration menus are links providing useful information on a technology or configuration. These links actually take you to a ZyXEL website called OneSecurity, full of useful information and guides. For example, in the VPN, Content Filtering and Anti-Spam menus there is a “Configuration Walkthrough” link, which brings up a helpful pdf document with screenshots and instructions. Below is a screenshot showing the Configuration Walkthrough link in the SSL menu.
SSL Configuration Help Screen
In addition to the Configuration Walkthrough links, there are also Troubleshooting, Download, and Info links for additional assistance. I hope ZyXEL continues to add to these links. For example, the Configuration Walkthrough link in the IPsec menu brings up a document on configuring Site-to-Site VPNs, but not on Client-to-Site VPNs.
ZyXEL told me they are going to upload to their knowledge base a handbook for the USG20-VPN that will include multiple guides on configuration, including IPsec.
Network
The USG20-VPN has a single 10/100/1000 RJ45 WAN port. There is also a Gigabit fiber SFP (small-form factor pluggable) port that can be used as a WAN port.
As noted earlier, a 3G/4GB USB dongle can be connected to the USG20-VPN USB port and used as a WAN port. The USG20-VPN can be used a Multi-WAN router if you have two of the three types of WAN interfaces (RJ45, SFP, USB). The USB port on the USG20-VPN can also be used to store sys logs and diagnostic information. It can not be used for shared network storage, though.
If you have multiple WAN interfaces, the USG20-VPN supports directing specific traffic types to specific WAN interfaces, as well as load balancing between WAN interfaces. A guide on configuring WAN load balancing/failover is located here. Load balancing methods include Weighted Round Robin (balances traffic over the WAN interfaces based on assigned weights), Least Load First (balances traffic over the WAN interfaces by sending new traffic to the least used interface), and Spillover (sends all traffic to one interface until full, then to the second interface).
There are four 10/100/1000 RJ45 LAN ports. Each of the four ports can be configured as lan1, lan2, or dmz interface types. By default, devices connected to lan1 ports are on the 192.168.1.0/24 subnet, devices connected to lan2 ports are on the 192.168.2.0/24 subnet, and devices connected to dmz ports are on the 192.168.3.0/24 subnet.
The USG20-VPN also supports 802.1Q VLAN tagging. Adding VLANs to the USG20-VPN creates a VLAN interface. ZyXEL doesn’t specify a VLAN limit on the USG20-VPN. As a reference, the USG40 spec sheet shows support for up to 8 VLANs.
The USG20-VPN also supports GRE (Generic Route Encapsulation) tunnels, as well as IPv6 in IPv4 and 6to4 tunnels. Creating any one of these tunnels creates a new tunnel interface on the USG20-VPN.
The USG20-VPN has extensive support for IPv6. IPv6 is a global setting that has to be enabled in the System-IPv6 menu. Once enabled, IPv6 configuration screens are available for configuring Interfaces, Security Policies, VPNs, and other menus involving IP addresses.
Bandwidth Management
Bandwidth utilization rules on the USG20-VPN can be applied by traffic type, user, or source IP address. A Configuration Walkthrough isn’t available and would be helpful for this feature, but I muddled through using the manual.
As a basic test, I did a quick speed test (speedtest.net) to determine my ISP speed. Before I enabled Bandwidth Management, my speed test results were 56.58 Mbps down and 5.65 Mbps up, shown below.
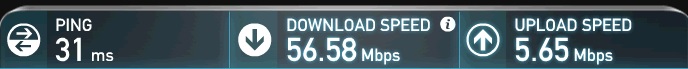
Speedtest Before BW Control
Then I enabled a Bandwidth Management rule to limit all traffic from my IP address to 1 Mbps, my configuration is shown below.
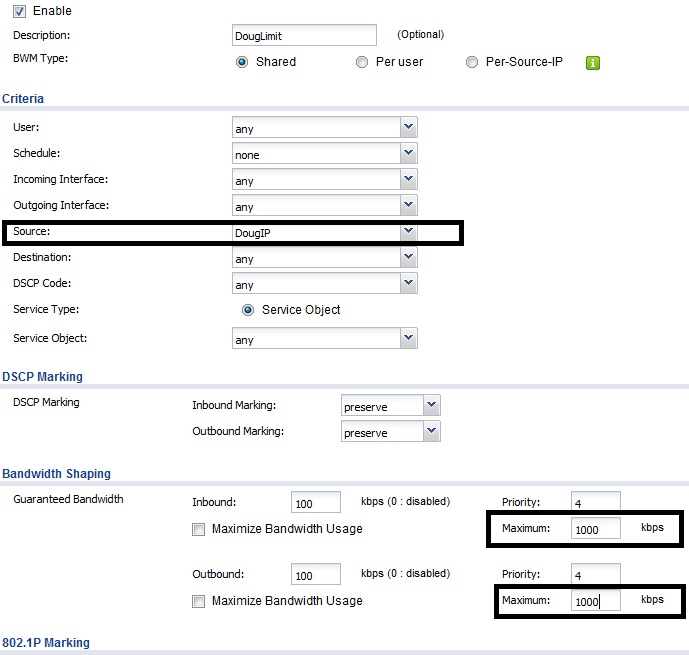
Bandwidth Config
Once the configuration was applied, I ran speed test again. As you can see below, my throughput was limited to approximately 1 Mbps down and 1 Mbps up, as configured.
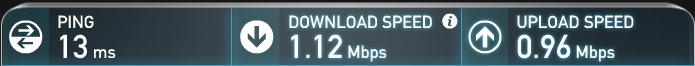
Speedtest After BW Control
Content Filtering
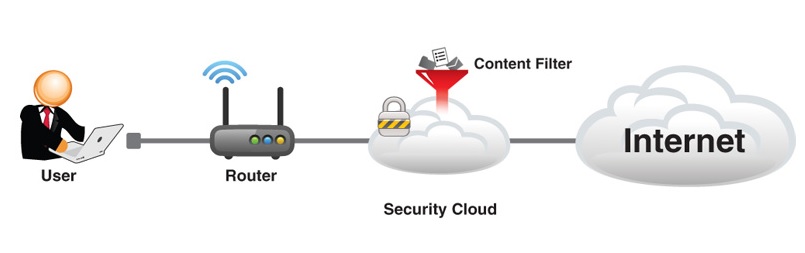
Content Filtering
The USG20-VPN optionally supports two UTM (Unified Threat Management) features. The licenseable features are Content Filtering and Anti-Spam. A 30 day trial license for both is activated when you register the router with ZyXEL. The OneSecurity site has information about recent security updates along with details on each of their UTM features. You can access this website by clicking the Content Filter or Anti-Spam Info link in either menu.
ZyXEL states their Content Filtering solution “covers 8 malware categories and 64 content categories for real-time analysis, management and site blocking”. You can also manually enter websites to block or permit. To categorize websites, ZyXEL uses “over 200 industry-leading Web data centers, boasting the broadest coverage around for content filtering”.
I followed the Configuration Walkthrough in the USG20-VPN menu to enable Content Filtering. Basically, you enable the feature and select categories of websites you’d like to block. There is a helpful test tool in the configuration menu where you can enter a URL to determine its category. The screenshot shows categories you can filter. Finally, you create and apply a Policy to filter Internet traffic based on the selected categories.
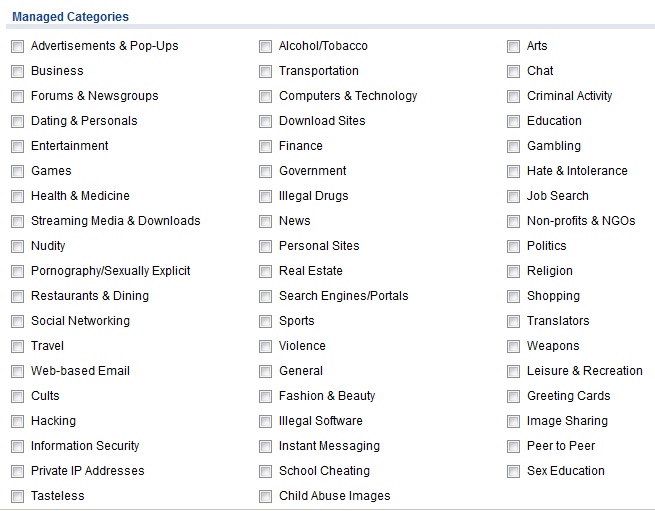
Content Filtering Categories
I did a simple before and after test on Content Filtering. First, I verified I could surf to https://www.smallnetbuilder.com/. Second, I used the ZyXEL test tool to identify as a “Computers & Technology” website. Third, I implemented a Policy to block the category “Computers & Technology.” Last, I tested my Policy. I got the below message on my screen when trying to surf to https://www.smallnetbuilder.com/ , validating the USG20-VPN Content Filtering capability. Note, you can customize the block message and provide a redirect URL if desired.
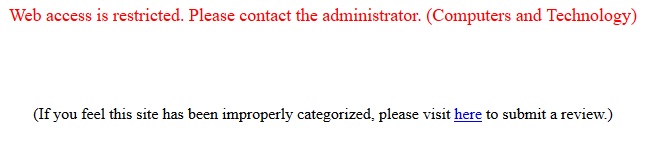
Content Filter Message
Anti-Spam
For its anti-spam feature, ZyXEL says “it shares the same database used by Google to protect its customers from malware. ZyXEL’s embedded Anti-Spam technology is powered by a large-scale, cloud-based security platform deployed across 12 carrier-grade data centers and multiple worldwide traffic collection nodes, gathering billions of Internet transactions daily to protect over 600 million users”.
The ZyXEL Anti-Spam feature tags incoming email so you can use your email client (Outlook or other) to delete or route the tagged emails to a folder. The default tag is “spam”, which can be changed. Spam can be detected and tagged through the use of the USG20-VPN’s DNSBL, Black and White lists, Mail Scanning and Profile menus. As with Content Filtering, the ZyXEL Configuration Walkthrough in the Anti-Spam menu was helpful to enable the Anti-Spam feature.
The DNSBL (DNS Black List) menu allows you to enable email filtering using an external DNSBL website, choices are listed at www.dnsbl.info, to check whether the sender’s source IP address is a known sender of spam. In the below screenshot, I’ve added b.barracudacentral.org and zombie.dnsbl.sorbs.net as two sites that the USG20-VPN will use to determine if an email is spam.
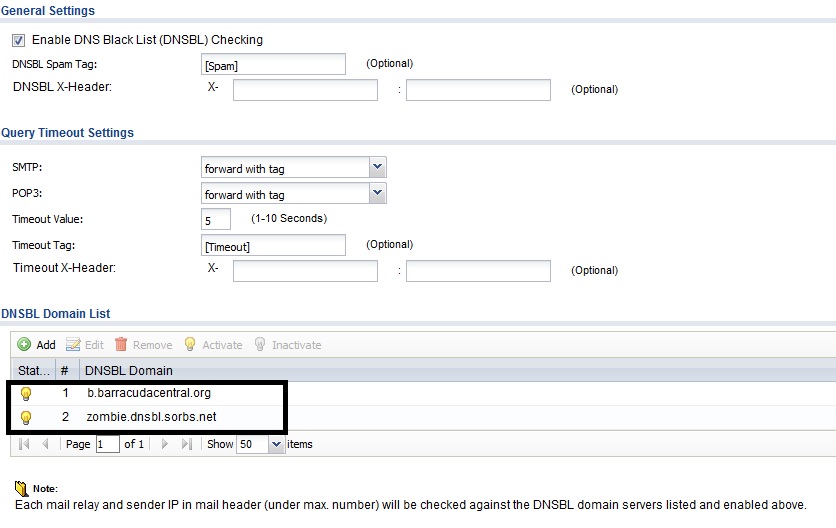
DNSBL Configs
Black and White lists allow you to manually filter (block or permit) emails sent via SMTP or POP based on keywords in the Subject line or Mail Header, the IPv4 or IPv6 address, or the email address. The Mail Scan tool allows the USG20-VPN to detect tag emails with viruses.
Finally, an Anti-Spam Profile enables you to drop, forward, or forward-with-tag emails that are detected by the DNSBL, Black List, or Mail scanner. In addition, detected spam emails can trigger a log or log alert.
VPN
The image below is a nice depiction of the VPN options on the USG20-VPN. The USG20-VPN supports L2TP, SSL, and IPsec VPN connections. L2TP support makes it easy for handheld devices to remotely connect to the USG20-VPN and L2TP can also be used by PCs. SSL support simplifies connectivity for remote PCs, and IPsec provides VPN connectivity for remote clients and routers.
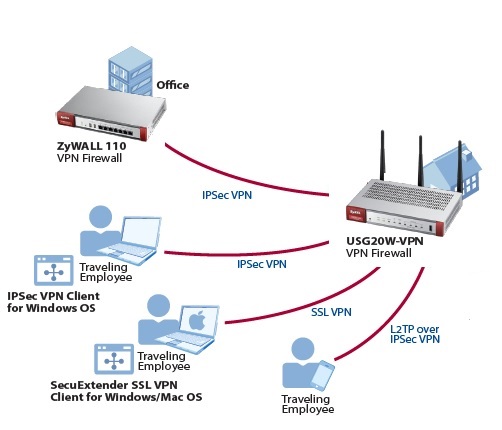
ZyXEL USG20-VPN VPN Capability
To set up an L2TP connection, I used the VPN Setup Wizard which does a pretty good job walking you through most of the L2TP setup. However, the Wizard omits the step to create a user, which is referenced in this help guide. With the Wizard to help me through the VPN setup, and the document’s instructions on creating a user and my iPhone, I successfully set up a connection between an iPhone 6s and the USG20-VPN. The USG20-VPN L2TP setup steps and connection status screen are shown in the gallery.![]()
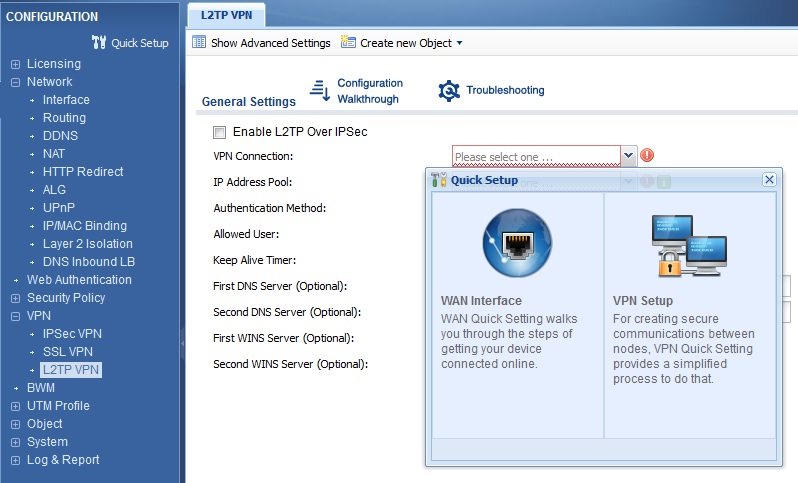
Quick Setup Menu for L2TP VPN Setup
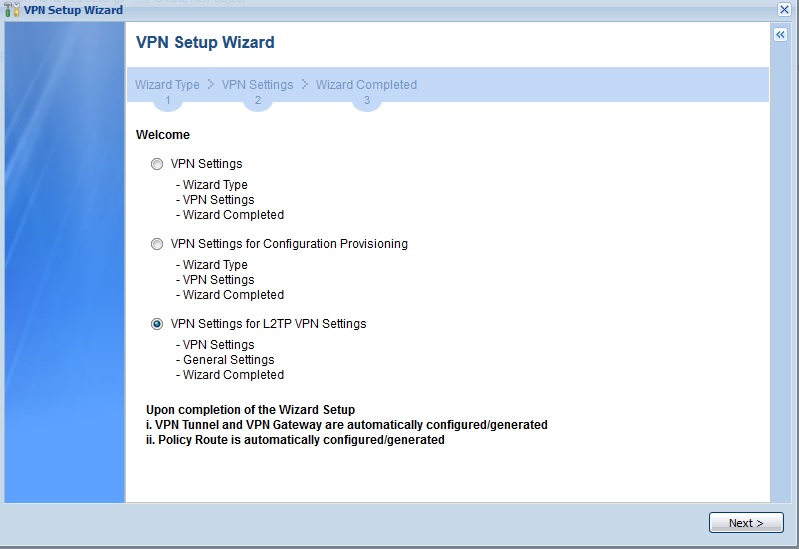
Select L2TP VPN Settings
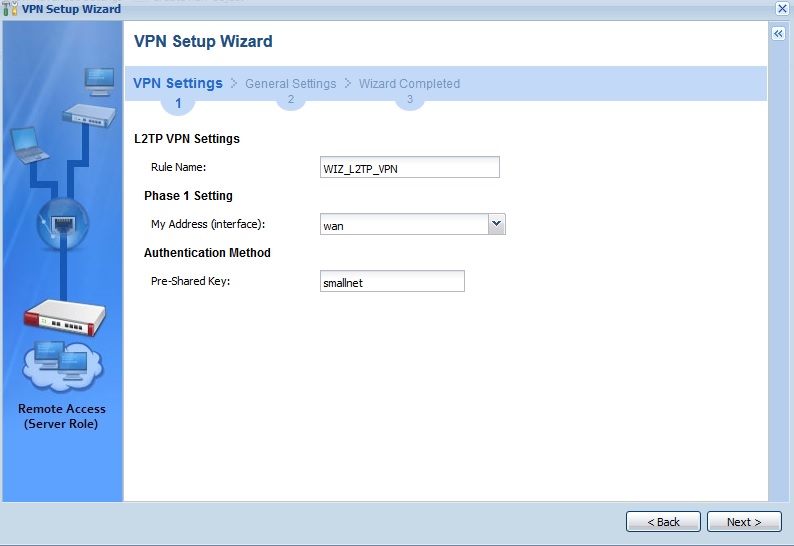
Create a Rule Name and Pre-Shared Key
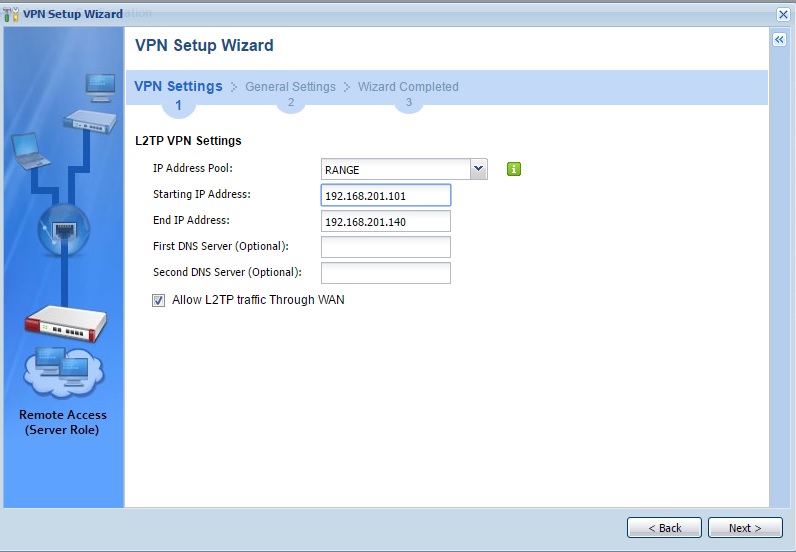
Set a range of IP addresses for L2TP VPN clients
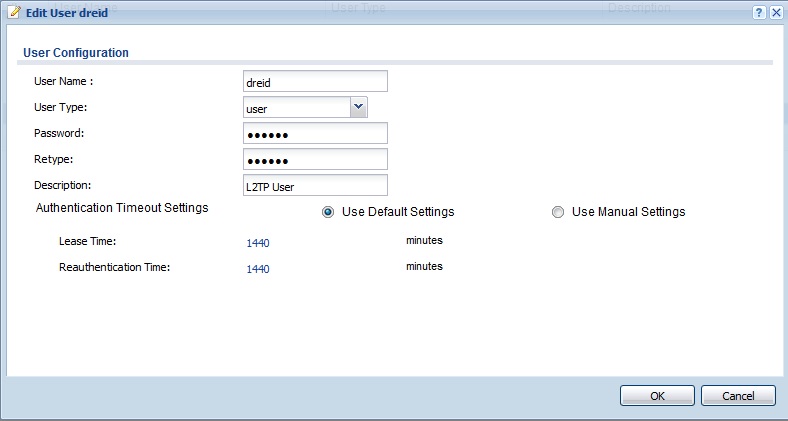
Create L2TP User
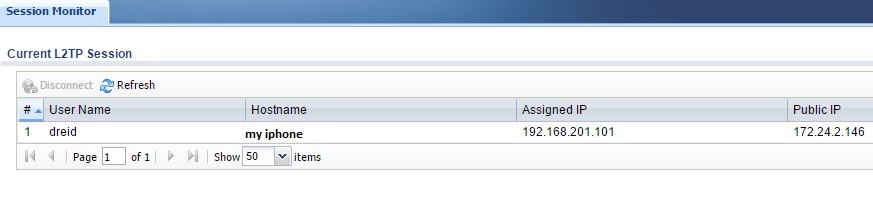
Successful L2TP Connection
Windows and MacOS also support L2TP connections. I successfully set up an L2TP connection to the USG20-VPN from a Windows 10 PC. On your Windows PC, configure the VPN Connection Properties for L2TP, enter your Pre-Shared-Key in the Advanced Settings and select Allow these protocols with MS-CHAP v2 selected, shown in the screenshot below.
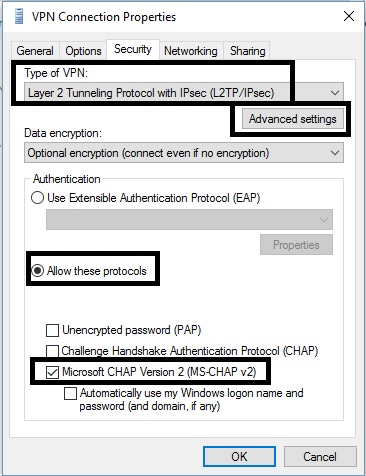
Windows L2TP Setup
The USG20-VPN SSL VPN configuration menu doesn’t have a Setup Wizard, but the configuration walkthough contained all the necessary steps. Configuration involves creating a user, a user group, an IP address pool and an SSL access policy. I copied the examples in the walkthrough.
ZyXEL supports SSL VPN connections on the USG20-VPN for MacOS 10.7 and above and Windows PCs with the SecuExtender SSL VPN client. For a Mac, the client is available via the download link in the SSL configuration menu. For a PC, you’re prompted to download and install the client the first time you attempt to connect via an SSL VPN tunnel to the USG20-VPN.
The only challenge I had connecting my Windows 8.1 PC was I had to run Internet Explorer in Administrator mode to successfully install the client and connect to the USG20-VPN. Below is a screenshot showing a live SSL connection from my Windows 8.1 PC to the USG20-VPN.
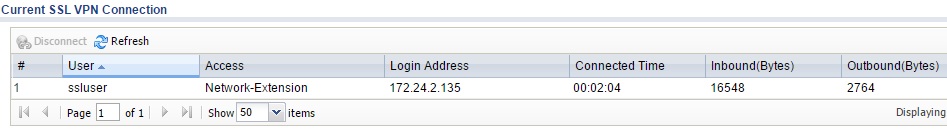
SSL VPN Connection
Although SecuExtender works, I prefer OpenVPN for SSL connections. OpenVPN is supported by multiple router manufacturers (ASUS, Linksys, and NETGEAR to name a few) and has client software for PCs and handhelds. If you connect to multiple different routers, it is helpful to use just one client. I’ve found multiple VPN client software applications can cause conflicts on a PC.
The USG20-VPN supports Client-to-Site IPsec VPN and Site-to-Site IPsec VPN connections. I was able to configure and connect a Client-to-Site IPsec tunnel, but I couldn’t pass traffic over the tunnel. I worked with ZyXEL engineering, but we couldn’t resolve the issue. It’s too bad the Client-to-Site IPsec tunnel didn’t work, because the configuration steps on the TheGreenBow client software and on the USG20-VPN were easier than on previous USG routers. However, I don’t consider the lack of a Client-to-Site IPsec solution a major issue, as I prefer L2TP and SSL connections for their simplicity. We’ll post an update when ZyXEL lets us know it has fixed the problem.
Update 7/29/16
After troubleshooting with ZyXEL, we determined the issue with the IPSec Client was that my client PC was on the same subnet as the USG-VPN’s WAN interface, which is my usual test scenario. Until now, I’ve never had a problem testing VPN clients from the same subnet as the router’s WAN interface. For example, the ZyXEL SSL VPN client worked on the same subnet as the USG20-VPN’s WAN interface.
Apparently, the latest version of the GreenBow client software requires the IPSec client is on a different subnet than the WAN interface. So, I put my PC on a different subnet, and sure enough, the tunnel came up and I could pass traffic over the tunnel.
As mentioned in my review of the USG20-VPN, ZyXEL made it easy to configure the IPSec client on both the USG20-VPN and the client software. ZyXEL sent me a step-by-step document on how to configure an IPSec client on the USG20-VPN and client software, which they said they’d post on their website soon. In the meantime, you can download it here.
The USG20-VPN also supports Site-to-Site IPsec VPN connections. I had no problem manually configuring an IPsec VPN tunnel from the USG20-VPN to a Linksys LRT224, using 3DES encryption and SHA-1 authentication. The tunnel connected as expected and I was able to pass traffic between both routers.
VPN Performance
To measure VPN throughput on the USG20-VPN, I used two PCs running 64-bit Windows with their software firewall disabled. Using TotuSoft’s LAN Speed Test client and server application, with a file size of 100 MB, I measured throughput over an L2TP, SSL, and IPsec tunnel. Below are my VPN throughput measurements for the USG20-VPN and the previously reviewed USG40.
| VPN Type | USG20-VPN | USG40 | USG20 |
|---|---|---|---|
| Client > Gateway (Mbps) | |||
| L2TP Client | 55.86 | 49.9 | N/A |
| SSL Client | 16.23 | 10.3 | N/A |
| IPsec Site to Site | 54.98 [Note 1] | 49.5 | N/A |
| Gateway > Client (Mbps) | |||
| L2TP Client | 59.07 | 56.0 | N/A |
| SSL Client | 24.09 | 19.7 | 4.79 |
| IPsec Site to Site | 52.61 [Note 1] | 53.8 | 27.9 |
Table 2: VPN Performance
VPN throughput on the new USG20-VPN is faster than the 2014 USG40, and significantly faster than the 2011 USG20. I measured peak L2TP throughput at 59.07 Mbps on the USG20-VPN compared to 56.0 Mbps on the 2014 USG40. The 2011 USG20 didn’t support L2TP. I measured peak SSL throughput at 24.09 Mbps on the USG20-VPN compared to 19.7 Mbps on the 2014 USG40 and 4.79 Mbps on the 2011 USG20. I measured peak IPsec throughput at 54.98 Mbps on the USG20-VPN compared to 53.8 Mbps on the 2014 USG40 and 27.9 Mbps on the 2011 USG20.
Note 1: I used Linksys’ LRT224 to measure IPsec throughput with the USG20-VPN. The USG20-VPN is rated by ZyXEL at 90 Mbps for IPsec throughput and the LRT224 is rated by Linksys at 110 Mbps for IPsec throughput.
Note 2: Router manufacturers typically use a UDP based test to rate throughput on their devices. The TotuSoft test uses TCP. UDP has a lower overhead than TCP, so manufacture VPN ratings are typically higher than my measurements.
VPN High Availability can be configured on the USG20-VPN if you have multiple WAN interfaces. This configuration is complex. ZyXEL has a configuration guide in section 6 of this document. It involves configuring GRE (Generic Route Encapsulation) tunnels via both WAN interfaces, configuring load balancing over the GRE tunnels, configuring IPsec tunnels and routing the GRE tunnels through the IPsec tunnels, and then routing local traffic through GRE. (I told you it was complex.)
Firewall
As mentioned previously, ZyXEL’s OneSecurity website has useful configuration tutorials and resources for security configurations on ZyXEL routers.
The firewall on the USG20-VPN uses stateful packet inspection and is configured via security policies. To understand a ZyXEL USG firewall, you have to understand policies and zones. Security policies are applied controlling traffic flows between zones. The default zones are LAN1, LAN2, DMZ, WAN, TUNNEL, IPsec_VPN, and SSL_VPN. Interfaces and connections are mapped to zones. The four interface types lan1, lan2, dmz, and wan map to firewall zones LAN1, LAN2, DMZ, and WAN. Virtual interfaces created by GRE, IPv6 to IPv4, and 6to4 tunnels map to the zone called TUNNEL. VPN connections map to zones labeled IPsec_VPN and SSL_VPN. Additional zones can be created and the mapping of interfaces to zones can be edited.
The default security policies on the USG20-VPN allow traffic from all zones to connect to the USG20-VPN’s admin server. Default security policies on the USG20-VPN also allow traffic from all zones, except the DMZ and WAN zones, to send traffic to all other zones. A default security policy also permits traffic from the DMZ zone to the WAN zone. Stateful packet inspection will allow traffic from the WAN through the firewall only if that traffic matches a known active connection. All other traffic by default is denied. The below screenshot shows the default security policies.
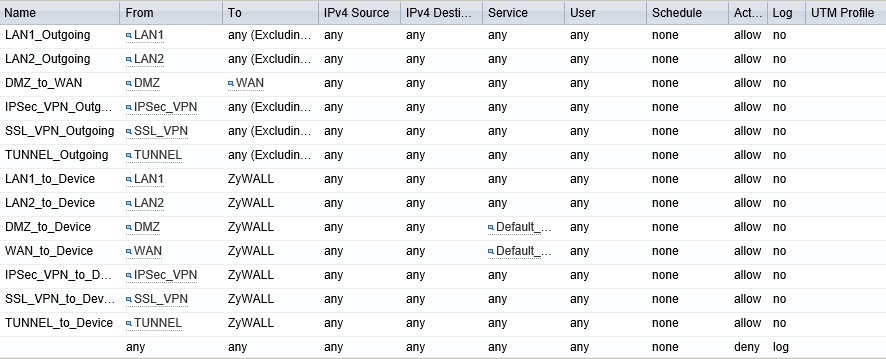
Default Firewall Policies
Additional security policies can be created to allow or deny traffic from specific zones and/or address objects to specific zones and/or address objects. Address objects can be created specifying single addresses, address ranges, or subnets. Security policies can allow or deny all traffic or predefined TCP, UDP, or ICMP traffic types. Custom traffic types can be defined as an object and used in a security policy. Security policies can also allow or deny traffic based on users and schedule.
Session limits can also be applied on the USG20-VPN to control network activity levels by user and/or address object.
Authentication
The USG20-VPN also supports user authentication. The basic login screen or a custom screen can be presented to users the first time they attempt to browse to a website. You can create different authentication policies based on schedule and based on source or destination IP addresses. Users can be authenticated via a local user database or via external Active Directory database.
I created a simple authentication policy using the USG20-VPN web authentication feature and a local user name and password. Once enabled, I was prompted to enter my user name and password before I was able to access web sites. My settings are shown below.
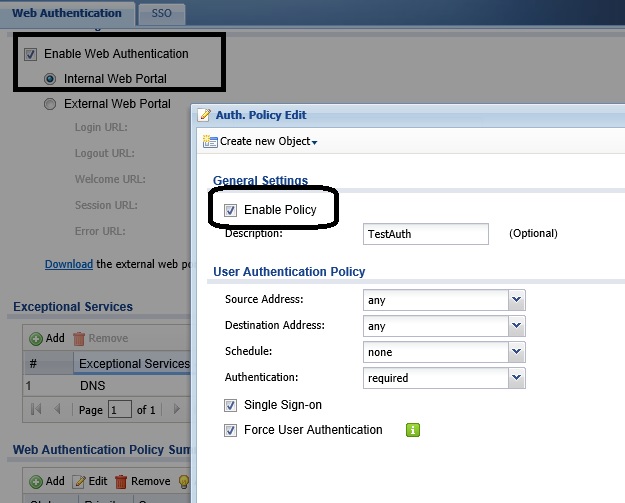
Authentication Configs
Reporting
The USG20-VPN provides a wealth of information about activity on your network. The dashboard, as previously discussed, is a quick way to see device info, system status, license status, content filter stats, system resources, and interface status.
The Monitor menu provides more detailed port statistics, traffic statistics, a session monitor, IGMP statistics, DDNS statistics, IP/MAC bindings, logged-in users, cellular statistics, UPnP port status, USB storage data, and detected Ethernet neighbors. It also provides a display of active VPN connections (shown in the previous VPN section.) The monitor menu also provides a display of Content Filtering and Anti-Spam activity.
You can also view current log messages in the Monitor menu. The USG20-VPN can be configured to email a Daily Report. The Daily Report provides General info about the USG20-VPN, plus daily graphs of CPU Usage, Memory Usage, Session Usage, Port Usage (for each port), Content Filter and Anti-Spam Statistics, and Interface Traffic Statistics.
The gallery shows sections of a daily report from a USG20-VPN to give you an idea of the format. The reports would be more interesting if the USG20-VPN had been in service for awhile before I grabbed them!

Quick Setup Menu for L2TP VPN Setup

Select L2TP VPN Settings

Create a Rule Name and Pre-Shared Key

Set a range of IP addresses for L2TP VPN clients

Create L2TP User

Successful L2TP Connection
Routing Performance
Testing and analysis by Tim Higgins
The USG20-VPN was one of the first devices to be put through our new V4 Router test process. So it received both performance and functional testing with V4.16(ABAQ.1) firmware loaded. You can download an Excel test summary that contains all functional and performance test results. You’ll note the performance tests include data we aren’t including in the Router Charts at this time, such as retries for TCP/IP tests, % packet loss for UDP and latency.
The Benchmark Summary shows throughput significantly lower than we’re accustomed to seeing in most of today’s routers. I verified the results with ZyXEL; they’re as expected. Note the router’s firewall was not doing any heavy lifting when performance tests were run, i.e. neither of the UTM features were engaged. So these numbers are best case.
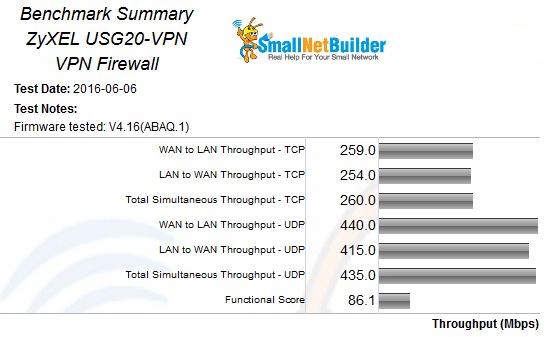
ZyXEL USG20-VPN Benchmark Summary
To compare to other routers tested with the V4 process, you’ll need to scroll down a bit in the Router Charts Benchmark selector. Here’s a link to the new WAN to LAN Throughput – TCP benchmark to start you off.
The USG20-VPN passed both the TCP and UDP 3,000 connection tests. The latter success was made possible by the router’s ability to set the UDP session timeout. I changed it from its default 60 seconds to 300 seconds. I could have made it shorter, since the UDP tests usually takes about 3 minutes to run. The only other router to pass the UDP session test so far is the NETGEAR R7000 Nighthawk, which has no controls to set UDP session timeout.
The Functional Score of 84.1% includes 39 failed functional tests. Key takeaways from the failed tests are:
- Deprecated HTTPs SSL protocols were not blocked
- Hairpin NAT translation for TCP/IP and UDP are not supported
- Triggered port forwarding tests failed because the feature isn’t supported
- More UPnP tests than usual failed.
- The router lost connection when the WAN IP address changed
In addition to the above, I noticed different results in the initial DoS tests from run to run. The test plan allows 30 seconds for the device to recover from each attack. Sometimes all tests recovered, other times they didn’t. The functional score doesn’t include any DoS test failures.
There were also differences in the number of UPnP tests that failed from run to run. I also suspect this is due to short UPnP mapping expiration times.
Closing Thoughts
The USG20-VPN is currently priced around $195, just about midway between the USG20 at around $165 and the USG40 at close to $240. This pricing passes the sniff test since the USG20-VPN’s features and performance are between the two devices’.
Extending the Content Filter license for one year will run you $74.99 and $129.99 for two. Extending the Anti-Spam license for one year is $109.99 and $189.99 for two. Additional IPsec Client Licenses are $64.99 for 1, $249.99 for 5, and $399.99 for 10. Additional SSL Client Licenses cost out at $135 for 5 and $225 for 10. MacOS SSL software will set you back $135 for 10 licenses; Windows SSL costs nothing.
UTM devices in general are no picnic to configure, as the amount of options can be overwhelming. The user manual for the USG20-VPN is 683 pages! However, I found that ZyXEL’s new embedded links with Configuration Walkthroughs and info pages, plus the Configuration Wizards were very helpful. Despite this and help from ZyXEL, I couldn’t get Client-to-Site IPsec tunnels to work. Other than this issue, though, I was able to configure and enable every feature on the USG20-VPN I explored.
As a Unified Threat Management device, the USG20-VPN provides Content Filtering and Anti-Spam protection, leveraging huge global databases. If you also need Anti-Virus and Intrusion Detection and Prevention, you can get those features from the USG40 for about $35 more. Overall, I found the ZyXEL USG20-VPN a compact and powerful network security device that does an excellent job as an Internet Gateway, VPN router for remote access, Firewall to protect your network and Security Appliance providing Content Filtering and Anti-Spam protection.
