Introduction

| At a Glance | |
|---|---|
| Product | D-Link NetDefend Firewall/VPN Security Appliance (DFL-CPG310) |
| Summary | UTM/VPN Firewall appliance OEM’d from CheckPoint with subscription web filtering and Antivirus. |
| Pros | • Good stability in real world test • Quick setup • Compact size • Good comparative throughput for a UTM device |
| Cons | • No gigabit support • VPN Client not Vista ready • Significant problems with VPN gateway connection • Confusing NAT/VPN Client settings |
The DFL-CPG310 is a small footprint offering in the Unified Threat Management (UTM) market from D-Link. At just 8″ long, 5″ wide, and a little over 1″ high, it’s pretty compact. Even its wireless antennas seem small, measuring just 3″.
As with other UTM devices, small size does not imply few features. D-Link’s DFL-CPG310 is an option-filled network control product providing Firewall functionality, Client and Site-to-Site VPN connectivity, Antivirus Protection, Intrusion Detection and Protection (IDS/IPS), Web Filtering, and Network Reporting, all in addition to being a multi-WAN gateway router, wireless access point, and USB print server.
The security features use CheckPoint/Sofaware technology. Essentially, the DFL-CPG310 is a UTM appliance OEM’d from CheckPoint. A quick look at CheckPoint’s web page shows the DFL-CPG310 has a striking resemblance to CheckPoint’s VPN-1 UTM Edge. If you look closely, you can see the CheckPoint logo on the front of the D-Link in Figure 1.
Visually, you can tell this isn’t the typical home network D-Link product. Instead of the familiar colorful and rounded D-Link chassis, this product is a compact rectangular gray box with simple indicator lights on the front and ports on the back; see Figures 1 and 2 below.

Figure 1: Front of the D-Link DFL-CPG310
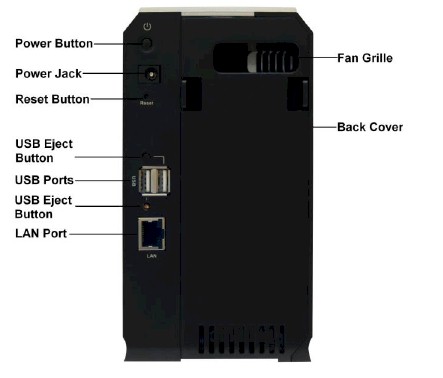
Figure 2: Rear of the D-Link DFL-CPG310
Taking a look at the motherboard shows that there are a few other companies involved in this product. In Figure 3, we can see the VIA VT6212L chip that is the USB 2.0 controller. In the center is a clearly labeled Gigabyte card providing the wireless control, with the passively cooled CPU just to the right. The DFL-CPG310 CPU is a Cavium model from their line of Brecis Secure Processing solutions running along with 64MB of RAM.
Figure 3: View of the mainboard
With components from D-Link, VIA, Gigabyte, Cavium, Check Point, and Sofaware, the DFL-CPG310 is quite the collaborative product. With all these players identified, let’s get into its functionality.
In Use
I’m a fan of admin menus that run down the left and across the top of the screen. This type of menu structure seems more intuitive, with high-level choices on the left and sub-choices across the top. I find this easier to navigate than those with expandable menus on the left or across the top.
Figure 4: Welcome screen
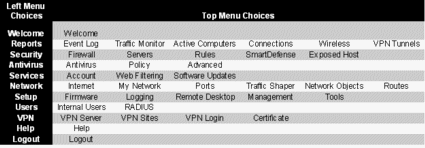
Of the 37 configuration choices on the DFL-CPG310, the first one is a simple Welcome screen as above in Figure 4, and the last two are a Help button and a Logout button. That leaves 34 screens to navigate for configuration, which I’ve summarized in the matrix shown in Table 1. Note that additional menu options are added as features are enabled, such as when USB Printers are connected.
Table 1: Chart of configuration screens
There is a general NetDefend Wizard for configuring the WAN, NTP, Wireless, Product Key, and enabling subscription based security options, as well as individual Wizards for setting up the Internet, Wireless, Firewall Rules, Site-to-Site VPNs and the SmartDefense IDS/IPS settings. I was disappointed that the NTP settings don’t allow for daylight savings, leaving the router’s time off by an hour from March to November.
Manually configuring the DFL-CPG310 for basic operation only takes a few minutes. I installed the D-Link at a small business with seven computers connected to a simple Layer 2 switch, using a basic DHCP Ethernet setting for WAN access.
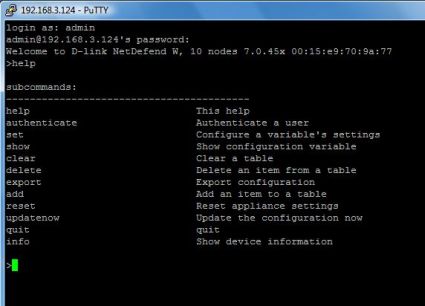
Remote access can be enabled via HTTPS and can be restricted to a VPN interface, a specific IP range, or fully allowed. SSH (Figure 5 below) is available for secure command line access to the router, if desired.
Figure 5: Secure command line via SSH
Wireless
The wireless radio supports 802.11b/g/super g connections. The security choices for the wireless radio are pretty typical, with support for WEP and WPA/WPA2 security, hiding the SSID and enabling MAC filtering. I had no problem connecting my Dell laptop with an Intel Pro/Wireless 3945A/B/G card to the DFL-CPG310 configured for WPA security with a hidden SSID and MAC filtering enabled.
The wireless network is a separate subnet from the wired subnet, running on the 192.168.252.0 /24 subnet with its own DHCP service. From a security standpoint, this is good. It enables greater control of the network through the use of separate subnets for the wired and wireless nodes.
Optionally, the DFL-CPG310 can provide greater wireless security by requiring the use of the VPN client to authenticate to the Wireless LAN. I’ll touch on the VPN Client software in more detail shortly.
Security
Intrusion Detection and Protection is an aspect of the DFL-CPG310 Firewall that increases the Security of your network. In addition to its CheckPoint-developed Stateful Packet Inspection Firewall, the DFL-CPG-310 offers greater levels of security intelligence through its SmartDefend Intrusion Detection and Protection. As you can see in Figure 6, SmartDefend allows for detection of a wide array of specific network attacks, such as Denial of Service, Ping of Death, Worms, and numerous other threats. As I’ll discuss in the pricing section, keeping the DFL’s security software up to date is a subscription-based service.
Figure 6: SmartDefend IDS/IPS options
The Firewall in the DFL-CPG310 has pre-built options to simplify port forwarding to Web, FTP, Telnet, Email, PPTP/VPN, Microsoft NBT (NetBIOS over TCP/IP), and VoIP (H.323) servers. Standard features, such as the ability to define a DMZ Host, are also available.
It is interesting that D-Link chose to have a pre-built configuration for H.323 VOIP signaling, when SIP VOIP signaling is more common. Nevertheless, building a rule to forward SIP signaling (port 5060) or other TCP/UDP ports can easily be done with the Firewall Rule Wizard.
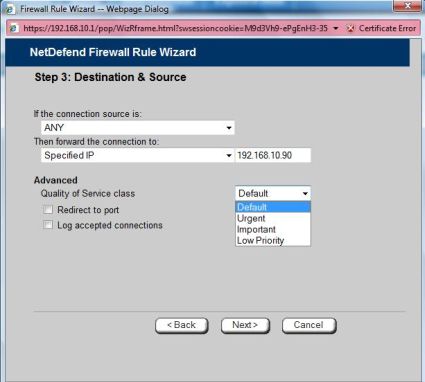
When you build a Firewall rule, the DFL-CPG310 provides QoS options to allocate bandwidth for specific traffic, a nice feature, especially for VOIP. As you can see in Figure 7, the bandwidth options for port forwarding are Default, Urgent, Important, and Low Priority.
Figure 7: Firewall rule QoS bandwidth options
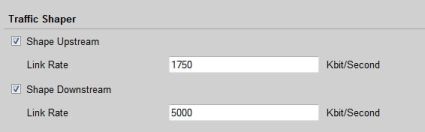
Understanding these options involves the DFL-CPG310’s Traffic Shaper, which requires configuring the speed of your WAN connection. Using a network speed test on www.speakeasy.net, my WAN speed came in at 1829Kbps Up and 5367Kbps Down. I used these numbers on the WAN Interface configuration page (see Figure 8) to set an Upstream rate of 1750Kbps and Downstream rate of 5000Kbps, per the manual’s recommendation to use settings below actual.
Figure 8: Setting the connection speed for traffic shaping
The DFL’s QoS settings use relative weight bandwidth allocation based on the Traffic Shaper configuration. Those settings and their weight are Default=10, Urgent=15, Important=20, and Low Priority=5. Thus, traffic assigned a priority of Important (20) will be allocated twice as much bandwidth as Default (10). If you upgrade to the PowerPack, you can configure the QoS settings to utilize more flexible QoS parameters, such as DSCP classifications or your own custom configuration. I’ll touch on the PowerPack option under the Pricing section.
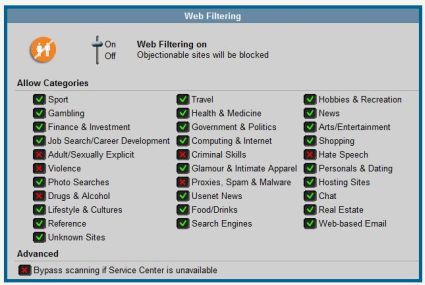
Additional subscription-based security features of the DFL-CPG310 include Antivirus and Web Filtering. The Antivirus feature allows for scanning and blocking of email at the gateway level, monitoring SMTP, POP3, and IMAP packets. The Web Filtering feature enables control of web surfing, providing over 30 different categories of web sites to screen, as you can see in Figure 9.
Figure 9: Web Filtering configuration
Other
There are two USB 2.0 ports on the back of the DFL-CPG310 for connecting a USB printer and sharing it on your network. Once a printer is connected to a USB port, the DFL-CPG310 will detect it and present an additional menu screen to customize the printer as necessary.
The OPT port offers multi-functionality, including the ability to connect a second WAN connection, or to connect and define a DMZ subnet. For second WAN connections, the DFL-CPG310 will failover from the primary WAN connection to a secondary WAN connection for Internet redundancy. In DMZ mode, this port will support a separate LAN subnet, complete with a DHCP server, and allow unrestricted traffic in and out of the interface.
There is also a serial port on the DFL-CPG310, which can be used either for a console connection, or to configure a backup modem. This backup modem connection, configurable for dial-up or ISDN BRI services, can also be set up for WAN failover.
Virtual Private Networking
The DFL-CPG310 is a “Security VPN Firewall” with both Client and Site-to-Site VPN functionality. VPN Client access involves using a software client on a remote PC to set up a secure connection to the home LAN, while Site-to-Site VPN access uses configurations in routers to securely connect LANs. Out of the box, the DFL-CPG310 provides five licenses for the VPN Client software and supports two Site-to-Site VPN tunnels.
The DFL-CPG310 supports DES, 3DES, AES-128 and AES-256 encryption, and both MD5 and SHA1 authentication. Diffie-Hellman Group 1 (768-bit), Group 2 (1024-bit), and Group 5 (1536-bit) Phase 1 and Phase 2 key exchange security are also supported. Perfect Forward Secrecy can be enabled to further enhance key exchange security.
VPN Client
Figure 10 below is a simple diagram depicting a network supporting VPN Client software. A common use for this technology is for mobile employees to securely access the home LAN over the Internet.
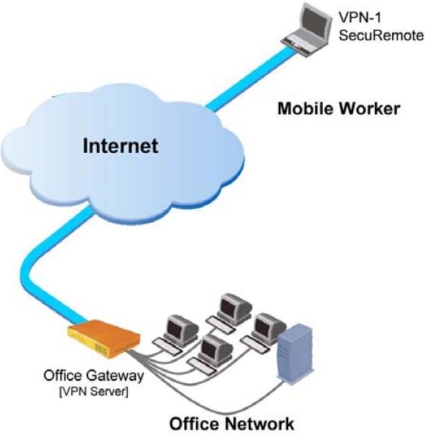
Figure 10: A VPN client software diagram
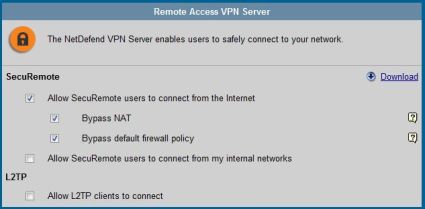
VPN Client access to the D-Link LAN is enabled through the CheckPoint VPN-1 Secure Client software. The software is available both on the included CD and through a simple download, with the download link provided in the DFL-CPG310’s VPN Server menu screen, as you can see on the right in Figure 11. This is handy, enabling an administrator to load the VPN client software on each PC without carrying around a CD.
Figure 11: VPN options and a link to download the VPN client software
As we’ve seen with other VPN Client offerings lately, Vista isn’t listed as a supported OS. I installed the software on an XP Pro machine using defaults, simply entering the dynamic DNS name of the D-Link as the target site, as you can see in Figure 12.
Figure 12: Settings for the VPN client software
VPN Client – more
We had significant challenges getting the VPN Client to work. We tried numerous different configurations in multiple network locations and configurations before we could get the VPN Client to successfully connect to the DFL-CPG310. Once we got it working, we undid the working configuration and re-tried some of the failed configurations to better understand what worked. The confusing result was that the previously failed options then worked! To add to the frustration, working configurations were not repeatable on other machines in later tests.
We suspect that once the VPN Client makes a successful connection, it learns aspects of the network configuration that enable future connections. For example, the VPN Client software learns the subnet of the DFL’s LAN after the first connection. This enables the Client to launch automatically if a user starts an application that attempts to connect to the DFL’s LAN subnet.
In our test case, the DFL’s LAN subnet is 192.168.10.0 /24. Pinging 192.168.10.1 from the remote PC with the VPN Client software automatically launches the connection screen shown in Figure 13 with a message saying, “Your computer is trying to establish communication with your site. Please connect.”
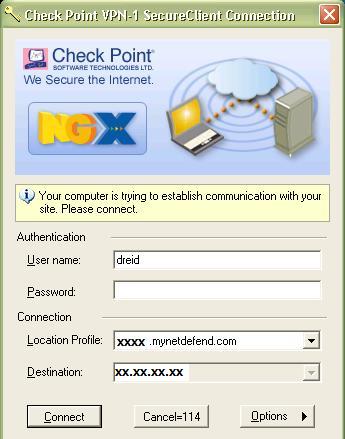
Figure 13: Automatic launch of the VPN client software on access attempt
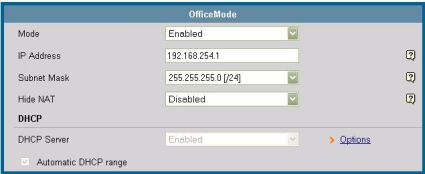
Understanding and managing DFL-CPG310 VPN Clients involves understanding the DFL-CPG310 “OfficeMode” configuration. OfficeMode, shown below in Figure 14, is a separate virtual LAN that assigns IP addresses from a unique subnet (192.168.254.0 /24; Figure 14 below) to VPN Clients as they connect. This unique subnet is then routed by the CPG310 so that remote clients tunneling in are treated as though they were on the local LAN.
As with the Wireless network, the separate subnet is a good security feature. Servers and storage devices will likely be on the wired LAN subnet, and having separate subnets for the Wireless and VPN clients enables building access control lists based on originating subnets into the Firewall.
Figure 14: OfficeMode configuration, showing separate VLAN subnet for VPN clients
However, from a configuration standpoint, it is a challenge to understand how the DFL-CPG310 VPN Server and OfficeMode’s NAT options work together.
The VPN Server has a configuration option to “Bypass NAT,” (see previous Figure 11) which the manual states will tell the router to “not perform Network Address Translation (NAT) to the internal network for authenticated remote users.” That makes sense. If you’re connecting via the VPN Client, you will have an IP from the OfficeMode subnet, and your traffic does not need NAT.
OfficeMode then has the further option to Enable or Disable “Hide NAT.” The manual explains Hide NAT “enables you to share a single public Internet IP address among several computers, by ‘hiding’ the private IP addresses of the internal computers behind the NetDefend firewall’s single Internet IP address.” Why D-Link calls it “Hide NAT,” I don’t know. It would be easier if they simply called it “NAT.”
The VPN Client worked with Bypass NAT checked and Disable Hide NAT selected. It seems like this can be simplified with a single option to Enable or Disable NAT, instead of creating so many double negatives. The end result is the various NAT options for VPN Client connections are poorly documented and confusing.
VPN Site-to-Site
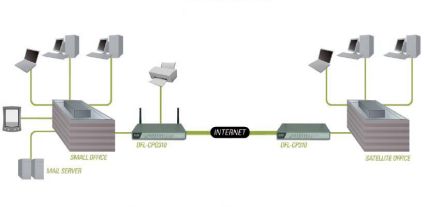
Figure 15 below from D-Link’s Product Data Sheet depicts using two D-Link DFL routers to create a site-to-site VPN connecting two small office LANs. As you can see in this example network, there is a Mail Server in the Small Office LAN on the left, which is securely accessible to the PCs in the Satellite Office LAN on the right, via this VPN.
Figure 15: Diagram of a typical site-to-site VPN
Compared to the VPN Client, site-to-site VPN functionality was easy. I was able to set up a site-to-site VPN using a DFL-CPG310 at one location and a Linksys RV042 as the other.
With the Site-to-Site configuration wizard, I used AES-128 Encryption and SHA-1 Authentication for IPSec Phase 1 and Phase 2 negotiation. I selected Diffie-Hellman Group 1 on both Phase 1 and Phase 2, and enabled Keep Alive to keep the tunnel active.
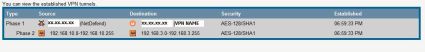
Each side used the other’s Dynamic DNS to locate and recognize the other side, and authentication was handled through a manually entered Shared Secret Key (PSK), which is a common text string you enter on both routers. Figure 16 is a status screen from the DFL-CPG310 showing the VPN has been successfully established, linking the 192.168.10.0 /24 LAN of the D-Link to the 192.168.3.0 /24 LAN of the Linksys.
Figure 16: VPN status screen showing connection
For more detail, please see the slide show of screen shots showing all the configuration options selected on both the D-Link and the Linksys.
I was impressed with the D-Link’s site-to-site VPN stability and resiliency. I left this site-to-site VPN running continuously, and it remained up for the several weeks I tested this router. I configured a couple of the PCs on the D-Link LAN to run automatic backups to a storage device on the Linksys LAN over this VPN, and they all ran without error.
Performance
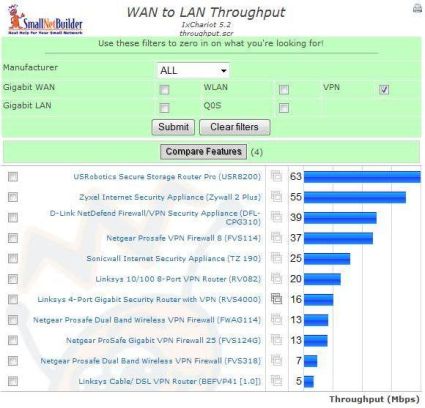
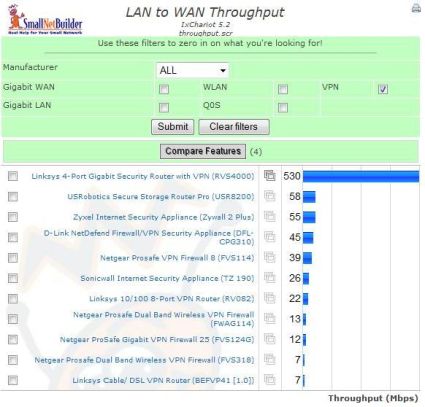
Let’s take a look at the throughput measurements from our Router Performance Charts in Figure 17 and Figure 18 below. Comparing WAN to LAN and LAN to WAN throughput for routers with VPN capability, we can see the DFL-CPG310’s performance is near the top with 39 Mbps WAN to LAN and 45 Mbps LAN to WAN throughput.
Figure 17: WAN to LAN throughput comparison chart
Figure 18: LAN to WAN throughput comparison chart
Performance – more
Directly comparing the DFL-CPG310 to another UTM product with similar features, the SonicWALL TZ190, displays the DFL’s relative performance strength. I pulled the numbers from the above charts into a simple table, below, which highlights that the D-Link’s throughput is over 50% greater than the SonicWALL’s.
| Throughput – (Mbps) | ||
|---|---|---|
| Router | WAN – LAN | LAN – WAN |
| SonicWALL TZ190 | 25 | 26 |
| D-Link DFL-CPG310 | 39 | 45 |
Table 2: D-Link DFL-CPG310 vs. SonicWALL TZ190 performance comparison
Good throughput speeds on this router are important, considering the number of possible interfaces that can be running simultaneously. A DFL-CPG310 configured with LAN, Wireless, DMZ, and OfficeMode interfaces could be routing packets between four different private subnets and the public Internet.
We unfortunately were unable to measure VPN tunnel throughput due to the problems we had consistently getting a client to connect. However, given the use of the Brecis / Cavium processor, we’d expect performance similar to that of the SonicWALL TZ 190, i.e. about 1.5 Mbps with 3DES tunnel encryption.
Pricing
The base DFL-CPG310 provides gateway/router/firewall functionality for up to 10 nodes, a wireless access point, five licenses for the VPN Client and two site-to-site VPN tunnels. Online, a base DFL-CPG310 will run about $335. The base price does not include the Antivirus protection, Web filtering, Dynamic DNS, security reporting, or the PowerPack functionality. Intrusion Protection software updates, Firmware updates and support are also subscription services.
Nodes are essentially devices with IP addresses that need access to the Internet, and the base price only supports 10 nodes. You can tell how many devices are being counted by the DFL-CPG310 as nodes by clicking on the Node Limit button in the Reports-Active Computers menu.
Computers count as nodes. A NAS may not need access to the Internet for web surfing, but if you use a NAS that gets its timing via external NTP functionality, count it as a node. Even devices in the DMZ count as nodes. For an additional $100, you can upgrade the DFL-CPG310 to support 25 nodes, and for an additional $620, you can upgrade the DFL-CPG310 to support unlimited nodes
If you’re going to upgrade to unlimited nodes, you should probably consider the D-Link PowerPack option. This upgrade, which runs an additional $499, enables a 50% increase in firewall and VPN throughput. The PowerPack also enables creating a secure wireless Hotspot, additional VPN Client Licenses and Site-to-Site VPN Tunnels, Advanced QoS, VLAN Tagging, and OSPF Routing.
D-Link has a link on its product page that provides a 90-day free trial for some of the subscription based services, including Antivirus, Dynamic DNS, Intrusion Protection software updates, and security reporting.
The DFL-CPG310 menu has a link to a web site with the following subscription pricing options for the 10-node model. $89/year buys Firmware updates, email/web/telephone support, an extended warranty, and Dynamic DNS. $219/year buys all these services plus Intrusion Protection software updates and the Gateway Antivirus service. For an extra $199/year, you can add the Web filtering service. These prices increase as you increase the number of nodes, and D-Link is working to get additional pricing information on the web.
With the D-Link DFL-CPG310 and the previously reviewed SonicWALL TZ190W, comparing pricing on UTM devices can be challenging. An apples to apples comparison of pricing is not completely fair. The D-Link’s PowerPack option and the SonicWALL’s eight LAN ports and WWAN support make them different devices. However, if you’re in the market for an all-in-one device, it is interesting to look at what you get for the money.
The chart in Table 3 compares online base prices for the D-Link DFL-CPG310 and the SonicWALL TZ190W. Online pricing information makes it easy to assess the cost for a 10 node D-Link and an unlimited node SonicWALL. For an apples to apples unlimited node price comparison, I used pricing information I received from D-Link and calculated the middle column.
| Functionality | D-Link DFL-CPG310 (10 nodes) | D-Link DFL-CPG310 (unlimited nodes) | SonicWALL TZ190W (unlimited nodes) |
|---|---|---|---|
| Base | $335 | $955 | $685 |
| Annual Antivirus / IDS / IPS / Firmware / Support | $219 | $449 | $295 |
| Annual Web Filtering / Antivirus / IDS / IPS / Firmware / Support | $418 | $748 | $395 |
Table 3: Base and annual subscription price comparison
When all is said and done, you’ll need to do an inventory of your network and needs to figure out how much a D-Link DFL-CPG310 or SonicWALL TZ190W will set you back, both as a purchase and on an annual basis. On a smaller network, the D-Link looks like a relative bargain. On a larger network, the SonicWALL looks to be the better deal.
Conclusion
UTM devices make a lot of sense on a small network. They provide a single connection point at the network edge for WANs, LANs, and VPNs, which is the logical point for network protection, web filtering, and filtering email.
The DFL-CPG310 UTM offering has some issues. First, I continue to be disappointed in new products that lack gigabit LAN and support for Microsoft Vista. But the bigger problem the DFL-CPG310’s Checkpoint VPN Client. As mentioned earlier, it was inconsistent and unreliable in its operation—to the point where I was unable to test VPN Client throughput.
The problems with the VPN Client are unfortunate, since, on the positive side, the Site-to-Site VPN worked well and the DFL’s WAN/LAN throughput was good. The D-Link DFL-CPG310 throughput in relation to its most similar competitor we’ve tested, the SonicWALL TZ190, was significantly superior.
I also liked that the DFL’s WAN/LAN stability in real world use was excellent. Users on the LAN never had a problem. I was able to access the DFL-CPG310 remotely via the WAN and site-to-site VPN connections without issue. The DFL-CPG310 ran continuously without a single crash or reset necessary. Further, the menu layout for the D-Link is a plus, making it easier to remember your way through the numerous options a UTM device provides.
In conclusion, the DFL-CPG310 is stable, it’s relatively simple for a UTM device, it has a powerful firewall and router, and has solid WAN/LAN performance. It’s a shame its VPN Client isn’t a good partner to an otherwise strong product.
See the slide show of screen shots for setting up a site-to-site IPsec tunnel between the DFL-CPG310 and Linksys RV042.