Introduction

| At a Glance | |
|---|---|
| Product | NETGEAR ProSafe 8-Port Gigabit VPN Firewall (FVS318G) |
| Summary | Updated FVS318 w/ Gigabit ports and hardware DMZ port supporting 5 IPsec tunnels |
| Pros | • 8 port Gigabit switch • Switchable DMZ port • Bandwidth throttling • Reasonably priced |
| Cons | • No Jumbo frames • No VLANs • Doesn’t meet 7 Mbps IPsec tunnel throughput spec. |
NETGEAR has finally improved its mainstay FVS318 Firewall / VPN router, in the form of the FVS318G. The 318G has eight Gigabit LAN ports and new hardware DMZ capability. And it’s even smaller than its predecessor, while offering more features.
Physically, the 318G has undergone a few changes. It measures only 7.5” x 4.9” x 1.4”, while the 318 was 10” x 7.4” x 1.4”. All ports are now on the front and NETGEAR has gone with a gray metal case on the 318G versus the "business blue" on the 318. (NETGEAR says that "business grey" is the new "business blue" for its SMB products.) The power switch is gone from the back of the 318G, but it still has an external power wall wart.
Figure 1: The FVS318G at work
Figure 2 below provides a listing of the front indicators.
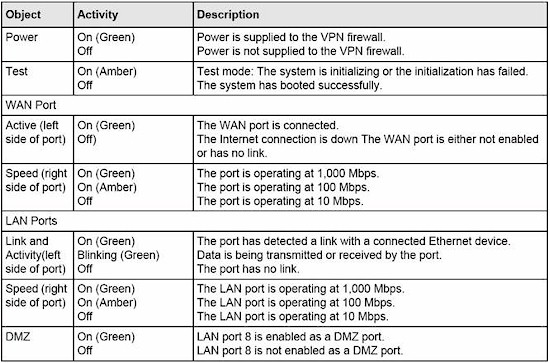
Figure 2: Front panel indicators
Figure 3 shows the spartan back panel.

Figure 3: Rear panel
My test version came with firmware 3.0.5-25, which isn’t released yet. So I downgraded it to the latest production firmware 3.0.5-24. I found the 318G’s software very similar to the software on the NETGEAR FVS336G which I reviewed in January 2008.
The 318G’s menu response seemed slower than the 336G’s, which I assume is due to the processor differences between the two routers (more shortly).
The focus of this review will be to look at the 318G’s strengths and what is new or different from previous models. Functionally, the 318G is more similar to the 336G than the FVS318, minus the 336G’s dual WAN ports and SSL VPN capability. So I’ll be making frequent comparisons between the 318G and 336G.
Internal Details
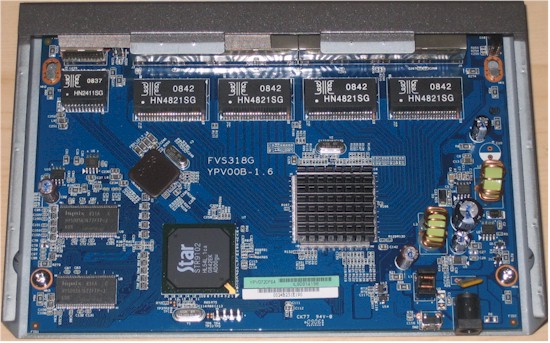
The photo below shows a Star (now Cavium) STR9102 as the "250 MHz" processor that NETGEAR specs, which is supported by 32 MB of RAM and 8 MB of flash.
Figure 4: FVS318G board
A Broadcom BCM53118 9-Port GbE Switch with 8 Integrated 10/100/1000 PHYs is hidden under the large heatsink and what appears to be a Broadcom Gigabit Ethernet PHY connected to the single router WAN port is under the smaller heatsink.
The 318G is midway between the 318 and 336G in terms of processor, RAM and flash as shown in Table 1.
| Component | FVS318 | FVS318G | FVS336G |
|---|---|---|---|
| Processor | Samsung S3C4510 | Star (Cavium) STR9102 | 300 MHz 32-bit RISC |
| RAM | 8 MB | 32 MB | 64 MB |
| Flash | 2 MB | 8 MB | 16 MB |
| Switch | Broadcom BCM5317 | Broadcom BCM53118 | Vitesse? |
Table 1: Key component comparison
New Features
The 318G lacks the dual WAN ports of the 336G, but supports a full range of routing features, including both NAT and Router modes, Dynamic DNS to four different providers (DynDNS, TZO, Oray, and 3322), dynamic routing (RIP), and static routing.
Of course a key improvement is the 318G’s Gigabit ports; one WAN and eight switched LAN. NETGEAR moved all ports to the front on the 318G, vs. the rear on the 318 and 336G. I like having the Ethernet ports in front since I’m moving cables around all the time. But it’s strictly a personal preference—you might be just as big a fan of rear-mounted ports and hate the 318G’s arrangement.
NETGEAR missed two key opportunities on the 318G’s switch, though. First, the 318G doesn’t have jumbo frame support. The MTU value on the WAN port can be changed to values other than 1500 Bytes to support various ISP requirements as shown in Figure 5. But there are no options on the LAN ports to change MTU size.
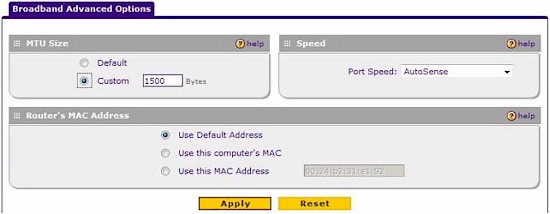
Figure 5: WAN MTU
Sometimes vendors don’t spec jumbo frame support, but enable them anyway. So I ran a test between two jumbo frame-enabled devices connected to the 318G’s LAN ports, and found I could not pass data with frame sizes larger than 1962 bytes. Technically, anything larger than 1500 Bytes is a jumbo frame. But typical jumbo frame devices use frame sizes of 4000-9000 Bytes, so the 318G fails the jumbo frame test.
Second, with eight LAN ports, I would like to have seen 802.1q VLAN support. Dividing a network into VLANs can provide a lot of value, including enhanced security and VoIP performance. In fact, the Broadcom BCM53118 switch used in the 318G supports VLANs, QoS and up to 9K jumbo frames. But NETGEAR hasn’t exposed any of those abilities.
The 318G does allow LAN Multi-homing, which can split the LAN into multiple subnets (see my review of NETGEAR’s FVX538). However, Multi-homing isn’t as useful as VLANs because it doesn’t separate broadcast domains. And the FVS318G’s LAN DHCP server only provides IP addresses in one subnet.
Security & Firewall
The Security menu has eight different sections, each with up to six subsections as shown in Table 2. The firewall uses a rules and services model, which is powerful, but sometimes confusing for less experienced networkers. Some services come preset in a pick list and you can define additional services if they aren’t in the list. Up to three different schedules can be created and applied to any rule.
The 318G also offers web traffic filtering based on keywords or URLs. MAC based filtering can also be applied, limiting network access to only known devices. Port Triggering is also supported to activate firewall rules when outbound traffic is detected on specific ports.
|
Security Menus |
Configuration Options |
|||||
|---|---|---|---|---|---|---|
|
Services |
Custom Services |
|||||
|
Schedule |
Schedule 1 |
Schedule 2 |
Schedule 3 |
|||
|
Block Sites |
Content Filtering |
Web Components |
Apply Keyword Blocking |
Keyword Blocking |
Trusted Domains |
|
|
Firewall |
LAN WAN Rules |
DMZ WAN Rules |
LAN DMZ Rules |
Attack Checks |
Session Limits |
Advanced (ALG) |
|
Address Filter |
Source MAC Filter |
IP/MAC Binding |
||||
|
Port Triggering |
||||||
|
UPnP |
||||||
|
Bandwidth Profile |
||||||
Table 2: Security menu summary
Next, let’s look at features that are different from the 336G’s, as well as a few of those I didn’t cover in my 336G review.
DMZ – One of the features lacking in the 336G was a Demilitarized Zone (DMZ) port. But the 318G has addressed that shortcoming. When enabled as a DMZ, port 8 is on a separate subnet, has a separate DHCP server, and traffic to and from port 8 is treated separately from traffic to and from ports 1-7.
There is a handy indicator light next to port 8 on the front of the 318G that is lit when port 8 is configured as a DMZ. When not enabled as a DMZ, port 8 functions the same as ports 1-7. Rules can be configured in the 318G to allow or block traffic between each of the three zones in the router, which are the WAN, LAN, and DMZ.
A potential use of a DMZ is to provide Internet access to guest devices, but not allow guest devices to access servers and other company resources on the LAN. This requires a firewall rule that allows traffic to and from the DMZ and WAN, but blocks traffic between the DMZ and LAN.
To test this scenario, I enabled the DMZ feature and connected my laptop to port 8. I received an IP address different from the IP address I received on ports 1-7, and couldn’t ping or Telnet to my devices in ports 1-7. Further, I couldn’t access the Internet. This means that the 318G’s DMZ blocks all traffic in and out of the DMZ until a rule permitting the traffic is created.
To allow my laptop to connect to the Internet from the DMZ, I created a rule to allow all services between the DMZ and WAN (Figure 6), which worked as intended.
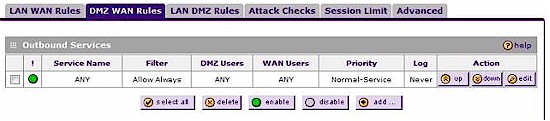
Figure 6: DMZ WAN rules
To test the DMZ’s flexibility, I created a rule in the LAN DMZ menu to see if I could allow traffic between the LAN and DMZ. The rule shown in Figure 7 also worked as intended. Of course, this rule defeats the purpose of having a DMZ port, so isn’t recommended!
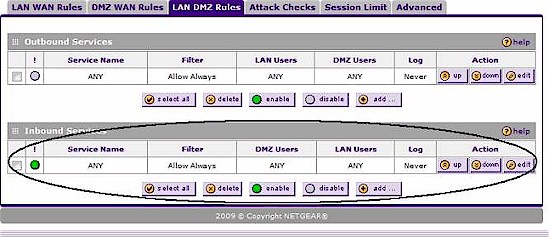
Figure 7: DMZ LAN rules
Note that rules can be disabled in addition to being deleted. This comes in handy for testing or temporary access control.
SIP ALG – As previously noted, the 318G’s firewall includes a SIP ALG (Application Level Gateway). A router with a SIP ALG changes the source IP address in the SIP header of a VoIP signaling packet to the router’s WAN IP address instead of the SIP device’s LAN IP address. This helps VoIP networks deal with private to public Network Address Translations (NATs).
The VoIP company I work for prefers customers disable ALGs, since our network has devices to overcome this problem. However, many other Service Providers and Enterprise VoIP networks find ALGs useful in maintaining VoIP connectivity behind NAT routers.
I enabled and tested NETGEAR’s ALG with a VoIP device set to connect to a public SIP server and ran a packet capture on the WAN interface of the 318G and Figure 8 shows the Wireshark output. The top circled IP address is the source IP address, which is my public WAN address, and the bottom circled IP address is the source IP address in the SIP header. As you can see, both addresses match.
Without an ALG, the addresses wouldn’t match. The bottom circled IP address would be a private LAN IP address (such as 192.168.1.44) In VoIP networks that can’t deal with different source and header IP addresses, call failures can occur.
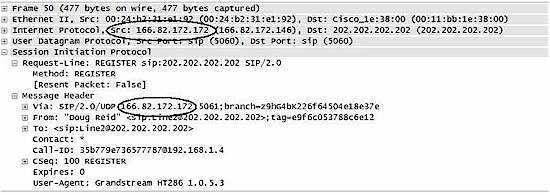
Figure 8: SIP ALG in action
UPnP – The 318G supports UPnP enable/disable and can display devices that have discovered the device through UPnP. With the UPnP feature enabled on the 318G, the router was detected and displayed as a “Linux Internet Gateway Device” in my Vista laptop’s View Computers and Devices display shown below. Double-clicking on the icon in my laptop brought me directly to the 318G’s web configuration page, which I found to be a handy way to locate and manage the router.
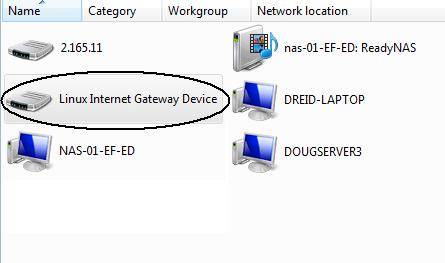
Figure 9: Admin access via UPnP
Bandwidth Profiles – The 318G can control how much bandwidth is used by specific types of traffic. For example, a Bandwidth Profile could be configured to limit FTP downloads to only 100 Kbps.
I tested this by running a speed test on my DSL service through speedtest.net, which showed 9.37 Mbps download and 630 Kbps upload throughput. I then built the Bandwidth Profile shown in Figure 10, applied it via the 318G’s firewall and re-ran the speed test to see if the router actually throttled my bandwidth usage. I then built a LAN WAN firewall rule to allow all traffic and applied the Bandwidth Profile to the new rule.
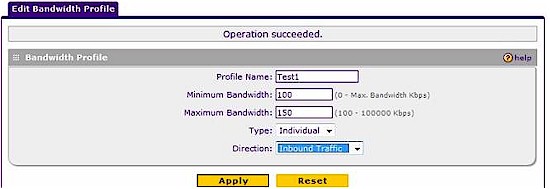
Figure 10: Bandwidth control
The Bandwidth Profile rule in Figure 10 should limit download bandwidth (Inbound traffic) to 100-150 Kbps. The Speedtest.net test result shown in Figure 11 shows download bandwidth after applying the Bandwidth Profile of only .14 Mbps, or about 140 Kbps, which is in the range of the configured Bandwidth Profile of 100-150 Kbps.
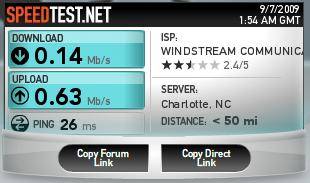
Figure 11: Bandwidth control test
I also disabled the firewall rule and re-ran the speed test again, confirming that bandwidth returned to normal.
Session Limits are another tool for bandwidth management. They cap the number of sessions each individual user can run simultaneously. In other words, using session limits could stop someone from surfing multiple web sites, downloading files, and streaming video simultaneously.
In all, I am impressed by the 318G’s security / firewall features.
VPN
The FVS318G supports up to five Site-to-Site and Client-to-Site IPsec tunnels (total, not each). All typical encryption algorithms are supported, including DES, 3DES, AES-128, AES-192, and AES-256.
The 318G comes with a single license for NETGEAR’s ProSafe VPN Client software, version 10.8.3, which installed easily on my Windows Vista laptop. The ProSafe VPN Client is a NETGEAR-branded version of SafeNet’s SoftRemote software (Figure 12) , which SafeNet lists on their website for $149 / license.
Figure 12: VPN client info
Unlike the 336G, the 318G doesn’t also support Client-to-Site SSL VPN tunnels, which provide secure access via web browser, or browser-downloaded applet. (However, I must point out that I recently had trouble with my 336G’s SSL VPN certificate, and haven’t been able to get it resolved.)
I was pleasantly surprised at how easy it was to configure an IPSec Client-to-Site tunnel on the 318G. I used NETGEAR’s Wizard to set up the router’s VPN Client configurations, and I found the NETGEAR manual useful in walking me through the configurations on the ProSafe Client Software. It took only a couple minutes to create the IKE and VPN policies on the router, install and configure the software on my laptop, and make a connection.
As with the 336G, NETGEAR offers a Mode Config option that allows remote VPN clients to be assigned an IP address in a different subnet than the devices on the LAN. This is a useful feature to restrict remote clients from accessing various services on the LAN.
I liked the fact that the 318G has a pop-up window within its menus that shows all the default values used by the VPN Wizard (Figure 13). One of the biggest challenges in configuring VPN tunnels is getting all the values on both ends to match. Matching values can be difficult when the end devices, such as a router and client software, have different field names and menu locations for the various values. So NETGEAR’s pop-up display listing the default values is very handy.
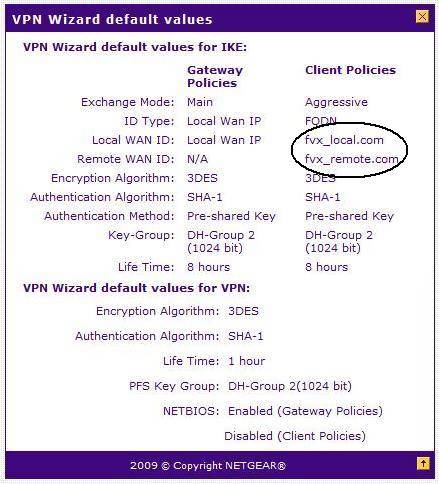
Figure 13: VPN wizard defaults
However, it would be more useful if all the values shown in the pop-up matched all the values used by the Wizard. The pop-up says the wizard’s default local and remote WAN ID values are fvx_local.com and fvx_remote.com as shown in Figure 13. Unfortunately, the 318G’s actual default local and remote WAN ID values are fvs318g_local.com and fvs318g_remote.com.
I caught this error when configuring my IPSec VPN Client tunnel. But folks less experienced with IPsec setup might not have caught it. I hope NETGEAR sorts this out in a firmware update.
I had no problem setting up an IPSec Site-to-Site tunnel between an FVS318G and an FVS336G. Since both are NETGEAR routers with similar menus, I used the VPN Wizard on both to create and enable a tunnel in minutes.
I also set up an IPSec Site-to-Site tunnel between the 318G and a ZyXEL USG100 to see if the NETGEAR would play well with another brand. It did, and was also quick and easy, using the VPN Wizards on both the NETGEAR and the ZyXEL to set up the configurations.
The FVS318G is rated to support up to 5 simultaneous IPSec VPN tunnels. Using my two other VPN routers, I was able to run 2 simultaneous Site-to-Site tunnels and a Client-to-Site tunnel for a total of 3 simultaneous IPSec VPN tunnels on the 318G (Figure 14).
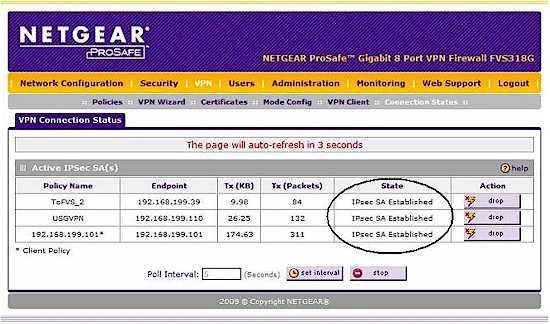
Figure 14: Three tunnels up
Additional VPN features on the 318G include the ability to add new certificates for security identification. NETGEAR includes a self-signed certificate, which worked fine for my IPSec VPN tests, but isn’t as secure as a certificate signed by a third party.
Performance
Tim put the 318G through the suite of router tests, with the results shown in Table 3, along with the 318 and 336G. Total Simultaneous throughput and Maximum Simultaneous Sessions results are not available for the FVS318, given that it was tested back in 2002!
| Test Description | FVS318G Throughput – (Mbps) |
FVS336G Throughput – (Mbps) |
FVS318 Throughput – (Mbps) |
|---|---|---|---|
| WAN – LAN | 22.5 | 59.2 | 7.0 |
| LAN – WAN | 22.9 | 58.3 | 7.0 |
| Total Simultaneous | 25.8 | 56.3 | N/A |
| Max. Simultaneous Sessions | 200 | 200 | N/A |
| Firmware Version | 3.0.5-25 | 2.2.0-67 | 1.0 |
Table 3: Routing throughput
Although the 318G won’t win any routing throughput competitions, it’s plenty fast for most DSL and cable business Internet connections, but not for fiber.
NETGEAR specs 7 Mbps throughput on IPSec VPN tunnels using 3DES encryption. To test this claim, I used the tunnel I created between the NETGEAR FVS318G and the NETGEAR FVS336G and ran throughput tests using iperf.
However, I wasn’t able to confirm NETGEAR’s 7 Mbps spec using TCP/IP traffic and 3DES encryption. After conferring with NETGEAR on my observations, I was informed that if I used UDP throughput tests and AES-128 encryption, I’d get higher measurements.
In Table 4, I’ve listed my VPN throughput measurements for the FVS318G. I ran several throughput measurements using TCP and UDP, with encryption set to None, 3DES, AES-128, and AES-256. As you can see, the 318G has higher throughput for UDP versus TCP transmissions. Further, the 318G has higher throughput with AES-128 encryption versus 3DES encryption. This isn’t surprising, since the computing load is lighter for AES-128.
| Encryption | Throughput (Mbps) | |
|---|---|---|
| TCP | UDP | |
| None | 6.81 | 12.2 |
| 3DES | 2.72 | 3.61 |
| AES-128 | 4.08 | 6.39 |
| AES-256 | 3.81 | 5.81 |
Table 4: IPsec test summary
The 3DES IPSec throughput of 2.72 Mbps for the 318G is certainly an improvement over the original 318, which we measured at less than 1 Mbps in the FVS318 review. However, other NETGEAR VPN routers, such as the 336G and the FVX538, easily outperform the 318G with 3DES IPSec throughput numbers of 16 Mbps and 12 Mbps, respectively.
The bottom line is that I wasn’t able to confirm NETGEAR’s 7 Mbps 3DES claim, even using UDP instead of TCP/IP. The only way I was able to approach 7 Mbps through-tunnel throughput was by using AES-128 tunnel encryption and UDP traffic.
I’ll note that using UDP for specing VPN tunnel performance is somewhat disingenuous, since most traffic passed over a VPN tunnel (E-mail, web, database / transactional) is likely to be TCP.
All that said, for typical cable and DSL Internet connections with upload speeds of 1-2 Mbps or lower, the 318G’s IPsec tunnel throughput shouldn’t be a huge issue. However, if you’re connecting VPN tunnels to the 318G over an ISP connection with upload speeds of 5 Mbps or higher, such as Verizon’s FIOS, the 318G will not be able to encrypt and decrypt data as fast as the network can carry data. But for that matter, its 22 Mbps routing speed won’t be able to keep up either.
Competitive Summary
The FVS318G presents a compelling combination of features at its price point. Let’s look at the comparison between the 318G and other similar devices including the older NETGEAR FVS318, the Cisco/Linksys RVL200 and RVS4000, as well as the NETGEAR FVS336G and FVX538 in Table 3. The table is sorted by price, with least expensive on the top. You can click on any of the models on the left to go to our review on that device.
| WAN Ports | LAN Ports | Tunnels | Throughput (Mbps) | Max Connects | Price | ||||
|---|---|---|---|---|---|---|---|---|---|
| SSL VPN | IPSec VPN | LAN-WAN | WAN-LAN | Total | |||||
| FVS318 | 1 | 8 | 8 | 7 | 7 | N/A | N/A | $97.13 | |
| RVS4000 | 1G | 4G | 10 | 530 | 15.9 | 525.6 | 48 | $116.84 | |
| FVS318G | 1G | 8G | 5 | 22.9 | 22.5 | 25.8 | 200 | $131.69 | |
| RVL200 | 1 | 4 | 5 | 1 | 38.9 | 36.9 | 38.6 | 180 | $167.12 |
| FVS336G | 2G | 4G | 15 | 25 | 58.3 | 59.2 | 56.3 | 200 | $245.00 |
| FVX538 | 2 | 1G, 8 | 200 | 77.5 | 79.6 | 81.9 | 200 | $359.44 | |
Table 5: Competitive Summary
I’ve listed the FVS318 in this chart for comparison purposes, but I wouldn’t consider the FVS318 an option with the release of the FVS318G. The 318G’s throughput and Gigabit ports make the 318 essentially obsolete. With the FVS318 out of the picture, the 318G is the only device with 8 LAN ports and VPN capability for under $200.
Note that performance numbers on the products generally align with price. The Cisco/Linksys RVS4000 is an outlier, however, with its super high LAN-WAN (and relatively unusable) throughput capability. Still, the RVS4000’s WAN-LAN throughput, which is a measurement of download capability, is lower than the 318G’s. Other than the RVS4000, the 318G’s throughput performance comes in right where you’d expect it based on its price, with a total throughput of 25.8 Mbps.
Closing Thoughts
NETGEAR has done a nice job with the 318G. In addition to the items tested in this review, the 318G has the ability to authenticate VPN users via an external Radius Server, send SNMP messages, keep track of traffic utilization, and email reports showing firewall detected activity and logs. Further, by adding a highly configurable DMZ to the firewall and including features found in the firewalls of its more expensive routers, the NETGEAR FVS318G provides a lot of configurable security options for a small network.
The 318G is a good IPsec VPN solution, and a relatively easy to use one at that. I had no problem configuring VPN tunnels between NETGEAR routers, as well as to a Zyxel router.
NETGEAR’s IPSec Client was easy to install and configure, and I had no problem using it with my Vista laptop, something I couldn’t say in previous NETGEAR VPN reviews. Ironically, I plan to upgrade to Windows 7 soon, which will probably create all sorts of new incompatibility problems for me with IPSec VPN Clients.
For Client VPN tunnels, though, I prefer SSL VPNs over IPSec VPNs. From an administration standpoint, SSL VPNs reduce the overhead of loading software on a client PCs. I don’t mind using an IPSec VPN application on my own laptop. But if I had to support multiple employees’ laptops, I’d choose the SSL solution every time.
I must say again that NETGEAR missed an opportunity to make this product really outstanding on the LAN side. The 318G has 8 Gigabit LAN ports, so why not support jumbo frames and VLANs? Since both Cisco routers I mentioned offer VLAN capability in the same price range, it seems I am not alone with this opinion.
And finally, I was disappointed to see that the VPN throughput numbers didn’t match NETGEAR’s advertised speeds. But the 318G is still an improvement over the 318.
With all this said, would I recommend the NETGEAR FVS318G? Yes I would. The 318G accommodates a growing network with 8 Gigabit Ethernet ports, has a customizable firewall, and provides usable VPN options at an attractive price point. Finally, NETGEAR offers the best guarantee for small network routers, a lifetime warranty, which is pretty hard to beat.