Introduction

| Netgear ProSafe VPN Firewall (FVS318) | |
|---|---|
| Summary | 8 port SPI based router with built-in IPsec endpoint for up to 8 tunnels. Also has content filtering and email hack alerts. |
| Update | None |
| Pros | • Scheduleable keyword-based website filtering • Built-in 10/100 8 port switch with auto MDI/MDI-X • Easy setup |
| Cons | • No port filtering • Admin interface can be irritating • VPN performance could limit some high-bandwidth connections • VPN tunnel doesn’t support NetBIOS broadcast (MS Network browsing) |
Judging from the number of requests that I received to review this product, NETGEAR’s FVS318 Cable/DSL ProSafe VPN Firewall has generated a good deal of interest. Although I found a lot to like, its VPN performance doesn’t set any speed records, and there are some rough spots that NETGEAR needs to smooth out…
Basic Features
The 318 comes in NETGEAR’s standard blue metal stackable cabinet. All indicators are on the front panel of the cabinet and include Link/Activity, and 100Mbps for each of the eight LAN ports, Link and Activity for the WAN, and Power and Test. All eight switched 10/100 LAN ports are on the rear, along with the 10BaseT WAN port, power socket, Power switch and Reset button.
All of the LAN ports are auto MDI/MDI-X (NETGEAR calls this “AutoUplink “), which means that you can connect any 10/100BaseT Ethernet device with either a normal or crossover cable, and the port will configure itself so that you get a connection. This eliminates the need for a dedicated or switchable “uplink” port, and is a feature that I’d like to see all consumer routers and switches have. Note that the 318 doesn’t support UPnP.
NETGEAR includes a printed Installation Guide, and Resource CD, and throws in a normal CAT5 patch cable to sweeten the pot. The CD contains:
- PDF versions of the Installation guide and Reference Manual,
- some helpful info on setting up port forwarding, including a list of ports used by popular applications
- setup information for major broadband ISPs
- a copy of the Adobe Acrobat Reader installer
- a copy of NETGEAR’s Installation Assist (more on this later)
- a copy of zer0knowledge’s Freedom Anti-Virus program (Version 3.2)
Setup
If you’re the type who doesn’t read manuals, maybe you’ll like NETGEAR’s Installation Assist application. I hadn’t used it before, but have to admin that it’s pretty slick. It runs in your web browser, and uses Flash animation to walk you through pretty much the same setup procedure described in the Installation Guide. Experienced users won’t find any value added here, but it just might help first-timers successfully get through the installation process without having to make that dreaded call to Tech Support.
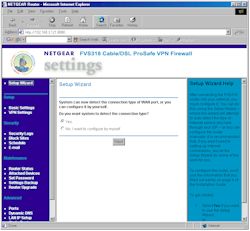
Opening the router’s default address for the first time 192.168.0.1 brings you to the Setup Wizard shown in Figure 1 below.
Figure 1: Setup Wizard
(click on the image for a full-sized view)
The Wizard’s main contribution is that it will auto-detect the type of connection you have and present you with the appropriate Internet connection configuration options. I don’t know how the Wizard does this, but it detected my Dynamic IP type connection without a problem. All the normal connection types and authentication methods are supported so you shouldn’t have a problem getting connected to your ISP.
The 318 automatically checks a NTP server (you can specify the IP address of your favorite one, or just use the default one) for the correct time once it gets connected to the Internet. The only thing you have to do is set your Time Zone and whether your location observes Daylight Savings time.
The overall responsiveness was good with screens coming up quickly and changes only taking a few seconds to be registered.
Remote Management can be enabled (it’s off by default), and you can set the port used and restrict access to a single IP address or range of addresses if you like. That gives you some measure of security, but it would be better if you could access the admin interface of a remote 318 via the VPN tunnel, which you can’t. You also can’t reboot the router via the admin interface, but can do a reset-to-factory-defaults (!), and save and load router settings to/from a local file.
The 318 does not allow multiple administrator logins at a time and tells the second would-be administrator the IP address of the current admin. NETGEAR has thoughtfully provided both a admin log-out function and the ability to set the time for auto-logout of an inactive admin session (I wish all manufacturers did this!)
The Interface does have some problems that became quite irritating in my short time with the product. I hope NETGEAR fixes them as soon as possible. Here’s my list:
-
Although I applaud the right hand “Help” frame, which automatically changes from screen to screen to provide an easy reference, I don’t like the fact that you can’t resize or get rid of it. Expanding the browser window doesn’t help, since the Help frame is the only frame that expands in size! It’s silly (and frustrating!) to constantly have to scroll the middle frame back and forth when you’re trying to read the Security logs, for example, because the log field doesn’t size itself to fit the frame.
-
The method of popping up another window for each of the four status screens was equally frustrating. First, the new window wasn’t always automatically brought to the front. Second, all four of the different statuses have the same target window, making it impossible to view more than one status at a time! This made debugging a VPN setup particularly hard (see next item). Finally, the status window can’t be resized!!! This design is not user friendly at all and really needs to be reworked
-
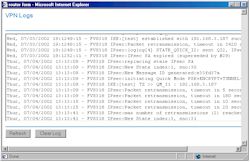
As I said above, the single status window method made VPN setup debugging much harder than it needed to be. Because of the fixed-size window (see Figure 2), I had to constantly scroll back and forth in the window get to the log window’s scroll bar. This caused me to get confused as to the time of the event that I was looking at.
There are also bugs in the log’s time stamps, which you’ll see if you click on Figure 2 and look at the highlighted area on the full-sized view. In addition to this obvious problem, I also found out-of-sequence time stamps (I thought I was imagining this at first), which made it difficult to figure out whether new events were added to the top or bottom of the window (they’re added to the bottom), even though the 318 writes “End of Log” into the log stream. Finally, I found that the log cleared itself from time to time for no reason.
 NOTE! I found two bugs in the admin login:
NOTE! I found two bugs in the admin login:
1) When you try to log into the router after being automatically logged out due to inactivity, you’ll be presented with the authentication/login box, but you’ll see the admin interface be refreshed in the browser window. If you just cancel the login box and refresh the browser, you’ll be back in without having to re-enter your login info. If you quit your browser between the time you’re auto logged out and when you try to re-login, you’ll have to enter the proper login info, however.
2) If an administrator (let’s call them Admin #1) quits their browser without logging out of the router and then Admin #2 else tries to log in from a different computer, Admin #2 will get the “Duplicate Administrator” message and not be able to log in. Admin #2 will have to wait until the auto-logout time expires, or have Admin #1 log back in from Admin #1’s computer, then log out to free up the session.
I guess I’ve beaten this to death, so let’s go check out the Firewall features.
Firewall, Port Mapping, Filters
The 318 features a SPI-based firewall, with a typical set of features. You can statically forward up to 10 ports or port ranges (no protocol selection), and put one computer in DMZ (outside the firewall). You can leave port forwarding information in the router and just enable / disable the forwarding when needed, but you can’t schedule the enabling for certain times of day or days of the week. Folks who run servers will appreciate that server “loopback” is supported.
Curiously, there are no port filters, so you can’t block, say, the ports needed for certain games or file-sharing services. Because this was such an obvious omission, I asked NETGEAR about it and they said that they will support port filtering in a future firmware release, but gave no time frame.
You do have the ability to control the websites and newsgroups that your users visit via the Block Sites feature shown in Figure 3.
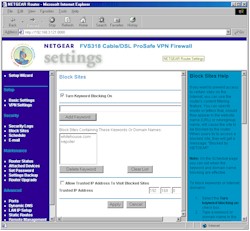
Figure 3: Block Sites
(click on the image for a full-sized view)
Block sites works by having you enter any portion of a website address (not including “http://”) for websites and newsgroups that you want to block. You can enter up to 32 keywords, each of which can be up to 32 characters long. The filter works by doing a wildcard match of the entered string against the URL or newsgroup name. If there’s a match, a “blocked” message appears on the user’s screen.
Logs of blocked attempts for filtered sites are sent to the security log (more on that later), and will be emailed to a single email address immediately, hourly, daily (you specify the hour), or when the log fills up.
Blocking can be scheduled for every day, or just specific days of the week. But you get only one time period that will apply to all selected days. For those who don’t want no steenking filters, you can enter one IP address that will get unfiltered Internet access.
So much for the firewall. On to the VPN features!
VPN Performance
There are three key differences among inexpensive VPN endpoint routers: the VPN standard they support; the throughput when using the VPN tunnel; and the configurability of the tunnel setup and operating features. The 318 is similar to many other inexpensive VPN endpoint routers in that its endpoint supports the IPsec protocol only. Although IPsec is becoming more common in VPNs, this limitation means that you won’t be able to use the endpoint feature if the remote VPN gateway that you’re trying to connect to uses another VPN protocol such as PPTP, L2TP, or a proprietary protocol. In that case, you’ll have to rely on the router’s VPN pass-through features, which require that you run the proper VPN client software on each computer that needs a VPN connection.
The second similarity of the 318 to other products is that it does not use a hardware co-processor for the IPsec encryption. This means that the connection speed through the VPN tunnel will be much slower than you’ll get with non-VPN connections, and may not be adequate if, for example, you transfer a lot of large files through the VPN tunnel.
Finally, the configurability of the 318’s VPN features may be ultimately what determines whether it will work in your VPN setup. If you’re using a pair of them to set up an IPsec VPN between two sites, you’ll be ok, and NETGEAR will provide support to get your connection working. However, if you’re just using one 318 on your home LAN to connect into your company’s VPN, or you want to have a VPN connection from one remote computer into your home’s LAN, you’d best read the disclaimer that appears a few times in NETGEAR’s User Guide:
Note: The FVS318 VPN Firewall uses industry standard VPN protocols. However, due to variations in how manufacturers interpret these standards, many VPN products are not interoperable. NETGEAR provides support for connections between two FVS318 VPN Firewalls, and between an FVS318 VPN Firewall and the SafeNet Secure VPN Client for Windows. Although the FVS318 can interoperate with many other VPN products, it is not possible for NETGEAR to provide specific technical support for every other interconnection.
Although you may not like NETGEAR’s restriction, or the fact that the SafeNet client costs $149, I give them points for at least being up front in their position so that buyers can make an informed decision. In poking around on NETGEAR’s support site, I found indications that they are working on applications notes that will describe how to set up a VPN connection to some of the more popular VPN products. But right now, there’s nothing that you can download… not even instructions on how to connect to the built-in IPsec client in a Win 2000 or XP machine.
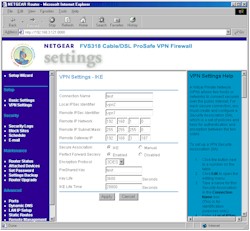
I used a subnet-to-subnet configuration with static IPs for the remote gateways, and IKE (automatic) Association mode to set up my test tunnel between two 318s. The setup screen for one router is shown in Figure 4 below. Note that I had to change the base IP address of one of the routers from the factory-default 192.168.0.1 to 192.168.1.1, so that the routers (and I!) wouldn’t get confused trying to route between two identically-numbered subnets.
Figure 4: VPN IKE
(click on the image for a full-sized view)
If you need finer control over your tunnel setup, you can choose Manual Association mode, which changes the screen to present the different setup options shown in Figure 5 below. Note that neither mode gives you control over what happens during Phase 1 and 2 of tunnel setup, which might be needed if you’re trying to connect to a different manufacturer’s gateway. You can’t select whether the
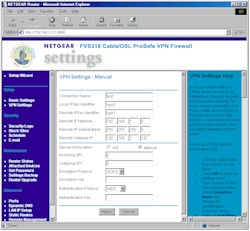
Figure 5: VPN Manual
(click on the image for a full-sized view)
I had no trouble getting my test connection established once I finished entering the setup information (which is good, given my frustration with the VPN Status and Log screens that I’ve already described!). All I had to do was try to access a computer on the “remote” end of the tunnel (the User Guide suggests just pinging the computer on the other end of the tunnel) and the routers established the tunnel automatically. That was good, because although there’s a button in the VPN status screen to drop a connection, there’s no “connect” button anywhere to be found!
Finding a computer on the remote end, however, was a little bit of a challenge, since the 318 does not support NetBIOS broadcast. This means that remote computers won’t appear in Network Neighborhood (or My Network Places) and you’ll have to do a little more work to connect to them.
Once I was connected, I used Qcheck to test the performance of the VPN tunnel. Having previously tested the MultiTech RF550VPN, which also does not use an IPsec hardware co-processor, I wasn’t surprised at the throughput, which came in about 800kbps. This is about 1/8 the speed that you’ll get running a normal, un-encrypted connection. Response time (latency) is a little higher than you normally see in non-VPN routers, but still acceptable. UDP streaming performance, however, shows that the router was having a hard time keeping up with UDP data coming at it at 500kbps, although when I reduced the rate to 100kbps, the error rate dropped to 0%. Performance was pretty much the same in both Local-to-Remote and Remote-to-Local runs for all tests.
IPsec VPN Performance Test Results
| Test Description | Transfer Rate (Mbps) [1 MByte data size] |
Response Time (msec) [10 iterations 100 Byte data size] |
UDP stream [10s @ 500kbps] |
|
|---|---|---|---|---|
| Actual throughput (kbps) | Lost data (%) | |||
| Local to Remote | 0.82 | 8 (avg) 10 (max) |
260 | 48 |
| Remote to Local | 0.79 | 8 (avg) 10 (max) |
265 | 47 |
| Firmware Version | V1.0 Apr 16 2002 | |||
See details of how we test.
Logging
I’ve already touched on the 318’s logging features, but I’ll tie up the loose ends here. The Security Log feature records “console” type events such as admin logins, port scans and other “attack” type events, and attempts to access blocked websites or newsgroups. But, as the name implies, you don’t get general traffic logging.
You can view, clear, refresh, and immediately send the log to one designated email address, and you can schedule the emailing of the log, or have an email sent immediately whenever a “security event” is detected, too. However, your view of the log itself is hampered by the same frame-is-too-small problem that the VPN log window has, and you’ll have to constantly scroll back and forth to work your way through the log.
Other Features
The router has a few other features that I haven’t mentioned, such as:
- you can set the router’s MTU (Maximum Transmission Unit) value (useful in getting some PPPoE-based connections to work)
- you can set and view 8 static routes (useful in networks that have more than one subnet)
- dynamic routing protocols RIP1, RIP1 compatible (transmit only) and RIP 2 send and receive are supported
- you can enable the router to respond to WAN ping requests (this is disabled by default, which is good security practice)
- dynamic DNS support is built-in for using dyndns.org.
Routing Performance
The test results above show non-VPN performance typical of a well-designed present-generation router. The only weak spot seems to be WAN-LAN UDP streaming performance, which shouldn’t be a problem.
Routing Performance Test Results
| Test Description | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
|---|---|---|---|---|
| Throughput (kbps) | Lost data (%) | |||
| WAN – LAN | 6.8 | 2 (avg) 2 (max) |
431 | 13 |
| LAN – WAN | 6.7 | 2 (avg) 3 (max) |
499 | 0 |
| Firmware Version | V1.0 Apr 16, 2002 | |||
See details of how we test.
Wrap Up
The main thing the FVS318 has going for it, in what is fast becoming a commodity market segment, is the fact that it’s an 8 port product, at a price the other guys charge you for 4. VPN performance is par for a product that doesn’t have an IPsec co-processor, and will be ok if your VPN traffic isn’t too heavy. But if you need to move lots of big files securely back and forth, you probably won’t be happy.
But what I’d really like to see is a version of this baby with the admin interface fixed, sporting an IPsec co-processor, and priced to sell! Now that would make the market share battle much more interesting!