Introduction

| U.S. Robotics Secure Storage Router Pro (USR-8200) | |
|---|---|
| Summary | SPI-based router with IPsec and PPTP VPN endpoints and ability to file share up to 30 external USB / Firewire hard drives. Runs on OpenRG / Linux software platform |
| Update | 10/28/2003 – Corrected processor type |
| Pros | • Near wire-speed routing • Supports SMB-based file sharing & FTP with optional USB or Firewire hard drive • Good UPnP integration • Has both PPTP and IPsec VPN endpoints |
| Cons | • No schedulable firewall features • Firewall and VPN configuration can be confusing • Documentation doesn’t do justice to the feature set |
It took only a few years for broadband routers to move from slow, expensive ($300 or so), hard-to-configure beasts with small feature sets to zippy, (almost) auto-configuring, full-featured and even physically attractive products that are commonly available for under $50. You can imagine what this price drop has done to manufacturers’ margins, and they’re all on a quest to get you to part with more of your money.
Adding VPN “endpoint” features has been one way to squeeze more out of our wallets and has met with moderate success. But U.S. Robotics’ USR8200 Secure Storage Router Pro has another “value proposition” to offer. It remains to be seen, though, how successful it will be at customer cash extraction.
Basic Features and Internals
The 8200 comes in USR’s signature plastic charcoal gray enclosure used by many other of their broadband networking products. But the 8200 has a larger footprint – a little over 9 inches wide and 5.5 inches deep. However, USR has thoughtfully arranged the cutouts in the 8200’s case so that the smaller footprint USR devices can still be stacked on top.
All LEDs are on the front panel and bright and readable from a wide angle. The indicator lineup includes PWR, WAN, USB1, USB2, 1394(Firewire) and Link/Activity/Speed for all four switched 10/100 LAN ports, which are on the rear panel.
Also bringing up the rear (panel) are the 10/100 WAN port, power socket, and Reset / Reset-to-Factory button. You won’t find a Normal/Uplink switch or shared Uplink port because all ports – WAN and LAN – are auto MDI / MDI-X. This means they’ll figure out how to connect to whatever you plug in, no matter whether you use a normal or crossover cable.
My pre-production sample didn’t come with final retail packaging, but had a UTP cable, printer quick install poster and CD. In addition to an HTML-based User Manual, the CD has a demo copy of Norton Internet Security and a bandwidth speed monitoring utility. The User Manual has the essentials, but lacks a lot of information that I think you’ll need to properly configure the 8200’s firewall.
The 8200 is based on Intel’s IXP422 network processor with 16MB flash and 64MB of DRAM, running Jungo’s OpenRG, which is – according to USR – based on Linux kernel 2.4.19. VIA VT6202 and 6307S Host Controllers provide USB 2.0 and Firewire capabilities respectively. Note that the IXP422 has integrated hardware acceleration for the SHA-1, MD5, DES, 3DES, AES encryption algorithms used by IPsec tunnels.
USR is considering releasing a SDK to allow third-party development of additional capabilities, but they have work to do to implement safety mechanisms so that a module having problems won’t shut down the rest of the router.
My performance testing found the combination of IXP422 and OpenRG to be a pretty powerful combination, but I’ll save those results for later.
Setup and Administration
The 8200 comes set to 192.168.1.1 and with its LAN DHCP server enabled. So as long as you have a client computer set to obtain its IP address automatically, you’ll be connected to the browser-based admin interface in no time.
I’m pleased to report that the first thing the 8200 does is force you to set an admin password. Yes, you can always set an easy to guess one, but you can’t set a blank one, and at least there won’t be a well-known default password known to every cracker trolling for 8200s to get into.
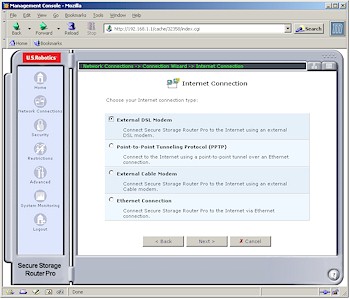
WAN connection setup is handled by the Connection Wizard on the Network Connections screen. I can appreciate that USR is trying to make things easy for less-knowledgeable users, but I found the organization of this section hard to navigate.
The first screen is simple enough, presenting choices of Internet Connection, Connect to a Virtual Private Network over the Internet and Advanced Connection. Once in Internet Connection (Figure 1), the choices seemed easy, but in reality ended up being confusing due to missing configuration options in the Wizard screens.
Figure 1: Internet Connection
(click on the image for a full-sized view)
And to make things even more confusing, the common option of Point-to-Point Protocol over Ethernet (PPPoE) is located in the Advanced Configuration section along with Network Bridging and PPTP and IPsec setup wizards. Turning to the HTML-based User Manual for help proved fruitless in most cases, since it tends to contain the “What” of each feature and little to nothing of the “Why”, “How” and “When”.
At any rate, I think most common WAN configurations are handled but I couldn’t find options to enter domain or host names and I suspect SingTel RAS and BigPond authentication isn’t supported.
In general the Admin interface is pretty responsive and I didn’t find any settings that required long reboot cycles for saves. If you do reset the 8200, however, it takes about a minute. But at least the admin page auto-refreshes when the router comes back up. And of course it automatically checks an NTP time server (you can’t select which one, however) for the correct time once it gets connected to the Internet.
Multiple Admin logins are supported but no warnings are issued. Remote admin via Telnet (you get access to an OpenRG command-line interface) and HTTP can be enabled and disabled with selection of only Ports 80 or 8080 for HTTP and 23 and 8023 for Telnet. You can also enable / disable incoming SNMP, ping, and traceroute queries. Everything I mentioned is disabled by default. Missing in action is the ability to restrict access to remote admin features, but a big plus is that I found I could access the admin interface via a VPN connection.
What’s Happening
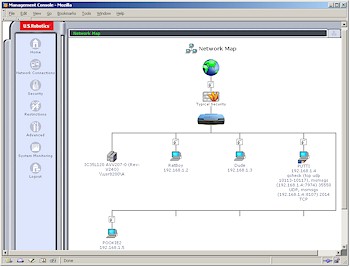
The main mechanism for getting an overview of the 8200’s setup is its Home / Network Map page shown in Figure 2.
Figure 2: Network Map
(click on the image for a full-sized view)
At first I thought this was just a cutesy way to show what’s going on in the router. But most of what you see is clickable and takes you to a screen for administering that section of the product.
An even nicer touch is the information you see for the client PUTTI (no cracks about the client names please…). Each client shows a list of any ports that are opened it. In addition to ports specifically opened by using the DMZ or Local Servers features, ports automatically opened by UPnP NAT Traversal are also shown! I’d still prefer to see products ask permission before automatically opening ports, but at least the 8200 shows some indication of the lessened security provided courtesy of UPnP NAT Traversal.
In the beginning, I really liked the Network Map and the overall interface. But, after my few days with the 8200, I found I grew to like the interface less. I found myself hunting around to get back to particular configuration pages, and just happening to stumble across others. Setting up firewall features was tedious, especially with no way to assign groups of LAN clients to the same rule sets.
Firewall Features
Once I started to dig into the 8200’s firewall configuration, however, I found the Network Map doesn’t reflect its Access Control (Port / Service filters) settings. Ok, so maybe that’s not so bad, but I found the Access Control tab didn’t reflect controls put into effect by the Security > General tab, which I think is a bad thing.
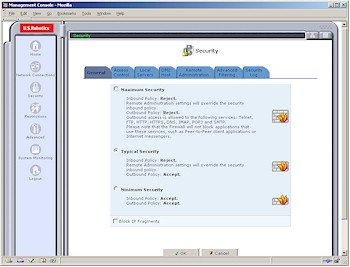
The Security tab offers three general Security levels – Maximum, Typical, and Minimum (Figure 3).
Figure 3: General Security Levels
(click on the image for a full-sized view)
Maximum allows all clients access to only Telnet, FTP, HTTP, HTTPS, DNS, IMAP, POP3 and SMTP services and is the default setting. I bumped into this early in my testing when I found that an SSH program that I use wouldn’t work – no thanks to the (lack of) information in the Access Control page. A quick change to the Typical setting fixed the problem.
But I’m puzzled by the inclusion of the Minimum setting, and its name. Since it essentially removes the 8200’s firewall by Accepting all Outbound and Inbound traffic, I think it would be more appropriately titled No Security and have some explanatory warning as to the security risk this setting exposes your LAN to. Although USR isn’t unique in its use of a Rule and Service firewall model, I think it is unique in providing access to an Accept All rule for Inbound traffic, which essentially turns off the 8200’s firewall protection.
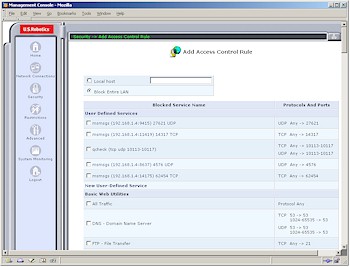
Figure 4: Access Control
(click on the image for a full-sized view)
At any rate, if you do want to set up Access Controls, the 8200 tries to make it easy by presenting an extensive list of pre-made filters that you can just check off (Figure 4). But then it makes it difficult by allowing you to set those filters only for either the entire LAN or a single IP address (or computer name) at a time. At least you can edit and temporarily disable rules, but there’s no ability to schedule them to be in effect during specific days and time periods.
Inbound port forwarding (Local Servers) setup looks and works pretty much like the Access Controls, except you don’t get an “entire LAN” option. As with Access Controls, Local Servers aren’t schedulable. Triggered port mappings are not supported, but “Loopback” for Local Servers is.
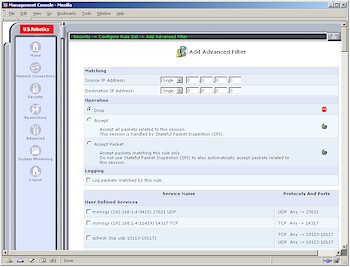
If these simple filtering options don’t suit you, and you have some experience in setting up multi-stage firewalls, you can try the Advanced Filtering features.
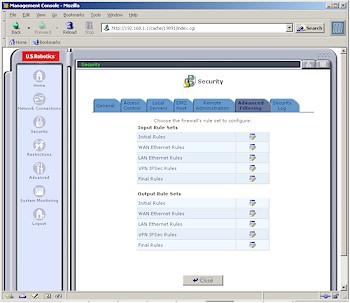
Figure 5: Advanced Filtering
(click on the image for a full-sized view)
Figure 5 shows the available rule sets and Figure 6 shows just some of the settings for each of the sets. The good news is that this is pro-level firewall configuration ability.
Figure 6: Advanced Filtering Rules
(click on the image for a full-sized view)
The bad news is that you’re on your own to figure out how and when to use this powerful capability and which of the rule sets to apply. The HTML User Manual is no help, and (at the time of review) there aren’t any applications notes to help either.
Rounding out the firewall’s features is the Restrictions feature. This is basic URL level filtering, but Figure 7 reveals a problem with USR’s implementation.
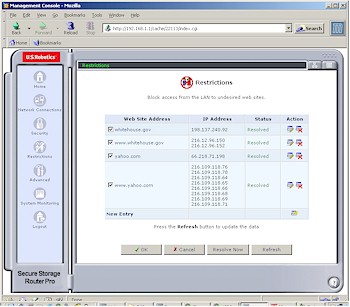
Figure 7: Restrictions
(click on the image for a full-sized view)
Clicking the New Entry link allows you to enter only IP addresses or URLs that can be resolved to IP addresses. You can’t enter just words or wildcard forms of URLs, i.e. *.yahoo.com. Figure 7 shows that two of the websites that I randomly chose resolve differently in their www and root forms. So entering www.whitehouse.gov would not block a user who tries to surf to whitehouse.gov.
Other limitations are that the Restrictions apply to all LAN users and you can’t set a “trusted user”. Options to block proxies, Java applets and Active X controls and Cookies also aren’t supported.
Let’s move on to the VPN features and performance.
VPN
There’s a lot of VPN power in the 8200, given that it supports IPsec and PPTP both in pass through and endpoint modes. The problem, I found, is getting to that power, and neither the Connection Wizards nor the User Manual seemed to be much help.
The Connection Wizard was pretty clear in its options of Point-to-Point Tunneling Protocol and Point-to-Point Tunneling Protocol Server that allow the 8200 to connect all LAN clients to a remote PPTP gateway and allow individual users to connect via PPTP connections respectively. The wizards ask only for the basics, though, and you may need to get to the Advanced settings screen (Figure 8) to change settings, or at least to figure out how to set up your PPTP client.

Figure 8: PPTP Advanced Settings
(click on the image for a full-sized view)
Once you set up the PPTP server, you’ll need to make a visit to the Users page (more later) to set up an account for each user who’ll be visiting the PPTP server.
IPsec wasn’t as easy, however. Its Connection Wizard provided only Network-to-Network and Gateway-to-Gateway options, neither of which seem to describe what I wanted to do – connect via an IPsec tunnel with a WinXP client running an IPsec client. So I just picked an option, completed the Wizard entries, then went into the Settings (Figure 9) to tweak things.
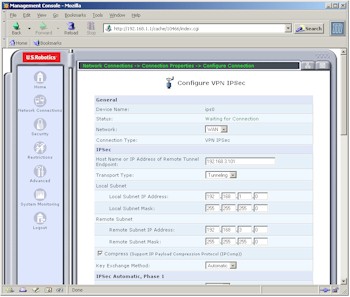
Figure 9: IPsec Settings
(click on the image for a full-sized view)
Although the settlings look like they’d provide what I wanted, entering a remote endpoint and remote subnet in the same Class C subnet (192.168.3.X) threw an error. I was able to successfully get a tunnel working when I switched to using a Linksys USBVPN1 [reviewed here] attached to my notebook instead of an IPsec client.
The 8200 looks like it has a pretty comprehensive selection of connection options – some more of which are shown in Figure 10 – including an option to allow the use of Authentication Header (AH) protocol during Phase 2 negotiation, which isn’t normally found in this class of IPsec device. But, once again, you’d better know what you’re doing with these settings, because the Wizards and supplied documentation will be of little help.
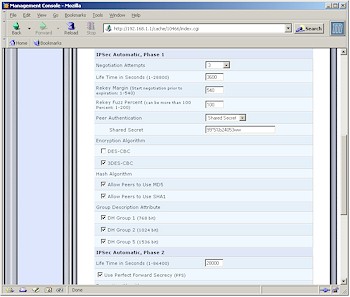
Figure 10: IPsec Key Exchange Phase 1 settings
(click on the image for a full-sized view)
VPN Performance
Once I made it through the setup, however, I found throughput to be surprisingly high. Figure 11 shows a composite Chariot plot of PPTP throughput test results in both Local-to-Remote and Remote-to-Local directions.
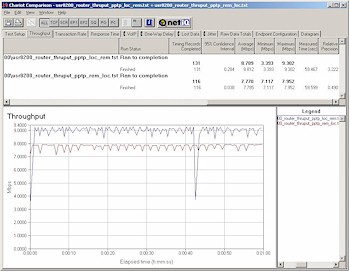
Figure 11: PPTP throughput
(click on the image for a full-sized view)
The PPTP client was a 1GHz Celeron-based notebook running WinXP home and using Microsoft’s built-in PPTP adapter. Note that these results were obtained with no other traffic running through the router and nothing else besides Chariot and its endpoint running on the test pair machines. Although the 8-9Mbps performance is for a PPTP tunnel which is less compute-intensive than IPsec, I think it’s still pretty impressive!
But since it’s unlikely that you’ll be running your network this way, I did a second test shown in Figure 12.
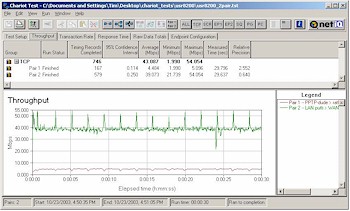
Figure 12: Two pair test – PPTP, LAN/WAN
(click on the image for a full-sized view)
This test used two pairs of computers, with each pair having a machine on the LAN and WAN side of the router. I set the Chariot script to send data via a normal LAN to WAN transfer between one pair, and via a PPTP tunnel in the Remote to Local direction between the other. The results show the 8200 was able to handle both normal NAT and PPTP chores with plenty of throughput for each task.
On a negative note, however, I found that disconnecting the PPTP session from my WinXP Home client locked up the 8200 each time and required a power cycle to get the router operating again.
Since I couldn’t get an IPsec tunnel running directly from an XP client, I wasn’t able to really test IPsec throughput. USR told me they have tested over 150 simultaneous IPSec connections with “typical throughput scenarios” without seeing any serious degradation in performance. They also “maxxed out” the number of PPTP connections without any performance issues.
USR says the only hard limit on number of connections is 254 – the number of IP addresses in a Class C subnet. So unless you run a lot of large file transfers through multiple IPsec tunnels, it looks like you won’t have any trouble with the 8200’s VPN performance.
Logging and Other Features
Given everything that the 8200 can do, its logging features pale by comparison. There are separate Security and System log screens, which can be cleared, but not saved, and don’t appear to allow capture of multiple screens of log information. Most of the interesting stuff goes to the System log, including plenty of Linux system console-type messages. But this stream also suffers from useless information overload, like the Byte-by-Byte reports generated by my test PPTP connection.
There’s also no syslog or SNMP trap capability for capturing log streams, but logs can be emailed if you enable the feature and enter your SMTP server and email address. I tried this out and logs did show up in my Inbox, but the contents weren’t that useful.
In general, this area needs lots more work to allow better control over logged information and the addition of website traffic logging.
The list of miscellaneous features is long and I kept discovering links to things that didn’t have useful explanations in the documentation. Some of the more easily understood features are:
- you can set and unlimited number static routes
- RIP 1 and 2 dynamic routing protocols and multicasting are supported
- you can have the 8200 automatically check for firmware upgrades and either upgrade automatically or send an email advising you of the upgrade
And, of course, this doesn’t include the 8200’s file serving features, which I’ll cover next.
Storage and File Serving
The new twist that the 8200 brings to the SOHO / SMB networking “appliance” party, however, is its ability to handle SMB and FTP-based file serving simply by adding a USB 2.0 or IEEE 1394 (Firewire) drive. Actually, USR told me that the 8200 will handle up to 30 drives connected to it, but only three – two USB and one Firewire – can be directly attached to the built-in ports.
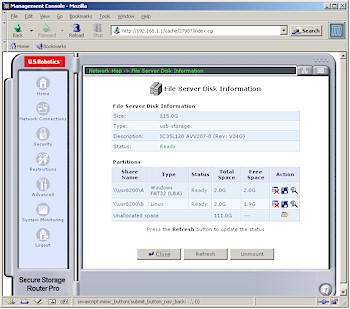
Figure 13: Disk Information
(click on the image for a full-sized view)
Once you attach a drive and power cycle the 8200, a drive icon will appear (refer back to Figure 2) that, when clicked on, will bring up the Disk Information screen (Figure 13). Just the essentials are here, which include the ability to create, format, check and delete partitions as well as mount and unmount the entire drive.
The 8200 uses SAMBA which is based on the SMB (Server Message Block) protocol. This means that systems running pretty much any OS should be able to access the 8200’s network shares.
Permissions are set on the Advanced > Users page (Figure 14), which you can see is not very sophisticated.
Figure 14: User Settings
(click on the image for a full-sized view)
You can only control whether a user has read and/or write privileges to all shares – no directory or even partition level access control is possible. You can see the other user settings possible from the screen shot, which include control of access via PPTP when the PPTP server is enabled.
FTP access to files is controlled via the Advanced > FTP screen (Figure 15).
Figure 15: FTP Server
(click on the image for a full-sized view)
Controls here are also pretty basic but will get the job done if your needs are simple.
The file sharing and FTP features need more work including bugfixes – I seemed to be able to access things that I didn’t think I had permissions to – and addition of better access controls. Note that the firmware that I tested didn’t allow controlling file sharing and FTP access separately.
Routing Performance
Testing Notes:
• All tests were run with LAN endpoint in DMZ
I don’t have much to say about the throughput results other than they’re damned impressive and make the 8200 the routing throughput champ of all the routers I’ve tested!
I also ran the UDP streaming tests at 1Mbps and the 8200 didn’t even flinch, turning in 1Mbps throughput with 0% lost data.
Routing Performance Test Results
| Test Description | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
|---|---|---|---|---|
| Throughput (kbps) | Lost data (%) | |||
| WAN – LAN | 63.0 | 1 (avg) 1 (max) |
500 | 0 |
| LAN – WAN | 57.5 | 1 (avg) 1 (max) |
499 | 0 |
| Firmware Version | 2.5.31 | |||
See details of how we test.
Wrap Up
In general, I have mixed feelings about the 8200. On the plus side is its routing and VPN performance, which are unmatched by anything else I’ve tested to date. Its feature set is also extensive, but accessing and understanding those features will be difficult for many users, given the exsiting documentation.
I guess I have to say that the 8200 is a diamond in the rough, and needs a firmware release or two of bugfixing and feature additions before it will really sparkle. Since it’s also a first-in-category product, it may need some time to find its target customer base. Its pricing – around $250 at the time of this review – will make it a pass for most home networkers, but still within reach of the home office / telecommuter/ SMB crowd – even with an external drive which will add, at minimum, about $100 to its price.
And in the end, that’s the real question: Is the combination of a PPTP and IPsec VPN endpoint router with optional file sharing and FTP capabilities – but no file or folder-level permissions – a compelling buy? I think it could be, but USR has some work to do before it is.