Introduction
These days, you can find a hot spot pretty much anywhere, allowing you free access to roam the Internet without much of a problem. But this isn’t exactly a safe way to browse the web, securing any content you might log in with, or post on a webpage that’s not the most secure. On the other hand, you might just not want people to know what you’re browsing.
I’ve found many uses for the technique that I’ll be describing; it even beats almost all of the content filters out today, providing the ability to securely access whatever you want, so long as you have a few small requirements.
Client / Server Setup
You’ll first need an SSH daemon. You can find these anywhere and most webpage hosts give you a login for one when you purchase hosting. You can also use a Linux box of some sort on your home network (This is my method of choice.) This will run remotely, you just need to be able to log into it using an SSH client.
Next, you need an SSH client that supports SSH Tunneling. I’ve used PuTTy for years, so it’s my client of choice.
Finally, you need a network that you don’t trust, or that you would just like to cover your tracks on.
I use Firefox for my secure browsing so that I don’t have to worry about constantly reconfiguring my browser. I just log into PuTTY, and then open Firefox. This method leaves my Internet Explorer untouched.
I’m assuming the SSH server is already set up. You just have to be able to remotely log in using an SSH client. The majority of Linux distros support this right after the OS is installed (assuming you didn’t install a firewall).
I’m using Ubuntu 7.10 server for my SSH daemon. It does everything from webpage hosting, to e-mail, and even backups. This will not affect anything running on that server, so for the most part, it’s completely safe.
Now we need to configure PuTTy to connect using Tunnels. Open PuTTy, scroll down the left side to SSH, then Tunnels. In Source port, enter a number that you won’t normally use, I chose 8080. Leave the Destination blank, set the first option to Dynamic, and the second to Auto. Click the Add button.
Figure 1: Setting the source port
You should now see D<port> In my case, I have D8080 (Figure 2).
Figure 2: After setting the source port
From here, click Session at the top, enter the SSH server’s PUBLIC IP address. You can either use an IP address or a host name. If you have a dynamic IP address, you can use a Dynamic DNS service to make things a lot easier when trying to connect to your home network. Make sure you’ve selected SSH (default most of the time) and don’t worry about changing the port from 22 unless you changed the default SSH port on the box you plan to use.
Type a name in the Save Session so you don’t have to go through all of this again. I’m original, so I use Test. Click Save. The name should now appear in the box under Default Settings. If you double-click on the saved name, PuTTY will connect with all of the settings you just entered. You can also hit Load which will load the settings into the client before hand, allowing you to edit them as needed.
Browser Setup
Your client is set up! Now for the browser. As I stated earlier, I’m using Firefox. However this technique will work with anything you wish to mask. I even use it for remote desktop connections, effectively giving you your own VPN.
In Firefox, go to Tools > Options > Advanced> Network, then click the Settings button under connections.
Figure 3: Firefox Network Settings
From here, select Manual Proxy Configuration, then under SOCKS Host enter an IP address of 127.0.0.1 and the port number you entered earlier in PuTTy (8080 in this example).
In the No Proxy for box, enter localhost, 127.0.0.1. I use both since some OS’s have different addresses for the loopback. However, localhost is the standard name in most cases. Select the SOCKS V4 radio button. V5 might also work, but I’ve never tried it. Click OK.
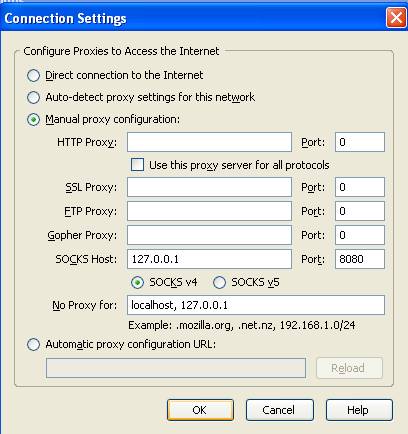
Figure 4: Completed Firefox Network Connection Settings
Now enter about:config into Firefox. Enter network.proxy.socks_remote_dns as the filter and double click on the parameter to change the value to true. This will use your SSH connection’s DNS, and not the one you’re currently connected to. Even when using the tunneled connection, your browser would normally be using the local DNS server. Using the remote, tunneled DNS server removes the risk of someone looking on the DNS server to see the web pages you’re viewing.
You’re now done! You should be browsing the web using your SSH server. Remember you have to stay connected for this to work. If your shell connection drops, you will lose your Internet access connection in that browser.
As I stated before, this can be used for anything that lets you set a Proxy to connect to the Internet (which is almost everything these days). Most of the settings look the same as the ones above in Firefox. Just make sure to specify a SOCKS proxy.
Happy secure surfing!
