Introduction
Updated August 16, 2005

In Part 1 of this review, I looked at the history behind PGP Corp., the PGP method of email and disk encryption, and provided a general overview of the PGP Universal gateway encryption product.
In this second and final part, I will focus on how the product actually functions, and will examine all of the different components of PGP Universal Series 500.
Learn Mode
A PGP Universal server begins life in something called Learn Mode. Learn Mode consists of the server proxying mail and creating keys for users as usual, but not encrypting or signing any mail it sends. This allows a server to safely generate keys for users and show administrators how different mail would be encrypted if Learn Mode were not active. But it doesn’t incur the nasty overhead of actually having to encrypt and sign messages while simultaneously generating keys for all of the users in the internal domain. Once enough keys have been generated, Learn Mode can be deactivated and encryption can begin.
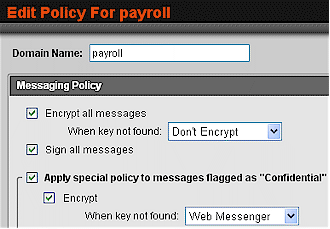
While in Learn Mode, you are also able to set up and test policies for encrypting mail. Everything about PGP Universal’s encryption system, such as who to encrypt mail to, what to do for recipients without a key and whether to use OpenPGP or S/MIME to encrypt messages, is controlled at the policy level. (Figure 1)
Figure 1: The mail encryption policy screen
(Click image for more detail)
I established a default policy that would apply to every domain that mail was sent to, and then established several contingencies and exceptions for messages. These exceptions could apply to both message subjects and recipient domains, and I established policies for both.
For the recipient domain, I specified foobar.net (our old friend Bob’s domain) and specified that all mail being sent to this domain should be encrypted. For the message subject, I followed the reviewer’s guide provided by PGP Corp. and specified “payroll” as the subject.
Setting up policies for message subjects seemed a little counter-intuitive, as it used the same interface as the recipient domain policy setup. Also, in order for message subjects to be considered for encryption the “Apply special policy to messages flagged as Confidential” option had to be selected.
Another thing that would have been nice is wildcard support for domains, which could be used, for example, to send only plaintext mail with no encryption options to top-level domains from countries where encryption is illegal.
Encrypting Mail
When I turned off Learn Mode, the real fun began, and I set about testing each of the delivery methods provided by the program. In an ideal world, everyone would have a key pair and everyone would be able to encrypt email. But we do not live in an ideal world, and PGP Universal takes this into account by providing delivery methods for messages destined for users without any kind of encryption on hand.
The first of these is WebMessenger, described in Part 1. (Figure 2)

Figure 2: A WebMessenger invitation
I tested both methods of sending WebMessenger mail: with implicit trust; and with requiring the authorization of the sender. I sent emails from a user (Alice) on my “Arpstorm” test network to a user (Bob) on my other test network, “Foobar” using both methods, and both worked well. The inclusion of sender authorization (in which the sender of the email gives the recipient a code to enter into the WebMessenger login, in the event that the email is intercepted or sniffed) was a nice touch.
Figure 3: The WebMessenger interface
(Click image for more detail)
The next delivery method I looked at was PGP Satellite. Satellite is a program available to external users that allows them to send and receive encrypted mail from their desktop systems without having to go through WebMessenger. It interacts with an installation of PGP Universal to create a key pair for the external user and allow him or her to utilize the public keys of anyone in the Universal domain.
As with everything in PGP Universal, downloads of Satellite (Figure 4) can be controlled through policy settings. A user can be offered to download Satellite through the use of ‘smart trailers’, which are footers appended to outgoing email messages explaining that they were potentially encrypted with PGP Universal. Satellite may also be downloaded through the preferences menu in WebMessenger.
Figure 4: PGP Universal Satellite download page
(Click image for more detail)
Satellite was downloaded from the PGP Universal server onto my external test host quickly and painlessly. An ActiveX control embedded in the site auto-detected the operating system that we were running and downloaded the appropriate Satellite version. When I tested a Satellite download without ActiveX enabled, I was still able to download the application through links on the page.
Satellite installed itself with only a minimum of input from me required to generate the key, and before long the machine was set up to send and receive mail from a PGP Universal domain. Satellite runs as a background process, without even a system tray icon to flag that it is running. But the machine’s ability to send and receive encrypted mail confirmed that it was that it was there and running.
PGP Universal (as well as the PGP Desktop component) sends encrypted email as .pgp attachments to the message (Figure 5), which are then decrypted (Figure 6) by Universal, Satellite, Desktop, or any other OpenPGP program that contains the recipient’s private key.
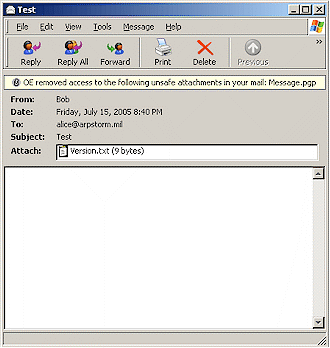
Figure 5: How an encrypted email looks to someone without the key
This could pose a problem with organizations that scrub all unknown attachments from email messages as a way of stopping viruses. So appropriate email filtering policies will need to be tweaked to accommodate.pgp attachments before PGP Universal is fully deployed.
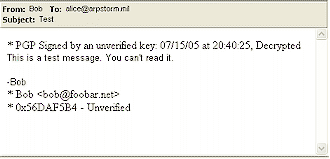
Figure 6:…and how it looks for its intended recipient once it is decrypted
PGP Desktop Integration
The final feature of PGP Universal that I examined was the integration with the PGP Desktop product. PGP Desktop (Figure 7) is a stand-alone encryption application that allows an individual user to encrypt his or her own email or files without PGP Universal. But it is also available integrated into PGP Universal Series 500.
Figure 7: PGP Desktop
(Click image for more detail)
A wizard (Figure 8) walked me through the process of setting up PGP Desktop and generating keys for a user. A basic 2048-bit RSA key pair is generated by default after a passphrase is entered, but any aspect of this key (such as key length, type, ciphers, hashes, etc) can be changed with the click of the Advanced button.
Figure 8: PGP Desktop key generation
(Click image for more detail)
PGP Desktop provides a nice companion to PGP Universal since it puts control of encryption in the hands of the user. It can sync up with a PGP Universal server automatically and download encryption policies, or a user can define his or her own policies. It also allows users to encrypt files right from the desktop before transmitting them over the network.
Desktop also allows encryption for AOL Instant Messanger conversations. But this feature requires the user on the other end to also have PGP Desktop installed, and I didn’t think it offered significant advantages over free encrypted IM solutions such as Off the Record and Trillian.
Possibly the most useful feature of PGP Desktop, next to its email encryption capabilities, is the ability to securely delete files. The PGP Shredder feature uses up to 28 passes of writing pseudo-random garbage characters and zeros over the data, protecting it from all but the most skilled recovery techniques.
Figure 8: PGP Shredder
While PGP Universal was designed for employees within the workplace, PGP Desktop seems designed more as a companion for employees on the road. Encrypting files from the desktop ensures that they will be secure even if a user connects from, say, an unsecured wireless access point. Whole-disk and folder encryption also allows mobile employees to keep data safe even if their laptop is stolen. While all this encryption may seem a bit over-the-top and only for the very paranoid, for organizational road warriors this level of protection can spell the difference between a sealed business deal and unsealed company information.
Closing Thoughts
There is no security “killer app” that will make an organization’s every dealing absolutely 100% secure. Even PGP itself has been defeated, not through cryptographic attacks, but by keyloggers or rootkits installed on machines, stolen private keys, and other methods that exploit the human side of security. Security is in essence a system, and attention must be paid to every single facet of the system for it to be effective as a whole.
That being said, PGP Universal solves a real security problem – enterprise-level encryption. It allows individuals with no knowledge of encryption to send secure messages both within and outside their organizations. While there are other products out there that do some of the individual things that PGP Universal does, such as encrypt disks or encrypt email, there are no products that cover everything that Universal does. Furthermore, there are also no products that do all of this with tested, proven, industry-standard encryption schemes such as OpenPGP and S/MIME, capabilities that also set PGP Universal apart from other solutions.
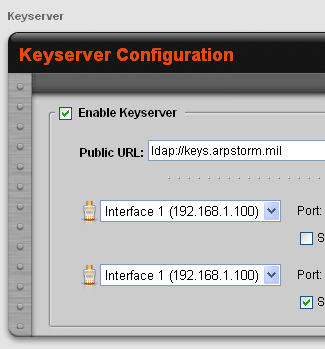
Figure 9: Integrated keyserver and SNMP traps make an administrator’s life easier
(Click image for more detail)
Updated August 16, 2005
The price tag of $2,950 for a 25 user, 1-year license for PGP Universal Series 500 may seem steep. But when compared to the cost of amassing similar products (as well as getting them all to work together and getting support for them), the price starts to look more reasonable. If you can do without PGP Desktop, a 25 user, 1-year license for PGP Universal Series 100 will run you only $1,475 ($59 per seat).
While there are a few things about the interface that could be made more intuitive, the product as a whole works well for both users and administrators. It provides the right amount of transparency for end-users to go about their daily activities, while providing enough hackability and creamy goodness to satisfy administrators. With PGP Universal 2.0, PGP Corp. proves that in addition to providing pretty good privacy, they can also provide pretty great enterprise encryption.