Introduction
Millions of wireless access points are spread across the US and the world. About 70% percent of these access points are unprotected – wide open to access by anyone who happens to drive by. The other 30% are protected by WEP (Wired Equivalent Privacy) and a small handful are protected by the new WPA (Wi-Fi Protected Access) standard.

Figure 1: FBI Computer Scientist James C. Smith (left) and
FBI Special Agent Geoff Bickers (right)
At a recent ISSA (Information Systems Security Association) meeting in Los Angeles, a team of FBI agents demonstrated current WEP-cracking techniques and broke a 128 bit WEP key in about three minutes. Special Agent Geoff Bickers ran the Powerpoint presentation and explained the attack, while the other agents (who did not want to be named or photographed) did the dirty work of sniffing wireless traffic and breaking the WEP keys.
This article will be a general overview of the procedures used by the FBI team. A future article will give step-by-step instructions on how to replicate the attack.
WEP Cracking – The Next Generation
WEP is an encryption scheme, based on the RC-4 cipher, that is available on all 802.11a, b and g wireless products. WEP uses a set of bits called a key to scramble information in the data frames as it leaves the access point or client adapter and the scrambled message is then decrypted by the receiver.
Both sides must have the same WEP key, which is usually a total of 64 or 128 bits long. A semi-random 24 bit number called an Initialization Vector (IV), is part of the key, so a 64 bit WEP key actually contains only 40 bits of “strong” encryption while a 128 bit key has 104. The IV is placed in encrypted frame’s header, and is transmitted in plain text.
Traditionally, cracking WEP keys has been a slow and boring process. An attacker would have to capture hundreds of thousands or millions of packets – a process that could take hours or even days, depending on the volume of traffic passing over the wireless network. After enough packets were captured, a WEP cracking program such as Aircrack would be used to find the WEP key.
Fast-forward to last summer, when the first of the latest generation of WEP cracking tools appeared. This current generation uses a combination of statistical techniques focused on unique IVs captured and brute-force dictionary attacks to break 128 bit WEP keys in minutes instead of hours. As Special Agent Bickers noted, “It doesn’t matter if you use 128 bit WEP keys, you are vulnerable!”
On with the Show
Before we get into the steps that the FBI used to break WEP, it should be noted there are numerous ways of hacking into a wireless network. The FBI team used publicly available tools and emphasized that they are demonstrating an attack that many other people are capable of performing. On the other hand, breaking the WEP key may not necessarily give an attacker complete access to a wireless network. There could also be other protection mechanisms such as VPNs or proxy servers to deal with.
For the demonstration, Special Agent Bickers brought in a NETGEAR wireless access point and assigned it a SSID of NETGEARWEP. He encrypted the access point with a 128 bit key – made by just keying in random letters and numbers.
Note that normally, you have to find wireless networks before you can crack them. The two wireless scanning tools of choice are Netstumbler for Windows or Kismet for Linux. Since the other WEP cracking tools are mainly Linux-based, most people find it easier to stick with Kismet, so they don’t have to switch between Windows and Linux.
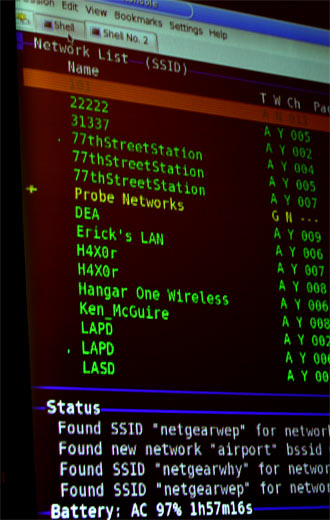
Figure 2: Scanning for Networks
Another FBI agent started Kismet and immediately found the NETGEARWEP access point. Just for fun, a third agent used his laptop and ran FakeAP, a program that confuses scanning programs by putting up fake access points.
Attack!
After a target WLAN is found, the next step is to start capturing packets and convert them into pcap (short for packet capture) format. These pcap files will then be processed by other programs. Many programs, both commercial and open source, can be used to capture packets, but the two favorites seem to be Kismet or Airodump (now part of Aircrack). Ideally, one laptop should be scanning, while another laptop will be running the attack – which is what the FBI team did.
About half a dozen different software tools were then used by the FBI team, and they are listed – along with their download links – at the end of the article. Thankfully, the Auditor’s Security Collection, which we reviewed last year, is a live CD that has all of these tools already installed. Even the FBI likes this distribution.
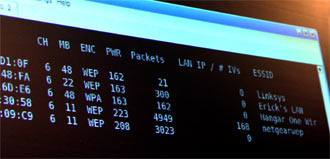
Figure 3: Capturing Packets
If a hacker is lucky enough to find an extremely busy wireless network, passive sniffing should provide enough good packets to allow the WEP key to be recovered. In most cases, however, an active attack or series of attacks are needed to jump start the process and produce more packets. Note that active attacks generate wireless traffic that can itself be detected and possibly alert the target of the attack.
The FBI team used the deauth feature of void11 to repeatedly disassociate the laptop from the access point. Desired additional traffic was then generated as Windows XP tried to re-associate back to the AP. Note that this is not a particularly stealthy attack, as the laptop user will notice a series of “Wireless Network unavailable” notifications in the taskbar of their desktop screen.
Another attack method the FBI team used is a replay attack. The basic premise of this attack is to capture at least one packet traveling from the victim laptop to victim access point. This packet can then be replayed into the network, causing the target AP to respond and provide more traffic to capture.
Aireplay (also part of Aircrack) can perform a replay attack based on captured ARP (Address Resolution Protocol) packets, which are broadcast at regular intervals in wired and wireless networks and are easy to spot. Aireplay automatically scans a captured pcap file, pulls out the suspected ARP requests, and replays them to the access point.
After about three minutes of capturing and cracking, the FBI team found the correct WEP key, and displayed it on a projected notebook screen. Agent Bickers, still speaking to the audience, turned around, looked at the screen and was surprised, “Usually it takes five to ten minutes.”
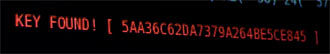
Figure 4: Gotcha!
Countermeasures & Conclusion
So what can you do to prevent hackers from getting into your network? Special Agent Bickers and his team have some tips for wireless users. He stresses that these are mainly for home users and should not be considered as official FBI best practices for businesses.
1) Network segregation
Put your access point on a separate subnet, with a firewall separating the wireless and internal users
2) Change the default settings on your access point
Default settings (SSID, administrator password, channel) are well known and even included as part of some WLAN attack tools
3) Use WPA with a strong key
WPA is a definite improvement over WEP in providing wireless security. But the version intended for home and SOHO use – WPA-PSK – has a weakness shared by any passphrase security mechanism. The choice of simple, common and short passphrases may allow your WPA-protected WLAN to be quickly compromised via dictionary attack (more info here).
4) Update your firmware
This is helpful if your AP or client doesn’t currently support WPA. Many manufacturers have newer firmware for 802.11g products that add WPA support. You may also find this for 802.11b gear, but it’s not as common. Check anyway!
5) Turn off the WLAN when not in use
A $5 lamp timer from your local hardware store is a simple, but effective way to keep your WLAN or LAN from harm while you’re sleeping.
Bickers also said that if you have an access point that can swap keys fast enough, you may be able to stay ahead of an attacker. “Most likely they will get bored and attack someone else.” But for most WLAN owners, this method isn’t practical.
The FBI demonstrated this attack to the computer security professionals at the ISSA meeting in order to show the inadequate protection offered by WEP. It is one thing to read stories of WEP being broken in minutes, but it is shocking to see the attack done right before your eyes. It was fast and simple.
Thankfully, the FBI are the good guys.
