Introduction
By now everyone has heard of wardriving, or maybe even Warflying. Wardrivers find wireless access points (WAPs) by driving around and using laptops with wireless cards. They typically track the WAPs using free and simple programs such as NetStumbler for Windows or Kismet for Linux.
The whole point of wardriving is not to hack into the wireless network, but to see how many WAPs you can find. It is also interesting to find out what vendors are the most popular and how far you can receive a signal. Hackers are generally not a destructive bunch, but they are very curious.
Screenshot during a ride on the Taipei Mass Rail Train (MRT)
Since I am already in Taipei for the Computex 2004 show, I decided to do a little wireless snooping. With wireless laptop in tow, I rode the Taipei mass transit system (called wartraining), then walked around the World Trade Center area (called warwalking), and finally rode a taxi around town (called wartaxiing). The results are surprising.
Equipment Used
All the tools you need for wardriving
You don’t need that much equipment to wardrive. You can go all out and spend thousands of dollars for tricked out antennas and wireless cards, but you can get by with what I used in the picture.
- Laptop with optional IrvineUnderground sticker
- IrvineUnderground is a large hacker group (about 50 members) based in Irvine, California
- Wireless PC Card
- I prefer Cisco Aironet cards, but you can use pretty much any vendor
- Auditor Security Collection CD
- The BEST network hacking CD ever made! Plus it is free!
- Oakley sunglasses to hide my identity
Warwalking
Free Internet at Taipei 101 Mall
The Taipei 101 skyscraper is the tallest building in the world and I wanted to find out how good wireless access was inside. A mall occupies the first eight floors or so. From a food court on the 7th floor I was able to access an unencrypted wireless network. It was slow as molasses, but at least I was able to pull up the Groklaw page!
I was also interested in finding out how wireless access is in downtown Taipei. After all, Computex, along with about 50000 computer savvy attendees will be there. Firing up NetStumbler at various points along the outside of the convention halls (there are four!!), I found a few dozen WAPs. Most belonged to HINET, which appears to be the Taipei version of Tmobile Hotspot.
Kneeling at front of the Exhibition Hall 1
I found ten WAPs in front of Exhibition Hall one. Since I did this the Saturday before Computex, this number will grow tremendously as the convention starts. Most were default and unencrypted, probably because the booths were being set up, and someone just need quick access. I also detected six WAPs that belonged to the Convention Center’s wireless service, but alas, you need a username and password to get in.
Wartraining
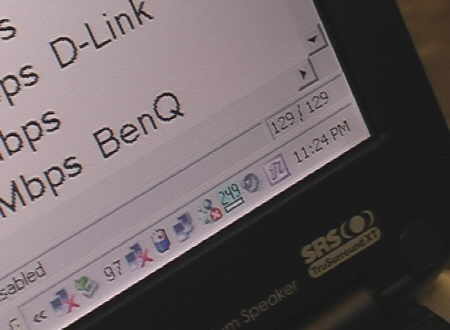
Screenshot just before exiting the train
Taipei has a great and inexpensive mass transit system. It combines a subway and above ground train. It would have been pointless to wartrain (or should we call it warsubway?) underground, as there wouldn’t have been that many WAPs to pick up. So, I took the Muzha (Brown) line, which is an elevated rail line, from Taipei Zoo to Zhongshan Junior High School. Total trip time was about 20 minutes.
I expected Taipei to have more WAPs, as this is the computer manufacturing capital of the world. The Muzha line runs through the center of the city. I only found 130 WAPs, 129 on the train, and one WAP as I stepped off. 90 out of the 130 (70%) had WEP disabled. You can download the wartaxi NetStumbler log at the end of this article.
Wartaxiing
Riding a taxi in Taipei is a religious experience. The fragrant incense and moth balls smells will overwhelm you if you are not prepared. The lanes painted on the roads bear no meaning, as cars and scooters alike make their own lanes. The taxi driver paid no attention as I sat in the front passenger seat and fired up my laptop.
The route taken was from the Four Points Sheraton in Chung Ho District to the United Hotel near the Taipei 101 skyscraper. I expected to find more WAPs on this 20 minute taxi ride, but ended up find 21 WAPs. 16 out of 21 had WEP disabled. You can download the wartaxi NetStumbler log at the end of this article.
Conclusion and Netstumbler logs
This all assumes that the information being broadcasted from the wireless access points was true. It is very possible that some of the wireless access points may have been honeypots broadcasting out false information. Using the tools in the Auditors Security Collection CD, it is very easy to spoof a MAC address, and pretend to be another vendor’s WAP.
About 71% of the WAPs I detected did not have WEP turned on, which is in line with wardriving results in the USA and other parts of the world. Just because WEP is disabled, however, doesn’t necessarily mean that the network is completely open. Most of the WAPs found in Taipei used some type of user/password authentication to gain Internet access. Of course, since WEP is not used, this traffic can be sniffed and fed back into the WAP.
The most interesting SSID found was test_dontuse. The popular vendors in Taipei seem to be D-Link, Melco (Buffalo), and Senao. Unlike the United States, Linksys is almost non-existent here.