Introduction
When we last left WPA (in our November 2002 WPA – Wireless Security for the rest of us NeedToKnow) it was but a gleam in the eye of the Wi-Fi Alliance and a hardy band of brave souls. They had decided to stop waiting for the IEEE Task Group i to finish its work, take a subset of the technologies the Task Group was working on and get them to market as soon as possible.
At April’s Networld+Interop show in Las Vegas, the Wi-Fi Alliance proudly announced that WPA and the Alliance’s certification process were ready to go, successfully marking the beginning of a new phase in wireless networking security.
In this NeedToKnow we’ll concentrate on how WPA turned out, its availability, and how it performs. But first let’s start with a quick review of what makes WPA tick.
What’s the Equation, Kenneth?
WPA is a subset of technologies taken from the upcoming 802.11i standard, which the Wi-Fi Alliance has now dubbed WPA2. The Wi-Fi Alliance has dedicated an entire portion of its website to promoting and explaining WPA, and it’s a decent resource if you need some help in wrapping your mind around this new wireless security feature-set.
A handy document there is a presentation they did for us slow-on-the-uptake Media types at last April’s Networld+Interop kickoff session. It gives a summary of both the background of WPA and the elements that now go into it.
One of the simple explanatory devices they used was this equation for WPA:
WPA = 802.1X + EAP + TKIP + MIC
It pretty much wraps all the “what” of WPA into a nutshell and I’ll use it to quickly review each of WPA’s components.
User Authentication
WPA uses 802.1x and Extensible Authentication Protocol (EAP) as the basis of its authentication mechanism. Authentication has a user provide some form of evidence (“credentials”) that they should be allowed access to a network and checks that evidence against a database of valid users. Anyone who has ever logged into a network has gone through an Authentication process.
The database and checking parts of the Authentication process mentioned above are usually done by a special server – typically RADIUS – in large “enterprise” networks. But since WPA was intended to also be used by all WLAN owners, it was also given a simpler mode that doesn’t require any fancy equipment.
This mode – called Pre-Shared Key (WPA-PSK) – only requires a single password entered into each WLAN node (Access Points, Wireless Routers, client adapters, bridges). As long as the passwords match, a client will be granted access to a WLAN. Figure 1 illustrates the process.
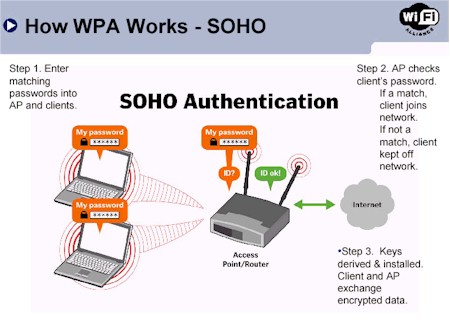
Figure 1: WPA – PSK Authentication
(Diagram from Wi-Fi Alliance Networld+Interop 2003 Media Presentation
Used by permission)
Encryption
Although WPA’s predecessor – WEP – didn’t have an Authentication mechanism at all, WEP’s main problems came from the cryptographic weakness of its encryption mechanism. As this nicely written explanation by RSA Security points out, WEP’s key problem is that the keys for different data packets are too similar.
The TKIP, MIC and 802.1X parts of the WPA equation each play a part in strengthening the data encryption in WPA-enabled LANs. This excerpt from the Wi-Fi Alliance’s WPA White Paper provides a good overview of how they play together:
TKIP increases the size of the key from 40 to 128 bits and replaces WEP’s single static key with keys that are dynamically generated and distributed by the authentication server. TKIP uses a key hierarchy and key management methodology that removes the predictability which intruders relied upon to exploit the WEP key.
To do this, TKIP leverages the 802.1X/EAP framework. The authentication server, after accepting a user’s credentials, uses 802.1X to produce a unique master, or “pair-wise” key for that computing session. TKIP distributes this key to the client and the AP and sets up a key hierarchy and management system, using the pair-wise key to dynamically generate unique data encryption keys to encrypt every data packet that is wirelessly communicated during that user’s session. TKIP’s key hierarchy exchanges WEP’s single static key for some 500 trillion possible keys that can be used on a given data packet.
The Message Integrity Check (MIC) is designed to prevent an attacker from capturing data packets, altering them and resending them. The MIC provides a strong mathematical function in which the receiver and the transmitter each compute and then compare the MIC. If they do not match, the data is assumed to have been tampered with and the packet is dropped.
By greatly expanding the size of keys, the number of keys in use, and by creating an integrity checking mechanism, TKIP magnifies the complexity and difficulty involved in decoding data on a Wi-Fi network. TKIP greatly increases the strength and complexity of wireless encryption, making it far more difficult – if not impossible – for a would-be intruder to break into a Wi-Fi network.
Couldn’t have said it better myself!
It’s important to note that the Encryption mechanisms used for WPA and WPA-PSK are the same. The only difference between the two is in WPA-PSK, authentication is reduced to a simple common password, instead of user-specific credentials. Some would argue that this common-password approach makes WPA-PSK too easily breakable via brute-force password-guessing attacks, and they would have a point. But I’d argue that WPA-PSK takes away the present mess of inconsistent WEP key entry and management and replaces it with a consistent, single alpha-numeric password entry system. And that puts it far ahead of WEP as far as I’m concerned, because it’s so simple that people might actually use it!
That wraps up the review. Now that you know the theory of WPA, let’s see how it works in practice!
Upgrading – 11g jumps to the head of the line
Updated June 30, 2003
So you’re sold on WPA and want to upgrade your wireless LAN ASAP! Where do you start?
Whether you’re an “enterprise” or SOHO user, there are three basic steps:
1) Find out whether your access point or wireless router is WPA-capable, or if there is a firmware upgrade available.
2) Find out whether your wireless client adapter(s) is WPA-capable, or if there is a driver upgrade available.
3) Find out whether you’ll need to purchase a “supplicant” application for your wireless client.
Steps 1 and 2 are simple in theory, but are turning out to a significant challenge for the entire food chain of wireless LAN related manufacturers. Since most consumer networking gear comes from a network of OEM and ODMs in Taiwan, those companies must first absorb the code from the wireless chip companies and then grind out the driver and firmware updates for their customers.
This is no small task, given the 700+ Wi-Fi certified products that the Alliance says are available today, not to mention the hundreds of uncertified products. Those updates must then be distributed to the networking gear companies, who then execute some sort of QA/acceptance process (let’s hope), and finally make the drivers available for download.
So far, it looks like 802.11g-based products are at the head of the WPA-upgrade line. Since manufacturers have a vested interest in keeping the sales of this latest version of WLAN products flying off the shelves, this first-availabilitiy should come as no surprise. But what is surprising is that Broadcom-based products seem to be getting the most early WPA upgrades, even though Intersil released WPA code to its customers in January for its 11b PRISM 2.5, and March for its 11g GT and 11a/b/g Duette chipsets.
Table 1 shows the WPA updates available for Broadcom-based products at the time this article was written:
|
Manufacturer
|
Product
|
|
Belkin
|
– F5D7130 Access Point |
|
Buffalo Technology
|
– WBRG54 router – WLI-CB-G54 CardBus client – WLI-CB-G54A CardBus client |
|
Linksys
|
– WPC54G CardBus client |
Updated August 17, 2003
Table 2 shows similar info for Intersil-based products. Note that no Intersil-based WPA-capable 11g clients were available at the time this article was written. The table originally showed NETGEAR as having WPA upgrades, but since they’ve yet to make WPA available on any of their products, I’ve removed them.
|
Manufacturer
|
Product
|
|
SMC
|
– SMC2804WBR Router – SMC2802W EZ Connect 2.4GHz 54Mbps Wireless PCI Adapter – SMC2835W EZ Connect 2.4GHz 54Mbps Wireless CardBus Adapter |
As for the other major wireless chipmakers, Atheros told me that they released WPA code to its customers on May 31. But Atheros President and CEO Craig Barratt told me at April’s Networld+Interop show that they would not be providing WPA on Atheros’ first-generation 11a-only chipset, which has already been removed from production.
After I posted this article SMC also told me about its WPA upgrades for its Atheros-based a/b and a/b/g cards, which are now reflected in Table 3 below.
|
Manufacturer
|
Product
|
|
SMC
|
– SMC2335W EZ Connect 2.4GHz/5GHz Universal Wireless Cardbus Adapter -SMC2336W-AG EZ Connect Universal 2.4GHz/5GHz 802.11a/g Wireless Cardbus Adapter |
Agere Systems sent WPA Beta code to its customers earlier this year, and released production code to them in May. Agere says its first WPA-certfied Wi-Fi product will be available by the end of June.
I also asked TI about its WPA releases, but didn’t receive a response.
Upgrading – 11b and other stuff
If the initial going is any indication, owners of 802.11b and a/b products may need an extra measure of patience in their wait for WPA upgrades. The only WPA-upgraded 11b products that I know of right now are Cisco’s 802.11b Aironet 1100 and 11a/b Aironet 1200, Linksys’ WPC11 ver3 client card, and 3Com’s AP8000 series.
Cisco released their updates without a peep in early June, actually beating out most other companies. But a WPA update for their Aironet 350 client hasn’t been issued yet, so Cisco’s solution is incomplete.
Linksys gets an attaboy for at least trying to do the right thing for its significant installed base of these cards. But what Linksys giveth, it also taketh away, since it has yet to make WPA upgrades available for any of its 11b Access Points or wireless routers, and will only say “soon” when asked when those upgrades might be available.
A poll of the usual suspects on their 11b product WPA-update plans garnered the following responses:
SMC – Its May 1 announcement said “its portfolio of wireless networking products will include support for the new Wi-Fi Protected Access (WPA) by the end of this quarter” (end of June).
U.S. Robotics – told me it should have WinXP-only WPA support in all its TI-based “802.11b+” 22Mbps products by early August. Updates are expected to be first available for USR’s PC Card and PCI adapters by the end of June, followed by access point/router support “several weeks later”.
ZyXEL – “WPA functionality will be built into the ZyAIR product line starting in mid-July. We are also on schedule for July WPA certification testing through the Wi-Fi Alliance.”
And what about products like Linksys’ WET11 and WET54G Wireless Ethernet Bridges as well as straight wireless bridges, bridge/repeaters, etc.? It turns out that the hangup seems to be the supplicant (more about supplicants in the next section).
The code to implement each supplicant EAP variation (EAP-MD5, EAP-TLS, etc.) is pretty sizable, especially considering the limited flash memory in these devices, which is where it has to reside. This means that designers of bridging devices will probably be selective about which WPA authentication methods they support, and that it will take longer to finish WPA support for these devices.
If I pull myself back from all the individual press releases, emails and conversations, two things clearly stand out:
1) Manufacturers are putting their primary WPA efforts behind their current-generation 802.11g and a/b/g products.
2) WPA upgrade support for older products is not guaranteed. Manufacturers’ commitments to providing the upgrades vary widely, with timetables tending toward later rather than sooner.
Conclusion 1: With limited product development resources, WLAN product manufacturers are putting their effort behind 11g and hoping 11g’s higher throughput will entice users to abandon their 11b products, relieving demand for those WPA upgrades.
BYO supplicant
Referring back to our three step process for WPA upgrading, Step 3 is turning out to be one of the dirty little secrets of WPA – at least in the initial going. It turns out that having a WPA-capable driver for your wireless adapter isn’t all you need on that end of things. Although a WPA-capable driver adds the code for the WPA “equation” elements (TKIP, 802.1x, etc.), it doesn’t necessarily provide the smarts that the client needs to know how to use those new capabilities.
That intelligence is contained in a piece of software known as a “supplicant”, which is turning out to be trickier to implement than networking vendors (and their WLAN chip suppliers) figured. Right now the most widely-available choice in supplicants are the WPA patch for Windows XP, Funk Software’s Odyssey client, and Meetinghouse Data Communications’ AEGIS client.
Pros and Cons of these choices are:
- The XP patch adds WPA capability to WinXP’s built-in “Zero Configuration” wireless client and as you’ll see later, gets the job done. The good news is that it’s a free download. The bad is that you must run WinXP to use it.
- Funk’s client has a free downloadable demo, runs on Windows XP/2000/98/Me/Pocket PC, and supports a wider variety of authentication protocols than the WinXP patch. But you’ll need to shell out about $50 per client if you end up purchasing it.
- The AEGIS client also has a free evaluation period and runs on more OSes including Linux, Mac OS X , Windows XP, NT, 2000, 98, ME, and Pocket PC 2002. The negative is that it’s also a pay-for option, although at $40 a copy slightly less expensive.
So, right now, WPA supplicants for operating systems other than WinXP are not guaranteed to be included when you download your wireless adapter’s WPA upgrade. I contacted a number of equipment and wireless chip vendors regarding this issue and asked their plans for providing supplicants for operating systems other than WinXP. Here’s what I found:
3Com – Plans to include a WPA supplicant in its client application for its 802.11g client card only that will support WPA-PSK for Win98SE/ME/2000/XP. Users that need to use WPA with RADIUS authentication (“Enterprise mode”) will be able to use the Win XP WPA patch and XP’s Zero Config utility, but will need to purchase a third-party supplicant for other OSes.
Agere Systems – Agere is bundling a fully-functional version of Funk’s Odyssey client with the client manager application that is supplied to its customers.
Apple – WPA support with supplicant will be included in Mac OS X version 10.3 (“Panther”) that will ship by the end of 2003.
Atheros – Has integrated a WPA supplicant into the client manager application that is supplied to its customers
Belkin – “As for the non-XP OSes, our hope is to build the WPA support into the client software that we currently ship.” Current WPA support is for WinXP with Microsoft’s WPA patch.
Buffalo Tech – Right now, WPA upgrade instructions direct XP users to download Microsoft’s WPA upgrade patch. Users of other OSes are referred to download Funk Software’s Odyssey client free trial demo (registered application costs about $50 per client).
A Buffalo spokesperson indicated that work is in progress on a client with built-in WPA support that will also cover 802.11i (WPA2), but didn’t say when the client would be available.Linksys – Relying on Microsoft XP WPA patch. Refers users to Funk’s Odyssey client for non-XP OSes.
NETGEAR – “We are looking to certify our products to work with Meetinghouse & Funk and are working with them now to see how we can provide with our client products.”
SMC – “All of our EliteConnect Wireless Products will include WPA supplicants for OSes other than XP.” SMC’s position for its other wireless adapter product lines was unclear, although it already bundles an earlier version of Meetinghouse’s AEGIS that doesn’t handle WPA with some of its products.
TI – Did not respond.
USR – “Our tentative schedule is PC Card/PCI adapter support by end of August, followed by access point/router by end of September. These are tenatative and are subject to updates by TI.”
ZyXEL – “ZyXEL currently provides a free copy of the Meetinghouse AEGIS client software with the ZyXEL wireless adapters. This enables customers running a non-XP or Win2000 SP3 OS to take advantage of IEEE802.1x authentication. ZyXEL will incorporate the additional WPA requirement of TKIP via a similar software upgrade for the existing base of ZyAIR client adapters, and for the newer ZyAIR products which are launching in the upcoming months, ZyXEL will include the supplicant software on the product CD.”
Conclusion 2: From the correspondence I’ve had with companies in preparation for this article, I sense that WLAN product vendors know that the present bring-your-own situation for non-XP users isn’t going to fly. Enough of them are working to fix this problem that any company that doesn’t address it will eventually (hopefully sooner rather than later) be at a competitive disadvantage.
Conclusion 2a: In the short-term, if you want to avoid hassles and extra cost with WPA, your OS better be WinXP.
WPA in action – AP “SOHO”
Once you manage to score WPA upgrades for your client and AP or wireless router, you’ll need to follow the manufacturer’s instructions and install them. So far the APs that I’ve tested were upgraded via their normal firmware update process. Client adapters have not required firmware upgrades and became WPA-capable by just upgrading their drivers using the normal Windows driver upgrade process.
Figure 2 shows the Security screen of a Belkin F5D7130 54G access point that’s received its WPA upgrade and has been set to the WPA-PSK (Pre-Shared Key) mode.
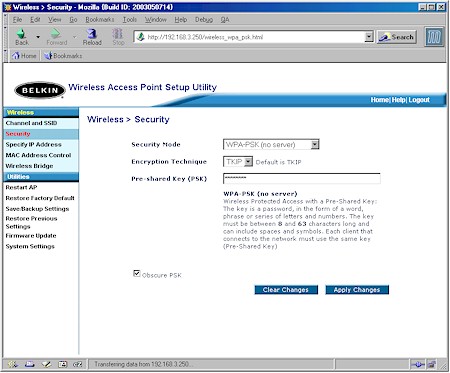
Figure 2: WPA – PSK Authentication
The screenshot shows that setup is pretty easy for WPA-PSK. All you need to do is turn it on, enter an alpha-numeric password between 8 and 63 characters long. The password can even include symbols and spaces!
So what’s with the Encryption Technique selector? It seems that Broadcom’s implementation for its “54g”-based products includes the optional selection of AES encryption, in addition to the requisite TKIP.
Since AES requires significantly more number-crunching power than WEP, it was not included in the WPA spec for fear that the throughput loss for “legacy” devices would be too great. But since Broadcom has included AES hardware acceleration in its 54g AirForce chipset, it looks like they chose to offer it as an option. (You’ll see why later…)
The story on AES support for other chipset manufacturers is:
Atheros‘ 11g and a/b/g chipsets also include AES hardware processing and will also offer AES as a WPA encryption option.
Although Intersil also has AES hardware in its GT and Duette chipsets, the 11g reference designs they supplied to me for testing didn’t offer AES as a WPA encryption option.
Finally, TI didn’t respond to my query, so I can’t say whether its 11g chipset – which includes AES hardware processing – will be offering the AES option.
That’s all there is to the AP end for WPA-PSK. Next I’ll cover the slightly more complicated “Enterprise” AP setup.
WPA in action – AP “Enterprise”
Updated June 30, 2003
Figure 3 shows the Belkin AP when I selected the WPA (with RADIUS server) option.
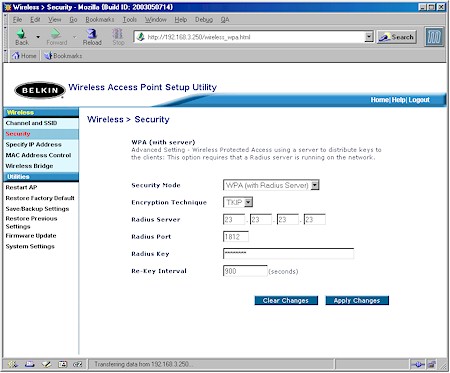
Figure 3: WPA (Radius) Authentication
You can see that setup for this “Enterprise” mode of WPA isn’t that much more complicated. All you need to enter is the IP address of the RADIUS server, its port number (the default of 1812 is entered for you), and the RADIUS key (similar to the WPA password).
Belkin also lets you specify the Re-Key Interval, which is the rate that the AP or RADIUS server pushes a new Group Key out to all clients. The Re-Keying process is part of WPA’s enhanced security and is the WPA equivalent of automatically changing the WEP key for an AP and all stations in a WLAN on a periodic basis. Setting of the Re-Key Interval is also supported by some APs in WPA-PSK mode, while others – like the Belkin – rely on a non-adjustable Re-Key Interval instead.
The configuration of the RADIUS server is beyond the scope of this NTK, but basically, it replaces the single password with per-user authentication. Figure 4 illustrates this mode, where the AP just passes the authentication request to a RADIUS server instead of performing the authentication itself. The server then checks the user’s credentials against its records, grants or denies network access accordingly, and then issues the Group Key to all stations so that they can begin encryption and sending / receiving data.
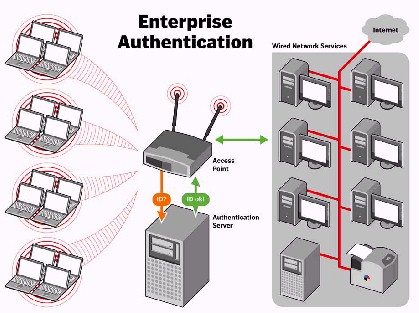
Figure 4: WPA “Enterprise” Authentication
(Diagram from Wi-Fi Alliance Networld+Interop 2003 Media Presentation
Used by permission)
There’s nothing special you need to do at the RADIUS server itself to support WPA, since the wireless client WPA authentication looks the same as any other client’s. This assumes, however, that the server supports 802.1X authentication and the desired EAP (Extensible Authentication Protocol) l types. I’ll go into this more in the next section, which describes the Client end of WPA.
WPA in action – Client “SOHO” mode
Since early implementations of WPA depend on WinXP and its WPA Patch, I’ll use it to illustrate WPA client-side setup. I’ll focus first on the WPA-PSK or “SOHO” mode.
Figure 5 shows the Wireless Network Properties screen if you have the XP WPA patch installed for your client adapter and the Network Authentication selections now available.
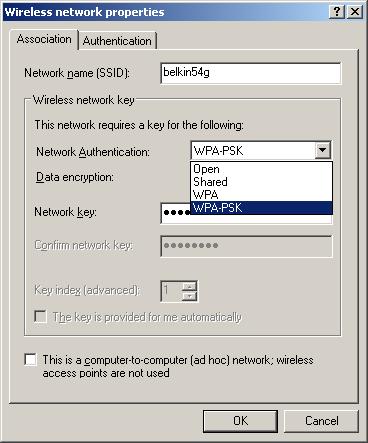
Figure 5: XP Client Network Authentication selection
The Open and Shared authentication options are used with WEP, and you probably have seen them before in pre-WPA products. The other two options presented are WPA and WPA-PSK, with the latter selected for the simpler “SOHO” WPA mode.
The Association tab is also where you enter your 8 to 63 character Network Key, which XP makes you enter twice to make sure it’s what you intended to enter. If you don’t enter it here, though, XP will prompt you for it when you go to choose a wireless connection.
Once you choose your authentication, you then need to select the Data Encryption method from the options shown in Figure 6.
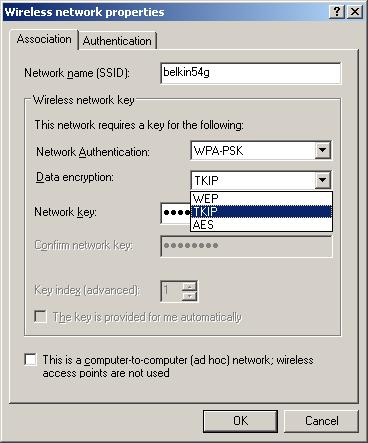
Figure 6: XP Client Encryption selection
As I mentioned before, TKIP (Temporal Key Integrity Protocol) is the encryption method mandated by the WPA spec, but, depending on your client adapter, you may see AES as an option also. You can choose either one as long as the AP or wireless router you’ll be connecting to also supports the same choice.
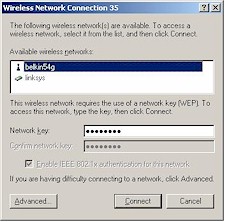
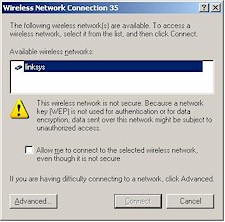
If you’ve done everything correctly, all you’ll need to do now is get your client in-range of the AP and bring up XP’s View Available Wireless Networks window. What you’ll see depends on whether your client detects a WPA-enabled AP. Figure 7 shows the window when you choose a WPA-enabled AP to connect to and Figure 8 shows a non-WPA connection.
|
|
|
|
Figure 7: WLAN select w/WPA
|
Figure 8: WLAN select w/o WPA
|
If you’ve already connected to the AP before and the Network Key is correct, XP probably won’t even pop up either screen and just automatically connect you instead. But if this is the first time you’ve connected to this WPA-enabled network and your other WPA settings are correct, all you’ll need to do is enter the Network Key twice and you should be ready to rock. Much easier than typing in a 26 character Hex WEP key, huh?
WPA in action – Client “Enterprise” mode
As I previously described, the only differences between WPA-PSK and “normal” WPA is in where authentication itself takes place and the credentials used for authentication. In WPA-PSK mode, authentication takes place in the AP or wireless router, using the Pre-Shared Key manually entered in the AP and wireless clients as the credentials.
In “Enterprise” WPA, authentication is done in an authentication server using a variety of credential types including digital certificates, unique usernames and passwords, smart cards, or other forms of secure IDs. The AP or wireless router serves only to bridge the authentication traffic between the wireless and wired networks.
WPA uses EAP (Extensible Authentication Protocol) to enforce user-level authentication using the 802.1x Port-Based Network Access Control standard framework. EAP was designed to be extendable to support a variety of authentication methods and protocols. The exact methods supported depend on the client supplicant and authentication server used, and of course the method you select must be supported on both client and server!
As I noted earlier, it’s turning out that WPA client supplicants are harder to implement than WLAN equipment vendors were led to believe. They’re also sizable applications, since they contain most of the intelligence in authentication process. So the client end of things may end up determining the exact authentication methods used.
As Figure 9 shows, the Windows XP WPA patch supports only EAP-Transport Level Security (EAP-TLS) for certificate and smart card-based authentication and Protected EAP-Microsoft Challenge Handshake Authentication Protocol version 2 (PEAP-MS-CHAP v2) for password-based authentication.
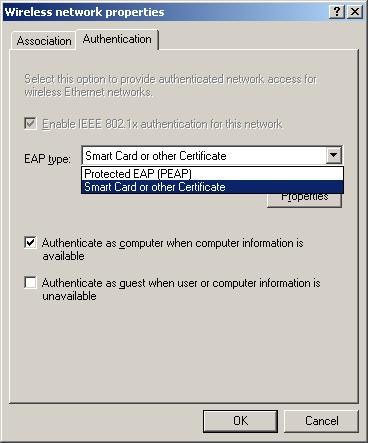
Figure 9: XP Client Authentication options
The Funk Odyssey and Meetinghouse AEGIS supplicants that some WLAN equipment vendors are either bundling or referring users to offer a wider choice of methods including EAP-TTLS, EAP-PEAP, EAP-TLS, Cisco’s LEAP, and EAP-MD5.
That’s about where I’m going to stop on this WPA mode, since the client side setup is very configuration and method dependent. Suffice it to say that if you’re faced with setting up a client for WPA “Enterprise” mode, you’d better hope that your network administrator gives you clear instructions!
Now that you know what’s involved in setting up WPA, it’s time to finally see whether you’ll be giving up throughput to use it!
WPA in action – Broadcom Performance
The good news is that using WPA doesn’t have to end up costing you throughput. But, at least in the early going, all WPA implementations aren’t created equal. Since Broadcom seems to be leading the pack slightly in WPA releases, I’ll start with a few examples of products based on their chipsets.
NOTES:
– As with draft-802.11g when it first appeared, WPA is in its early stages. Even though WPA is a released spec., manufacturers are still on the learning curve and tuning their implementations. Your mileage may vary when you try your own experiments with later drivers.
– All testing was done under close-range conditions, with client and AP about 5 feet apart and data flow from client to AP. All clients were tested in a Dell Inspiron 4100 notebook running WinXP Home SP1 with WPA patch.
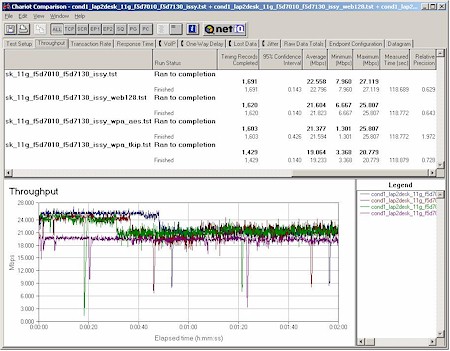
Since Belkin was first to have both client and AP that are 11g released-spec and WPA complaint, my initial testing focused on those products. Figure 10 shows a throughput comparison for a Belkin F5D7010 11g Client and Belkin F5D7130 11g AP test pair with the following test conditions:
- No security features enabled
- 128 bit WEP enabled
- WPA-PSK TKIP
- WPA-PSK AES
Figure 10: Belkin F5D7010 11g Client and Belkin F5D7130 11g AP
Condition 1 Throughput vs. Security modes
(click on image for a larger view)
The results are a little tough to see using the plots due to the periodic change in throughput that seems to be a part of at least these Belkin released-spec 11g products. But the numbers in the screen shot reveal that the only throughput hit is approximately 15% in the WPA-PSK TKIP mode. Guess now we know why Broadcom chose to add the optional support for AES!
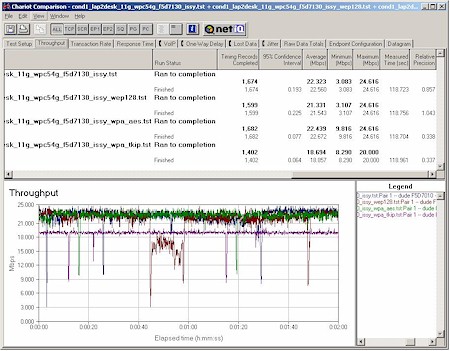
To see if there was a difference in Broadcom client implementations, I tested a Linksys WPC54G with the first driver that Linksys released that supported WPA, but not 11g spec compliance.
Figure 11: Linksys WPC54G 11g Client and Belkin F5D7130 11g AP
Condition 1 Throughput vs. Security modes
(click on image for a larger view)
Figure 11 shows more consistent throughput performance in all modes, but still has about a 15% throughput decrease in WPA-PSK / TKIP mode.
WPA in action – Intersil 11g Performance
Now that I saw what Broadcom could do, I turned my attention to Intersil. Since WLAN equipment manufacturers have yet to release WPA drivers for any Intersil-based products, I went directly to Intersil for help.
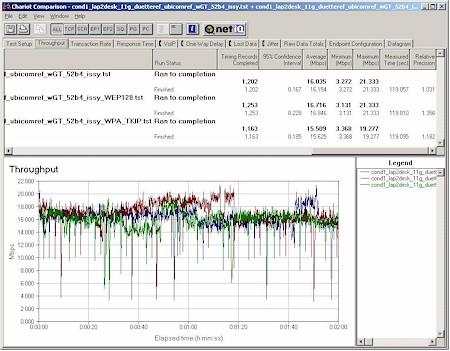
They supplied me with a number of goodies that enabled me to look at their WPA-enabled performance. I first tried their PRISM Duette (a/b/g) Cardbus Reference Design with an AP reference designed based on Ubicom’s IP2022 Internet Processor and an Intersil PRISM GT CardBus radio. Figure 12 tells the tale.
Figure 12: Intersil Duette CardBus Reference Design Client and
Ubicom IP2022 / Intersil GT Reference Design AP
Condition 1 Throughput vs. Security modes
(click on image for a larger view)
The throughput variation makes it hard to separate out WEP and WPA effects, but since the worst-case difference in average throughput is only about 4% between no security and WPA-PSK / TKIP, I’d have to say that’s within the accuracy of my measurement and conclude there’s basically no throughput hit for enabling either WPA TKIP or WEP with these designs.
Note that there’s no plot for WPA – AES. That’s because even though the hardware supports AES hardware acceleration, Intersil has decided to stick with the WPA spec and not enable it at this time. Doesn’t look like they need it to keep throughput chugging right along, either!
WPA in action – Intersil 11b Performance
Intersil has a considerable installed base of earlier PRISM-based 11b products, so I was especially interested to see whether enabling WPA on older 11b products would cause a considerable throughput reduction. I’m happy to report that it doesn’t – at least for the test cases I tried!
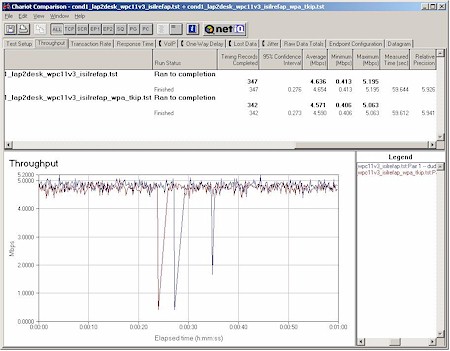
Figure 13: Linksys WPC11v3 11b Client and Intersil 11b WPA Reference AP
Condition 1 Throughput vs. Security modes
(click on image for a larger view)
Figure 13 shows the results from tests using a Linksys WPC11v3 11b Client and Intersil 11b WPA Reference AP. The AP is the same design used by the Wi-Fi Alliance as part of its WPA certification test bed, and I used the WPA driver that was part of Linksys’ first WPA update release a few weeks ago.
I was very pleasantly surprised by these results, but perhaps I shouldn’t have been, given the WPC11v3’s use of Intersil’s last 11b-only PRISM 3 chipset. So I decided to also run the PRISM 2.5 Reference design card that Intersil supplied and that’s the other half of the Wi-Fi Alliance testbed. Maybe the older chipset would suffer some performance hit?
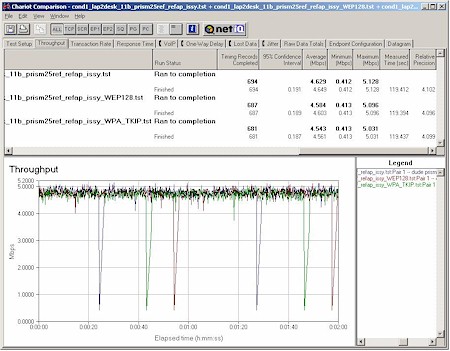
Figure 14: Intersil PRISM 2.5 Reference 11b Client and Intersil 11b WPA Reference AP
Condition 1 Throughput vs. Security modes
(click on image for a larger view)
Figure 14 again shows throughput difference within the limit of my measurement. I couldn’t go back to a PRISM 2-based design because I didn’t have WPA drivers (although Intersil has made them available to their customers for incorporation into end products).
So it looks like Intersil did a good job with their WPA implementation for their 11b chipsets. Now if only manufacturers will do the work they need to do and get their WPA driver upgrades finished and posted for download!
WPA in action – Mix ‘n Match
While I had everything set up and available, I decided to run a few tests mixing Broadcom and Intersil-based products. I apologize that omitted WEP128 mode tests from some of the runs, but since my experience has been that WEP-enabled throughput problems have been eliminated in all the 11g designs I’ve seen, I decided to save a little time.
Figure 15: Belkin F5D7010 11g Client and
Ubicom IP2022 / Intersil GT Reference Design AP
Condition 1 Throughput vs. Security modes
(click on image for a larger view)
Figure 15 pits the Broadcom-based Belkin 11g client vs. the Ubicom / Intersil reference AP. All the throughput “dropouts” you see come from the WPA / TKIP enabled run and push the average throughput down.
But even without the dropouts, the throughput variation without WPA-enabled makes it hard to separate out any WPA throughput effects. So for now, all I can conclude is that there’s a significant (almost 40%) average throughput hit with this combination of WPA-enabled devices.
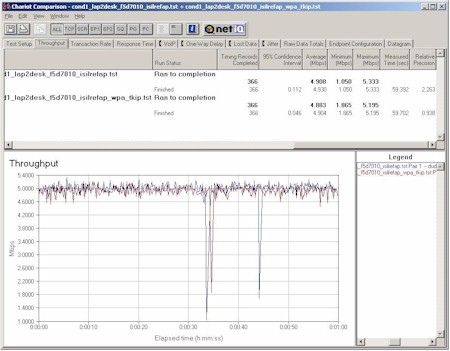
Figure 16: Belkin F5D7010 11g Client and Intersil 11b WPA Reference AP
Condition 1 Throughput vs. Security modes
(click on image for a larger view)
Since I had the equipment, I decided to see how an 11g client and 11b AP behaved with WPA in use. Figure 16 shows the Belkin client used with the Intersil 11b WPA reference AP and reveals that you’ll be able to use that combination with no loss of throughput.
That wraps up what I was able to make work. Now for the not-so-successful experiments.
Failed experiments
Not everything is wonderful – or at least interoperable – in WPA-land. Intersil-based clients and the Belkin Broadcom-based AP don’t appear to get along very well, for instance. When I tried to get the Linksys WPC11v3 to talk to the Belkin AP with WPA-PSK enabled, the AP locked up, requiring a power cycle to reset it.
I had a little better luck when I tried a WPA-enabled Intersil Duette reference card supplied by Intersil. It couldn’t associate, but at least it didn’t lock up the Belkin AP!
As I was getting ready to publish this NTK, Atheros provided me with WPA-capable drivers that I tried with a NETGEAR WAG511, which is based on Atheros AR5001X+ a/b/g chipset. Unfortunately, I was unsuccessful in getting the Atheros client to work with WPA enabled. With the Intersil / Ubicom reference setup, everything worked fine with WPA disabled. But when I enabled WPA-PSK, I could associate with the AP, but not pass traffic.
When I tried the client with the Belkin AP, it won’t even associate with WPA-PSK enabled, but again, worked fine with WPA-PSK disabled. I was unable to obtain any Atheros-based 11g APs to test the card with, so can’t say how an all-Atheros solution works.
A Few More Points of Note
As I looked over this NTK, I found there were still a few important points that I hadn’t covered in other sections. Since they’re loosely related, I’ll just put them up in “bullet” form:
-
No Mixing allowed!
It appears that the APs that I looked at don’t support WEP and WPA-enabled clients simultaneously. This function is not part of the WPA spec because any WEP-based clients would be the weak link in the security chain. A mixed WPA / WPA2 mode will be part of the WPA2 spec, but that’s still a ways off. For now, your choice of security modes are none, WEP (of various key lengths depending on your chipset vendor), and WPA.Updated August 17, 2003 After having a reader point out that the SMC2804WBR 802.11g router does support WEP and WPA simultaneously, i asked the Wi-Fi Alliance for clarification of their position on this subject. Here is the reply I received from C. Brian Grimm, the Alliance’s Marketing Director:
– Mixed mode WPA (simultaneous WEP and WPA clients in one BSS/ESS) is discouraged by the Wi-Fi Alliance because this mode of operation is inherently insecure.
– WPA Certification testing includes a negative test to ensure that the device under test does not support mixed mode in its default configuration.
– However, as a general rule, any vendor is free to offer any proprietary feature above and beyond Wi-Fi features. LEAP is probably the most famous example. LEAP-enabled products may still receive Wi-Fi Certification even though the LEAP feature is not part of any Wi-Fi certification test. Similarly, if a vendor offered a mixed mode feature that was not part of the product’s default configuration, though the Alliance discourages this, the product could still be WPA and Wi-Fi Certified.
- No AdHoc support
WPA currently supports Infrastructure mode only, with AdHoc mode support delayed until WPA2. The larger impact of this missing feature may be on Wireless Ethernet Bridges like the Linksys WET11 and WET54G, which perform some of their more useful tricks in AdHoc mode.
Conclusions
I have to say that the WPA-enabled performance I’ve seen so far, especially on older Intersil-based 11b clients, is much better than I expected it to be. I’m also surprised at the optional implementation of AES encryption by Broadcom, although the throughput loss when using the default WPA TKIP encryption might explain that choice.
The good news is that when it works, WPA is vastly more secure than WEP, and a hell of a lot easier to use, especially in the consumer-friendly Pre-Shared Key (WPA-PSK) mode. The bad is that if the present trend continues, many WLAN owners may have to abandon their older products and purchase all new stuff in order to enjoy the benefits of WPA.
For more info:
- Wi-Fi Alliance’s WPA website
- Wi-Fi Protected Access White Paper – Contains clear explanations of WPA’s technical underpinnings (PDF)
- Wi-Fi Protected Access Media Presentation – Presentation with good background and overview of WPA (PDF)