Introduction & Basic Features
| BuffaloTech 125* High Speed Mode Wireless Remote Secure Gateway (WZR-RS-G54) | |
|---|---|
| Summary | 802.11g router with Broadcom ‘Afterburner’ speedup technology, AOSS, and built-in PPTP VPN endpoint |
| Update | None |
| Pros | • Wireless routing w/ WDS bridging / repeating • Push-button secure wireless setup • No WEP or WPA throughput hit • Built-in fast PPTP endpoint with Wake-on-LAN • Includes TightVNC remote desktop control app |
| Cons | • WPA not supported for WDS bridging • Firewall lacks competitive features • Can’t use bridging/repeating with AOSS • Poor range performance in 125* High Speed Mode |

Buffalo Technology’s WZR-RS-G54 125* High Speed mode Wireless Remote Secure Gateway is the company’s first attempt at a consumer router with built-in VPN endpoint. But instead of going with the usual IPsec endpoint, Buffalo instead chose to break from the pack and incorporate a PPTP-based solution. While my first reaction to this choice was puzzlement, after my time with the product, and a little research, I think I’ve come to understand why the company decided to buck the current competitive approach.
The WZR is the first Buffalo product I’ve had my hands on that uses their rounded rectangular packaging. But instead of the off-white case used by its WHR3-G54 non-endpoint sibling, the WZR has a pearlescent light-gray finish, which, to my eye, is a big improvement over Buffalo’s previous ovoid case.
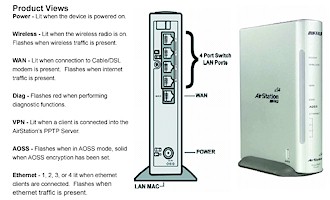
Indicators on the front panel (Figure 1) include Power, Wireless, and Diag plus Remote Access (VPN), which lights when a PPTP tunnel is active and AOSS, which indicates when Buffalo’s AirStation OneTouch Secure System automatic secure wireless setup system is working. There’s also a single WAN and four Ethernet (LAN) link / activity lights
Figure 1: Front and Rear panels
(from WZR-RS-G54 User Manual)
(click image for larger view)
The rear panel has four 10/100 LAN ports, single 10/100 WAN port, power connector and external “MC (custom “Lucent”) antenna connector hidden behind a little sliding cover. All ports are auto MDI / MDI-X and the WAN port can have its speed and mode set via the Admin interface. The Reset-to-Factory-Defaults Init switch is on the bottom and there’s a dedicated AOSS switch on the side.
Negatives were that I found that the translucent panel over the indicator lights softened them so much that they tended to blur together and also limited their visibility when viewed off axis. I also found that the itty-bitty MC external antenna connector also wasn’t aligned with the hole in the case. (When I opened the case I found this caused by the antenna board not having been seated properly during assembly. When I popped the board into its proper place, it aligned correctly.) And finally, neither the case nor stand have any wall / ceiling mounting features.
Internal Details
Opening the WZR’s case reveals a clean, simple design, based on a Broadcom BCM4704 processor, which is a suped-up version of the BCM4702 used in earlier Buffalo products. The dual-dipole antennas are on a board seen on the left hand side of Figure 2, which puts them at the top of the case when the product is normally positioned on a desk or shelf.
Figure 2: Case open
(click image for larger view)
Figure 3 shows the same side of the board, but with the antenna and main boards removed from the case. The pad pattern in the empty space to the left of the processor looks to me like it’s set up for a second mini-PCI connector, so it appears that the board could also be used in a dual-radio product.
Figure 3: Board – Processor side
(click image for larger view)
Figure 4 reveals the hiding spot for the Broadcom-based Buffalo WLI-MPCI-G54 mini-PCI radio, which has been used in other Buffalo designs and is essentially a copy of the Broadcom reference design. You can also see the Broadcom BCM5325 5/6 Port 10/100 switch that handles LAN (and radio) switching duties.
Figure 4: Board – Radio side
(click image for larger view)
Rounding out the design are 64 MBytes of RAM, 8 MBytes of Flash and an Altima (Broadcom) AC101L 10/100 Ethernet Tranceiver for the WAN port.
Routing Features
Aside from the PPTP endpoint features that I’ll cover shortly, the WZR’s routing features are essentially those of its predecessor, the WBR2-G54 (and probably, the WHR3-G54). The first difference I encountered was upon logging into the WZR for the first time (its default IP address is 192.168.12.1, its DHCP server is enabled by default and the radio is on with no security enabled).
Figure 5: First-Time “Top” screen
(click image for larger view)
Figure 5 shows a familiar-looking screen, except for the Network Service List link at the top that when clicked, takes you to that screen (Figure 6). Your exact screen will depend on what services and computers the WZR finds running (it does this by analyzing ARP requests) from among this list:
- Web / HTTP
- FTP
- File sharing
- Microsoft Remote Desktop / Terminal Services
- VNC Server
Figure 6: Network Services
(click image for larger view)
You’ll also always get a Wake-On-LAN icon that, when clicked, will send a WOL command to its respective computer. I first thought this screen was just eye candy, but found that it could have its uses, especially during remote access (note the ppp:tim service group from my PPTP connection). Of course, WOL isn’t supported on all systems and it’s up to you to track it down and enable it. On Win XP systems, you’ll find the control by clicking the Configure button in your network adapter’s connection properties and navigating to the tab shown in Figure 7.
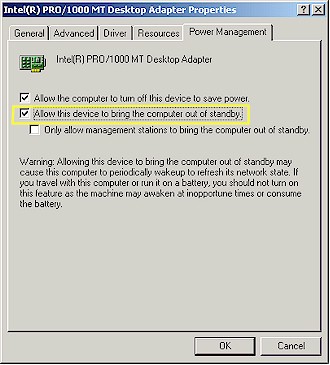
Figure 7: Wake-On-LAN enable (Win XP)
Tip: The Network Services screen can also be accessed by entering the LAN IP address for your WZR followed by /hosts.htm, i.e. http://192.168.12.1/hosts.htm.
Tip: Browsing shared files only works with Internet Explorer 5.0 and above.
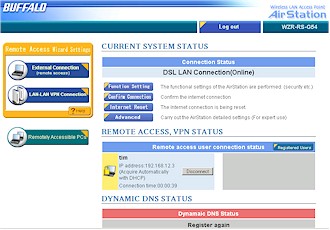
Every time after the first access, the “Top” page becomes the new, user-friendlier page shown in Figure 8. This page is perhaps a little too VPN-centric, but once I figured out the terminology used in the various buttons, I was able to figure out where to go.
Figure 8: New Top Page
(click image for larger view)
Note: According to Buffalo, it turns out that this new page and the “wizards” accessible from it need some tweaking. They may be temporarily removed in a firmware update due out soon.
Another welcome touch is the addition of dynamic DNS – especially useful in a product that’s meant to be frequently remotely-accessed via the Internet. Either the DynDNS or TZO services can keep the changing IP address that you get from your ISP pointed to either a domain name that you already own, or new one that they can provide.
In general, the admin server is responsive with mini-reboot time for each page’s changes around 5 seconds. Only one admin login is allowed at a time (you’ll get a cryptic screen if you’re admin #2) and you still can’t change the idle timeout for the admin interface. Network Address Translation (port forwarding) and Packet Filter (port / service filtering) controls are essentially unchanged and remain in need of a more user-friendly design. There’s also still no scheduled packet filtering or any sort of content filtering or proxy, Java, Active X , etc. blockers.
VPN Features
Before I plunge into the PPTP endpoint description, let’s first cover the WZR’s VPN pass-through capabilities. In a nutshell, it supports multiple pass-through sessions for IPsec, L2TP and PPTP clients and also supports connection to multiple remote VPN gateways. For some reason, there’s only a checkbox for IPsec passthrough on the Network Address Translation page, but Buffalo assured me that all three protocols are supported.
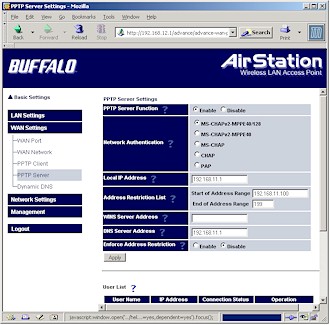
Figure 9 shows the controls (and defaults) for the WZR’s PPTP server, which turned out to be just fine for my test using a Win XP Home SP2 client.
Note: I actually started out using the built-in External Connection wizard (accessible via a button on the Top page). But I bailed out at the Host Name Registration step because I couldn’t follow the explanation of what I was supposed to enter, and just ended up entering my User account information on the PPTP Server page.
Figure 9: PPTP server configuration
(click image for larger view)
Note that the default “authentication” actually sets MS-CHAPv2 authentication and MPPE 40 / 128 bit tunnel encryption. The latter part is especially important since early PPTP implementations encrypted the authentication (login) transaction only, leaving the actual data in the VPN tunnel unencrypted. This false sense of security helped PPTP gain its reputation as a very weak “VPN” technology, which remains to this day…at least among some users.
I have to confess that I was one of those users, until I did a little research while writing this review. I’ve reached the conclusion that while the combination of MS-CHAPv2 / MPPE 40 / 128 isn’t as secure as L2TP or IPsec – which use stronger 3DES encryption and have the options of certificate-based authentication – it’s a hell of a lot easier to set up and use.
|
VPN Features, Continued
At any rate, the only thing I had to do in the WZR was to create a User account via the lower half of the PPTP Server page (Figure 10).

Figure 10: PPTP user account setup
A subtle point that you may have missed from Figures 9 and 10 is that there are two Address Restriction List entries. The one in the Server Settings section controls the range of IP addresses from the WZR’s DHCP server that are handed out to PPTP clients. The list in the User List section restricts the range of IP addresses that the WZR will accept PPTP connections from. This confusion is compounded by the fact that the Enforce Address Restriction enable / disable is grouped with the DHCP server-based restrictions. At any rate, you should note that you can’t define IP address ranges or subnets in the PPTP connection restriction control.
Once I had the WZR PPTP server setup, I followed the procedure in the printed VPN Setup Guide that came with the WZR to configure my Win XP computer (the instructions also cover Win 98SE, ME, and 2000 setup). All I had then to do was hit the Connect button on the WinXP Network Connection window and I was part of the WZR’s LAN.
Once connected, I found that network browsing (My Network Places) didn’t work, so I had to find out the IP address of the share(s) that I wanted to connect to and use Run and enter the UNC notation (i.e. 192.168.12.4). An easier way, however, was to log into the WZR’s admin interface and use the /hosts.htm screen or click the Remotely Accessible PC’s button on the /vpn/top-vpn.htm screen to get a screen similar to Figure 6. Once there I could see the IP addresses of all connected PCs or, if running IE, click on the Shared Files icon to get to the shares.
Buffalo’s main pitch for the WZR is “Access your PCs..Anytime…Anywhere”, i.e. as a replacement for GoToMyPC and similar remote-access subscription services. But rather than leaving buyers on their own to obtain a remote control application, Buffalo bundles one with the WZR. I installed the copy of TightVNC that Buffalo includes on the WZR’s CD onto both my test machines. (TightVNC is a free remote control software package derived from the popular VNC software.) I’ve used pcAnywhere and, at least for my simple needs, TightVNC seemed like a good (and did I mention free?) substitute, and I got it up and running with no problems on the first try.
VPN Features – LAN to LAN PPTP
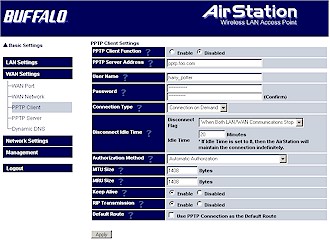
The WZR’s PPTP endpoint also contains a PPTP Client (Figure 11) that can be used to connect to a remote PPTP server to form a LAN-to-LAN PPTP tunnel. It also has a built-in configuration “wizard” (LAN-LAN VPN Connection button), but once again I bailed out while using it.
This time it was at the CONFIRM HEAD OFFICE CONNECTION SETTINGS screen, where I was baffled by the User idea used for connection entry. With no on-line help, or information in the User Manual or VPN Setup Guide to help me out, I actually found the PPTP Client screen less confusing.
Figure 11: PPTP client setup
(click image for larger view)
The Client screen contains a number of options that could use better explanations somewhere in the documentation, along with some setup examples. Since I didn’t have a second WZR (Buffalo actually was going to send one, but I asked them not to) and no PPTP server handy, I didn’t test a LAN-to-LAN connection. But if you’re familiar with PPTP setup, you should be up and running in no time – just use the PPTP Client and skip the “wizard”.
Buffalo has included a number of handy features for more advanced PPTP setup that you can see by looking at the PPTP Server and Client screen shots. The Client has many options for keeping the tunnel connected (or not), and also lets you control whether RIP routing information is sent through the tunnel and whether all Internet-bound traffic is directed through the PPTP tunnel (Default Route).
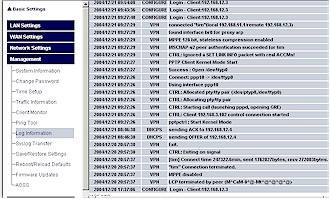
Finally, decent VPN setup and teardown information is available either via the built-in Log Information screen (Figure 12) or directed to a syslog server of your choice.
Figure 12: PPTP logging
(click image for larger view)
By the way, the WZR’s logging features are pretty extensive (14 different categories with “Error” and “Notice” levels), with the notable exception of website traffic logging.
VPN Performance
I used Qcheck and IxChariot to get a handle on the WZR’s PPTP tunnel throughput. The chart below shows that the PPTP tunnel throughput in both directions is the fastest that I’ve ever seen! Its 14 – 16Mbps is faster than some consumer routers provide for normal NAT routing and enough to keep up with even some of the faster broadband connections available outside the U.S. And all without RC4 encryption hardware acceleration in the Broadcom processor.
Although the number of User accounts that the WZR supports is 100, I asked Buffalo whether there was a limit on the number of simultaneous PPTP tunnels. The reply came back that there is no hard limit enforced (nor is there any way to limit it in the User interface), so it’s up to the administrator to monitor his / her network traffic patterns to ensure that tunnel users’ response times are satisfactory.
IPsec VPN Performance Test Results
| Test Description | Transfer Rate (Mbps) [1 MByte data size] |
Response Time (msec) [10 iterations 100 Byte data size] |
UDP stream [10s @ 500kbps] |
|
|---|---|---|---|---|
| Actual throughput (kbps) | Lost data (%) | |||
| Local to Remote | 14.4 | 1 (avg) 1 (max) |
500 | 0 |
| Remote to Local | 16.2 | 1 (avg) 3 (max) |
500 | 0 |
| Firmware Version | V 2.31 | |||
See details of how we test.
Routing Performance
Testing Notes:
• All tests are all run with LAN endpoint in DMZ
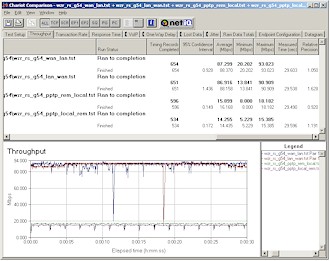
Routing performance was extremely impressive and shows the punch that the newer Broadcom processor packs. The chart and Figure 13 show for all intents and purposes wire-speed routing, which I’ve seen on only the ASUS SL-1000 and USR 8200. These products use the Philips PTD2210 Gateway-on-a-chip and Intel IXP422 network processor respectively.
Figure 13: PPTP and Routing throughput
(click image for larger view)
Since throughput was so speedy, I thought I’d check to see how good UDP streaming was and ran tests using a 1Mbps stream rate in addition to my usual 500 kbps. The results showed that the WZR was still going strong at the higher streaming rate with results in both directions losing only a few Kbps and an occasional error rate in the 0 – 1% range. Impressive!
Routing Performance Test Results
| Test Description | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
|---|---|---|---|---|
| Throughput (kbps) | Lost data (%) | |||
| WAN – LAN | 88.4 | 1 (avg) 1 (max) |
500 | 0 |
| LAN – WAN | 88.2 | 1 (avg) 1 (max) |
500 | 0 |
| Firmware Version | V2.31 | |||
See details of how we test.
Wireless Features
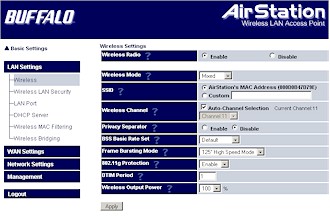
Figure 14 shows the main wireless settings screen, which has a few changes.
Figure 14: Wireless settings
(click image for larger view)
The screenshot shows the default settings, which include Mixed Wireless Mode (vs. alternates of 11b only and 11g only), Broadcom’s 125* High Speed Mode (Afterburner) Frame Bursting Mode kicked in (alternates are normal Frame Bursting Mode and Disable) and 802.11g Protection (which ensures that 802.11b clients are heard) enabled.
A new control is the Auto-Channel Selection, which ensures that “the AirStation will continually search for the clearest channel and set itself accordingly”, according to its on-line Help. I was disappointed to see that there are still no Transmit rate controls and that there isn’t a control to keep WLAN and LAN traffic separate, as the Privacy Separator does for WLAN-to-WLAN client traffic.
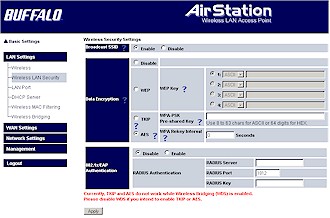
Moving on to wireless security (Figure 15), Buffalo has added AES as a WPA-PSK option and added support to relay 802.1x authentication requests to an external RADIUS server. But WPA RADIUS (“Enterprise”) mode is still not supported, nor is WPA-PSK in WDS connections.
Figure 15: Wireless security
(click image for larger view)
Finally, WDS-based bridging and repeating remains essentially unchanged, except for a note that “* WDS cannot be enabled while TKIP or AES is enabled” added right under the Wireless Bridging enable control. I also found that trying to enable WDS when the router was set to 125* High Speed Mode was answered with a screen telling me that was a no-no.
Wireless Performance
NOTES:
• “Signal Strength” readings were not available
• Test client was a Buffalo Tech WLI-CB-G54S Cardbus client card in a WinXP Home Dell Inspiron 4100 laptop
• Tests are for STA to AP (uplink) unless otherwise noted
Even though I’d previously tested Broadcom’s “Afterburner” throughput-enhancement technology when I reviewed the Linksys WRT54GS back in April, this was my first test of Afterburner with its 125* High Speed Mode moniker. No matter what it’s called, however, I once again found that Broadcom’s wireless speed-enhancement technology hurts rather than helps throughput under lower-signal conditions.
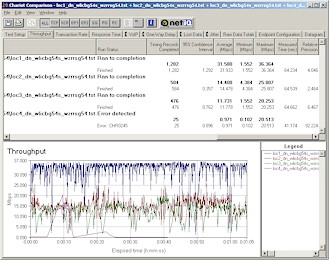
Figure 16: Four location throughput comparison – downlink
(click image for larger view)
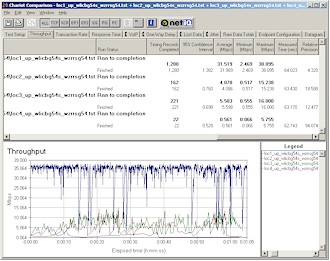
Figures 16 and 17 are IxChariot plots at my four test locations for down and uplink tests respectively. You can see that once you get a wall or two between the WZR and client that throughput drops significantly, with the uplink case definitely suffering more. Both tests fared very poorly in my outside Location 4 test with the downlink test quitting after about 40 seconds when the connection was lost.
Figure 17: Four location throughput comparison – uplink
(click image for larger view)
The missing UDP streaming results in the uplink throughput table above were caused by BSOD’s shortly after I started Qcheck UDP streaming tests at my normal 500kbps rate. I could consistently get a Win XP SP2 BSOD with DRIVER_IRQL_NOT_LESS_OR_EQUAL message and crash dump when I tried to run the test at anything other than my best-case test location (with approximately 6 feet between WZR and client). After some thought, I decided to try changing the WZR’s Frame Bursting settings – first to Frame Bursting, then to Disabled. In both of these cases, the UDP streaming test ran fine at the same test location where it had consistently BSOD’d.
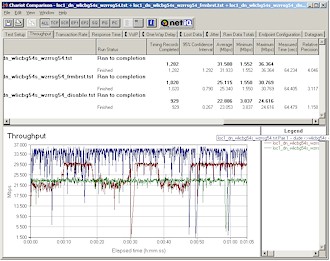
This UDP streaming fix prompted me to also re-run throughput tests with the Frame Bursting and Disabled Frame Bursting settings at my outside test location (Location 4). Figure 18 shows that throughput performance significantly improved – essentially changing this location from unusable to having respectable throughput.
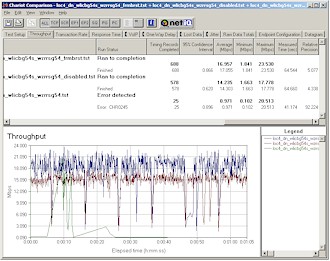
Figure 18: Location 4 downlink – Frame Bursting mode comparison
(click image for larger view)
802.11g Wireless Performance Test Results
| Test Conditions
– WEP encryption: DISABLED |
Firmware/Driver Versions
AP f/w: |
||||
|---|---|---|---|---|---|
| Test Description | Signal Strength (%) | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
| Throughput (kbps) | Lost data (%) | ||||
| Client to AP – Condition 1 | 0 | 32 [No WEP] 31.6 [w/ WEP] |
1 (avg) 1 (max) |
469 | 0 |
| Client to AP – Condition 2 | 0 | 4.1 | 1 (avg) 1 (max) |
0 | 0 |
| Client to AP – Condition 3 | 0 | 5.6 | 1 (avg) 1 (max) |
0 | 0 |
| Client to AP – Condition 4 | 0 | 0.6 | 1 (avg) 1 (max) |
0 | 0 |
See details of how we test.
More fun with Frame Bursting
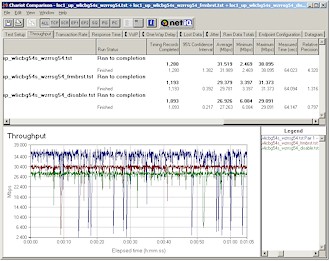
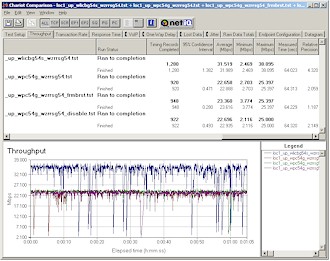
For a look at best-case throughput improvement from 125* High Speed Mode, I repeated the three Frame Bursting Mode tests at Location 1. Results in Figures 19 and 20 show approximately 17% uplink (27.263 to 31.989 Mbps) and 39% downlink throughput improvement (23.053 to 31.933).
Figure 19: Location 1 uplink – Frame Bursting mode comparison
(click image for larger view)
Figure 20: Location 1 downlink – Frame Bursting mode comparison
(click image for larger view)
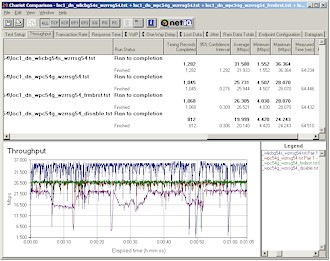
The last comparison I did was to see if the WZR could improve throughput for non-125* High Speed Mode Broadcom clients. I used a Linksys WPC54G (original rev) with Win XP 3.30.15.0 driver and once again ran uplink and downlink tests with the WZR set to its three Frame Bursting modes.
Figure 21: Location 1 uplink – Frame Bursting mode comparison w/ Linksys WPC54G
(click image for larger view)
Figure 21 shows no improvement in best-case uplink throughput improvement with the Linksys card, but Figure 22 shows a boost in downlink throughput for both Frame Bursting and 125* High Speed Mode modes. But note that neither improvement matches the performance of the WZR with its matching 125* High Speed Mode-enabled card (the top trace in both plots).
Figure 22: Location 1 downlink – Frame Bursting mode comparison w/ Linksys WPC54G
(click image for larger view)
Given these results, my recommendation would be to switch the WZR’s Frame Bursting Mode to its Frame Bursting setting if you want to reach clients anywhere outside of the same room. You’ll still get some throughput boost, but more importantly, you’ll get vastly improved throughput vs. range performance.
By the way, security mode performance is excellent, with no discernible throughput change when using WEP 128 or WPA-PSK / TKIP or AES modes.
Wrap Up
In the dog-eat-dog market that consumer networking has become, manufacturers are constantly challenged to come up with products that allow them to eke out anything above the razor-thin margins they normally get. So I have to give Buffalo credit for the buzz they have created around the WZR-RS-G54, especially since its main “innovations” are smart feature bundling and savvy marketing.
But what I haven’t seen before the WZR-RS-G54, is the combination of near wire-speed routing and equally impressive PPTP endpoint throughput. And the bundling of the open source TightVNC remote control application with a mainstream consumer router is also a welcome first.
To offset these positive points, however, is the fact that Buffalo’s routing features are getting a bit long in the tooth. Competitive products have incorporated Class of Service (CoS), Quality of Service (QoS), bandwidth control and user-based content filtering, and it’s about time that Buffalo came up to par, and even raised the stakes a little. And finally, its user interface, though slowly improving, still lacks polish when compared to what’s found on many other products.
But all things considered, the WZR-RS-G54 is definitely a step forward, and one worth taking if you frequently need to reach out and touch your home or office LAN while keeping the bad guys at bay.