Introduction

| At a Glance | |
|---|---|
| Product | DrayTek Vigor 2910G Dual WAN Wireless Router (DR2910G) |
| Summary | Wireless dual-WAN router with 4 port 10/100 Ethernet switch, Atheros Super-G wireless, VPN endpoints and FTP to USB drive. |
| Pros | • Dual-WAN and 3G WWAN Support • Up and downlink bandwidth control • No Subscription Content Filtering • Wake on LAN/WAN |
| Cons | • No Gigabit LAN • Not fast enough for fiber or other high B/W connections • Not a true UTM – no Anti-Virus • Documentation lacks examples |
An article in the December 31, 2009 USA Today reports an increase in the amount of cyber-robberies targeted at small businesses. The article cites an example of a county government that was a victim of cyber crime for nearly $300,000 dollars. The county’s bank faulted the county government as “the county’s network did not have an effective firewall, its virus protection was woefully out of date and the county’s treasurer did not follow internal controls that would have prevented the unauthorized transfers.”
The article illustrates that security threats to businesses and consumer networks from the Internet are growing, making it more important than ever to deploy solid network security devices such as firewalls, virus protection, and web filtering technology.
In this review, I’m going to look at the Draytek Vigor2910G Dual-WAN Security Router. This router is equipped with a highly configurable firewall with the ability to filter Instant Messaging (IM), Peer-to-Peer (P2P), and Web traffic to help reduce the risk of network compromise such as the one cited in the USA Today article.
The 2910G is one of six models in Draytek’s 2910G line, ranging from the 2910G to the2910VGi. The “V” in the model name means the router has 2 FXS ports, the “G” in the model name means the router has wireless capability, and the “i” in the model name means the router has ISDN capability. I’m going to cover the “G” model with wireless capability.
Under the Covers
The router is enclosed in a basic plastic black case measuring 8.5”W x 6.25”D x 1”H. The front of the device has indicator lights showing activity on the WAN and LAN ports, as well as a several other indicators providing status on enabled features.
Feature indicator lights show when the DMZ functionality is enabled, when a QoS rule is enabled, when DoS protection (=”Attack”) is enabled, when the WLAN radio is enabled, and when a 3G USB card is active as shown below in Figure 1.
Figure 1: 2910G LEDs
The rear of the device has (4) 10/100 LAN ports, (1) 10/100 WAN port, a USB port, power connector and on/off switch, as well as two upgradeable (RP-SMA connector) wireless antennas (Figure 2). The power supply is a typical 100 – 240 V wall wart. I appreciate that the 2910G has an on/off switch. To me, it just seems better turning a device off before unplugging it.

Figure 2: Rear view of ports
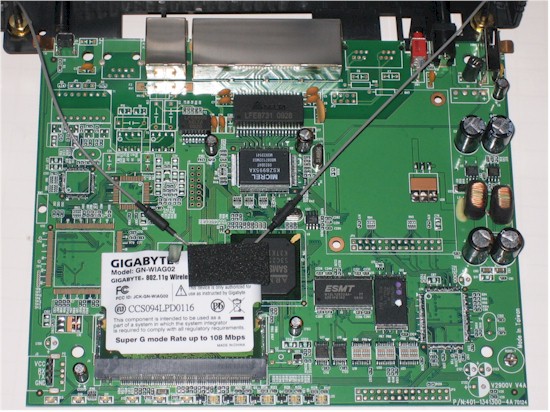
Taking a look at the board (Figure 3) reveals a Samsung S3C2510 32Bit ARM9 processor clocked at 166 MHz. Additional components include a Micrel KSZ8995XA 10/100 switch, 16 MB of RAM and 4 MB of flash. The radio is a Gigabyte GN-WIAG02 mini PCI card using an Atheros AR2414A SoC Super-G radio.
Figure 3: 2910G board
Configuration
The 2910G is configured via a web browser at its default LAN IP address of 192.168.1.1. There are 15 menus choices along the left hand side of the web configuration GUI. Each menu has three to eleven sub menus, for a total of 80 different configuration screens. Draytek has a nice live demo of all its menu screens located here. I recommend you poke through these screens as you read through the review.
Draytek provides a 214 page manual on the CD that comes with the router. There is a more detailed manual on the Draytek website. Both manuals are concise, but I found them lacking examples and clear explanation on how to configure desired functions.
In the US, Draytek is represented by Strowger Inc. I mention this, as I found Strowger’s website to be a useful source of information on networking and configuring the Draytek router, with guides on how to configure VPNs, Load-Balancing, and QoS.
WAN
The 2910G supports up to two WAN connections. It has a primary 10/100 Mbps WAN port for connecting a wired ISP service such as a DSL or Cable modem using Static, DHCP, PPPoE, and PPTP/L2TP connection methods. The 2910G also supports a second WAN connection via a second Ethernet or USB-connected WWAN dongle or mobile phone.
Draytek lists 72 different compatible 3G modems / phones on their website. Alternatively, a second wired ISP service such as a DSL or Cable ISP service can be connected to the WAN2/P1 port. When the WAN2/P1 port is enabled as a WAN port, the router will only have 3 LAN ports. I tested the 2910G with two wired Internet connections.
In either dual-WAN configuration, the 2910G supports failover, bandwidth based load-balancing, and protocol specific load-balancing between the two WAN connections. Failover is pretty quick on the 2910G. I set up the router for failover mode with WAN1 as primary, ran a continuous ping to yahoo.com, then disconnected WAN1. As you can see in Figure 4 below, only one ping was lost while the router switched over to the second WAN connection.
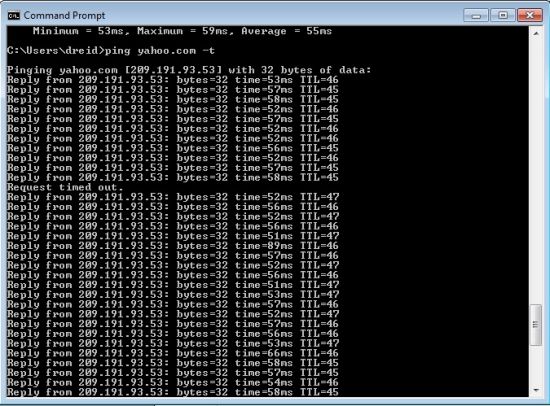
Figure 4: Ping test for WAN failover
The default setting is for the 2910G to automatically load balance traffic between WAN1 and WAN2, essentially balancing traffic equally across the two ports. Load balancing can be fine-tuned by defining the upload and download speed of each WAN connection. This is useful if one of the two connections has significantly higher upload or download speeds.
Traffic flows can be defined over the two WAN ports so specific traffic routes primarily over one connection, yet will still failover in case one connection is down. Protocol, source and destination IP addresses, and destination port values can be used to define which traffic flows route over which WAN port.
To test this feature, I set up a simple rule to route ICMP (ping) traffic over the WAN2 interface as shown in Figure 5. While running a continuous ping to yahoo.com, I could see packet counts increasing on the WAN2 interface (via the Online Status menu), but not on the WAN1 interface, verifying the ICMP traffic was indeed routing over the WAN2 interface as specified.
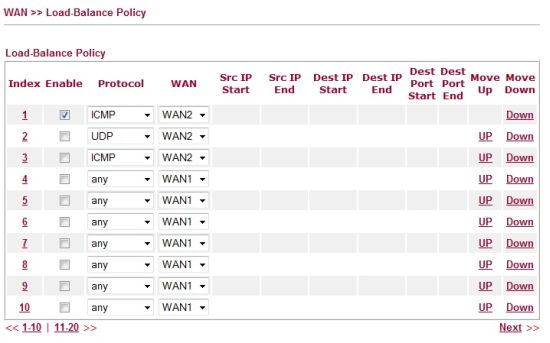
Figure 5: Load balancing policy setup
A possible use for this load balancing feature on the 2910G is to separate UDP delay sensitive traffic from TCP based traffic. For example, UDP based VOIP traffic could be routed over one WAN connection while TCP based web and email traffic could be routed over the other WAN connection, ensuring bandwidth and quality for the VOIP calls and still passing web and email traffic over the other WAN connection.
Bandwidth Management
In addition to bandwidth and protocol based load balancing over Dual-WAN connections, the 2910G can apply bandwidth limits to specific hosts or services, as well as reserve bandwidth for specific applications.
There are three bandwidth configuration options labeled as Session, Bandwidth and Quality of Service. The Session bandwidth configuration option enables limiting bandwidth utilization per connection, such as P2P file transfers. A P2P file transfer is a connection which can consume multiple sessions to complete. By limiting host connections to a maximum number of sessions, the 2910G can control bandwidth consumption by session hungry applications such as BitTorrent.
A more straightforward option is to limit bandwidth utilization by host or IP range using the Bandwidth configuration option. As you can see below, I’ve restricted host 192.168.1.10 (my laptop) to a 250 kbps upload and download bandwidth limit.
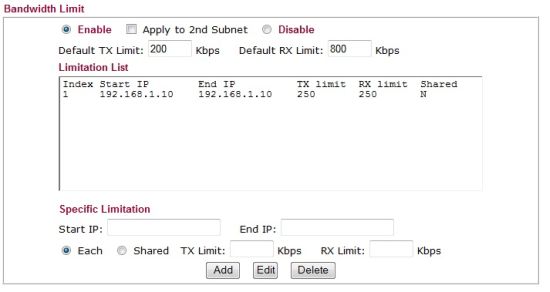
Figure 6: Setting bandwidth limits
To test this configuration, I ran a speed test on my DSL line from my laptop behind the 2910G via speedtest.net with bandwidth limits disabled. My DSL line measured 630 Kbps upload and 11.31 Mbps download. With the bandwidth limit shown in Figure 6 enabled, my DSL line measured 220 Kbps upload and 310 Kbps download, showing the 2910G effectively limited my bandwidth consumption. The 2910G didn’t exactly limit bandwidth to 250 Kbps, but it clearly showed its effectiveness.
The third bandwidth configuration option is to implement Quality of Service (QoS). The 2910G allows QoS to be applied to packets via Class Indexes based on IP address, IP Precedence or DSCP values, as well as custom or predefined protocols. There are three customizable Class Indexes, and each can have up to 20 rules of matching conditions. A percentage of the total bandwidth is assigned to each of these three Class Indexes, with the remainder going to all undefined traffic.
For example, I created a simple QoS rule to guarantee 10% of the bandwidth reserved for traffic using the POP3 protocol (Email) and for traffic using the HTTP protocol (Web). Once configured, there is a useful Online Statistics feature that gives a snapshot of bandwidth usage by traffic type as shown in Figure 7.
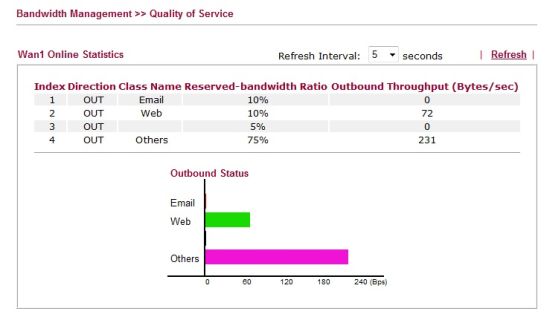
Figure 7: QoS bandwidth statistics
VPNs
The 2910G supports several forms of VPN connections, including IPSec site-to-site tunnels with other VPN capable routers, IPSec client-to-site tunnels for remote user access, and PPTP client-to-site tunnels for even simple remote user access. As mentioned, Strowger’s website has some useful screen shots on configuring VPNs on the 2910G. Draytek lists the 2910G as capable of supporting up to 32 VPN tunnels (16 dial-in and 16 dial-out).
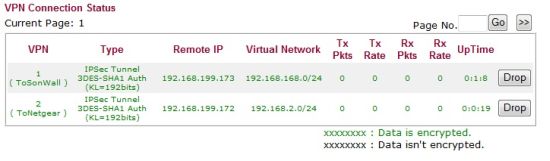
I was able to set up 3DES IPSec site-to-site tunnels between the 2910G and both a Netgear UTM10 and SonicWall TZ100W. DES, 3DES, and AES 128,192, and 256 bit encryption are all supported. Figure 8 shows the VPN status screen with my two active tunnels.
Figure 8: VPN status
The 2910G comes with unlimited licenses for Draytek’s IPSec SmartVPN Client software. The manual lists this client as compatible with Windows XP and 2000. I had no problem installing and configuring the Smart VPN Client on an XP Pro machine. Setting up the 2910G was a little more difficult, it took some poking around on the router before I figured out that Client VPN connections are configured in the Remote-Dial-in User menu. Once configured, the software connected as expected to the router, allowing me to access devices on the 2910G’s LAN from a remote location.
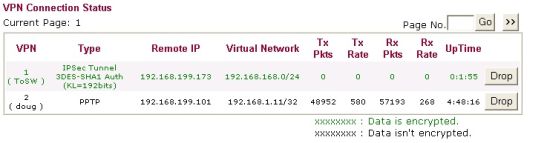
I also tested client-to-site VPN with the 2910G using Microsoft’s built in PPTP client on both XP and Windows 7. PPTP VPN set up is a breeze. There is no need to configure things like encryption type, Main or Aggressive mode, DH Group 1 or 2, pre-shared keys, or Perfect Forward Secrecy (PFS). All you need to do is create a user name and password in the router and set up the destination IP/URL on the Windows PC. Figure 9 shows the VPN status screen with a site-to-site tunnel and my PPTP tunnel.
Figure 9: IPsec and PPTP VPNs
I like that Draytek provides this PPTP VPN option. I’m not a big fan of IPSec VPN Clients as they can be a pain to configure and supporting end users can be challenging. SSL VPN Clients are a lot easier than IPSec and about as secure, but the 2910G doesn’t support SSL VPNs. PPTP isn’t as secure as SSL or IPSec, but it’s better than nothing, and extremely simple!
Security
To manage security on a network, a router must first control who has access. Simple authentication can be applied via the 2910G’s Web Authentication menu. Enabling Web Authentication will force each end user (wired and wireless) to authenticate to the router with a valid user name and password before they are allowed to pass traffic through the router. For a small network, I found this feature to be a simple way to force end user authentication.
The 2910G’s Stateful Packet Inspection (SPI) firewall supports the usual features such as port forwarding and DMZ configurations. For more detailed control over specific traffic flows through the 2910’s firewall, you configure Call and Data Filter Sets. Call Filter Sets on the 2910G are used with dial-up Internet Services, such as ISDN connections. Data Filter Sets are used with always-on Internet Services, such as DSL or Cable connections.
Filter Sets are lists of rules specifying traffic flows permitted or denied through the router, based on traffic characteristics defined in various Objects, Groups, and Profiles. Twelve different Filter Sets can be created, each with up to seven Rules. Multiple Filter Sets can be daisy-chained together. (For those familiar with Cisco IOS, a Filter Set is akin to an Access Control List [ACL] and a Rule is akin to an individual line in an ACL.)
To apply Call and Data Filter Sets, you need to get comfortable with configuring Objects, Groups and Profiles. Objects are: IP addresses, ranges, or subnets; services defined by protocols or port ranges; and IM, P2P, or streaming applications. Groups are collections of IP or service Objects. Profiles are collections of IM, P2P, and streaming Objects.
Below are the defined IM, P2P and streaming applications for creating Call and Data Filter Sets.
- Instant Messenger (IM) Applications: MSN, Yahoo, AIM, ICQ, QQ, iChat, Jabber/GoogleTalk, GoogleChat, and AliWW.
- Web IM services: eMessenger, WebMSN, meebo, eBuddy, ILoveIM, ICQ Java, ICQ Flash, goowy, IMhaha, getMessenger, IMUnitive, Wablet, mabber, MSN2GO, KoolIM, MessengerFX, MessengerAdictos, and WebYahooIM.
- P2P protocols: SoulSeek, eDonkey, FastTrack, OpenFT, Gnutella, OpenNap, BitTorrent, and Winny.
- Streaming applications: MMS, RTSP, TVAnts, PPStream, PPlive, FeiDian, UUSee, NSPlayer, PCAST, TVKoo, SopCast, UDLiveX, TVUPlayer, MySee, Joost, and FlashVideo.
So, to block all of the above IM, P2P and streaming applications, I created three objects. One object included all the IM applications, the second object included all the P2P protocols, and the third object included all the streaming applications. I then created a Profile which included all three of these objects. This Profile was then selected as the first Rule of a Filter Set, and the Firewall was configured to use this Data Filter Set.
With the 2910G’s firewall configured with the above rule, I tried launching the Yahoo Messenger client, but it kept failing to login, verifying the filter and my configuration was active.
In addition to the firewall controls above, the 2910G’s firewall provides Denial of Service (DoS) protection. Any of the following traffic types can be selected for detection and blocking on the 2910G: SYN flooding; UDP flooding; ICMP flooding; Port Scans; IP Options; Land; Smurf; Traceroute; SYN fragments; Fraggle Attacks; TCP flag scans; Tear Drop; Ping of Death; ICMP fragment; and Unknown Protocols.
With DoS protection enabled on the router, I ran a port scan from outside the router on the WAN interface. Syslog messages, such as those below, were generated indicating the port scan was detected.
2010/01/04 20:50:02 — DoS portscan 166.82.166.198,34488 -> 166.82.199.15,3918 PR 6(tcp) len 20 44 -S 858797236 0
2010/01/04 20:50:02 — DoS portscan 166.82.166.198,34488 -> 166.82.199.15,19315 PR 6(tcp) len 20 44 -S 858797236 0
In addition to the firewall, the 2910G offers Content Security Management (CSM). The 2910G’s CSM menu lists IM/P2P, URL, and Web Content filtering options. IM/P2P (and streaming) filtering are applied via firewall Call and Data Filter Sets as described previously, while URL and Web Content filters are applied in the CSM menu.
URL content filtering on the 2910G allows logging URL access and applying blacklists or whitelists. Up to eight different 32-character lists of keywords can be filtered in a blacklist or whitelist. (For reference, all seven of George Carlin’s famous “Words You Can Never Say on Television” total 48 characters.)
Also within the URL content filter menu is the ability to block web sites with embedded code or files in the form of Java, ActiveX, compressed files, executable files, multimedia files, cookies, and proxy services. The URL content filter can also be customized to exclude specific subnets, and can be applied in a user-defined schedule.
Finally, the 2910G offers Web Content filtering through a partnership with SurfControl, which is owned by WebSense, a well-recognized name in Content filtering. There are 41 different categories that can be selected for filtering as shown in Figure 10 below.
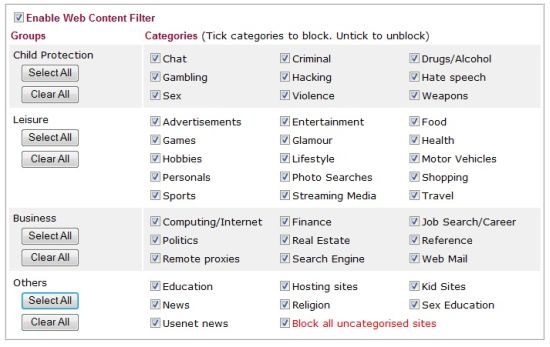
Figure 10: Web content filter categories
With the web content filter enabled, trying to surf to a web site that matches any of the above categories results in a screen showing the message in Figure 11.
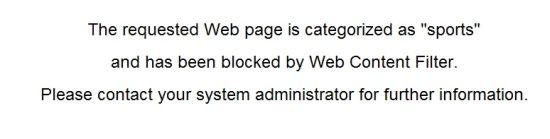
Figure 11: Blocked site message
Wake On LAN
A simple but effective feature I really like on the 2910G is the ability to do Wake on LAN (WOL) from the router. Not only does this provide a central place to power on PCs with WOL capability, it also enables WOL over the Internet, or WAN. (For more information on WOL, take a look at these articles here and here.)
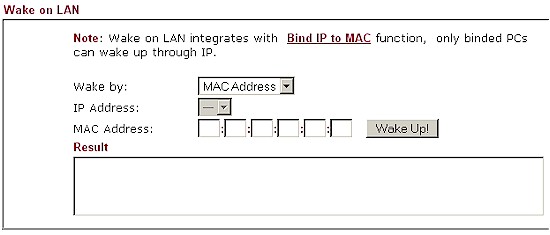
Figure 12: WOL screen
Let’s say you want to to access a PC or Server on your network remotely, but want to leave it powered off while you’re away. With remote access enabled on the 2910G or via a VPN connection, you can log into your 2910G from anywhere in the world. Once you’ve logged into your 2910G, you can then use the WOL function (Figure 12) on the router to power on your PC or Server for whatever purpose you had in mind, then power it off when you’re done. Not only does this save power and money, it is more secure to leave devices powered down when not in use.
Wireless
The 2910G has an 802.11b/g radio, and supports Atheros’ Super G, which is the bonding of two 802.11g 54 Mbps channels. Super G can improve wireless throughput if your wireless client supports it. I tested the wireless functionality of the 2910G with my laptop and had no issues with network connectivity. I’ll touch on wireless performance later.
To secure your wireless network, standard wireless security features include WEP, WPA, WPA2, and 802.1x authentication, with WPA / WPA2 in both in Personal (PSK) and Enterprise (RADIUS) forms. MAC address filtering can also be applied. As mentioned in the discussion on security features, Web Authentication when enabled will force wireless users to authenticate before being able to use the network.
Wireless Distribution System (WDS) bridging / repeating is also supported, allowing for an expanded wireless network using common security and network settings.
Consistent with the other bandwidth management features on the 2910G, there is an option for Station Rate Control. This feature allows configuring a bandwidth limit for each wireless client between 100 Kbps and 30 Mbps in increments of 100 Kbps. There’s also a Web Portal feature, which will redirect wireless clients upon first connection to a settable URL or show them a short message before passing them on to their desired destination.
Although you can block SSID broadcast, you can’t set the router’s transmit rate or power.
VLAN
The 2910G has basic VLAN capability in the form of port based VLANs. 802.1q VLAN tagging or trunking is not supported. Each of the four LAN ports can be a member of one or more of VLAN0-VLAN3.
To separate traffic between wireless PC, wireless users can be divided into 16 different wireless VLANs (similar to port based VLANs) based on authentication credentials. Further, members of each wireless VLAN can have a bandwidth limit applied, similar to the individual wireless bandwidth management feature.
Once wired and wireless VLANs are defined, a matrix of wired to wireless VLANs is available for defining whether clients in each wired and wireless vlan can access each other.
USB
If not in use with a 3G WWAN card, the USB port on the 2910G can be used to share files on a USB drive via FTP. I connected several USB thumb drives and they were all recognized by the 2910G. However, my SimpleTech 40 GB USB external drive was not recognized.
User names and passwords need to be created to allow for access to the FTP service since anonymous access isn’t allowed. Users can be configured for Read Only, Read/Write, and Read/Write/Delete permissions to the FTP service.
Logging and Reporting
Log messages on the 2910G can be sent via email and/or to a syslog server, but they aren’t saved on the router. It would be useful if the router could save logs to a file on the USB drive if enabled.
Draytek includes a syslog application (Figure 13) on the CD that comes with the router. I installed the application on an XP Pro PC and configured the 2910G to send its log messages to the IP address of the PC.
Figure 13: Draytek syslog application
With this application running, firewall, VPN, user access, WAN activity, and network activity are all saved and viewable, providing information on the performance of your network and providing a nice troubleshooting tool.
The 2910G also has a basic utility to display a chart of Data Flows as well as a simple Traffic Flow graph. The Data Flow chart shows a snapshot of current users TX and RX rates and active sessions. It also shows the number of active sessions on the WAN and peak TX and RX bandwidth usage as shown in Figure 14 below.
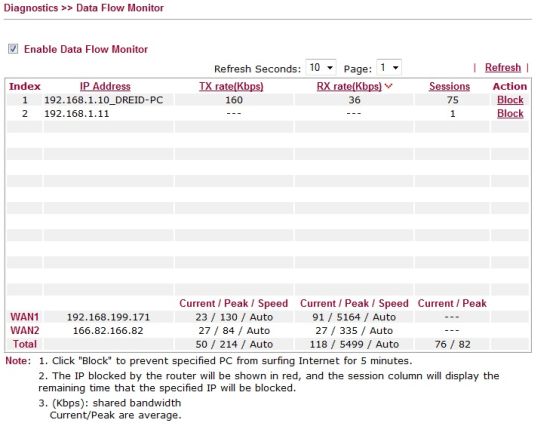
Figure 14: Data flow monitor
Performance
Some testing and analysis by Tim Higgins
The 2910G was tested by Tim using the standard SmallNetBuilder router and wireless performance tests and added to the Router and Wireless Charts. Routing throughput test results are summarized in Table 1 below. The results reflect the relatively old Samsung CPU used and won’t win any speed contests.
| Test Description | Throughput – (Mbps) |
|---|---|
| WAN – LAN | 27.5 |
| LAN – WAN | 27.9 |
| Total Simultaneous | 27.8 |
| Max Simultaneous Connections | 40 |
| Firmware Version | 3.2.3.1 |
Table 1: Routing throughput
Wireless performance is in line with other 802.11g routers. There is only one other 802.11g product in the Wireless Charts with open-air test results—the Cisco / Linksys WRT54G2. The performance comparison table for both products (Figure 15) shows similar performance, with perhaps a slight edge for the 2910G at the weaker signal test locations E and F.
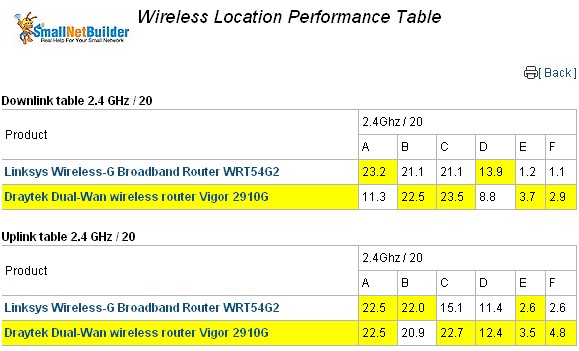
Figure 15: Wireless performance comparison – Cisco / Linksys WRT54G2
Tim’s testing didn’t cover VPN performance or performance with all the 2910G’s security features kicked in. So I used jperf with its default settings as my TCP throughput measurement tool. I used two laptops with a measured minimum throughput between them of 350 Mbps as my endpoints.
In other security-focused routers I’ve tested recently, I’ve seen significant differences in upstream versus downstream throughput. The 2910G’s throughput were so close between upstream and downstream measurements, I listed them as a single value in Table 2.
Table 2 shows that the 2910G passes data between the LAN and WAN interfaces at 30.2 Mbps with its Security features disabled, and at 24.1 Mbps with its Security features enabled. The Security features I enabled and disabled are the Firewall Call and Data filters, all DoS protection, and all CSM Features. In the last column, I measured VPN throughput on a site-to-site 3DES-encrypted tunnel between the 2910G and a SonicWall TZ100W at 5.3 Mbps.

Table 2: 2910G Routing and VPN throughput
Competitive Analysis
For a competitive measure, I compared the 2910G to a couple older routers with similar components. I used the TZ190 from SonicWall, a dual-WAN firewall security router to compare wired performance and the WRT54G2 from Linksys, a basic 802.11g wireless router, to compare wireless performance.
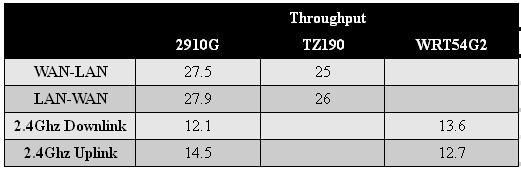
Table 3: Competitive performance comparison
As shown in Table 3, the 2910G’s wired performance is comparable to the TZ190 and the 2910G’s wireless performance is comparable the the WRT54G2. The key point is although the 2910G has solid security capabilities, it is running an older processor and wireless radio, which limit its routing and wireless speeds.
I recently reviewed Unified Threat Management devices including Netgear’s UTM10 and SonicWall’s TZ100W. Those two devices have significantly more security features than the 2910G, such as anti-virus, anti-malware, anti-spam, and Intrusion Protection/Detection. Their price tags are also significantly higher! Take a look at Table 4. As you can see, the 2910G holds its own for router features and supports more VPN tunnels.
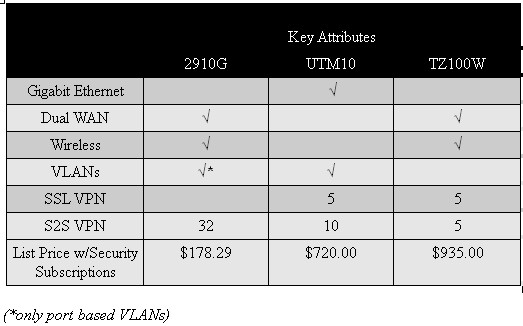
Table 4: Competitive Feature Comparison
Certainly, the price on the 2910G is an eye-catcher. At only $178 (Draytek devices are only sold at a couple locations to US customers, including GuideBand.com and DSL-Warehouse.com) with no annual subscription fees, the 2910G presents a very economical solution. The content filtering from WebSense for no extra charge alone is a heck of a deal! Equivalent content filtering capability on the TZ100W runs $95/year.
I asked Draytek how they can deliver the Content Filtering for free, and found that is is probably a temporary situation, judging from this reply:
"I’d like to inform you that we don’t need to pay for Surf Control’s Web Content Filter service for the moment since Surf Control was merged by another company. The server is still under maintenance and we could use this services till we change to another service provider."
Closing Thoughts
As a firewall, the 2910G has as many options for traffic filtering as some more advanced Cisco routers. But as a security device, the 2910G’s main value is its content filter. Even though I made comparisons to UTM devices earlier, the 2910G isn’t a UTM, nor does it pretend to be. It doesn’t scan traffic for malware and other malicious software, nor does it scan for viruses.
But it does have subscription-based content filtering, which provides a step up in security over other routers. Malware is often picked up through web activity, so a quality content filter blocking access to unnecessary and unacceptable web sites is a good step toward preventing malware from ever reaching your network.
In all, I was pleasantly surprised by the Draytek 2910G. Having never heard of the company before reviewing the device, I didn’t expect much. Draytek isn’t as well known in the US as Cisco, SonicWall or Netgear. But among the in-the-know folks who do know the company, their products have a reputation for reliable performance and plenty of features. And after spending a few weeks testing this device, I can see that reputation is well earned.
If you’re looking for a relatively inexpensive, yet effective solution to control web traffic on your small network, I recommend the 2910G. Its routing and firewall features are impressive, its content filtering is effective and it’s priced right. The only downside is its performance, which isn’t fast enough to keep up with any connection over 25 Mbps or so. But Draytek has plenty of other products that are built with more current processing cores that are up to the task. So we’ll be putting some of those to the test on SmallNetBuilder in the near future.