
| At a glance | |
|---|---|
| Product | Circle Media Circle With Disney () [Website] |
| Summary | Network appliance providing content filtering and scheduling of Internet access based on filters and user profiles. |
| Pros | • Easy to set up • Automatically detects Smart Home devices and excludes from management • BedTime schedules • No subscription fee • Remote management requires no setup port forwarding |
| Cons | • Management is iOS only • Device assignment can be tedious • Filtering results somewhat sporadic |
Typical Price: $72 Buy From Amazon
Introduction
5/13/16 – Product does track website visits
Determining and enforcing age-appropriate and scheduled Internet access for your children can prove to be a difficult challenge for parents. Which categories of content should they be able to access? How much Internet time per day should they have? How can you ensure they aren’t using the Internet after bedtime?
Many routers have some very basic parental controls built-in. You can schedule when to disable Wi-Fi, and you might be able to block or allow specific sites. But often those rules apply to everyone on your network. DNS-based content filtering offered by companies such as OpenDNS can provide category filtering, but don’t provide general access management.
Circle, a network appliance designed to help you manage access to the Internet on your home network, started its life as a Kickstarter project. Unfortunately, it didn’t reach its funding goal. But the product surfaced late last year as Circle With Disney. Circle’s debut press release explained the partnership:
“…Additionally, through a licensing partnership with Disney, Circle also provides families with Disney entertainment that parents trust and children love. Circle with Disney will deliver a curated selection of Disney content including videos, blogs, gifs, emojis, music, games, characters and lots more through a unique experience called MyCircle.”
Circle is designed to work with virtually all routers and connects to your network via Wi-Fi or Ethernet. According to the company, Circle’s”secret sauce” is “ARP Spoofing“. According to Wikipedia :
“…ARP spoofing, ARP cache poisoning, or ARP poison routing, is a technique by which an attacker sends (spoofed) Address Resolution Protocol (ARP) messages onto a local area network. Generally, the aim is to associate the attacker’s MAC address with the IP address of another host, such as the default gateway, causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing may allow an attacker to intercept data frames on a network, modify the traffic, or stop all traffic. Often the attack is used as an opening for other attacks, such as denial of service, man in the middle, or session hijacking attacks. ARP Spoofing is more often associated with Black Hat Hackers who use the technique for “Man-in-the-middle” attacks.”
The image below, courtesy of Wikipedia.org, shows a typical router and one that has been compromised by a “Malicious User”. However, the Circle uses ARP spoofing not for a malicious purpose, but rather to monitor all traffic on your local network without requiring any special network configuration on your part.
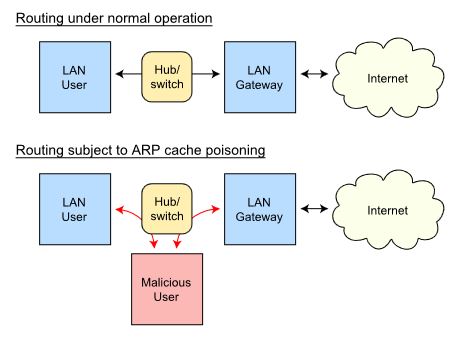
ARP Spoofing diagram (courtesy Wikipedia)
Circle has a “How it works” document on their site that is well worth reading. It demystifies ARP Spoofing, presenting it in terms more friendly to consumers than most technical documents. One of its introductory paragraphs contains all of the information many people will need.
“When Circle is configured in a home, it identifies the router and begins to pose as the gateway to the other devices on the network. This allows Circle to receive traffic for the Internet and to inspect it. Any traffic that Circle allows is sent on to the router, which in turn sends it on the Internet.”
The white plastic case for the Circle is a perfect 3.25″ cube with rounded edges. With the clean lines and white case, at first glance, it looks like it might be an Apple product. It’s a very simple design, so callouts almost aren’t necessary but I’ve included them anyway. The Circle has a power button, a single LED indicator and a USB Mini plug for power. The Ethernet port is covered by a plastic tab and has built-in link and activity indicators. The Circle ships with a USB power cable, 2.0A power supply and Ethernet cable.
Circle Callouts
Setup
Setup is a fairly simple process, but you’ll probably need about 10-15 minutes to set it up and configure your first user profile. Like many new networking products, your configure Circle with an app, not a web browser. Note you must have an iOS device running iOS 8.0 or later in order to configure the Circle.
Once you launch the Circle app, it walks you through the entire process. Here are the basic steps:
- Attach to the default “Circle-XXXX” Wi-Fi network and enter the default password “mycircle”
- When prompted select your home network from the list of Wi-Fi networks discovered and enter its network key – this is the network that the Circle will be managing.
- When prompted, connect to your home network.
- Setup an account with Circle. This requires your name and an email address. You must also provide a phone number capable of receiving a text message. Circle will send you a four digit code that you enter to validate account creation.
- Create the first user profile.
Note there is no submit-your-credit-card step. Circle is free of ongoing subscription fees.
During the setup process, Circle will identify all of the devices on your network. For my network, I have quite a few Smart Home devices running and Circle was smart enough to recognize them and automatically place them in an “Unmanaged” category that won’t be managed by the Circle. Other devices that should go into the unmanaged category would be network printers, NASes, your router, any VOIP phone devices, streaming devices and wireless access points.
As Circle discovers devices on your network, it makes an educated guess about the vendor of the product based on its MAC address.But you can rename any device so a name that’s more easily recognized than just the vendor’s name.
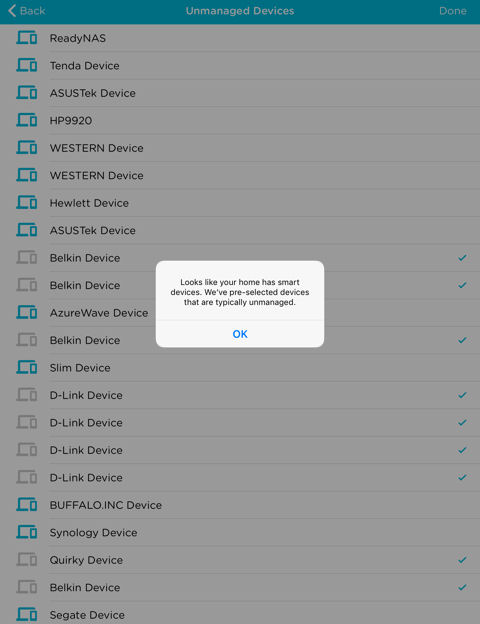
Unmanaged devices
On a large network, identifying the actual hosts to be managed (such as “Samsung S7” in the screenshot below) can be a time-consuming task. I’ve documented all the MAC, IP addresses and associated host names for all the devices on my network, so my renaming task went quickly. If you’re not as organized, Circle has a web page you can visit from each device (assuming it has a web browser) to see how Circle has named it.
As you create a user profile, you can choose from one of four preset filter levels: Pre-K; Kid; Teen; and Adult. Each filter level has age-appropriate, pre-configured platforms and categories that you can edit. The composite screenshot below shows the category and filters for the “Kid” profile. Note that each profile level has its own color scheme that you’ll see repeated in other screenshots. You can adjust the categories and filters as you want, then save it. In addition, you can also add specific websites you want to block.
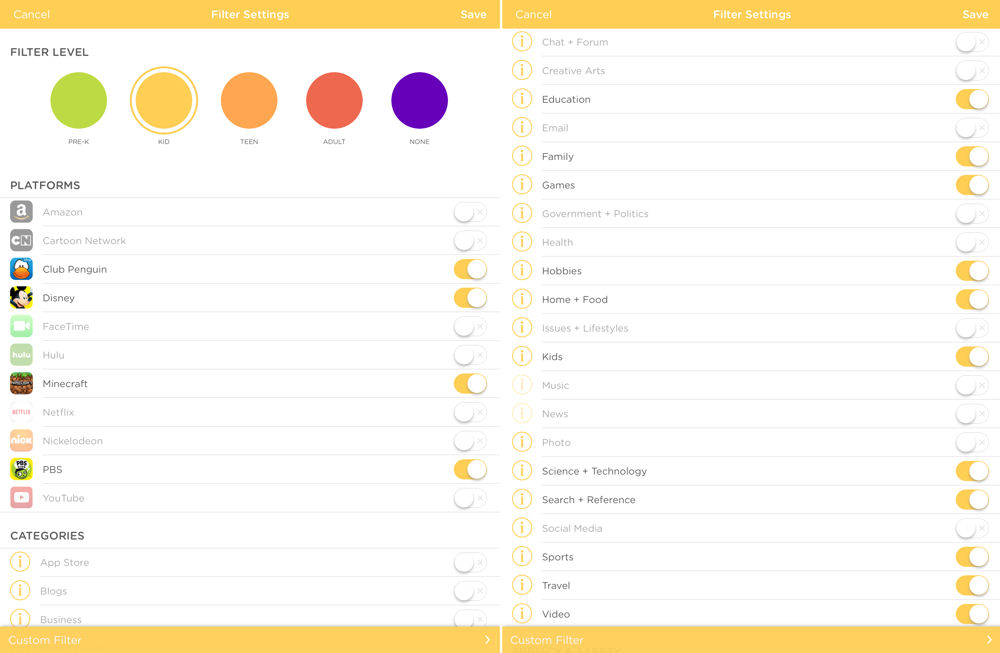
Circle Kid profile filter configuration
In addition to assigning a filter level to a user profile, you can also set Internet use time limits for platforms or categories. The platforms and categories are the same for all filter levels. The screenshot below shows that for profile “Sue” assigned the “Teen” filter level, time limits have been set for various applications. Sue is allowed four hours of internet time per day and time limits are imposed for the aapplications shown. Each time restriction is individually configurable. For applications and categories without restrictions, the default is the limit of allowed Internet access.
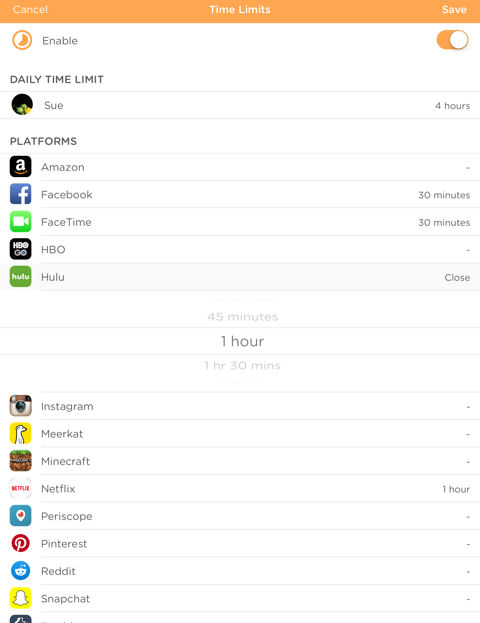
Time limits set for Profile “Sue”
What’s one sure way to get your kids to bed? Turn off their Internet access. For each user profile, you can choose to enable/disable the BedTime feature. Once bedtime arrives, Internet access is shut off for that user profile. As with any of the settings, you can enable/disable them, change time restrictions and bedtime settings. Just be sure to click Save.
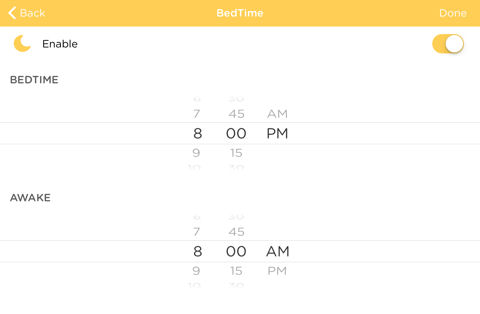
Set Bedtime and Wake up time
In addition to the four preset profiles, there’s also a default “Home” profile. All new devices discovered on the network are automatically added into this profile using the application, category, time restrictions and BedTime settings you define.
Hands On
For testing purposes, I set up multiple profiles. I created a “Kid” profile, a “Teen” profile and two “Adult” profiles. The rest of the devices on my network were either in the “Home” profile or were unmanaged. I did most of my testing using the Kid profile, since it was the one with the most restrictions. However, I used the “Sue” user profile with Teen filtering for most of the afternoon and didn’t really run into restrictions unless I specifically went to sites that were excluded in the Teen Filter Levels.
The screenshot below shows the landing page for the application. It also shows one of the problems with the product. As you set up a profile, you can associate a photo from either the camera or from your iOS device’s camera roll. I decided to use photos from my camera roll. Unfortunately, the resize/reposition feature didn’t appear to work and what appears in the “circle” icon for each user was a portion of the selected photo from the upper left corner.
If you leave the image blank, it uses the first letter of the profile name. If you take a photo using the camera on your iOS device, however, the image appears properly as long as you’ve centered it when you take the photo. I contacted Circle Technical Support and they confirmed the bug and reported it to their development team.
Each user profile is arranged in, yup, you guessed it, a circle that surrounds the Home profile icon. The Menu icon in the upper left corner lets you add profiles, view / manage devices and perform administrative tasks such as rebooting, disabling and resetting the Circle. The icon in the upper right corner shows all devices on the network. The pause button at the bottom of the screen will temporarily block internet access for all managed devices. A similar pause button appears on each individual’s profile page and on each device page.
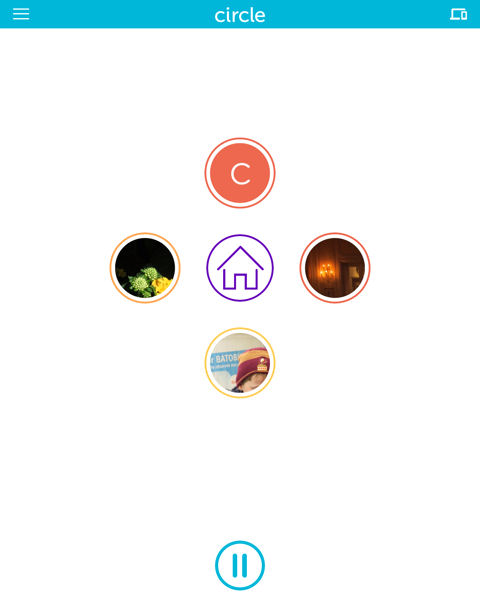
Circle Landing Page
When you press the Pause icon for a user profile, a specific device or the entire network, the user will see this message after their next browser request.
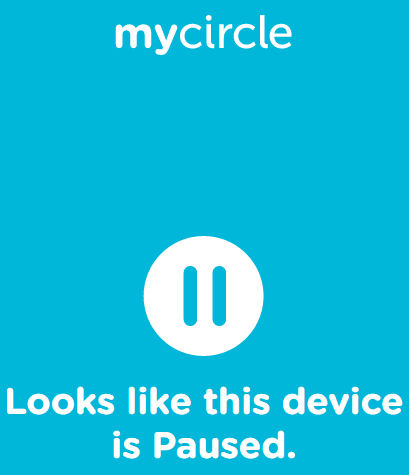
Circle – Paused screen
The composite screenshot below shows the top-level screen and the Insight for the “Kid” profile David. As you can see from the time stamp at the top of the screen, it’s early in the morning and David has used no internet time today. Currently, David has one device assigned to him, the Filter level is set to “Kid” and Time Limits and BedTime is currently disabled. Clicking on any menu item lets you edit the current settings.
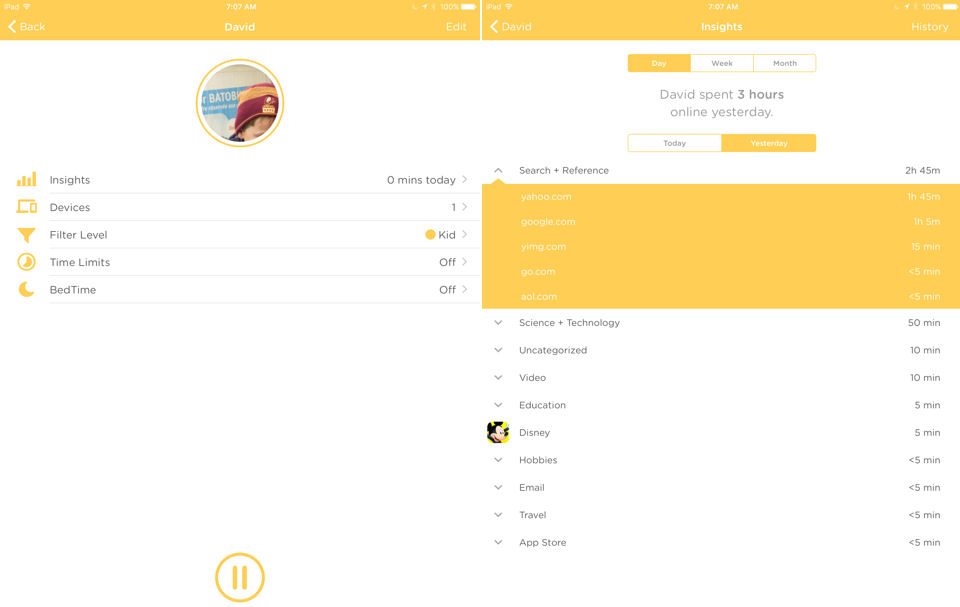
Circle – Profile landing and Insight pages for “Kid”
The image on the right shows the detail for the Insights menu. The Circle lets you view usage for either today or yesterday. In addition, you can view totals for the day, week or month. Time is totaled by category. I’m not sure how the total time is calculated, however. Yesterday, “David” spent three hours on the Internet, but the sum of the categories appears to add up to more than three hours. The discrepancy may be due to how Circle aggregates time for web sessions. Actually, yesterday, I had enforced a three-hour time limit on “David” and when the limit was reached, he was notified and Internet access was terminated.
It’s important to note that you can assign more than one device to a user profile. In some of my testing, I had multiple devices assigned to the “David” profile. Usage for both devices was aggregated and shown in the Insights summary. However, usage between multiple devices was not broken out separately.
Enforcement
Of course, the whole idea behind Circle is to manage the devices and enforce the policies that you’ve created for your family. To test this, I tried accessing sites using various profiles, and also checked enforcement of time limits and bedtime hours. To test, I used both a desktop computer using Chrome as well as a Samsung Android tablet. For some sites, I tested both the browser version and corresponding app on the tablet. The table below summarizes the results for the “Kid” profile – the most restrictive filter that I set up.
| App/Category | Test search | Allowed | Result – Samsung Tablet | Result – Desktop | Notes – Tablet | Notes – Desktop |
|---|---|---|---|---|---|---|
| Amazon – browser | www.amaon.com | n | filtered page | filtered page | ||
| Business (linked in) | www.linkedin.com | n | filtered page | filtered page | ||
| Disney | www.disney.com | y | allowed | allowed | ||
| www.gmail.com | n | blocked | filtered page | Certificate error | Certificate Error | |
| www.mail.yahoo.com | n | blocked | blocked | Certificate error | Certificate Error | |
| Facebook app | N/A | n | blocked | N/A | can’t connect | N/A |
| Facebook web | www.facebook.com | n | blocked | blocked | Certificate Error | Certificate Error |
| Government and Politics | secaucusnj.gov | n | allowed | allowed | ||
| Government and Politics | www.wh.com | n | blocked | blocked | Certificate Error | Certificate Error |
| Government and Politics | bluenationreview.com | n | filtered page | filtered page | ||
| Health | www.webmd.com | n | filtered page | filtered page | ||
| Hulu – app | N/A | n | blocked | blocked | SSL Error 143 | N/A |
| Hulu – browser | www.hulu.com | n | filtered page | filtered page | ||
| News | www.abcnews.com | n | filtered page | filtered page | ||
| News | www.yahoo.com | n | allowed | allowed | ||
| News | www.msnbc.com | n | filtered page | filtered page | ||
| News – USATODAY app | N/A | n | allowed | N/A | N/A | |
| News – USATODAY | www.usatoday.com | n | filtered page | filtered page | ||
| News AOL browser | www.aol.com | n | Allowed | Allowed | ||
| Nickelodeon | www.nick.com | n | filtered page | filtered page | ||
| Photo | images.google.com | n | allowed | allowed | ||
| Play Store | N/A | n | blocked | N/A | check connection, try again | N/A |
| Sports | www.espn.com | n | filtered page | filtered page | ||
| YouTube App | N/A | n | blocked | N/A | check network connection | |
| YouTube web | www.youtube.com | n | filtered page | blocked | Certificate error | |
| Searches | ||||||
| creative arts | watercolor painting | n | allowed | allowed | results shown, links worked | results shown, links worked |
| Google Image Search | boobs | n | allowed | allowed | found images | found images |
| Google Search | boobs | n | blocked | blocked | results shown, links blocked | results shown, links blocked |
| issues + lifestyles (google search) | LGBT | n | allowed/filtered | blocked | some links allowed – some got filter page | results shown, links blocked |
Table 1: Test results for user profile “David” using Kid level filtering
The “Allowed” column shows whether or not I expected the site/app to be blocked. The “filtered page” result indicates that the site was intercepted, and a Circle web page was displayed showing that the site had been filtered. The “filter page” displayed varies depending on the filter level. Each filter page is a customized page for the individual user and shows age-appropriate Disney content as well as usage statistics, time remaining statistics, and, if enabled, time remaining until bedtime.
Initially, I had some inconsistent results. Sites I expected to be blocked were not. I contacted Technical Support and they recommended rebooting both the router as well as the Circle device. This undoubtedly cleared the ARP cache in both devices. Following the reboot, in most cases, the sites were blocked as expected. There were exceptions, however.
For example, I had expected Yahoo and AOL to be blocked because their landing pages are primarily news portals. However, both sites were allowed. Similarly, I had expected images.google.com to be blocked because the Photo filter had been applied to the profile. By drilling down into the usage stats provided by Insight, I discovered that AOL, Yahoo and images.google.com were all permitted because they fell under the Search & Reference filter, which had been permitted by the profile. I disabled that category filter and retested, and those sites were blocked.
The composite screenshot below shows the Circle filtered pages shown for the “Kid” and “Teen” users. The filtered page, in addition to notifying the user that content is filtered, is also where the Disney content is displayed. The filtered page for each category includes an extensive scrollable list of age-appropriate Disney content. The Disney content actually is hosted at filter.meetcircle.com, so is frequently updated. But if you try to hit the filter.meetcircle.com/teen URL shown in the screenshot and don’t have a Circle, you’ll get a page telling you so. No free Disney content for you!
The filtered pages follow the user interface color scheme, using mustard yellow for "Kid" and orange for "Teen". The “Kid” profile includes time limits, BedTime countdown timer and Time online summary. The “Teen” profile doesn’t have time or bedtime restrictions, but limits have been set for various apps.
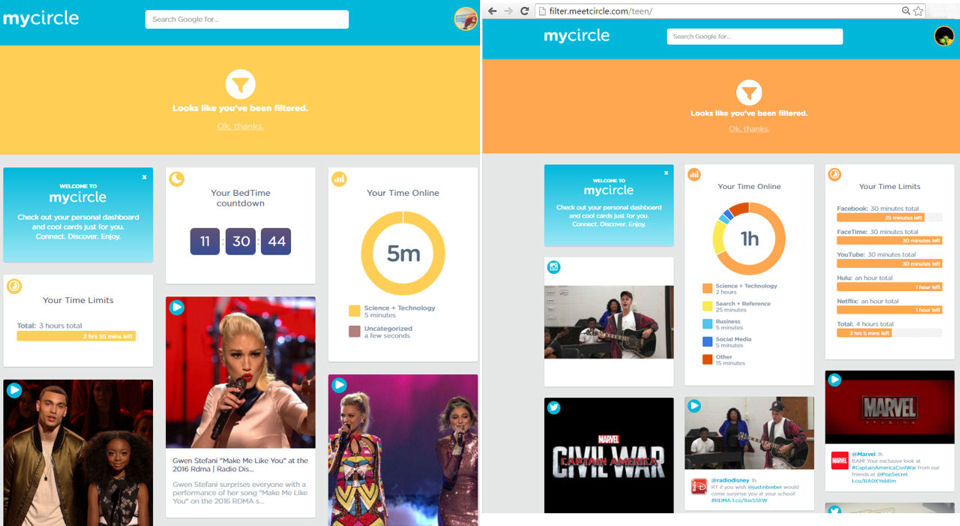
Circle Filter Page for “Kid” and “Teen” users
Access to a number of sites was blocked, but the Circle filtered page didn’t appear. Instead, Chrome intercepted the page and warned “Attackers might be trying to steal your information” or that there was an SSL error. In these cases, the browser had detected a certificate mismatch problem between the SSL certificate on the site and the Circle device.
The image below shows the error message on my desktop when I attempted to connect to Facebook with Chrome. Actually, that’s good news, because it indicates that the browser had protected you from a suspected “man in the middle” attack. As noted in the introduction, ARP spoofing is how Circle works.
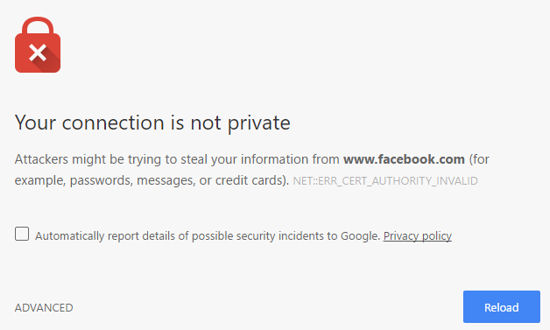
Chrome warning about a certificate problem
Outlook on my desktop also complained about the SSL certificate mismatch that allowed me to check out the suspect certificate. Here’s what it showed:
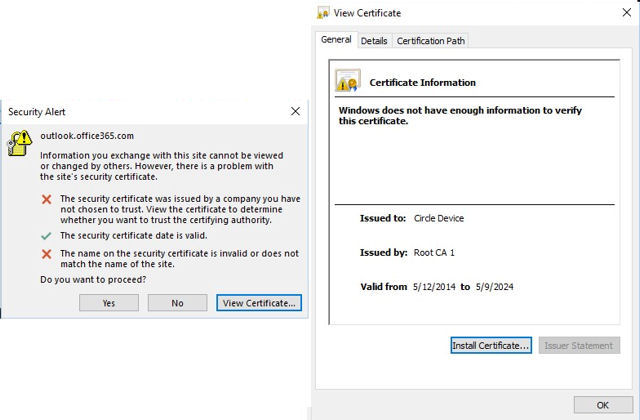
Outlook Security Warning and Circle Certificate
Circle enforced both the daily and BedTime limits set. Notification is done via a simple filter page shown below.

Circle Time Limit and BedTime Enforcement
Closing Thoughts
At first, I was a bit skeptical about installing an ARP-spoofing device on my network. But it appeared to make the discovery and setup of Circle very easy. No network expertise was required beyond connecting Circle to my Wi-Fi network, entering a password and following the steps in the setup wizard.
I was a bit disappointed that I couldn’t use my Camera Roll photos for profile icons, but I’m sure that’s a bug Circle will quickly eradicate. I was also a bit concerned that the total time shown in the Insight summary didn’t seem to sum up to the total allowed time. That’s something that still seems to need a bit of work. But the product was effective in blocking applications and categories – once I understood what was included in the filter categories.
Other software parental control applications are able to more granularly control content, but they require installation on each device. And, they aren’t centrally managed, nor do they all work across the spectrum of computing devices families are likely to use. Since Circle operates at Layer 2, it’s compatible with virtually all devices. One shortcoming noted is that Circle does not log failed (blocked) access attempts. Sometimes knowing what your child is trying to access is more valuable than knowing what they did access.
5/13/16 update
A helpful reader pointed out that Circle does track visited and blocked websites.
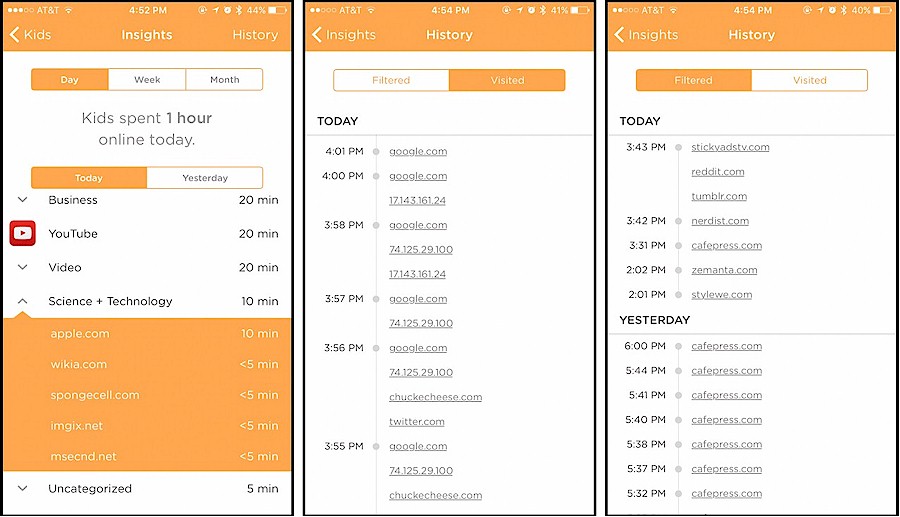
Insights – Web History
Circle groups history into categories and then sites. You can view activity today, this week, this month. When you click on any of those, you can look at the previous one (so yesterday, last week and last month). You can also view visited and blocked sites.
Circle currently works on only a single local network segment because it relies on Layer 2 ARP protocol. In fact, the FAQs tell you not to attach Circle to your guest network, as devices on that network are the only ones that you’d be able to manage. But Circle is also promoting Circle Go, which will bring Circle’s features to any network, including cellular networks. Circle Go will be a subscription product and come in the form of an iOS app "with Android support to follow". The product page says "Coming Spring", but doesn’t say which year.
No one parental control tool for Internet access is perfect, just as no parental Internet policy is perfect. But this hardware-based easy-to-set up device provides a lot of control. And for $99, it’s a good tool to have in your parental control toolbox. If you decide to buy Circle, I recommend you spend some time testing the profiles you set up for your children to ensure they are filtering content that’s in line with your view of age-appropriateness. ![]()

