Introduction
| At a Glance | |
|---|---|
| Product | Zyxel Zywall 2 Plus (K28388) |
| Summary | Zippy IPsec VPN endpoint router supporting two VPN IPsec tunnels and lots of options for use in multi-router networks |
| Pros | • Extensive routing and firewall configuration features • Built-in 32 user authentication • Plenty of routing and VPN tunnel throughput • Lots of documentation |
| Cons | • Easy things aren’t easy • Documentation lacks useful examples • No bundled IPsec client • Only two tunnels |

I’ve been getting requests lately for recommendations on routers that include VPN endpoints. But when I checked my past reviews, I found that the last time I looked at one of these products was back in 2004. Yikes! So one of my (early) new year’s resolutions is to get back to reviewing wired routers, starting with this review.
Zyxel’s Zywall 2 and 2 Plus are the entry-level products in Zyxel’s Security Appliance portfolio. Both are four port 10/100 routers with SPI firewalls and IPsec endpoints capable of supporting two tunnels, with feature sets supporting use in larger networks behind multiple layers of routers. The key differences between the two products are summarized in Table 1 below.
| Spec | Zywall 2 Plus | Zywall 2 |
|---|---|---|
| CPU | Intel IxP 422 266Mhz | Samsung 2500 166Mhz |
| Flash/SDRAM | 8 MB / 32 MB | 2 MB / 16 MB |
| Firewall performance | 24 Mbps | 12 Mbps |
| VPN performance | 24 Mbps | 2.2 Mbps |
| Key Features | Zywall 2 feature set plus: – Bandwidth Management – Bridge mode – VPN High Availability (HA) |
– Firewall – IPsec VPN endpoint – Content Filtering – Dial Backup – 4-port 10/100 switch |
Table 1: Zywall 2 and 2 Plus comparison
The router has the footprint of a typical plastic DVD box and stands about two such boxes high. The enclosure is plastic and there are two screw slots on the bottom cover for wall mounting. Figure 1 shows the complement of LEDs on the front panel, which are bright and viewable from a wide angle.
Figure 1 : Front panel
Figure 2 shows the available ports, which include two RJ45 sockets supporting serial port connections to a console device and analog modem (remember those?) for dialup failover.
Figure 2: Rear panel
Internal Details
Figure 3 is a photo of the 2 Plus’ board, which is built around a 266MHz Intel IXP422 CPU with 32MB of SDRAM and 8MB of FLASH memory. A Marvell Link Street 88E6060 6 port Fast Ethernet Switch rounds out the essential components.
Figure 3: The 2plus board (click image to enlarge)
Setup and Configuration – LAN
In addition to its IPsec endpoint, the 2 plus has a lot more routing and firewall features than your typical consumer router. IT folks who have wrassled with low end Cisco, Juniper and other "pro" level routers aimed at the small-biz crowd will probably feel right at home with the 2 plus’ way of doing things. But others who have drawn the short straw and end up saddled with supporting the company (or home) network on an occasional basis may find the product’s user interface a bit opaque at times.
The good news is that Zyxel provides more documentation than you typically find with consumer routers. The bad news is that you’ll probably need it, and might not find much help when you turn to it. The 613 page User Guide is long on the what and where, but often comes up short on the how and why. And even when examples are given, they often lack key information or require multiple careful readings to make sense of them.
That being said, initial setup isn’t too bad. The 2 plus comes set to a default IP of 192.168.1.1 and its DHCP server enabled, so getting connected and into the admin screen is relatively easy. The login screen has the default password automatically entered, so all you need to do is click the Login button. You then get sent to a screen that prompts you to change the default password, which you can bypass with a click on the Ignore button. But you’ll be nagged upon each login until you change the password, so you might as well get it out of the way.
The next screen will prompt you to create a custom security certificate (for IPsec tunnel) based on the router’s MAC address to replace the generic factory default certificate. This is not the place to accept a factory default, so another click takes care of this screen and takes you to the Home screen (Figure 4) that holds some useful info.
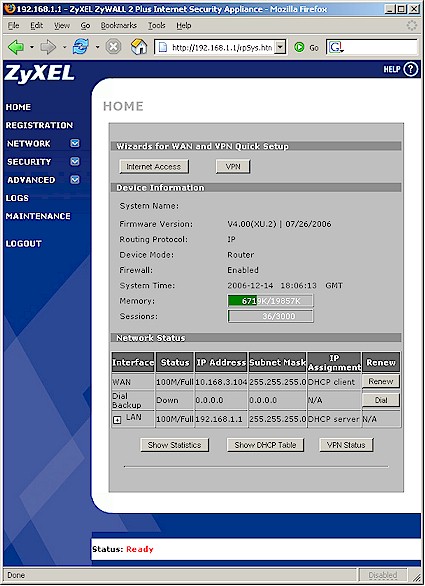
Figure 4: Home screen
The Internet Access Wizard isn’t very wizzy and just takes you to a screen where you manually select Ethernet , PPPoE or PPTP "Encapsulation", i.e. Internet connection type and either static or dynamic IP address assignment for the WAN IP. Other vendors’ wizards (such as Netgear) handle this sort of thing automatically, so Zyxel’s manual method may feel a bit retro. Another weakness of this "wizard" is that it doesn’t expose all of the configuration options for each Encapsulation method (more later). But given the target audience for this product, the manual "wizard" will probably better satisfy most IT geeks.
The VPN Wizard button is a bit more useful, but I’ll save that for later. The Show Statistics, Show DHCP Table and VPN Status buttons at the bottom of the screen pop up windows populated with the named information.
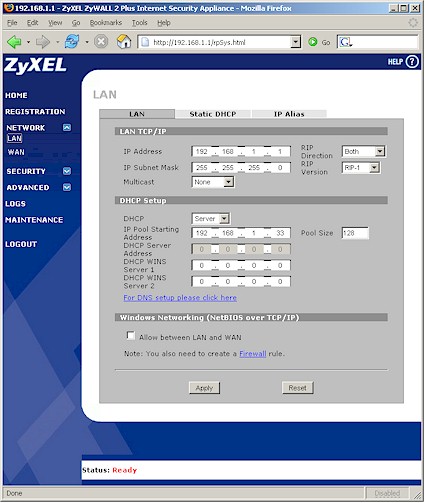
The LAN screen in Figure 5 shows the controls available, some of which bear explanation. The Static DHCP tab is where you can assign IP addresses by MAC address, which is handy for things you don’t want moving around like NASes, printers, servers, etc. An easier way to assign IPs, however, is to just check the box beside a device in the Show DHCP Table screen available from the Home page. Note that you can’t set the DHCP lease time, nor can you force disconnection of devices. RIP-1, 2B and 2M dynamic routing protocols are supported for inbound, outbound and packets traveling in both directions.
Figure 5: LAN screen (click image to enlarge)
I have to confess that I didn’t understand the IP Alias feature (Figure 6) and also didn’t find much help in the feature’s single page explanation in the User Guide. It appears to be a sort of VLAN-like capability, but with LAN segment-to-segment data flow controlled by the 2 plus’ firewall rules.
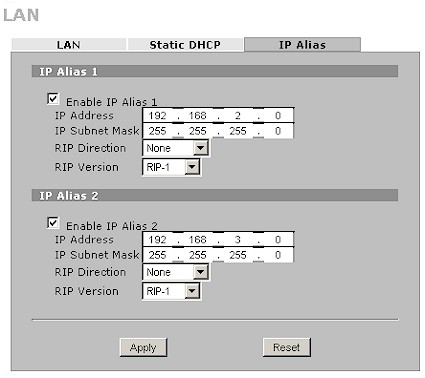
Figure 6: IP Alias screen
Setup and Configuration – WAN
The Network > WAN screen again presents numerous options that won’t be familar to those who aren’t IT pros. The Route tab lets you set the Routing Priority (metric) for the WAN, Traffic Redirection and Dialup back up features. It also contains checkboxes to allow Windows Networking (NetBIOS over TCP/IP) to trigger a dialup session and to allow networking traffic to flow between WAN and LAN. The latter seems an odd choice for a checkbox here, given that it is more a firewall function.
As mentioned earlier, the WAN screen in Figure 7 provides more WAN configuration options than the Internet Access Wizard. Except for the Service Type dropdown, most of the options you see are also available with PPPoE and PPTP connections. PPPoE and PPTP setup options include PAP/CHAP, PAP and CHAP authentication and connection nail-up, but an MTU adjustment control was nowhere to be found.
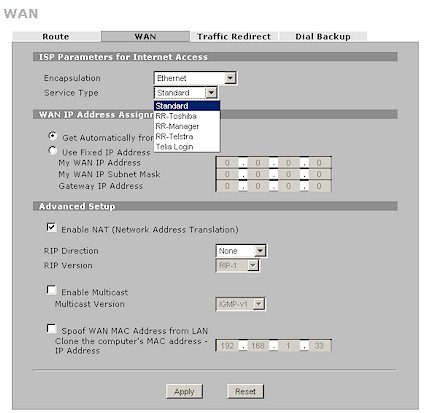
Figure 7: WAN screen
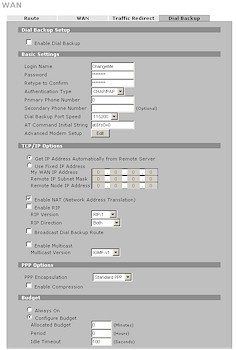
The Traffic Redirect and Dial Backup tabs support failover features that provide two backup connection options should the normal Internet connection path fail. Traffic Redirect pings a WAN IP address that you enter (the time between pings and response timeout are programmable) and switches the 2 Plus’ gateway to the IP address of a backup gateway that you enter. Should that connection then fail, you can configure a dialup backup to kick in using the controls in Figure 8. The 2 plus supplies the serial port (via an RJ45 connector); you supply the modem. I didn’t test either of these options.
Figure 8: Dialup backup screen (click image to enlarge)
Firewall
The 2 Plus has a rule-based full-featured SPI firewall that is configured separately from the router’s NAT features. And when I say separately, I mean it, since the 2 Plus does not automatically create corresponding firewall rules for things as simple as when you forward a port in the NAT section interface.
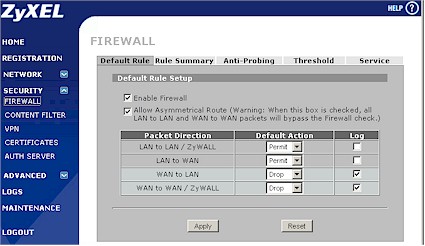
The only nod to user-friendliness here are notes on some of the NAT section pages that say you may need to create a firewall rule. This is another place where IT geeks will be comfortable with the 2 plus’ way of doing things but occasional admins will just find it annoying and/or frustrating. Figure 9 is a shot of the Firewall Default Rule screen, where you can see the firewall options.
Figure 9: Firewall Default Rule screen (click image to enlarge)
The LAN to LAN / ZyWall option is used in conjunction with the IP Alias feature mentioned earlier, while the WAN to WAN / ZyWall option handles IPsec tunnel firewalling. WAN to LAN is used if you need finer control over inbound packets than basic NAT firewalling and port forwarding gives you. Finally, the LAN to WAN rules are where you set rules for what most routers refer to as Port or Application filtering.
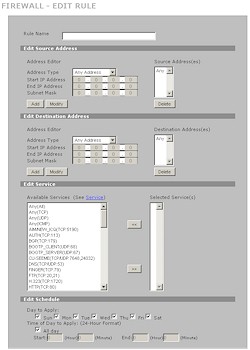
Figure 10 shows the Edit Rule screen used for creating and editing rules. Note the simple day / time scheduling at the bottom of the screen. Not visible are other options for logging or sending an alert when a rule is matched and Permit, Deny and Drop options for rule action. Of course, if you don’t see the service you want from the default pick list, you can use the Service tab to add a new one.
Figure 10: Firewall Edit Rule screen (click image to enlarge)
The Service edit screen lets you name the service and enter its port range as well as choose from TCP, UDP, TCP/UDP, ICMP and Custom (you enter the protocol number) protocols. Other Firewall section tabs let you disable DoS attack protection on the WAN and LAN interfaces, set DoS session thresholds and specify the action taken when the TCP Maximum Incomplete threshold is tripped. Ping response is controlled in the Anti-Probing section separately for LAN and WAN interfaces.
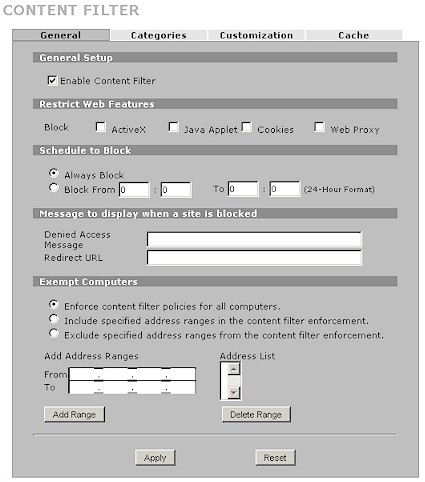
Moving on to Content Filtering, Figure 11 shows the basic options. Notable are the ability to specify a "blocked" message and redirect URL. You can also specify clients that are "exempt" from the content filter. Note that this exemption is by IP and not MAC address, so you would best assign static IPs (or reserve them using the LAN > Static DHCP feature) to any clients that you add to this list.
Figure 11: Content Filter General screen
The Categories screen (Figure 12) works in conjunction to an optional subscription based filtering service OEM’d from Bluecoat. You get a one month trial subscription with the 2 plus that you activate in the Registration page so that you can check things out.
Figure 12: Content Filter Category screen
If your filtering needs are simpler (or budget is tighter), you can use the Customization tab to create a list of "Trusted" and "Forbidden" web sites as well as keyword URL filters. I did a quick check of the keyword URL filtering and found it smart enough to block the IP address of a blocked site. Also of note is the Cache tab that provides control over how long (1-720 hours) a record of attempted visits to sites in the "Trusted" and "Forbidden" lists are kept. You also view and flush the list here.
VPN
The star of the 2 Plus show, however, is its IPsec VPN capability. But while its throughput lives up to Zyxel’s claims, the 2 Plus does not greatly advance the state of the art in terms of ease of VPN setup or usefulness of its documentation. I have to admit, however, that the VPN Wizard was helpful in getting my test router-to-router tunnel set up, mostly because it presented screens containing all the settings that needed to be configured to get a basic tunnel going and had online help that could be popped up for each screen.
But neither the wizard nor the online help may be bullet-proof enough to get an IPsec tunnel virgin through the process on the first try. For example, I couldn’t find a warning about one of the most common mistakes—the failure to make sure that the LANs at each end of the tunnel use different subnets—in the wizard, online help, User Guide or Quick Start.
I also found a subtle error that used the tem "remote" instead of "local" in the online help that, if followed, would never get a successful tunnel up. But since I’ve set up a successful tunnel or two, I was able to get through the wizard and have a working router-to-router tunnel—after, of course, changing the LAN subnet of one of the routers to 192.168.0.X from its default of 192.168.1.X.
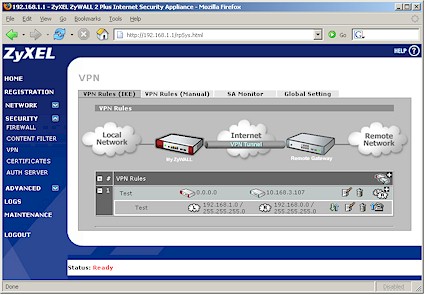
The other way to set up a tunnel is to start at the Security > VPN screen and create your Gateway and Network policies from there. Figure 13 shows the rules established by my VPN Wizard session, with the network policy associated with its gateway policy expanded using the "+" icon in the left column. Clicking on the edit icons for each policy brings up its associated edit screen.
Figure 13: VPN Rules IKE screen (click image to enlarge)
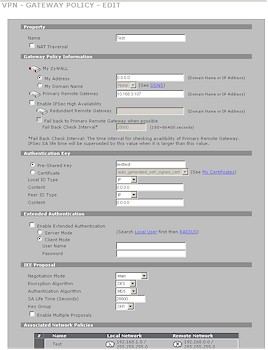
Figure 14 shows the Gateway policy edit screen with its extensive options. Of special note are the abilities to enable a redundant remote gateway (the "VPN High Availability (HA)" feature), use a certificate for authentication and the extended authentication options using the built-in authentication database or external RADIUS server. Note also that the gateway policy can handle a dynamic IP address on the local gateway, but the remote must have either a fixed IP address or domain name.
Figure 14: VPN Gateway policy screen (click image to enlarge)
VPN – more
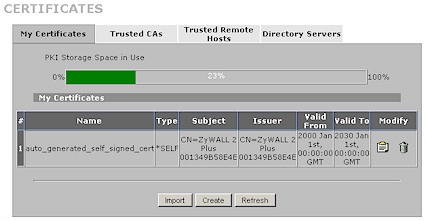
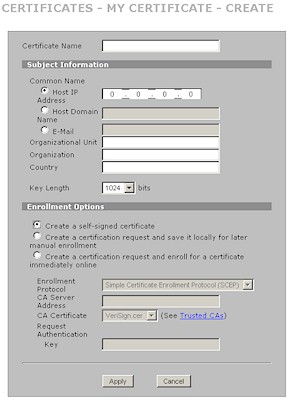
I used a pretty weak pre-shared key to set up my test tunnel, which, after wresting with an errant setting (more shortly), worked without a problem. I also made an unsuccessful attempt at certificate-based authentication. The failure was likely caused by my being pressed for time and not working my way through all the steps required to successfully exchange certificates between the two routers. The Certificates section (Figure 15) is quite extensive and include tabs for setting up certificates, Trusted CAs (Certificate Authorities), Trusted Remote Hosts and Directory Servers that hold certificate lists.
Figure 15: Certificates screen (click image to enlarge)
Figure 16 shows the screen for creating a certificate.
Figure 16: Certificate creation screen (click image to enlarge)
Once you have your authentication configured, you need to set up a Network Policy for the tunnel. The controls for that are shown in Figure 17.
Figure 17: VPN Network policy screen (click image to enlarge)
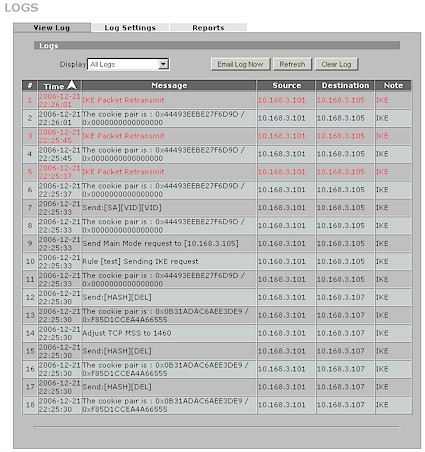
Once you get the rules entered, the usual fun of trying to get the tunnel up and running starts. My first attempt was thwarted by a firewall rule that I had entered during my throughput testing. As usual the information in the logs was too cryptic to be useful (Figure 18 shows an example of a failed tunnel setup) and it took a Zyxel factory engineer examing my router’s configuration dump to get me sorted out. It’s interesting to note that a successful tunnel setup gets rewarded with a "Tunnel built successfully" entry in the log, but a failed tunnel attempt doesn’t get a corresponding failure message.
Figure 18: Log of IPsec tunnel setup failure (click image to enlarge)
After I cleared the problem rule, I was able to get a tunnel up using a pre-shared key, the VPN "Wizard" and accepting most of the defaults for IKE and IPsec proposals. The SA Monitor screen is where you can see the tunnels that are up and running (would be nice if some sort of indication were provided in the Home page, too). The Global Setting tab holds input and output idle timer settings as well as a gateway domain name update timer and TCP Maximum Segment Size (MSS) controls. The latter defaults to Auto, with Off and User-defined options.
In all, I’ve had more painful IPsec setup experiences. But as I said at the beginning of this section, the 2 Plus doesn’t advance the state of the art in IPsec user friendliness. It should also be noted that Zyxel leaves you on your own to select an IPsec client to use with PCs that need to connect to it securely.
NAT Features
In addition to the Firewall, Content Filtering and VPN services, the 2 Plus has many more NAT routing functions than found in less expensive routers. First, you can specify the number of maximum concurrent sessions per host. The default is 2048 out of 3000 total maximum sessions. You can also disable NAT entirely.
If you have multiple IP addresses from your ISP, the 2 Plus can help you get the most out of them. Supported NAT Mapping types in the Address Mapping screen include One-to-One, Many-to-One, Many-to-Many Overload, Many One-to-One and Server.
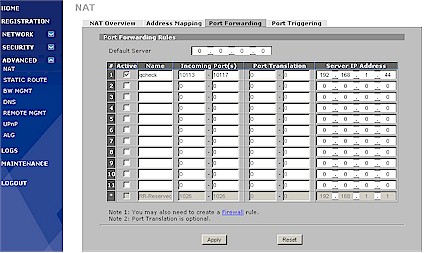
Those with single WAN IP addresses will bypass the Address Mapping screen and use the Port Forwarding rules shown in Figure 19. (The "Default Server" entry at the top of the screenshot is same as the "DMZ" function on other NAT routers.) You can also specify twelve Port Triggering rules using port ranges on the incoming and trigger ports.
Figure 19: NAT Port Forwarding screen (click image to enlarge)
Other methods of helping applications to deal with the 2 plus’ NAT firewall include Universal Plug and Play (UPnP) and Application Layer Gateway (ALG) support. UPnP is disabled by default and has separage enables for allowing clients to make router configuration changes via UPnP and using UPnP NAT Traversal. I liked that the 2 plus displays any ports opened by any UPnP clients. The UPnP Ports screen also provides a checkbox that allows those rules to be stored in flash if you want to preserve them.
Options are a bit simpler for ALG and include checkboxes to enable handling for FTP, H.323 and SIP. You can also change the SIP ALG timeout from its default of 3600 seconds or disable it by entering 0.
The Static Route screen lets you specify up to eleven static routes including destination IP address, subnet mask, gateway IP and metric.
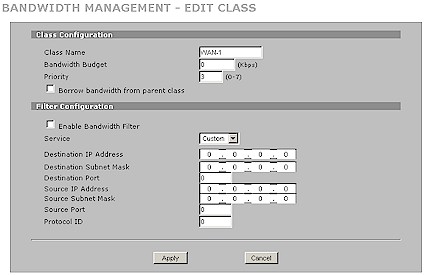
The Bandwidth Management section provides separate controls for both WAN to LAN and LAN to WAN traffic, using Fairness or Priority-based packet scheduling. You can set a maximum speed in each direction, define classes and subclasses of traffic (Figure 20) with eight priority levels. Statistics and Monitor screens let you see the effects of the rules you put in place. I usually like to check out how smoothly bandwidth is managed, but, unfortunately didn’t have time.
Figure 20: Bandwidth Management Class Edit screen (click image to enlarge)
Like many of the 2 plus’ features, its DNS handling is pretty flexible. You can enter Address Records and assign them to specific IP addresses if you like. Different DNS servers can be assigned for different domain zones, with choices of ISP, Public or Private DNS servers available. The 2 plus can cache both positive (default enabled) and negative DNS resolutions, with separately settable caching times (60 – 3600 seconds), display of cached entries and ability to flush the cache. Up to three DNS servers that are handed out by the 2 plus’ DHCP server can also be set. Wrapping up the DNS features is a built-in dynamic DNS client for dyndns.org that handles up to five domain names.
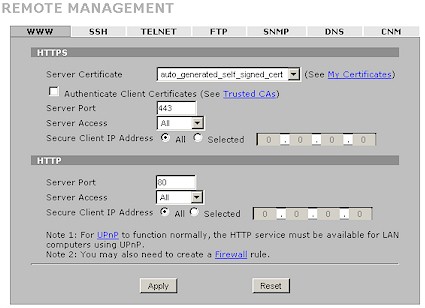
Figure 21 shows the plethora of options for 2 plus management. Note that HTTPs management is always enabled, but you are not auto-forwarded to it from a http login and need to specify https:// when you enter the 2 plus’ IP address into your browser. You can reach the command line interface via both SSH and Telnet, both of which are enabled by default to both LAN and WAN clients—not the most secure default configuration! You can limit access to LAN or WAN clients only, disable it entirely or limit SSH and Telnet access to a specific IP address. You can also change the operating port for each service.
Figure 21: Remote Mangement screen
If up and downloading router configurations and firmware updates via web browser isn’t your cup of tea, you can use FTP access, which also has the same access and port change options as SSH and Telnet.
If the 2 plus is going to be part of a larger network, its SNMPv1 support will come in handy, along with the ability to tweak its access and port options like the previous services. If you’re a ZyXEL shop and use its Vantage CNM Server as your network management system, the 2 plus can handle that too. Finally, if you need to control the interfaces that support DNS queries, you can do that on the DNS tab.
Other Features
Rounding out the 2 plus feature set are its Logging and other features. Logging is better than you normally get, with informative entries, source and destination IP addresses and notes. Port scans and other activity that are deemed attacks are entered in red with an "Attack" note. The log viewer can sort entries in ascending or descending time/date order with a click, as well as limit display to specific log categories.
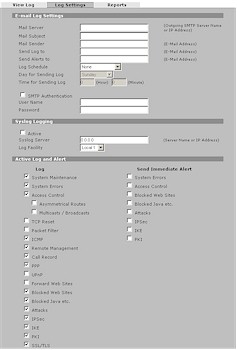
Logs can be emailed immediate, on a schedule, manually refreshed and cleared. Figure 22 shows that the log mailer supports SMTP authentication, but doesn’t have a test button to let you easily check whether the 2 plus’ emailer is going to work with your ISP’s SMTP server.
Figure 22: Log Settings screen (click image to enlarge)
Logging to a syslog server is supported and Zyxel throws in a copy of its Vantage Report application (Windows only) so that you can slice and dice logs to your heart’s content. The array of checkboxes at the bottom of Figure 21 provides control over what appears in the log and what is immediately sent in an email alert.
Not shown in the screenshot are the Log Consolidation controls that include an Active checkbox (checked by default) and period (1 to 600 seconds, default 10). According to the online help, this feature "merges logs with identical messages into one log". But I think that what really happens is that repeated log entries are merged, since I found some port scan attack entries that said "ports scan UDP (Repeated: 2)" in my log.
The Maintenance menu bats cleanup and holds the admin idle timeout value (0 to disable), password, date/time setup (including NTP server and time zone settings), firmware upload, configuration backup / restore / reset to factory defaults and restart. But oddly buried in the Device Mode tab is the ability to change the 2 Plus from its default router mode to being a bridge. This allows you to use its firewall and content management features between network segments without having to deal with a NAT router. The bridge mode supports 802.1w Rapid Spanning Tree Protocol to break network loops and prevent broadcast storms.
Performance and Closing Thoughts
I used IxChariot as described in this procedure to test routing and VPN tunnel throughput with firmware version V4.00(XU.2) | 07/26/2006 loaded in both routers. I don’t bother to check Response (ping) times any more since all current routers have times below the minimum measurement resolution of 1 msec.
I tried to test UDP streaming throughput, but was unable to get the test to complete in either direction and with or without the 2 plus’ firewall enabled. As I’ve noted before, Qcheck and IxChariot just don’t get along with some NAT routers that also have SPI firewalls features.
Table 2 shows that using the firewall exacts a significant price in performance. But with 30+ Mbps of throughput available even with the firewall kicked in, there is plenty left for most broadband connections.
| Test Description | Throughput – Firewall enabled (Mbps) |
Throughput – Firewall disabled (Mbps) |
|---|---|---|
| WAN – LAN | 34.1 | 54.9 |
| LAN – WAN | 35.6 | 55.5 |
| Firmware Version | V4.00(XU.2) | 07/26/2006 | |
Table 2: Routing throughput
Table 3 shows the results for tunnel throughput, which are close enough to Zyxel’s 24 Mbps spec and, once again, enough for most broadband connections. Note that I didn’t run this test with the firewall disabled.
| Test Description | Throughput – Firewall enabled (Mbps) |
|---|---|
| Local to Remote | 22.2 |
| Remote to Local | 21.9 |
| Firmware Version | V4.00(XU.2) | 07/26/2006 |
Table 3: IPsec tunnel throughput
So what’s the bottom line? Zyxel has packed a lot into the Zywall 2 plus, both in features and performance. But Zyxel has never distinguished itself with superior user interface design and the 2 plus continues that tradition. Yes, I know that the firewall has more bells and whistles than are found in products in this price class. But even the simplest NAT routers know how to throw the correct switches in their firewalls when a port is forwarded, so why can’t the 2 plus do it, too?
The other missing nod to user friendliness is in the IPsec features. Some other vendors throw in at least a IPsec client trial with appliances in this class. Zyxel would be wise to do the same, complete with default settings and/or setup wizard that can get a newbie connected with a minimum of fuss. And two tunnels is pretty miserly, considering that Netgear’s FVS124G supports 25 tunnels for about the same price and also has a 4 port gigabit switch and dual WAN ports.
All things considered, the Zyxel Zywall 2 plus is a good two-tunnel IPsec router with advanced firewall features. It should serve you well if you can live with its very small tunnel count and get your kicks from playing with rules-based firewalls.