Introduction
When you set out to choose a bank, you probably look at things like the accounts they offer, how much interest they pay, and how helpful they are to customers when you need to take out a loan or get a mortgage. But in the increasingly online world, in which Internet banking is becoming as commonplace as ATMs, perhaps it’s also time to start looking at the security these banks offer you?
In this series we’ve explored the weaknesses of the common login page. Banks generally use more rigid looking login pages, utilizing your PIN on top of a password in many instances. But what are the flaws in these systems, which can make them as unsecured as any old login page? And what are the security heads of these companies doing to step up to the plate and make logging into your online bank account a more secure thing to do?
In this article, we’re first going to examine the holes that exist in the current systems. Then we’re going to take a closer look at the options that will soon be available to us to consider, in addition to interest rates and ATMs – the security of our online banking.
The big catchphrase among security experts for tomorrow is 2 Factor Authentication (2FA). This is not the solution to all of the difficulties relating to identity management on the Internet, but it is a big improvement on what’s out there right now. We’ll put the term 2 Factor in context with other solutions commonly found on the Internet, and discuss what it actually is, and is not.
By way of introduction, 2FA aims to put another barrier between you, a hacker and your bank account. The crux of this is to put this second factor of authentication outside the reach of hackers, oftentimes by making it separate from the computer on which you are entering your data. For example, it might be a use-once code, based on your PIN or distinct from it, that is generated by a handheld computer.
But we’re getting ahead of ourselves. First, let’s take a look at what’s currently keeping (and failing to keep) our bank accounts and other data secure online.
The Current Crop
In our last article, we took a look at some of the security threats that face the ordinary Joe who is logging into online services today. From that you will have (I hope) received a very succinct impression regarding the state of your personal security as you transact online.
Let us take a look at the types of solutions that are being used on the Internet right now, culminating with a look at 2 Factor Authentication.
Single Factor Authentication Solutions: this is where the password is not ciphered or disguised in a manner that protects it from key loggers/screen scrapers, and social engineering techniques such as phishing. We’ll be looking at:
- The fully transmitted login password
- The partially transmitted login password
- Scramble Pads
- Virtual Keyboard
2 (Separate) Factor Authentication Solutions: this is where two factors exist to produce unrelated information as sources for the login process. This means that a password or PIN is entered, plus a separate piece of data that is sourced from something other than the computer.
- The Bingo Card (Static Grid Card)
- The TAN list
- Mobile Phone SMS Password
2 (Combined) Factor Authentication Solutions: this is where the user combines their password and an issued token to produce either a ciphered representation of a password/PIN, or a unique one time password/PIN dispatched through a mobile phone or similar device. In this category we’ll be examining:
- The Dynamic Grid Card OTP
- Electronic Token OTP
- Mobile Phone/PDA OTP
Let us begin at the beginning, with that dreaded login box.
Single Factor Authentication
A fully transmitted login password or PIN is about as much use in security terms as a chocolate fire safe, as we outlined in the previous article. This is where the username and password are entered in full in the login box, ripe for the picking. What is most incredible is the number of otherwise prestigious sites that use them.
Does the following look familiar?
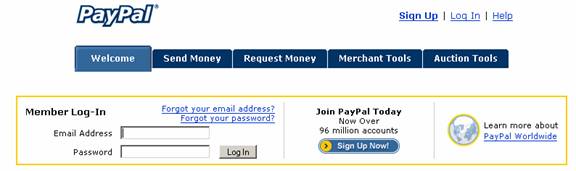
It should then come as no surprise that Fraudwatch cites PayPal as the most targeted site on Earth for phishers.
Fraudwatch is a site that monitors a variety of types of online fraud. In PayPal’s favor is the fact that they are actually listed in Fraudwatch. I’m aware of many online sites that are targets of online fraud, but their names do not even show up in sites like Fraudwatch.
The cynic in the audience might be moved to say “I wonder why?” But let’s not dwell on questions that cannot be answered without a trip down to the libel courts.
Here is another type of business that might be concerned with the protection of its customers:
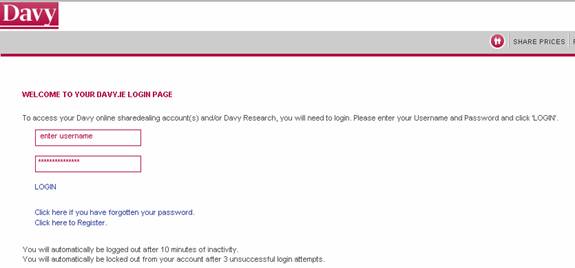
This is Davy Stock Brokers.
Now, a variant on the theme of looking for another piece of data, but in reality, both the password and PIN are equally vulnerable:
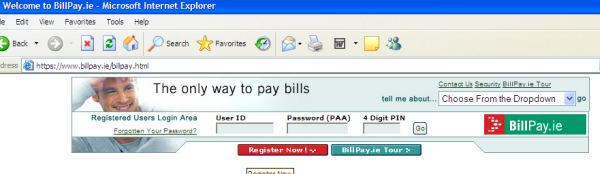
Sites that use these systems are really looking for trouble, because it isn’t that difficult to actually download the Web code from someone’s site. A program such as WGET will grab every object that it can find in a web site and copy it onto your hard disk. You then have a complete copy of this website, down to the images and copyright notices, and even the phishing warnings! It isn’t difficult then to comprehend why phishing has been such a successful attack.
Single Factor Authentication, Continued
Partial Transmission of Passwords/PINs is a step up from the chocolate fire safe – maybe to a hard plastic one. Again, it is very vulnerable to phishing, social engineering of all sorts, and key loggers, which will get the information they want after two or three successful logins. Despite that, it is by far the most used method in online banking today. Effectively, all the data necessary to break the login will become available through attacks on the PC, and instantly available through phishing and social engineering.
Scrabble Pads are a joke! Here, the user looks for the alternative letter that is provided onscreen and enters it in the password box. Unfortunately, all the information required for reverse engineering the password or PIN is on this page. The hacker essentially “has the screen”, and the letters that are entered, so where’s the security? Take a closer look:
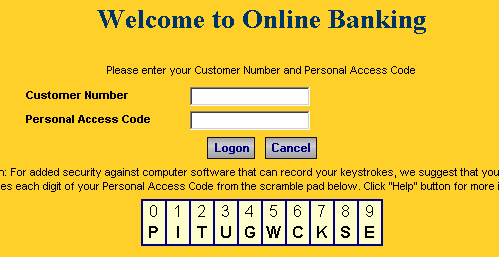
My desktop Trojan with key logger and screen scraper says “thank you very much” to this sort of thing. It offers no resistance to phishing at all, as the password or PIN is the basis of the substitution, the ‘cipher key’ displayed onscreen.
And Virtual Keyboards are not much better…
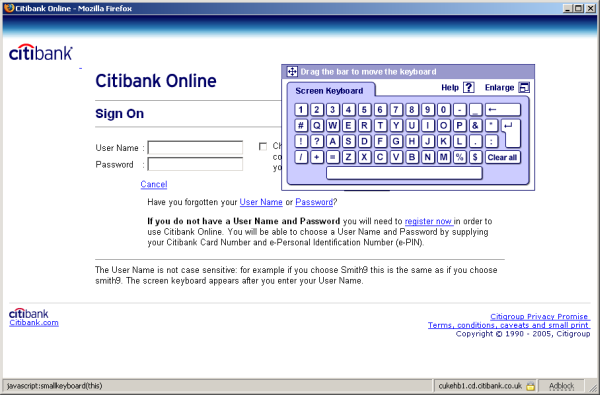
As above, my screen scraper can see every button click, irrespective of the ‘cipher’ that is passed to the server. This also offers no resistance to phishing at all, because if the user has given up the password/PIN, then the virtual keyboard is irrelevant.
2 Factor Authentication Methods
The Bingo Card (Static Grid Card) is a 2 (Separate) Factor Authentication solution and is definitely a step up the security ladder. Look at the following and then I’ll explain.
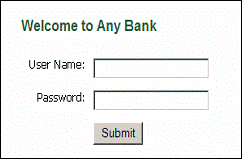
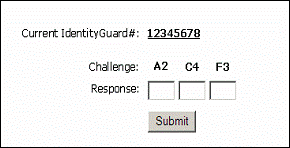
The user is first prompted for a username and password as normal. Then a challenge is received to derive values from the grid card:
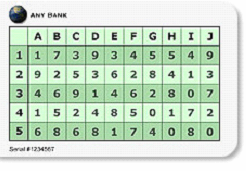
Now we have a number of individual factors that determine a successful outcome. This fact renders it very resistant to phishing. The only snag here is administration – each time a set of co-ordinates is used, they cannot be used again or security degrades. This is further restricted by the size of the card, and the amount of data that it can contain.
TAN Lists Transactional Access Numbers (TANs) are considered to be a weaker form of grid card than the bingo cousin above. They are in the 2 (Separate) Factor Authentication solution category. A TAN list is a series of numbers of varying length (chosen by the creators) entered on a card.
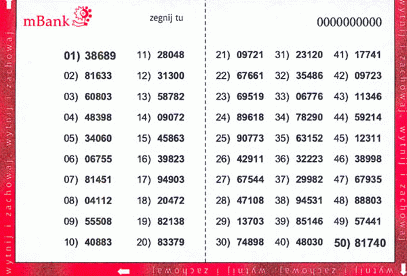
A user might be prompted for details as follows (note that this example does not use the TAN list above):
Having entered a username (or number in this case) and password, the user is prompted to select a number from the TAN list and enter it. This is a popular solution in EU countries.
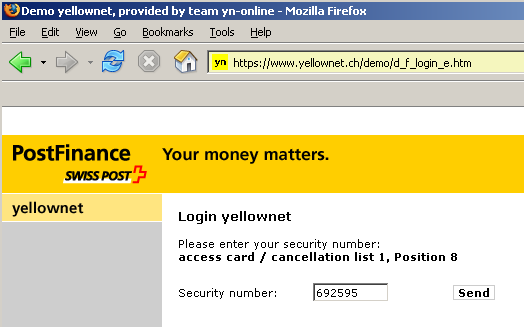
Mobile Phone SMS Passwords are another form of a 2 (Separate) Factor Authentication, in which one-off numbers are sent via SMS to your mobile phone when logging in. The user registers their mobile phone with the site, and at login time, the SMS message is sent containing a password or PIN. The user enters that unique data as a factor in the login process.
This service can be constrained by the ability of the phone carrier to route SMS messages through in a timely fashion, and to provide coverage to the location from which the user is connected to the Internet. Of course, there is also the somewhat relevant point that not everyone owns a mobile phone (surprising, but true!)
2 (Combined) Factor Authentication
2 (Combined) Factor Authentication means combining something that you know, with something that you must produce as a one-time representative value in place of your PIN. This second factor can then be interpreted and verified by the site to which you are connecting. The core idea is that the password or PIN is altered into some form of cipher that is not traceable by anything on the computer.
The two factors usually take the form of a PIN (the something that you know) and a token (the something that you have).
Tokens come in several forms, but are most commonly electronic ‘calculator like‘ devices. These are integrated with common electronic objects such as PDAs, mobile phones and such like, or take the form of plastic cards about the size of a credit card.
The following is a synopsis of the common options. (Please note that the mention of any vendor product is not an endorsement of the product nor an indication of preference on behalf of the author, who is himself involved in 2 Factor Authentication.)
Electronic Tokens: These solutions are very secure. Each user is issued with an electronic token that is designed to go on a keyring, similar to the following:
![]()


The user inputs their PIN into the electronic token, which in turn returns a number that is an OTP. This is entered into the site login box and the OTP is validated.
The upside of these tokens is that they provide very good security. The downside is that they are expensive.
2 (Combined) Factor Authentication, Continued
Dynamic Grid Cards: A Dynamic Grid Card is similar to the Bingo Card above, with one important difference: This solution combines the user’s password or PIN with information presented on a user screen, and interprets it using a token.
The user is presented with a screen not unlike the following:
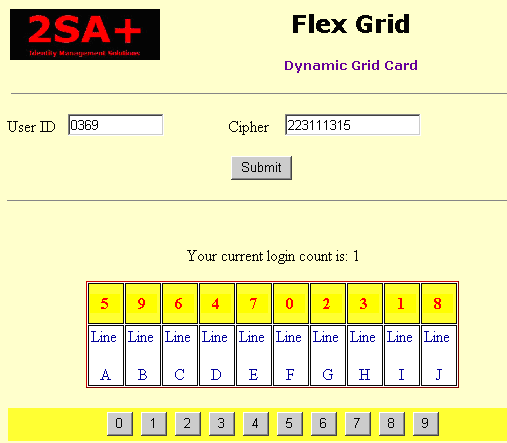
The user has a password or PIN, and a token.
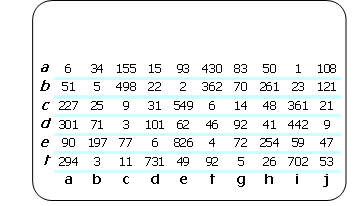
In conjunction with screen, token and PIN, a cipher text is derived and passed to the site software for validation.
Mobile Phones / PDAs:
An initiative is currently underway to enable personal electronic devices such as mobile phones, PDAs and the like to generate a cipher text representation of their PIN. The functionality is not unlike the electronic token, and seeks to use existing technology that may already be in the possession of potential users, to reduce costs.
In Conclusion
We have looked at a sampling of the current 2 Factor product segment. The uptake of these solutions certainly increases security considerably, and will allow sites to expand the services that are currently available online. There is a sting in the tail however. Given our previous article explaining Man in the Middle attacks, what actual use would a 2 Factor solution be when session hijacking was an issue?
That is the question that the security industry is targeting now.
All trademarks and registered trademarks referenced in this article are the property of their respective owners.
Pat McKenna is a Security Consultant and CTO with 2SA Plus, a company specializing in 2 Factor Authentication and matters of Identity Management. He is 45 and has been in the IT business for 15 years, during which he has held many positions, including company director. Prior to a career in IT, he worked in the security and intelligence field. He is proficient with many computer languages, old and new, and has trained hundreds of programmers.
His hobbies are chess and penetration testing, aka ethical hacking.
