Introduction
4/21/2013 – Auditor was long ago replaced by Backtrack.
12/16/2006 – Replaced references to Moser Informatik with Remote Exploit.org

| Auditor Security Collection | |
|---|---|
| Summary | Extensive collection of network security analysis tools professionally integrated into a bootable Knoppix-based CD. Organized into foot-printing, analysis, scanning, wireless, brute-forcing, cracking categories. Free and released under the GPL. |
| Update | 2 July 2004 – Added more wireless card information |
| Pros | • No hassles with installation or configuration • All the tools you need for network security analysis • Free |
| Cons | • Can be very damaging if misused |
What if you could have the best network hacking and auditing tools on a single bootable CD? The folks at Remote Exploit.org have cooked up their Auditor Security Collection (ASC) CD, which has 300+ network security programs pre-installed. Here is the best part, it’s FREE.
Whether you are a Network Penetration Analyst or just a curious hacker, the ASC will provide you with all the software tools you need. You don’t have to install any drivers as the Knoppix Linux based CD will automatically detect and configure your hardware. Let’s take a closer look at the Auditor Security Collection.
How to get it
The ASC is downloadable from Remote Exploit.org. The file is about 518 MegaBytes. After you download it, you have to unzip and then burn the ISO image. You can use any popular CD-Burning program such as Ahead Nero. Keep the.ISO image around just in case you need to burn another copy. Remember it’s free, so you don’t have to worry about any pesky license agreements.
Booting Up
To start the ASC, simply put in the CD and set your BIOS to boot from CD-ROM. At the first screen, you can select a wide range of screen resolutions. Even non-standard ones such as 1400X1050 and 1600X1200 are available. You can also boot from USB CD-ROMs, which are common to some ultra-portable laptops.
The next screen lets you choose the keyboard language layout. The DVORAK layout is not available, which hurts the DVORAK typers out there (like myself). Of course, if you don’t type on a DVORAK layout then this doesn’t matter. The real magic starts after you pick the keyboard layout.
Since the ASC is based on Knoppix Linux and the 2.6.6 Kernel, hardware compatibility is amazing. You can see THG’s review of Knoppix in this article. ASC detected every ethernet interface on four different laptops and three desktops. ASC detects USB keychains and hard-drives. Those are mounted in the /mnt/sda1 folder.
I tested five wireless cards; US Robotics, Linksys, Buffalo, MSI and Cisco Aironet (not pictured below). Only the MSI card was not detected. The popular Atheros wireless interface that is built-in to many laptops was also detected.

Figure 1: Auditor handled all these except the MSI
Updated 2 July 2004
Cards [and chipset if known] used were:
- Cisco Aironet PCM350 [ Cisco ]
- Linksys WPC11 ver3 [ Conexant PRISM III ]
- Buffalo WLI-PCM-L11 [ Lucent Hermes ]
- US Robotics USR2410 [ Conexant PRISM II ]
- MSI CB54G [ Broadcom AirForce ]
- Toshiba Satellite laptop integrated [ Atheros ]
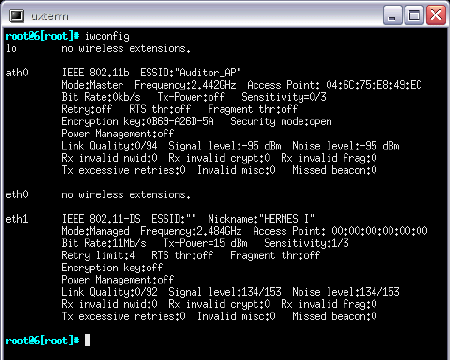
Figure 2: Networking interface details
Tools
All of the network tools are under the Auditor menu. The full list of network tools can be found here. There are several dozen programs for footprinting, scanning and analyzing networks. Think of footprinting as network recon, where you just want to find out what is out there, but you don’t want to break in yet. You have your basic port scanners such as NMap. SMB scanners are also included that will scope out available Windows and Samba shares.
Scanning involves sniffing the network. The best open source scanner Ethereal is included. With Ethereal, you get to see the raw network traffic flowing over the cable or through the air. EtherApe, which monitors how the computers are communicating to each other, is also included.
Several analyzers are included which will literally rip passwords and URLs from the network stream. For example, Dsniff will parse out mail, FTP, telnet, AIM and many other types of passwords.
Wireless Mayhem

Figure 3: The Wireless Tools selection
Arguably, you will have the most fun with the wireless security tools. I know I did. You get scanners such as Kismet and Wellenreiter. You can see a screenshot of Kismet running below. All of the installation and configuration nightmares have been taken care of. You just have to open the application.
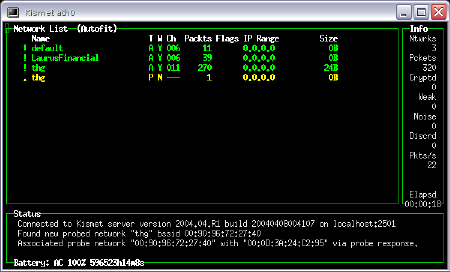
Figure 4: Kismet in action
If you have any network training, then you know the Media Access Control (MAC) address is burned into your network card. This creates a “serial number” of sorts for every wireless and wireless interface card out there. With the handy dandy MAC address changer utility (Auditor > Wireless > Change your macaddress), you can have a new MAC address in about five seconds.
You can have the program make a random MAC address or you type in your own. So you can make your Cisco card appear to be a Linksys card. Or you can spoof an existing MAC address on the network.
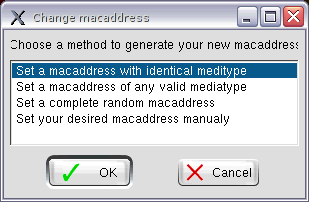
Figure 5: Changing your MAC address is easy
Figure 6 shows the address resolution protocol (ARP) table of our Windows “victim” computer. I pinged the computer from the ASC booted laptop. Our real MAC address is 00-90-96-85-4c-e6. After the first ping, I used the MAC address changer and made up a random MAC address. After the second ping, the victim ARP table saw the MAC address of 04-6c-75-e8-49-ec.
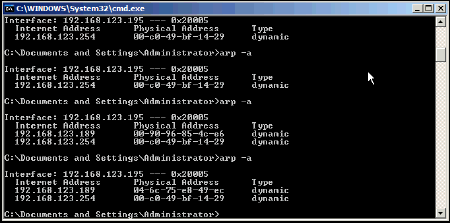
Figure 6: Detection of changed MAC address by Windows
Finally, you can make the computer appear to be a wireless hotspot and intercept all the wireless traffic. In the screenshot below you can see our Windows machine detecting the fake hotspot.

Figure 7: It’s easy to spoof an AP
Password Breaking Tools
This CD has more than a dozen password breaking tools. Zip passwords, VNC passwords, even SMB (Windows shares) passwords can be broken. All of the programs are already installed and ready to be fired up. In addition, wordlist files in many languages are included. There are even themed wordlists such as movies and people names.
Figure 8: Wordlists used by password cracking tools
Applications Menu
Essential applications are also included. You get Firefox for web-browsing, GFtp for FTP, GEdit for text-editing, and Gimp for graphical work. In fact, all the screenshots were taken using the Gimp screenshot feature. There are no games or useless applications.
I was able to browse the web with Firefox after setting up my wireless SSID, WEP key and DHCP settings in the Configuration menu (explained below). Firefox has a minor comestic glitch that will show an error screen upon startup, but you can close it and continue surfing.
Utilities Menu
Some other important programs are included in the Utilities menu. You get Virtual Network Connection (VNC) for remote control, a basic calculator and a PDF viewer.
Configuration
In the Configuration page, you can prepare your USB memorystick / keychain. This will put a.auditor file on the keychain, which will contain some persistant settings. When you boot the ASC with the prepared keychain in the USB port, the.auditor file will be read and your settings will come back. You will also be able to save other information to the keychain. We were able to save the screenshots that we took to our USB Cruzer keychain.
Figure 9: Settings and files can be saved to a USB flash key
Even though the ASC detects most network and wireless interfaces, you still have to configure them with settings such as IP address, SSIDs, and WEP keys. The configuration menu makes this easy by providing intuitive menus. One nice feature is that the network interface configuration will automatically come up after you setup your wireless SSID and WEP keys.
The last option is very interesting as it actually will install all the operating system and all the programs to the hard-drive. This is still somewhat experimental and we did not test it out.
Documentation
Almost every one of the networking tools has documentation. The ASC makes life easy by putting the documentation in the main menu bar. If you are used to command line, you can open up a terminal window and look at the MAN pages directly. The documentation is a great learning resource as some of these tools are not well known.
Conclusion
I consider the Auditor Security Collection the best CD available for the networking professional. The ASC contains almost every network security program (good and bad) known to man. It automatically detects and configures almost all hardware. Output from these programs can be saved to a USB keychain. To top it all off, it’s free.
The authors are asking for a small donation (via Paypal) when you download the CD image. Given the hard work that has been put into this software, I would say that a donation is well deserved.
I have admired the open-source community for developing some of the best networking tools available (Ethereal, Kismet, Snort, etc). Traditionally there were two problems with getting the software to work; software installation was difficult and hardware detection (especially with wireless cards) was spotty.
The Auditor Security Collection has solved both problems and in a big way. Auditor is definitely a must-have!
