Introduction
Please see How to Crack WEP…Reloaded for the most up-to-date WEP cracking how to.

After demonstrating in How To Crack WEP – Part 1 and Part 2 that WEP cracking is easier than you may have thought, I will now switch gears. In this last part of the WEP Crack How To, I will show you how to take a common sense approach to protecting your wireless network.
As any security professional knows, there is no such thing as perfect security. A good security plan takes into account the value of what needs to be protected, the cost of implementing the protection and the nature and skillset of the potential intruder in order to formulate an effective security plan. In other words, rather than implementing every defensive measure known to man, a more prudent (and cost-effective) approach may be to tailor your defense to the threats that you most likely face.
For example, wireless networks located in cities generally face more possible intrusions than those located in sparsely-populated areas. During the course of a day in a city, dozens, maybe hundreds of people may pass by your wireless LAN. And a car could also be parked outside your home for hours, without attracting notice. But a wireless AP located in a home on a ten-acre farm would be unlikely to see any client but its owner’s and any unfamiliar vehicles would be noticed and investigated in short order.
Why Bother?
For some people, setting up a secure wireless network is so daunting, they give up and run it wide open, ie. unsecured. I also hear people say, “I just surf the web and have nothing valuable on my computer. Why should I bother with security?” Good question, but here are some equally good answers.
Running your WLAN wide open entails three major risks:
1) Your network resources are exposed to unknown users
Once someone wirelessly connects to your LAN, they have the same access as users directly connected into your LAN’s Ethernet switch. Unless you have taken precautions to limit access to network resources and shares, intruders can do anything trusted, known users can do.
Files, directories, or entire hard drives can be copied, changed or entirely deleted. Or worse, keystroke loggers, Trojans, zombie clients or other programs can be installed and left to work for their unknown masters.2) All of your network traffic can be captured and examined
With the right tools, web pages can be reconstructed in real-time, URLs of websites you are visiting captured, and most importantly passwords you enter stolen and logged for future mis-use, most notably identify theft.
3) Your Internet connection can be used for illegal, immoral or objectionable activities
If your open WLAN is used to transfer bootleg movies or music, you could possibly be the recipient of a lawsuit notice from the RIAA. In a more extreme case, if your Internet connection were used to upload child pornography to an FTP site, or used to host the server itself, you could face more serious trouble. Your Internet connection could also be used by spammers, DoS extortionists and purveyors of malware, viruses and their like.
It may be a noble sentiment to give free Internet access to anyone within range of your wireless LAN. But unless you put some serious protection between your “open” LAN and the one you use, you are exposing your data, and perhaps more, to serious risk.
The approach I’ll take in formulating WLAN security recommendations is based on the expected skill level of potential wireless intruders. I’ll then provide recommended security countermeasures for each skill level.
NOTE: I will generally use “AP” (Access Point) throughout this article, but this should be read as meaning “Access Point or wireless router”.
Skill Level 0: Anyone with a wireless computer
It doesn’t take special skills to “hack” an unprotected wireless LAN – anyone with a wireless-enabled computer and the ability to turn it on is a potential intruder. Ease of use is often touted as a selling point of wireless networking products, but this often is a double-edged sword. In many cases, people innocently turning on their wireless computers will either automatically connect to your access point or see it in a list of “available” access points.
The following countermeasures should help in securing your network against casual access, but offer no real protection against more skilled intruders. These are listed in relative order of importance. But most of them are so easy to do that I recommend doing them all if your equipment allows.
Countermeasure 1: Change Your Default Settings
At minimum, change the administration password (and username if your equipment allows), and default SSID on your AP or wireless router. Admin passwords for most consumer wireless gear are widely available. So if you don’t change yours, you could find yourself locked out of being able to control your own WLAN (until you regain control via a factory reset)!
Changing the default SSID is especially necessary when you are operating in proximity of other APs. If multiple APs from the same manufacturer are in the area, they will have the same SSID and client PCs will have a good chance of “accidentally” connecting to APs other than their own. When you change the SSID, don’t use personal information in your SSID! During my Netstumbler sessions, I have seen the following as SSIDs:
- First and Last names
- Street Addresses with apartment numbers
- Social Security Numbers
- Phone Numbers
Changing the default channel of your AP might help you avoid interference from nearby wireless LANs, but it has little value as a security precaution since wireless clients generally automatically scan all available channels for potential connections.
Countermeasure 2: Upgrade Your Firmware, and maybe Hardware
Having the most current firmware installed on your AP can sometimes help improve security. Updated firmware often includes security bug fixes and sometimes adds new security features. With some newer consumer APs, a single click will check for and install new firmware. This is in contrast to older APs which required the user to look up, download and install the latest firmware from a sometimes difficult-to-navigate support site.
APs that are more than a few years old have often reached their end of support lifecycle, meaning that no new firmware upgrades will be made available. If you find that your AP’s latest firmware doesn’t support at least the improved security of WPA (Wi-Fi Protected Access), and preferably the latest version called WPA2, you should seriously consider upgrading to new gear. The same goes for your wireless clients!
Virtually all currently-available 802.11g gear supports at least WPA and is technically capable of being upgraded to WPA2. But manufacturers are not always diligent in their support of older products, so if you want to be sure that your gear supports WPA2, either check the Wi-Fi Alliance’s certification database, or do some Googling in both the Web and Groups.
Countermeasure 3: Disable SSID broadcast
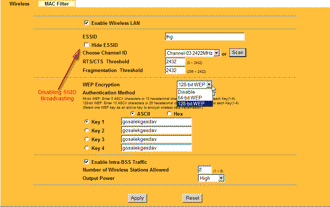
Most APs allow users to disable SSID broadcasting, which will thwart a Netstumbler scan. This will also stop Windows XP users using XP’s built-in Wireless Zero Configuration utility and other client applications from initially seeing the wireless network. Figure 1 shows the control labeled “Hide ESSID” that will do the trick on a ParkerVision access point. (“SSID” and “ESSID” both refer to the same thing.)
Figure 1: Disabling SSID Broadcast on a Parkervision AP
(click image to enlarge)
NOTE: Disabling SSID broadcast will not prevent a potential intruder using Kismet or other wireless survey tools such as AirMagnet from seeing your wireless network. These tools don’t rely on SSID broadcast for available network detection.
Skill Level 0 Countermeasures – more
Countermeasure 4: Turn it off!
People commonly overlook the simplest way of securing their wireless network – turning off the AP! A simple lamp timer can be used to turn off your AP during the overnight hours when you’re not using it. If you have a wireless router, this will mean that your Internet connection will also be disabled, which also isn’t such a bad thing.
If you can’t or don’t want to periodically shut down your Internet connection, you’ll have to remember to disable your wireless router’s radio manually – if it has this feature. Figure 2 shows a typical wireless disable control. This manual method is more prone to error, however, since it’s just one more thing to forget. Perhaps at some point manufacturers will add radio disable to the features that can be scheduled on wireless routers.
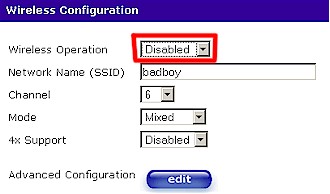
Figure 2: Shutting off the radio
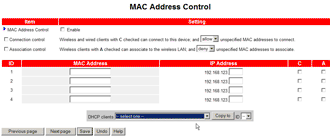
Countermeasure 5: MAC Address Filtering
MAC Address filtering is used to control access to your AP by allowing (or denying) access to a list of wireless client MAC addresses you enter. It will prevent an unskilled intruder from connecting to your WLAN, but MAC addresses are easily captured by more skilled attackers and wireless adapter MAC addresses easily changed to match a captured address.
Figure 3: MAC Address filtering on an older USR 8011 AP
(click image to enlarge)
Countermeasure 6: Lower the transmit power
While only a few consumer APs have this feature, lowering your transmit power can help limit intentional and accidental unauthorized connections. But with the increased sensitivity of wireless cards that even unskilled users can purchase, it may not be worth the bother – especially if you’re trying to prevent unwanted connections in an apartment building or dorm.
Most skilled attackers typically use high-gain antennas, which allow them to detect very low signal levels and effectively offset this countermeasure.
Skill Level 1: Anyone with commonly available wardriving tools
Now let’s move up a notch on skill level to that of your common “wardriver”, who actively cruises around looking for wireless LANs. Some people wardrive for kicks to see how many wireless networks they can detect and never attempt to use the vulnerable networks they find. But others are not so benign in their intent and do connect, use and sometimes abuse unsuspecting wireless LAN owners.
At Skill Level 1, I’ll assume that all the countermeasures suggested for Skill Level 0 do not work and the potential intruder can see your wireless network. The only effective countermeasures at this point involve encryption and authentication. I’ll save authentication for later and focus on encryption.
NOTE: While forcing all wireless traffic to use a VPN (Virtual Private Network) is one solution, VPN’s are notoriously difficult to set up and beyond the scope of this article.
Countermeasure 7: Encryption
Wireless LAN owners should run the strongest type of encryption available to them. Your choices will be dictated by the capabilities of your WLAN hardware and your options are WEP, WPA and WPA2.
WEP (Wireless Equivalent Privacy) is the weakest wireless security technology, but currently the most widely deployed due to its availability on virtually all 802.11 wireless products. You may have to use it because many consumer wireless product manufacturers have opted to not provide upgrades from WEP to WPA for 802.11b products. And others are still creating new products such as some VoIP wireless phones that support only WEP, forcing some WLAN owners to downgrade their security to accomodate the lowest common level of security.
Either WPA (Wi-Fi Protected Access) or WPA2 provide adequate wireless security, due to their stronger encryption technology and improved key management. The main difference between the two is that WPA2 supports stronger AES (Advanced Encryption Standard) encryption. But to further confuse users, there are some WPA-labeled products that allow the selection of AES vs. the WPA-standard TKIP encryption.
Most 802.11g products support WPA (but there are exceptions), but upgrades to WPA2 for older products are still in the process of being rolled out – even though the 802.11i standard that WPA2 is based on was ratified in June 2004.
I recommend that you use WPA as a minimum. It is as effective as WPA2 and, at least as I write this, more widely supported. Implementing this recommendation, however, may require purchasing new equipment, especially if you currently are using 802.11b in your WLAN. But standard 11g gear is relatively inexpensive and could be the best security investment you make.
Most consumer APs support only the “Personal” version of WPA or WPA2, which is also referred to as WPA-PSK (Pre-Shared Key) (see Figure 4). WPA2 or WPA “Enterprise” (also known as WPA “RADIUS”) is also supported by some consumer wireless gear, but is of little use without the additional RADIUS server required to implement it.
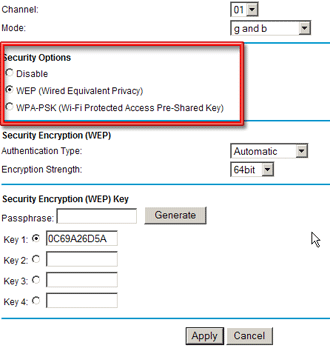
Figure 4: Encrypting traffic on a Netgear AP
For most personal WLANs, using WPA-PSK will provide adequate protection, but it is essential to use a key that is sufficiently long and random. Do not use a number, or a word from the dictionary, since programs such as cowpatty are already available to perform dictionary-based attacks against WPA-PSK.
Robert Moskowitz, Senior Technical Director ICSA Labs, recommended in this article using an 128 bit PSK. Fortunately, all WPA implementations accept alphanumeric PSKs, which would require only 16 characters to implement Mr. Moskowitz’ recommendation.
There are many password generators available on the Internet that can be found by a quick search. This one has lots of bells and whistles and even provides an estimation of how long it would take to crack the password it generates.
As a final note, some manufacturers have started selling APs and wireless cards that promise “one touch” easy setup of secured wireless connections. Buffalo Technology had the first products based on their AOSS (AirStation One-Touch Secure Station) technology. Linksys has recently starting selling products based on similar technology from Broadcom dubbed SecureEasySetup. You can read a comparative review of these two technolgies here.
Skill Level 2: Anyone with WEP / WPA-PSK Cracking Skills
While WPA and WPA2 eliminate many of the problems associated with WEP, they are still vulnerable to attack, particularly in their PSK form. Many people have already cracked WEP and Parts 1 and 2 of this series provided a step-by-step procedure.
Breaking the pre-shared key of WPA and WPA2 “Personal” is much harder and time consuming – especially if you are using AES encryption – but it is possible.
Countermeasure 8: Add Authentication
To address this emerging threat, users should implement authentication. Authentication adds another layer of security by requiring a client computer to “sign-in” to the network. Traditionally this has been done with a mix of certificates, tokens, or hand-typed passwords (also called Pre-Shared-Keys) that are negotiated with an authentication server.
802.1X provides the access control framework used by WEP, WPA and WPA2 and supports several EAP (Extensible Authentication Protocol) types that do the actual authentication. George Ou’s excellent article on Authentication Protocols contains probably more than you’d ever want to know about EAP, WPA and WPA2!
Configuring authentication can be a daunting and expensive task for networking professionals, let alone home networkers. At this year’s RSA conference in San Francisco, for example, many attendees didn’t bother to set up their wireless connection because of the full page of instructions they had to follow to do it!
Thankfully, things are getting better, and you don’t need to buy a full-blown RADIUS server, as there are a number of easier-to-implement alternatives. McAfee’s Wireless Security Suite is a subscription-based product starting at $4.95 per user per month with discounts for volume purchases. A free 30 day trial download is available here.
Another free option worth investigating for more experienced networkers is TinyPEAP, which adds a small RADIUS server supporting PEAP-based authentication into Linksys WRT54G and GS wireless routers. Note that since this firmware isn’t officially supported by Linksys, you’re on your own if you mess up your router while installing TinyPEAP.
Skill Level 3: Expert Cracker
Up until this point, we have blocked an intruder from wirelessly doing the equivalent of plugging their laptop into an Ethernet port on your LAN. But despite your best efforts, someone with expert cracking skills may penetrate all of your wireless defenses. What do you do now?
There are wired and wireless LAN intrusion detection and prevention product available, but they are targeted at enterprise applications and come priced accordingly. There are also open source solutions that are unfortunately not user-friendly for networking novices. The most widely-used of these is Snort, which I hope to explore in a future article.
But general network security practices have long dealt with traditional wired LAN intrusions, and can be used to combat an expert wireless intruder.
Countermeasure 9: Implement general LAN security
Implement the following countermeasures to improve general LAN security:
1) Require authentication to access any network resource
Any server, network share, router, etc. should preferably require user-level authentication for access. Although you won’t be able to implement real user-level authentication without some sort of authentication server, you can at least password-protect all shared folders and disable Guest logins if you’re running Windows XP. And never share the contents of entire hard drives!
2) Segment your network
In the extreme case, a computer not attached to a network is safe from network-based intrusion. But there are other ways to keep network users away from where they shouldn’t be. A few properly-connected Inexpensive NAT-based routers can be used to establish firewalled LAN segments while still allowing Internet access. See this How To for the details.
Switches or routers with VLAN capabilities can also be used to separate LAN users. VLAN features can be found on most any “smart” or managed switch, but are harder to come by in consumer-priced routers and unmanaged switches.
3) Bulk up your software-based protection
At minimum, you need to run current versions of good anti-virus applications that automatically update their virus definition files. Personal firewalls such as ZoneAlarm, BlackICE, etc. can alert you to suspicious use of your network. And, unfortunately, the latest generaton of malware and spyware threats make adding an anti-spyware application also necessary. Webroot Software’s Spy Sweeper seems to be getting good marks lately, along with Sunbelt Software’s CounterSpy.
Note that you must install protection on every machine on your LAN in order to have effective protection!4) Encrypt your files
Encrypting your files with strong encryption should provide effective protection in the event unauthorized users do gain access to them. Windows XP users can use Windows Encrypted File System (EFS). Mac OS X Tiger users can use FileVault. The downside to encryption is that it takes time and computing power to encrypt and de-crypt files, which could slow things down more than you’d like.
Conclusion
Wireless networking provides us with convenience, but we must take a common sense approach in securing it. There is no single thing that will shield you from attack and complete protection is very difficult to achieve against a determined intruder.
But if you take the time to understand the possible risks your wireless LAN is likely to encouter, you can implement effective protection.