IPv6 RFC 6555 = Happy Eyeballs
Introduction
In my article Switch Your Network to IPv6, I covered checking your router for IPv6 support, enabling IPv6, enabling DHCP-PD on your router’s WAN interface and verifying IPv6 functionality. I also discussed a few IPv6 terms and touched on IPv6 security.
In this second IPv6 article, I’m going to provide more detail on IPv6 addressing, security and VLANs. The goal is to provide more insight into IPv6, as well as provide information on some of IPv6’s quirks.
Before I get into details on IPv6 addressing, let me explain the eyeball graphic above. RFC (Request For Comment) 6555, also known as "Happy Eyeballs", refers to the ability of a dual-stacked PC to choose when to use IPv4 or IPv6.
While Windows XP and later versions include support for IPv6, they are not all equal in their support. A Windows PC should prefer IPv6 when possible and fall back to IPv4 if no IPv6 connectivity exists. Windows 8.1, 8, and Windows 7 have Happy Eyeballs support, allowing them to prefer IPv6 yet quickly fall back to IPv4 if needed. However, Windows XP IPv6 is not fully RFC standard compliant and has to wait for an IPv6 session to time out before it falls back to IPv4. So it is recommended to upgrade to Windows 7 or later if you’re migrating your network to IPv6. (Reference: Practical IPv6 for Windows Administrators, Edward Horley, 2013)
How an IPv6 Address Gets Made
With that said, it is useful to understand how IPv6 addresses are deployed. IPv4 addresses are either dynamically assigned to a device using DHCP (Dynamic Host Configuration Protocol) or they’re statically assigned to a device by a human. IPv6 addresses are created in the following ways:
- manually assigned
- automatically assigned by a device
- dynamically assigned using DHCPv6
- dynamically derived using SLAAC (Stateless Address Auto-configuration)
- derived/assigned using a combination of SLAAC and DHCPv6.
When IPv6 is enabled on a device, it will automatically assign itself a link-local address on its interfaces. The link-local address is important, as it is used by the device to communicate with other devices within the LAN.
A link-local address starts with FE80. An IPv6 device will complete its link-local address with the EUI-64 method, or in the case of Windows, a random method. Both methods are used to populate the last 64 bits of the address.
The EUI-64 method generates the last 64 bits of an IPv6 address by modifying its MAC address and inserting FFFE in the middle of the MAC. I’ll cover why Windows uses a random method shortly.
In the image below, you can see my Windows PC has generated its link-local address using the Windows random method, as there is no FFFE in the middle of the last 64 bits.
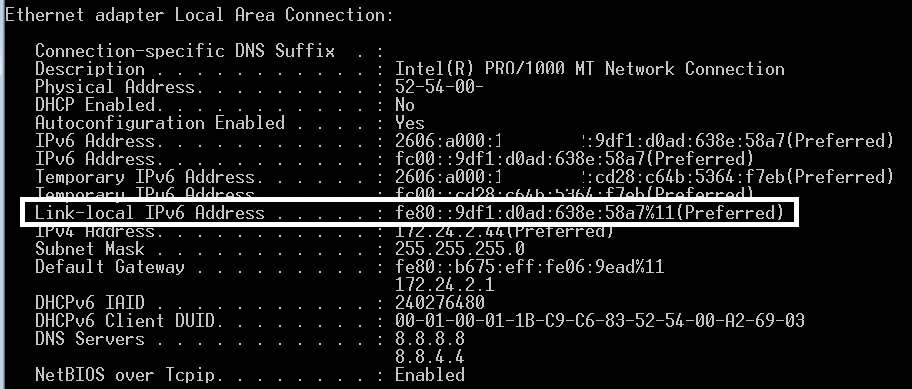
IPv6 Link-Local Address
An interesting IPv6 quirk is a device can use the same link-local address on multiple interfaces. Packets with link-local source and destination addresses are not routed, so the same link-local address can be used by a single device on multiple interfaces. As long as the link-local address is unique on the LAN, there won’t be an address conflict.
An IPv6 device uses Neighbor Discovery Protocol (NDP) Neighbor Solicitation (NS) messages to ensure it has created a unique link-local address on the LAN. Duplicate Address Detection (DAD) is the IPv6 process where NS messages are sent to verify that automatically assigned or dynamically derived messages are unique. Other IPv6 devices respond to NS messages with NDP Neighbor Advertisement (NA) messages, identifying whether the automatically assigned link-local address is unique.
SLAAC uses NDP Router Advertisement (RA) messages. IPv6 SLAAC partially replaces IPv4 DHCP. When a router is enabled for IPv6, it will regularly multicast RA messages advertising its global IPv6 prefix. The router will use its link-local address as the source of its RA messages.
Devices enabled for IPv6 will receive the RA message and use the source IPv6 link-local address in the router’s RA message as their default gateway to derive their global IPv6 address using the advertised global IPv6 prefix plus either the EUI-64 or random method. The DAD process is used by the IPv6 device to ensure its derived IPv6 address is unique. The screenshot below shows my PC’s default gateway address, which is my router’s link-local address.
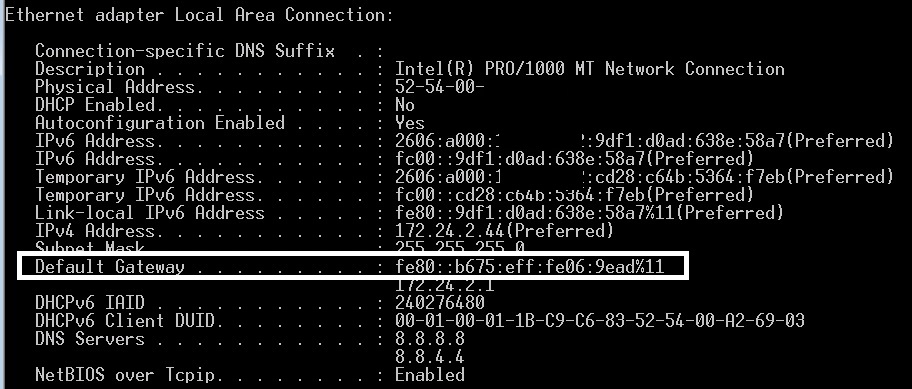
IPv6 Default Gateway
If no RA messages are received, a device will send a Router Solicitation (RS) message, looking for a RA. If there is no RA message sent, a device may then send a DHCPv6 request to get its IPv6 information.
Where’s The DHCP Table?
An unfortunate downside to SLAAC is the lack of a DHCP table. IPv4 routers typically have a means to display a DHCP table, which provides a list of DHCP-assigned devices on the LAN and their IPv4 address. The IPv4 DHCP table is a useful tool to list IPv4 devices on a LAN, shown below.
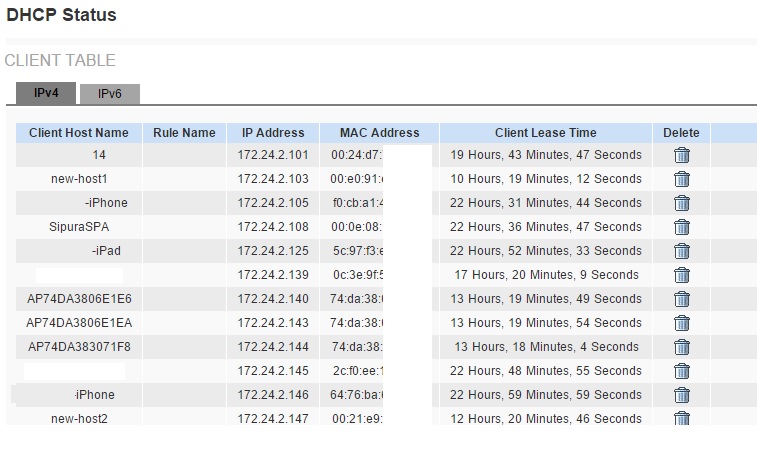
IPv4 DHCP Table
If SLAAC is used with IPv6, there may not be a DHCP table, because DHCPv6 may not even be running. The Linksys LRT224, for example, has DHCP for IPv4 enabled, but DHCPv6 disabled. The downside to SLAAC is you lose the DHCP list. The upside to SLAAC is less resources are used by the router to maintain lists, making the network more efficient.
IPv6 may use a combination of SLAAC and DHCPv6. The RA may have its Other Configuration Flag set to 1, which tells devices that further addressing information, such as IPv6 DNS addresses, is available via DHCPv6. A device receiving an RA with the Other Configuration Flag set to 1 may derive an address via SLAAC as well as use DHCPv6 to receive additional IPv6 information.
This lack of an IPv6 address table in a router can make bringing up new devices more difficult. With no DHCP table and tools like Overlook Soft’s Fing not supporting IPv6, it can be frustrating to find a device’s IP address so that you can get to its admin interface. Fortunately, manufacturers are building captive portals and default names into devices, freeing you from having to address it by IP address, either IPv4 or v6.
Finding MAC-IP Association
Another IPv6 by-product is the elimination of ARP (Address Resolution Protocol). IPv4 devices broadcast an ARP request over a LAN asking all devices for the MAC address associated with a specific IPv4 address. In contrast, IPv6 uses NDP messages to map IPv6 addresses to MAC addresses on a LAN. IPv6 multicasts an NS message asking all IPv6 enabled devices for a MAC address associated with a specific IPv6 address.
In Windows, you see MAC-IPv4 associations by using arp -a and MAC-IPv6 associations by netsh interface IPv6 show neighbors from the command line. Here’s output from arp -a…
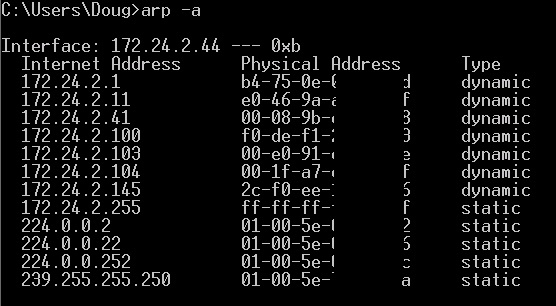
IPv4-MAC Table
and netsh interface IPv6 show neighbors commands.
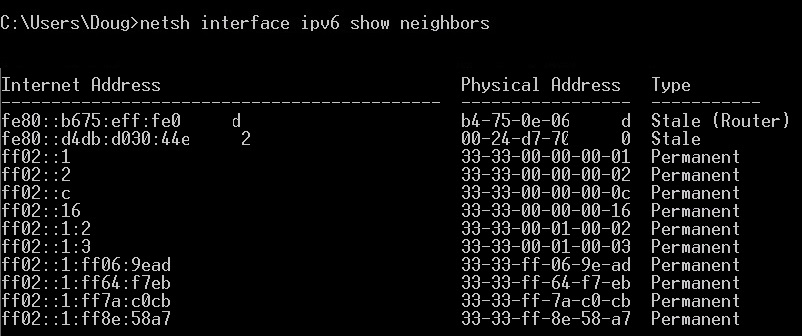
IPv6-MAC Table
Notice in the above output that arp shows multiple MAC-IPv4 associations, but the netsh output shows only two MAC-IPv6 associations. This illustrates an efficiency in IPv6. In many small networks, a PC only needs to know the MAC address of its default gateway. Due to the broadcast nature of arp, a PC is likely to learn the MAC-IPv4 associations of multiple PCs on the LAN. With the more focused multicast messages of NDP, a PC is going to only learn the MAC-IPv6 associations it needs, such as its default gateway.
Temporary Addresses
Another interesting Windows IPv6 quirk is its use of temporary addresses. You may have noticed your IPv6-enabled PC has multiple global IPv6 addresses, some labeled IPv6 Address and others labeled Temporary IPv6 Address. In the image below, generated via ipconfig /all, you can see my PC has global and unique local IPv6 addresses, some preceded by the word “Temporary.”
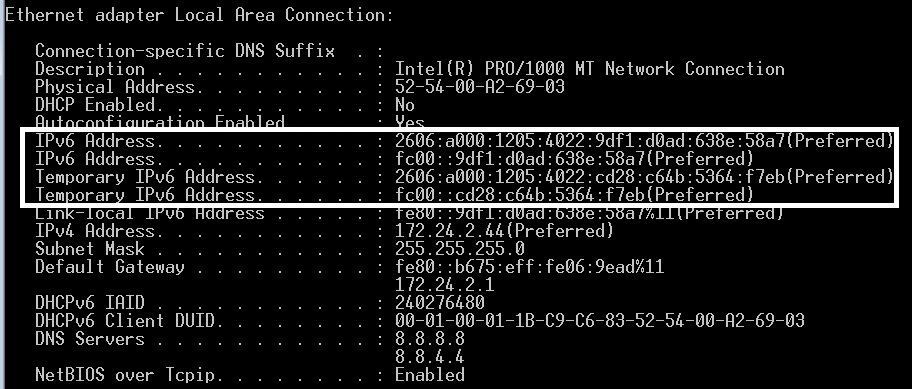
Windows’ Temporary IPv6 Addresses
With EUI-64 derived addresses, even though the global IPv6 prefix may change from network to network, the last 64 bits will be constant. Thus, it is possible a device using EUI-64 could be tracked as it moves from network to network, reducing anonymity and security.
Windows solves that issue with the combination of random addressing and deriving permanent IPv6 and temporary IPv6 addresses. Windows periodically changes temporary IPv6 addresses. The end result is outbound traffic from a Windows device and its inbound response will use the temporary address. Since the last 64 bits of a Windows IPv6 address changes periodically anonymity and security are preserved.
I observed that web traffic from my IPv6-enabled Windows PC to IPv6 enabled sites on the Internet used my temporary IPv6 address as the source address instead of the permanent IPv6 address. I also observed over a few days that my temporary IPv6 address changed, while my permanent IPv6 address did not.
IPv6 IPsec
You’ll often see references to IPsec being "built into" or being an "integral part" of IPv6, implying that all IPv6 traffic is encrypted, making it more secure than IPv4. This isn’t true. The only difference is IPv6 packets include an IPsec AH (Authentication Header) and ESP (Encapsulating Security Payload) header, whereas IPv4 uses header extensions to support IPsec AH and ESP.
IPv6 and IPv4 IPsec can be configured directly in Windows using Windows Firewall with the Advanced Security snap-in. IPsec rules are created with Connection Security Rules in the Windows Firewall. A screenshot showing the Connection Security Rules section is shown below.
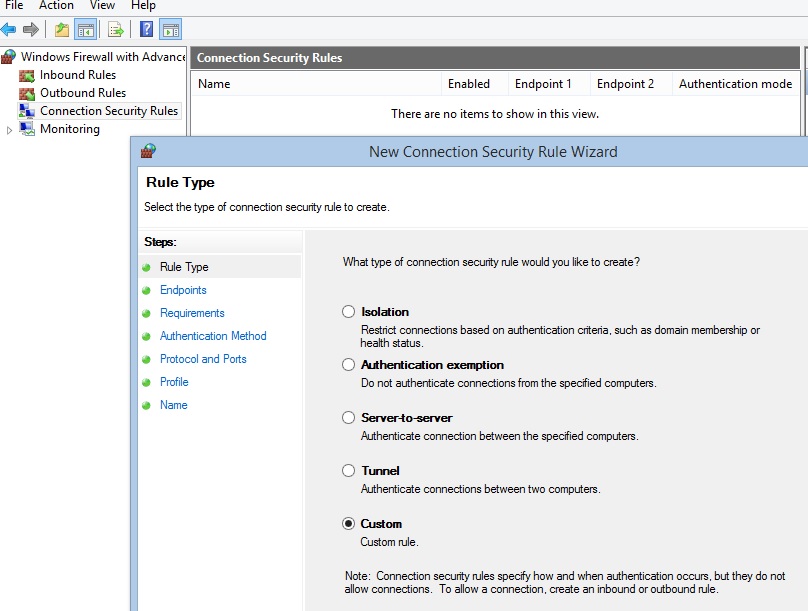
Windows and IPsec
Completing Windows IPsec configurations and getting an IPv6 IPsec tunnel running is another story, which I’ll leave to a future article. With Windows 2012 and Windows 8, Windows PowerShell can also be used for configuring IPsec. Neither method is easy. As we’ve seen with IPv4, practical use of IPsec with IPv6 will rely on running an IPv6 application.
IPv6 and NAT Firewalls
Many people think IPv6 with its globally-routable addresses for each device means that you no longer have to deal with your router’s firewall when you want inbound traffic to reach a LAN-based server. But this isn’t the case. There are a few things to keep in mind.
1) Your router blocks inbound IPv6 traffic by default, too.
With IPv4, devices have private addresses that are hidden behind a router’s simple NAT firewall. But since IPv6 has enough addresses for every device to have a globally routable IPv6 address, there is no need for Network Address Translation (NAT). So a common concern is that having a globally routable IPv6 address on a device connected to your LAN exposes that device to all the bad guys on the Internet.
The reality is that your router’s firewall blocks all incoming connections that aren’t initiated by a LAN device. This applies to IPv6 as well as IPv4. It’s just not performing NAT on IPv6 traffic. That means traffic coming from the Internet to your network is going to get dropped unless the router thinks the internal device initiated that traffic, such as a web page request.
2) You’ll need to open ports to reach IPv6 servers on your LAN
But what if you want inbound traffic to reach an IPv6 server on your router’s LAN? Even though you have a globally routable IPv6 address on your device, you will need to modify your firewall if you wish to permit externally initiated traffic access to a LAN device. Fortunately, the same methods used to permit externally initiated IPv4 traffic, such as port forwarding or DMZ, can permit externally initiated IPv6 traffic.
For example, let’s say I’m running an FTP server with a permanent global IPv6 address of 2606:a000:xxxx:xxxx:5dea:56f9:xxxx:8609 on my home network. If I want to allow externally initiated IPv6 access to my server, I need to put in a rule such as the one below, configured on a Linksys LRT224.
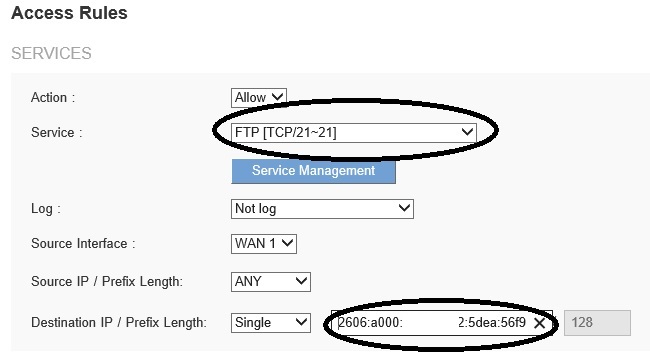
IPv6 Firewall Rule
The above example assumed I knew my device IPv6 address. Finding a Windows device IPv6 address is the same as finding its IPv4 address, simply type ipconfig /all from the command line. Note you’ll want to use your IPv6 Address, not your Temporary IPv6 Address in the firewall rule. Of course, if your router doesn’t provide an IPv6 firewall rule configuration screen, you’ll be out of luck.
3) For every IPv4 port you open, you need to open an IPv6 port too.
Since IPv4 and IPv6 are for the most part independent of each other, rules you create in your firewall to block or permit specific IPv4 traffic have to be duplicated with IPv6. A dual-stack network means you have dual tasks when configuring your router’s firewall.
4) Parental Controls and Content filters need to handle IPv6
Routers that support keyword/URL based parental controls and content filters need to listen to both IPv4 and IPv6 traffic. Because in an automatic dual-stack world, websites that support IPv6 will respond using it. If your router is watching only IPv4 traffic for the naughty bits, then it won’t block the bad stuff. However, as I’ll discuss in the VLAN section next, not all IPv6 enabled routers have equal functionality for IPv4 and IPv6.
5) UPnP might not work
UPnP NAT Traversal automatically opens router firewall ports, easing the pain of getting "personal cloud" NASes, remote access, gaming and other applications running. While there is a spec for UPnP support in IPv6, not all router manufacturers have implemented it.
VLANs
If you’re using a non VLAN capable router, you’re going to use one IPv4 and one IPv6 address range for all VLANs. Thus, simply set up the router for IPv6 as if there aren’t VLANs, and set up the switch as described in my article on Segmenting a Small LAN.
If you’re using a VLAN capable router in a dual-stack network, you’re using different IPv4 address ranges (subnets) and different global IPv6 address ranges (prefixes) for each VLAN. That means you have to configure VLANs for both IPv4 and IPv6, which is another example of the double-the-work nature of a dual stack network.
The examples listed in the Segmenting a Small LAN article linked above have steps for IPv4 addressing with a VLAN capable router. For IPv6 addressing with a VLAN capable router, here are a few useful IPv6 address details:
- IPv6 digits are hexadecimal instead of decimal. (MAC addresses also use hexadecimal digits.)
- An IPv6 address is made up of eight “quartets” of four hexadecimal digits, with each quartet separated by a “:”
- Each digit in an IPv6 address represents four binary bits.
- The prefix length of an IPv6 address represents how many binary bits are fixed.
- You can subnet an IPv6 prefix by using one or more of the non fixed bits. (A /56 prefix has 56 fixed bits, you can use the remain 72 bits for subnetting.)
- Subnetting IPv6 addresses is easier if your subnet ends on a quartet boundary, such as a /64, /80, /96, or /112.
With IPv6 addressing, you need to know when to use SLAAC, Router Advertisements, and DHCPv6. For IPv6 addressing with a VLAN capable router, there are two common scenarios. The scenarios are dictated by the prefix provided by your ISP.
Scenario 1: Your ISP provides a /56 global prefix. Use SLAAC and Router Advertisements
A /56 prefix lends itself well to VLANs. Let’s say my ISP provided the following prefix: 2606:a000:1234:2200::/56. The first 56 bits, or 14 digits (2606:a000:1234:22), are fixed. I can use digits 15-16 to create new /64 prefixes for each VLAN. This gives me 8 bits, or 256 possible prefixes. In this case, I could assign 2606:a000:1234:2201::/64 to VLAN1, 2606:a000:1234:2202::/64 to VLAN2, and so on, up to 2606:a000:1234:22FF::/64 for VLAN 256.
My next step would be to statically configure each VLAN interface on the router with the appropriate VLAN and address. For VLAN1, the prefix would be 2606:a000:1234:2201::/64 and the VLAN1 interface IPv6 address would be 2606:a000:1234:2201::1. Further, make sure Router Advertisements are enabled on each VLAN interface. This will allow devices on each VLAN to use SLAAC and derive an address from the appropriate prefix.
Scenario 2: Your ISP provides a /64 global prefix. Use DHCPv6
My ISP, Time Warner, provides a /64 global prefix. In this case, you could create /80 prefixes. SLAAC requires the use of /64 prefixes, so instead of SLAAC, you’re going to use DHCPv6 to dynamically provide addresses to PCs in each VLAN.
Let’s say the prefix I received from my ISP from my internal network is 2606:a000:1234:2222::/64. The first 64 bits, or 16 digits (2606:a000:1234:2222), are fixed. I can use digits 17-20 to create new /80 prefixes for each VLAN. In this case, I could assign 2606:a000:1234:2222:1::/80 to VLAN1, 2606:a000:1234:2222:2::/80 to VLAN2, all the way up to 2606:a000:1234:2222:FFFF::/80 for a total of 65,536 VLANs (!) on my internal network. (I doubt you need 65,536 VLANs on a small network!)
Here is a configuration example. The screenshots below are from a ZyXEL USG40 router. The below screenshot shows I’ve enabled SLAAC and DHCPv6 with DHCP-PD (Prefix Delegation) on the WAN interface to receive an IPv6 address, an IPv6 gateway address and an IPv6 prefix from my ISP. As you can see, I’ve received a /64 IPv6 prefix starting with 2606. (Note, in the following screenshots, portions of the addresses may be blocked for my privacy.)
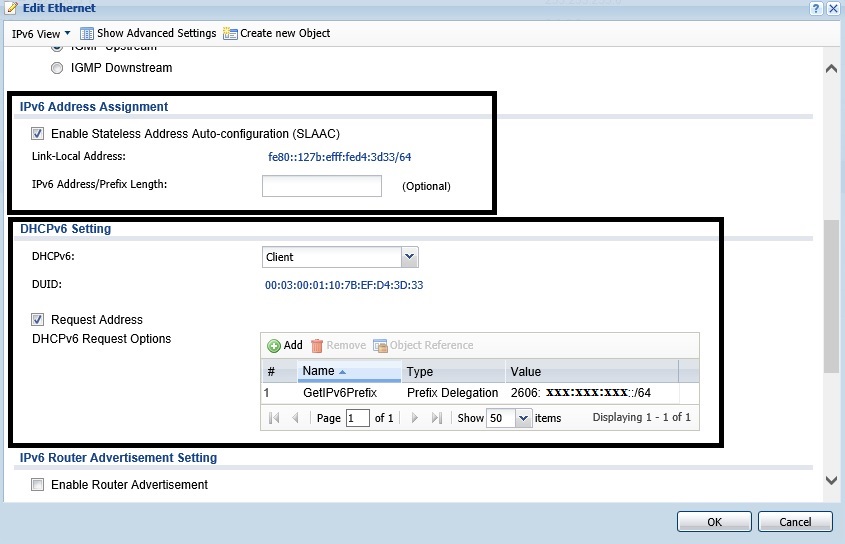
IPv6 WAN Config
I created VLAN5 on the USG40 for this example. For IPv4, I configured the USG40 using 192.168.5.0 for VLAN5. For IPv6, I statically addressed the VLAN5 interface with an IPv6 address of 2606:a000:1234:2222:5::1/80 and created a DHCPv6 address pool to assign 2606:a000:1234:2222:5::10 to 2606:a000:1234:2222:5::50 to PCs on VLAN5. (Note, the fields in the USG40 displaying the IPv6 address and IPv6 address pool aren’t large enough to display all digits at once, so I had to do some image editing.)
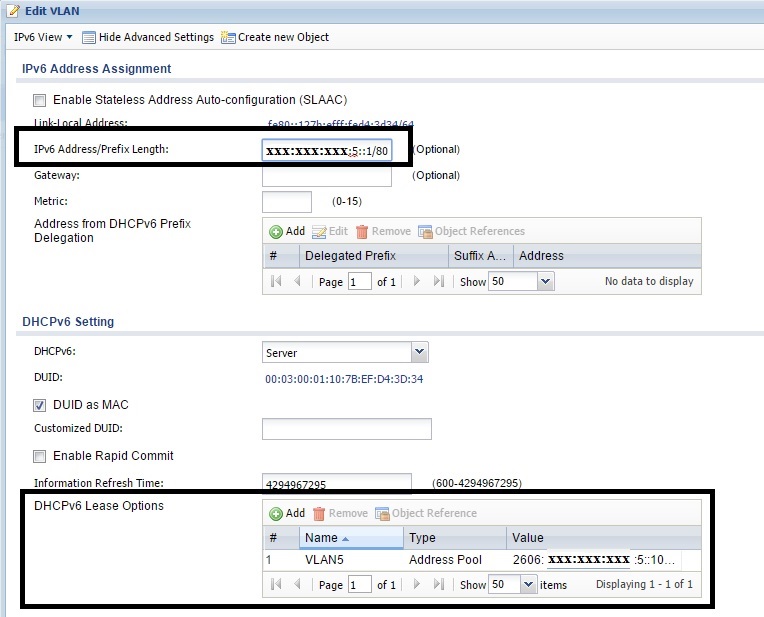
IPv6 VLAN Interface Config
With these configurations in place and connecting the USG40’s LAN port to a switch properly configured for VLAN tagging, devices connected to switch ports assigned to VLAN5 will get a 2606:a000:1234:2222:5::/80 IPv6 address and a 192.168.5.0/24 IPv4 address. The below screenshot shows the ipconfig output from a Windows machine connected to a switch port assigned to VLAN5. It has an IPv6 address of 2606:a000:1234:2222:5::10 and an IPv4 address of 192.168.5.50.
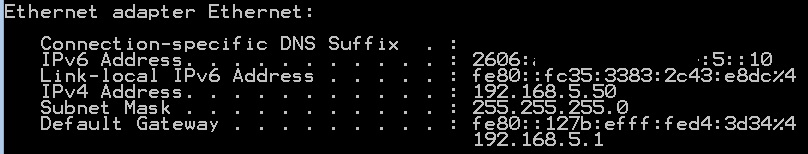
IPv6 and IPv4 on a PC on VLAN5
In putting this example together, I was surprised to find the Linksys LRT224 doesn’t support VLANs with different IPv6 prefixes. Linksys acknowledged this issue and is working on an software update. This quirk is another example where some IPv6 enabled routers may not have equal functionality for IPv4 and IPv6.
Conclusion
Most of us have a lot to learn to fully use IPv6. I hope this article has helped. I think you can see we’re pretty far from being able to turn off IPv4 and go IPv6 only on your LAN. While many routers now support IPv6 WAN connection, they may not handle IPv6 in all the places it needs to be including port forwarding, outbound service control, web filtering, VLANs and more. Dual-stack LANs will be with us for quite awhile.
