Introduction

| D-Link DI-604 ExpressEtherNetwork 4 Port Broadband Router | |
|---|---|
| Summary | Fast 4 port 10/100 switched broadband router with SPI-based firewall & street price around $40. |
| Update | 8/5/2002 – Corrected logging info. 7/30/2002 – Corrected performance test info. 7/8/2002 – |
| Pros | • Establishes a new price / performance point for SOHO routers • Faster than you’ll ever need • Lots of filtering / firewall features |
| Cons | • No traffic logging |
When I heard D-Link’s price of $49 for the DI-604, I’m sure I wasn’t alone when I thought that it would be some feature-crippled, slow-as-a-dog loss-leader that only folks who didn’t know better would buy. After spending some time with the 604, I’m glad to say that I couldn’t have been more wrong…
The Basics
The 604 is packaged in virtually the same case that their new DWL-900AP+ AirPlus Wireless Access Point [reviewed here] comes in. It’s about the size of a stack of three CD “jewel cases”, and has its status LEDs on the front panel, which are viewable from a wide range of top and front angles, and all connectors on the rear panel. The top of the cabinet is slightly sloped and not stacking-friendly, but has mounting features molded into the bottom, in case you wanted to wall-mount it. You get Link/Activity LEDs for each of the four LAN ports and single WAN port, and a Power light, too. D-Link throws in a normal UTP cable, printed Quick Installation Guide, CD with the PDF User Manual, and ZeroKnowledge bundle.
There’s no support for uplink capability, so you’ll need to depend on having it in whatever you use to expand the number of ports (if four aren’t enough), or use a crossover cable. The 604 also doesn’t support dialup modem or ISDN WAN connections, since it has only a 10BaseT Ethernet WAN connector.
Setting Up
The 604 is administered entirely via web-browser, including firmware updating (once you download the firmware file). Opening the router’s default address of 192.168.0.1 brings you to an opening screen (after you log in), where you can start an install wizard, or hit the controls directly.
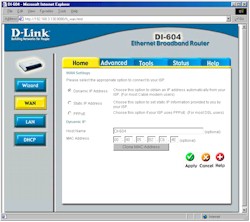
Figure 1: WAN Settings
(click on the image for a full-sized view)
The 604 comes with its LAN DHCP server enabled and its WAN side set to be a DHCP client, which may enough for some users. But it also lets you set the router’s Host Name or WAN MAC address (the two most common methods of non-PPPoE authentication) right on the Dynamic IP screen (shown in Figure 1 above). Selecting the other choices of Static IP or PPPoE change the screen to show the entries you’ll need for those connection types. I found everything in this section to be logically organized, with decent on-line help on each screen to help newbies through the rough spots.
The overall responsiveness was good with screens coming up quickly. Clicking the Apply button for each screen required only a second or so wait for a confirmation screen before you could move to the next settings screen.
An interesting admin feature is the admin and user level access, with different logins. Both let you see all the screens, but you have to be logged in as admin to change anything. Remote administration can be enabled (it’s off by default), and you can set the port and restrict access to a single IP address if you like. It’s also nice that you can either reboot the router, or force it to reload factory defaults (although these functions are curiously on two different screens) via the admin interface.
The 604 allows multiple administrator logins at a time and doesn’t provide any warning when an administrator joins the party. An omission is the fact that D-Link hasn’t provided any way to log yourself out of the admin interface, and there’s no time out either. The only way to “log off” is to quit your browser entirely (not just close the browser window that’s opened to the admin interface). I hope this gets fixed in a future firmware upgrade.
NOTE! There’s also a hardware reset-to-factory-defaults button on the back of the 604, but I found that if you followed the instructions in the manual, you will be forced to reload the firmware…which D-Link does not supply on the CD!
Just don’t remove power from the router and press and hold the button for 5 seconds to get the normal reset function.
One other thing. If there are still any Netscape 4.7X users out there, you’ll find problems viewing the admin screens. Switch over to Internet Explorer and all should be well. That’s about it for the basics. Let’s go check out the firewall’s features…
Firewall, Port Mapping, & Filters
There has tended to be a lot of confusion about the merits of NAT vs. SPI firewalls, and most vendors have priced their SPI-based products at a slight premium to their NAT-based products.
Given it’s extremely good bang for the buck, I think the 604 will basically put the nail in the coffin of the whole NAT-vs-SPI debate and expect we’ll soon see SPI used in all SOHO routers, with no more price premium.
I was, frankly, surprised that D-Link packed as many firewall features as it did into the 604, given its precedent-setting price point. Suffice it to say that the 604 has a very nice set of firewall features, and you’ll probably find that it will do what you need.
I’ve tried to show some of the key features in the screen shots below, but frankly, there are more features than I have the patience to create screen shots for! The only curious thing is the omission of Universal Plug and Play (UPnP) support, especially given that D-Link has been pretty aggressive in adding this to its new routers. UPnP’s NAT Transversal feature would be a nice complement to the 604’s flexible port forwarding features (even though I won’t be a UPnP convert until Microsoft addresses UPnP’s security issues).
I’m pleased to see that D-Link has added time controls to some of the filtering and port forwarding features. Even though you can only set one time period per feature, you can set the times for each filter set or virtual server separately, giving you some flexibility.
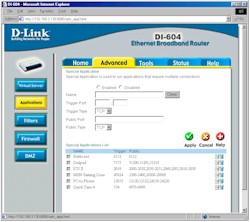
Figure 2: Applications Settings
(click on the image for a full-sized view)
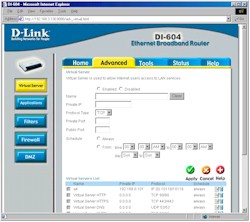
You can have ten single port to IP static mappings (Virtual Servers), and port ranges are handled separately via the Applications feature, which includes outbound triggers for dynamic port mapping. 20 Special Applications can be defined.
Figure 3: Virtual Server Settings
(click on the image for a full-sized view)
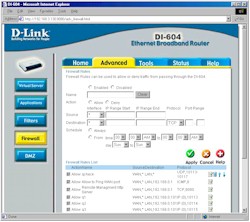
I was puzzled, though, by the inclusion of the Firewall Rules feature, since it can be confusing enough for those of us who have been messing with SOHO routers for awhile, let alone the first-time buyers who will be attracted by the 604’s price.
Figure 4: Firewall Settings
(click on the image for a full-sized view)
The manual isn’t much help in explaining when you use a firewall rule and when you use an IP filter, other than saying that “It works the same way as IP Filters with additional settings”.
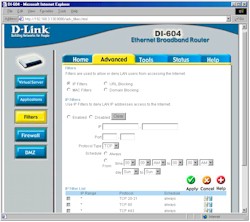
Figure 5: IP Filter Settings
(click on the image for a full-sized view)
VPN
If you need to connect to your office’s Virtual Private Network, the 604 can support 50 IPsec, 20 PPTP, and some number of L2TP pass-thru sessions. Sessions can be simultaneously established to multiple remote VPN gateways, too. Mapping of LAN based VPN servers for all three VPN protocols is also handled.
Note also that you can enable/disable VPN pass through for IPsec and PPTP protocols. Curiously, there’s no enable control for the L2TP VPN protocol that’s also supposed to be supported, so I’ll assume that it’s always on.
Logging and other Features
Given the firewall features that D-Link packed into this thing, I was surprised at the logging capability that was included. D-Link stresses the parental control capabilities of the 604, but doesn’t include logging of plain old network traffic, i.e. websites, FTP servers, etc. They log pretty much everything else, however, and you can view and clear the logs via the admin pages. The only way to save the logs is to manually email them (sorry, no scheduled emailing or “hack” email alerts), but since the log entries are limited (the oldest entries just roll off into oblivion), the entries you want may be gone by the time you remember to go get them.
Update 8/5/2002 – A helpful reader pointed out that the 604 automatically emails the log when it fills up, provided you fill in your SMTP server and email address info on the Status > Log > Log Settings page. The log holds a maximum of 200 entries (20 pages, 10 entries each).
Let’s see, what else is there…?
- there’s a real-time clock that automatically syncs up to an NTP server (you have to manually set your time zone and Daylight savings information)
- you can save and load the router’s configuration to a file on your computer
- you can set the router to discard ping requests (disabled by default).
 If you want your 604 to be invisible to port scanners, you’ll want to click on the “Discard PING from WAN side” radio button on the Tools > Misc. screen.
If you want your 604 to be invisible to port scanners, you’ll want to click on the “Discard PING from WAN side” radio button on the Tools > Misc. screen.
Routing Performance
Testing Notes:
• WAN to LAN tests are all run with LAN endpoint in DMZ
• LAN to WAN tests are run with LAN endpoint not in DMZ, except UDP Stream
No, that’s not a typo in the throughput results. Both Qcheck and Chariot confirm that this sucker really does run at about 15Mbps!! Although this is really a… ahem… matching of manhood type of number, and speed far beyond that of your puny little “broadband” connection, it’s unprecedented for any routing product that I’ve ever seen.
I personally think this is mainly D-Link’s way of making a point to its competitors vs. providing a product benefit that’s really going to make a difference to 99.9% of the people who will buy this product! Don’t get me wrong, this is impressive performance! But as I said, since most broadband connections run at 1.5Mbps MAX (on a good day, with following wind, no sunspots, etc.), they’ll have a hard time using a tenth of the 604’s horsepower!
Update 7/2/2002 – I found a problem with the Qcheck endpoint that was causing the UDP streaming tests to fail in both directions. After I corrected the problem, the tests showed results in both directions were just ducky!
Update 7/30/2002 – The Performance test results have been republished, using a new test method for SPI+NAT routers. This has dropped the top LAN to WAN measured speed slightly and significantly lowered the WAN to LAN speed.
LAN to WAN test results with the LAN endpoint in DMZ are:
- Throughput – 2.9Mbps
- Response Time – 279mS avg / 346ms max.
For more information on the new test methods, read the “How we Test” page linked above, and the SMC 7004VBR review Performance section.
Routing Performance Test Results
| Test Description | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
|---|---|---|---|---|
| Throughput (kbps) | Lost data (%) | |||
| WAN – LAN | 2.9 | 275 (avg) 349 (max) |
499 | 0 |
| LAN – WAN | 13.6 | 58 (avg) 109 (max) |
501 | 0 |
| Firmware Version | V1.1 30 May 2002 | |||
See details of how we test.
BAM!!
What can I say? Just as Linksys set the bar a few years ago with their flagship BEFSR41 “Linky” router, D-Link is now lowering the boom on the SOHO router industry with the DI-604. I mean, given all they’ve packed into this little silver box, who’s gonna pay more than $50 ($38 from some on-line retailers at the time of this review) for a non VPN endpoint router any more?
I’m always reluctant to fully endorse a product until it’s had a little marketplace “aging”, especially given all the different broadband systems with all their particular quirks. But if D-Link has done their homework (and especially their testing) correctly, you’re not gonna pay a lot for a SOHO router any more!