Introduction
Updated 11/18/2009: Added more VPN throughput test results.

| At a Glance | |
|---|---|
| Product | SonicWall Internet Security Appliance (TZ100W) |
| Summary | Relatively low cost multi-function UTM device |
| Pros | • High UTM and VPN Throughput • Flexible configuration options • Dual WAN capability • Stable • SSL and IPsec VPN |
| Cons | • No Gigabit ports • Menus could be better organized • SSL VPN installation can be challenging |
The white plastic cover and simple design of the SonicWall TZ100W give the impression of just another wireless gateway router. But don’t judge this book by its cover, since the TZ100W has a lot more than meets the eye!
The SonicWall TZ100W is a Unified Threat Management (UTM) device with the ability to securely manage complex networks and the horsepower to handle the traffic loads efficiently. In addition to wired and wireless network functionality, the TZ100W provides Anti-Spam, Content Filtering, Anti-Virus, Intrusion Detection and Prevention, Anti-Spyware, SSL and IPSec VPN services along with a powerful firewall.
SonicWall’s TZ line has been revamped for 2009, replacing previous models including the TZ180 and the SonicWall TZ190W I reviewed a few years ago. The newer TZs are designed to provide a significant upgrade in performance “maximize the highest speeds available from modern ISPs while delivering full UTM protection,” according to the SonicWall spec sheet.
Under the Covers
The case on the TZ100W is a white plastic housing measuring 6.3” wide x 5.6” deep x 1.5” high with two large popsicle stick shaped wireless antennas in the back. The actual indicator lights are on the top front edge of the device as shown in Figure 2.
The TZ100W runs on a 64-bit 300Mhz CPU from Cavium Networks. Along with this processor, the TZ100W has 128 MBof RAM and 16 MB of flash memory. The board is shown in Figure 1.
Figure 1: TZ100W main board
There is an Atheros AR9160 chip visible on the Wi-Fi radio board. This is the BB/MAC for the AR9100 chipset. There are three antenna terminals on the board, which indicates that the radio chip is probably an AR9132 3X3. Note that only two antenna connects are used.
The CPU is passively cooled with the heat sink shown in the lower right of Figure 1. I noticed the heat sink gets pretty warm to the touch. There is a small cooling fan on the right side of the board that exhausts heat through ventilation holes on the top of the case.
Fan noise was never an issue with my test unit. SonicWall told me that the cooling fans in their TZ products are controlled by ambient temperature, thus they only run when the temperature reaches a certain threshold. With the case open (which would help the device run cooler) and the device turned on, I could see the fan wasn’t even running.
In the back of the TZ100W (Figure 2) are the five 10/100 Ethernet ports, a pair of detachable antennas for the 802.11b/g/n radio, and the power connector. Also on the back is a serial console port for device management.

Figure 2: TZ100W rear view
I think the TZ100W should have Gigabit Ethernet ports. When I asked SonicWall about this, they replied that the more expensive models in the TZ line have Gigabit Ethernet ports. But to keep the cost down on the TZ100W, they equipped it with only 10/100 Ethernet ports. In my mind, SonicWall went half way on this one. They equipped the TZ100W with the latest 802.11n wireless network capability, why not the latest wired network capability?
Configuration
The TZ100W is a multi-function device, with a tremendous number of configurable options. The SonicWall Operating System (OS) has 12 main menus, each with 2-15 submenus, for a total of 82 different configuration pages! The menus are all available via a Web GUI and are relatively intuitive. To help understand the configurable options, there is a 1085 page manual available on SonicWall’s website.
I like SonicWall’s use of Address Objects, which can be single IP addresses, ranges of IP addresses, subnets, MAC addresses and Domain names. With Address Objects, you assign names to each address, which makes network management easier. Further, Address Objects are reusable throughout the SonicWall configuration pages, providing useful configuration flexibility.
For example, to control wireless access by MAC address, you create an Address Object for each allowed client MAC addresses. Then, you create an Address Group which includes all the Address Objects you created. Last, you configure wireless MAC security to point to your Address Group.
In Figure 3, I created an Address Group called Allowed MACs which contains the Address Objects Doug Laptop and Doug Laptop2. The value of the Address Group and Objects is they remain in the configuration even if I disable wireless MAC security, allowing me to easily re-enable wireless MAC security to the same list of MAC addresses.
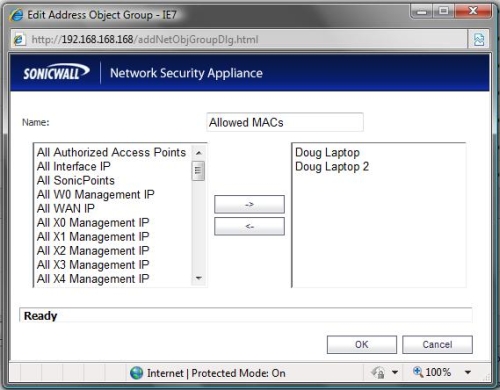
Figure 3: Address Objects and Groups
Even with the use of Address Objects and Wizards, there are still 82 different configuration pages. Perhaps through the use of the Wizards and default values, the TZ100W can be managed by non-technical people. But I think the multitude of options and configurations require some networking knowledge and experience to fully optimize this router.
I think SonicWall could do a better job organizing the menus. Several submenus seem to be misplaced. For example, there is a Security Dashboard submenu in the System menu, displaying information about viruses, intrusion prevention, and spyware. However, configuring anti-virus, intrusion prevention, and anti-spyware is in the Security Services menu. Why not put the Security Dashboard in the Security Services menu?
Many of the menus have a status display. But in some of the menus, the status display is the first option, while in others, the status display is the second option and in still others it is named differently, such as Call Status or Station Status. I suggest making the menus consistent by placing a status display as the first choice in each main menu. Another issue is there is menu duplication with both the RBL Filter menu and Licensing information. These menu issues may be minor, but for overall ease of use, they make a difference.
Networking
To understand the TZ100W’s network options, you have to understand SonicWall’s use of ports, interfaces and zones. Physically, the TZ100W has five 10/100 Ethernet ports. Those five ports can be configured in three different port assignment schemes as shown in Figure 4.
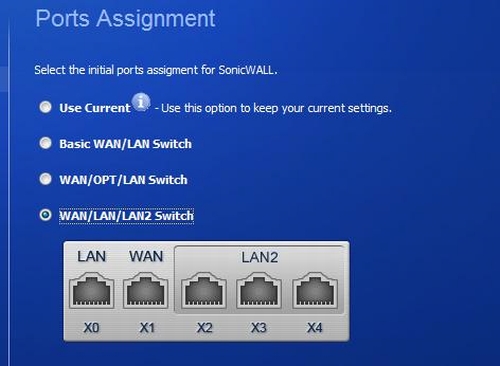
Figure 4: Port Assignment
The first port assignment scheme results in a single WAN port and four LAN ports. The second port assignment scheme results in dual WAN ports and three LAN ports. The third port assignment scheme, labeled in Figure 4 as WAN/LAN/LAN2 Switch, results in a single WAN port, one LAN port, and three LAN2 ports. There are options to further customize the port assignments via the Port Shield menu, but with only five ports, these three options should be good for most small networks.
Ports are associated with interfaces on the router. IP addresses, routing and DHCP pools are applied by interface, not ports. Depending on the chosen port assignment scheme, there will be one to four ports associated with each interface on the router. For example, in the third port assignment scheme shown above, ports X2-X4 are associated with the LAN2 interface.
The third port assignment scheme is a “poor man’s VLAN.” When enabled, this scheme separates the LAN ports into two VLANs called LAN and LAN2. This scheme doesn’t support 802.1q VLANs, but it does allow for running two separate LANs with true network broadcast separation.
Zones are how firewall and security features are managed on the TZ100W. Each interface is assigned to a zone, and there are seven default zones: LAN, WAN, DMZ, VPN, SSL VPN, MULTICAST, and WLAN. Additional zones can be added for customization.
Once you get the hang of it, the concept of ports assigned to interfaces and interfaces assigned to zones makes sense. It also is necessary for configuring security. Security on the TZ100W is managed by defining which traffic flows are permitted between zones, and which security features are enabled in each zone. Security features include content filtering, anti-virus, anti-spyware and Intrusion Prevention Service (IPS). I’m going to cover the security features in more detail shortly.
Back to the three port assignment schemes, the second port assignment scheme allows for dual WAN ports with options for load balancing and failover. I found that failover worked almost instantly on the TZ100W using the default configurations. I connected the primary and optional WAN ports to two different Internet connections and disconnected the Ethernet cable on the primary WAN port. Within seconds, I could access the Internet again from a PC connected to a TZ100W LAN port. Restoral was equally quick. Upon reconnecting the primary WAN port, a traceroute showed traffic was again flowing through the primary.
As I’ve stated in past reviews, I highly recommend routers with dual WAN ports for anyone that relies on Internet connectivity for revenue, communications or productivity. To utilize dual WAN ports you have to subscribe to two different ISPs, but the TZ100W’s load balancing options allows the use of both connections, maximizing your bandwidth when both ISPs are up.
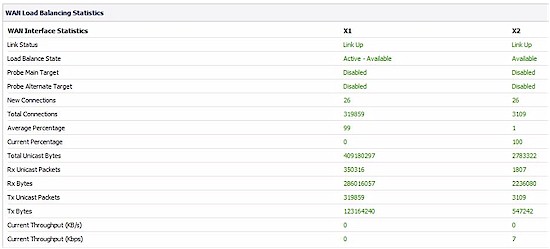
Load balancing configuration options are Round-Robin, Bandwidth-based and Percentage-based. Round-Robin equally distributes utilization between WAN ports, Bandwidth-based sends a fixed bandwidth amount of traffic out one WAN interface with the remaining going to the other, and Percentage-based sends a percentage of traffic out one WAN interface with the remaining going to the other. Traffic statistics on each WAN port’s utilization are available in the Load Balancing menu as shown in Figure 5.
Figure 5: Load balancing
Wireless
Wireless client security options include WEP, WPA, WPA-2 and MAC address filtering. For much of my testing, I was connected to the TZ100W via the wireless interface, and I had no issues with dropped connections or poor performance.
The TZ100W has Wireless Intrusion Detection Services (IDS) which will detect other Access Points, a nice feature for network administrators trying to control internal users from enabling their own Access Points. As you can see in Figure 7, my test TZ100W detected five other Access Points nearby.
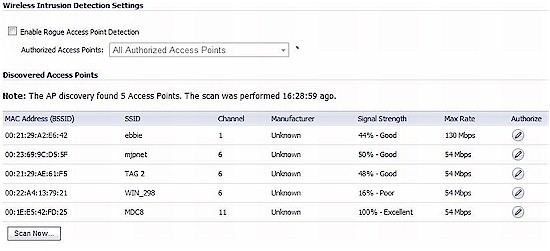
Figure 6: AP Discovery
To expand the physical range of a wireless network, SonicWall Access Points, called SonicPoints integrate directly with the TZ100W, allowing for expanded network coverage with centralized network management.
Wireless networks are a security risk. The TZ100W separates the wireless network into a different security zone than the wired networks. Security features can be enabled or disabled for the wireless clients, just as with the wired clients, they just need to be applied to the WLAN zone.
By default, the WLAN zone is considered Untrusted, which means wireless clients can’t access devices on the LAN unless rules are created in the firewall to enable them. I’ll cover firewall rules shortly.
Anti-spam
The TZ100W is a Unified Threat Management (UTM) network device designed to provide an array of security functions at the core of a small network. In addition to a complex firewall, the TZ100W provides Anti-Spam, Real-time Black Listing, Content Filtering, Gateway Anti-Virus, Intrusion Prevention, and Anti-Spyware.
Detailed testing of these security functions require sophisticated tools. Subsequently, many UTM manufacturers submit their devices to third party organizations, such as AVTest.org. SonicWall is not one of those manufacturers, however. I did run some limited checks of the TZ100W’s UTM features. But I think it would be good if Sonicwall submitted its product for independent Anti-Virus and malware effectiveness testing.
SonicWall’s “Comprehensive” Anti-Spam feature is a server based tool, designed to work with an Exchange or other SMTP email server. To enable and configure the Anti-Spam tool, you have to enter the local IP address of your email server. Once configured, the Anti-Spam tool will filter email at the network level, giving you the option to Tag, Store, Reject, or Delete emails detected as Spam.
SonicWall’s Anti-Spam service uses the Global Response Intelligent Defense (GRID) Network, which it has expanded since its acquisition of MailFrontier in 2006. Essentially, when a user connected to the GRID network marks an email as Spam, the information about the email sender, its content, and associated links are uploaded to the GRID, enabling devices such as the TZ100W to block this newly identified source of spam.
If you don’t have your own Email server, the TZ100W blocks spam through the use of Real-Time Black List (RBL) services. The RBL feature works by comparing the source IP address of an email to lists of known spammer IP addresses and dropping the matches. Connections to two well known RBL providers, spamhaus.org and sorbs.net, are enabled by default. Additional Black List services can be added. Note, however, that the TZ100W does not filter spam based on actual analysis of email content or via heuristics.
The value of blocking Spam at the mail serverl is improved network and PC performance. Blocking the spam before it enters your network improves bandwidth on the LAN, as well as frees up LAN PC processors from filtering Spam independently. The Anti-Spam features are managed directly through the Anti-Spam menu.
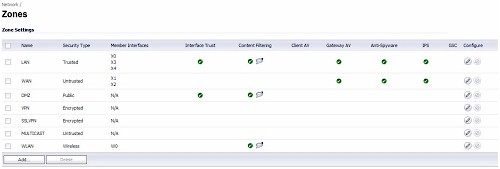
The rest of the TZ100W security features are enabled or disabled by network zones. As you can see in Figure 7, I’ve enabled Content Filtering on the LAN, WAN and WLAN zones. Further, I’ve enabled Gateway Anti-Virus, Anti-Spyware, and Intrusion Prevention on the LAN and WAN zones.
Figure 7: Zones
Content Filtering
Content filtering on the TZ100W can be configured via policies to block up to 56 different categories of content leveraging a database of “millions of URLS, IP addresses and domains” maintained at worldwide SonicWALL facilities.
I can tell you this, if you create and apply a policy that blocks all 56 categories, you might as well turn off your computer. With the default policy blocking all 56 categories, I received the message shown in Figure 9 just surfing to Yahoo.com and couldn’t find a web page I could access.
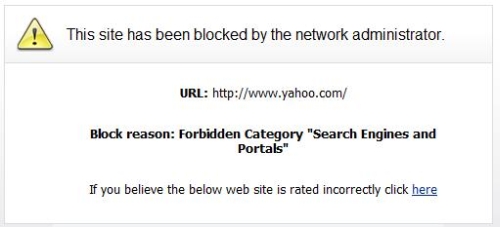
Figure 8: Content Filter block message
I found the last filtering category, “Not Rated” to be useful. If you’re worried SonicWall’s database isn’t complete enough, filtering unrated websites will block all websites not found in the SonicWall database. Finally, in the event a blocked site should be permitted, the TZ100W has a custom list feature, allowing for adding allowed or blocked domains as well as keyword blocking.
Although the SonicWall Content Filtering was effective in blocking rated websites based on selected categories, like most other content filters I have tested, it wasn’t difficult to defeat. With the category pornography selected for content filtering, the TZ100W blocked browsing to adult sites. However, simply typing “porn” in a search on Yahoo.com and clicking the images option presented adult images that should have been blocked.
Anti-Virus
The TZ100W uses two levels of anti-virus protection: client-based and gateway. The Client Anti-Virus feature enforces the use of Anti-Virus software on all computers in each selected zone. Computers that don’t have the required Anti-Virus software will receive the message in Figure 9 when they try to use the Web. Clicking on the Install VirusScan link will direct users to install McAfee Anti-Virus software. My test TZ100W came with five licenses for the Client Anti-Virus feature.
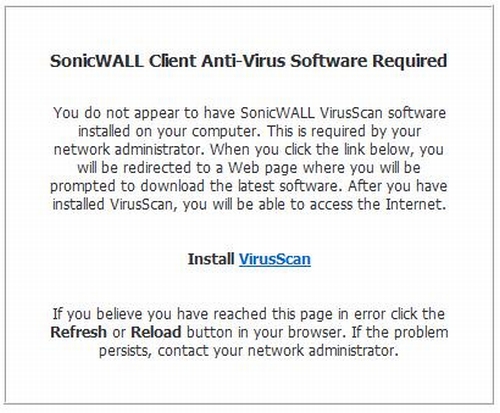
Figure 9: Client AV message
The Gateway Anti-Virus (GAV), Intrusion Prevention (IPS), and Anti-Spyware features provide centralized filtering of viruses, malware, and other undesirable programs and files that can infect a network via email, downloads or web surfing. As with the Anti-Spam feature, the value in centralized filtering is improved LAN and PC performance.
All three of these features are individually enabled by zone with multiple configuration options in their own submenus. These features all communicate with the SonicWall security network to keep a current database of security threats and signatures.
The GAV feature works by inspecting files as they enter the network and comparing them to a dynamically updated database of virus signatures. SonicWall’s documentation states this database, as well as the database for the Anti-Spyware feature, is maintained by their own “SonicAlert Team,” third-party virus analysts, open source developers and other sources. The TZ100W does the work for you and automatically checks for signature updates every hour. There is also an Update button allowing an administrator to manually trigger a database update.
SonicWall employs a four layer approach with its GAV service. Both incoming and outgoing emails are scanned for known virus signatures. Infected incoming emails are blocked, and infected outgoing emails are deleted. The GAV feature also filters HTTP downloads for known virus signatures and discards infected files. Last, since the GAV filtering is performed at the router level, emails destined for an internal email server are also filtered.
A simple test for checking network Anti-Virus protection is available at eicar.org. This site has safe test files available for download that should trigger Anti-Virus protection, but are not viruses. I tried downloading one of the files from eicar.org with GAV enabled and received the alert shown in Figure 10, verifying the TZ100W had done its job.
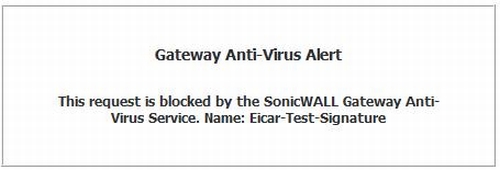
Figure 10: Gateway AV alert
My test TZ100W’s IPS feature listed 48 different categories of attacks that it inspects in traffic flows. The key to the IPS security feature is it inspects packets at the application layer instead of just at the IP or Protocol layer where most firewall activity occurs. Further, SonicWall’s IPS feature monitors network activity, looking for anomalies indicative of a network attack.
To run a basic test, I launched a port scan from another network at the WAN port of the TZ100W to see how it would be handled by the router. Figure 11 shows the log messages generated within the TZ100W, showing the TZ100W successfully detected the external port scan activity.
Figure 11: IPS log messages
There are three levels of IPS settings on the TZ100W, I had my test device set to detect High, Medium and Low Priority attacks for test purposes. Flagging Low Priority attacks is probably overkill, as the TZ100W flagged outgoing update activity from a SonicWall’s CDP device with a Low Priority alert, erroneously identifying the activity as a possible IPS threat.
The TZ100W Anti-Spyware works by monitoring ActiveX components in browsers, scans emails and network traffic for recognized spyware signatures, blocks outgoing spyware traffic from leaving the network, and enables administrators to control network based program installation. As with the GAV feature, the key is the constantly updated database of signatures identifying known malware.
Firewall
The TZ100W firewall rules are created in a nice matrix style display. Rules are defined based on source and destination zones, source and destination objects, and various pre-defined or custom services. By default, the firewall allows all traffic from the LAN to the WAN and blocks all traffic from the WAN to LAN. Further, Quality of Service (QoS) controls can be applied in firewall rules to each service as it flows from one zone to another.
Port Forwarding, or opening a port in the firewall and directing a traffic flow to specific service inside the network isn’t in the firewall menu on the TZ100W, but in the Network menu under NAT Policies. For example, I created a customer service called “iperf” for TCP traffic on port 5001. Then, I set up the following NAT Policy to forward WAN-LAN iperf traffic flows to my laptop as shown in Figure 12.
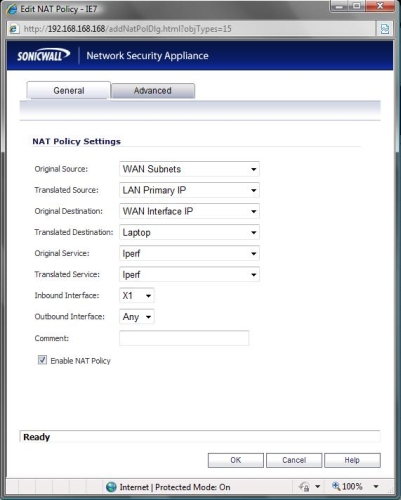
Figure 12: Port forwarding NAT Policy
VoIP
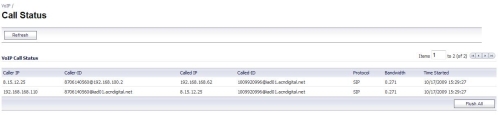
Voice over IP is a common network traffic flow, and the TZ100W is designed to detect both SIP and H.323 VoIP traffic. The TZ100W will detect SIP or H.323 based VoIP traffic on your network and display calls in progress as shown in Figure 13. The TZ100W does not recognize proprietary VoIP protocols, or some of the more common protocols such as MGCP or Cisco’s “skinny” (SCCP) protocol.
Figure 13: VoIP call status
The TZ100W also has a SIP Application Layer Gateway (ALG) function, labeled as “SIP Transformations” if your VoIP provider requires an ALG for connectivity. The SIP Transformations feature will change the source IP address in a SIP message to match the external IP address of the router, making it easier to connect VoIP calls over the Internet.
VPNs
The TZ100W offers three VPN options, SSL Client-to-Site tunnels, IPSec Client-to-Site tunnels and IPSec Site-to-Site tunnels. All the standard IPSec encryption algorithms are supported, including DES, 3DES, AES-128, AES-192, and AES-256.
I prefer SSL VPN tunnels for client solutions. Typically, SSL VPN clients are easier to install, configure and manage for the end users. Enabling SSL Client-to-Site functionality on the TZ100W is a matter of defining user names and passwords for SSL authentication, specifying a range of IP addresses for SSL clients, and defining which subnets could be accesses over the SSL tunnel.
The SonicWall SSL VPN solution is called NetExtender, with versions for Windows XP Home and Professional, Windows Vista 32-bit and 64-bit, Windows 2000 Pro and Server, Windows 2003 Server, MAC and Linux. The SonicWall product team tells me the NetExtender software will also work with the Windows 7 64-bit.
NetExtender has versions for the MAC and Linux, too. The MAC version requires MacOS 10.4 or higher and the Linux version runs on Fedora 3 or higher, Ubuntu 7 or higher, and OpenSUSE.
NetExtender worked great for me on XP Pro, I logged on to my TZ100W and installed the software per the instructions in the manual. Once installed, launch the NetExtender icon, enter your user name and password, click connect, and you’re remotely connected to the TZ100W as shown in Figure 15.
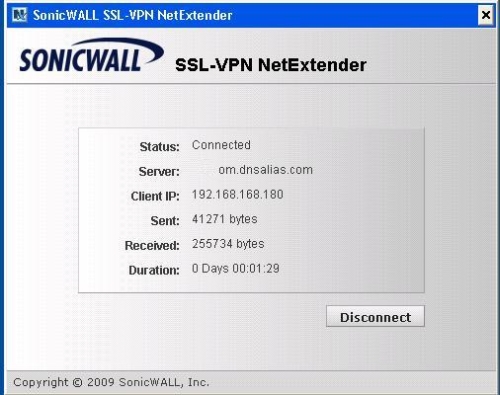
Figure 14: SSL VPN
But I couldn’t get NetExtender to work in Windows 32-bit Vista. I tried installing the software directly from the TZ100W and from mysonicwall.com, but in both cases it failed. In fairness to SonicWall, this might be a problem with my Vista PC which has had so many VPN clients installed and uninstalled, I think it is time for a fresh OS. I’m encouraged to hear that NetExtender works with Windows 7 64-bit, which I plan as my next OS.
I was also able to install NetExtender on an Ubuntu 9.04 Linux PC. It wasn’t as easy as with XP Pro, and I had to download the Linux client from mysonicwall.com instead of directly from the TZ100W, but it worked.
If you prefer an IPSec Client-to-Site solution, SonicWall offers Global VPN Clients for 32-bit and 64-bit Windows XP, Vista and 7. The Global VPN Client software is available for download along with firmware updates, support documentation, and other resources at mysonicwall.com.
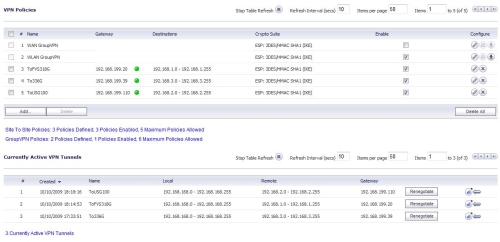
The TZ100W will support up to five IPSec Site-to-Site VPN tunnels. I managed to configure and run three tunnels simultaneously as shown in Figure 15 from the TZ100W to a NETGEAR FVS318G, NETGEAR FVS336G, and Zyxel USG100.
Figure 14: Three IPsec tunnels
I found configuring IPSec Site-to-Site parameters on the TZ100W straightforward. I used the menu to set up 3DES tunnels. There is also a VPN Wizard to simplify the configurations.
VPN throughput is limited by the speed of the slower router, so I tested throughput from the TZ100W to the fastest of my three routers, the Netgear FVS336G. Using standard iperf TCP throughput tests, I measured 11.9 Mbps throughput between the TZ100W and the FVS336G, which is the FVS336G’s throughput limit.
SonicWall rates the TZ100W with a maximum VPN throughput of 75 Mbps. Thus, if both ends of the VPN tunnel are TZ100W routers and there is enough bandwidth between them, the throughput over the tunnel could reach 75 Mbps. But since Sonicwall sent only one TZ100W for review, I couldn’t verify the 75 Mbps claim.
Updated 11/18/2009: Added more VPN throughput test results.
After the review published, it occured to me that I could have tested VPN performance also with clients. So I went back and tested VPN throughput using both the SSL and IPSec client solutions.
I first ran three standard iperf TCP throughput tests between a Windows XP PC and a Windows Vista PC connected via Gigabit switch to establish a baseline. I then left the Windows XP PC on the Gigabit switch and moved the Windows Vista PC behind the TZ100W, with the TZ100W’s WAN port attached to the Gigabit LAN. I then used SSL and IPSec VPN clients on the Windows XP Pro PC to connect to the Windows Vista PC on the TZ100W’s LAN.
The table below shows a summary of the three tests.
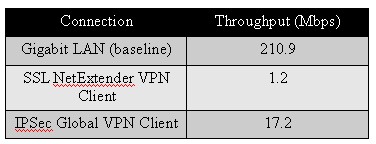
VPN client-based throughput
The first row of the table shows that my two PCs can pass data at 210.9 Mbps when they are both on a Gigabit LAN. The second row of the table shows the SSL VPN Client throughput at 1.2 Mbps. Although low, I wasn’t too surprised with this measurement for the SSL VPN Client since SonicWall’s claim of 75 Mbps is for IPSec 3DES throughput, not SSL throughput.
The third row of the table shows 3DES IPSec VPN Client throughput at 17.2 Mbps. This result was surprising because it’s very far below Sonicwall’s claimed performance. When this data was shared with Sonicwall, however, they reminded me that the 75 Mbps spec is between two TZ100’s and using UDP, not TCP/IP. Sonicwall has no spec for client to TZ100 VPN throughput.
So Sonicwall is sending me a second TZ100 so that I can test VPN performance between them and they are in the process of verifying my client-to-TZ100 results. I’ll update this review again when we have those results.
Logging and Reporting
Activity on the TZ100W is logged and stored locally, with the option to send syslog data to an external server. Logs are recorded in 8 different priorities and 68 different categories, and can be filtered and viewed by priority, category, or source/destination IP or interface. Further, log messages can be sent via email to alert an administrator of any issues on the network or router.
There are also three reports available providing a nice snapshot of end user network activity, showing the top 25 most frequently accessed Web sites, the top 25 users of bandwidth by IP address, and the top 25 services consuming the most bandwidth.
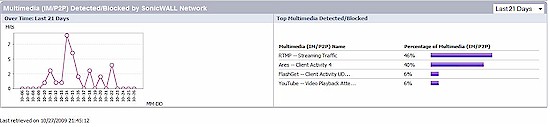
The System Security Dashboard, a feature I covered in my review of the TZ190W, provides a display of Viruses, Intrusions, Spyware, and Multimedia activity detected by the Global SonicWall network, as well as your individual device. Figure 17 shows the amount of multimedia activity detected by my test TZ100W.
Figure 15: Security Dashboard display
Performance
SonicWall told me that their #1 goal for the new TZ series is performance, which I found was a weak spot on the TZ190W I reviewed several years ago.
Both the TZ190W and the TZ100W use Cavium Networks CPUs, but the TZ100W uses Cavium’s newer 300 MHz 64-bit Octeon Processor over the TZ190W’s Nitrox processor. In my testing, it appears this Octeon processor is a significant improvement over the Nitrox processor.
SonicWall’s goal for the TZ100W is to maintain 30-50 Mbps of throughput with the UTM features enabled between separate zones. To test this, I ran iperf TCP throughput tests in both directions between the LAN and WAN zones and compared the results to those I measured in my review of the Zyxel USG100.
As you can see in the column labeled UTM ON in Table 1, the TZ100W ran 31.2 – 31.4 Mbps throughput between the LAN and WAN zones. By comparison, throughput on the Zyxel USG100 with all UTM features ON was only 16 – 17 Mbps. Further, in the column labeled UTM OFF in Table 1, the TZ100W’s throughput was between 71 and 87 Mbps.
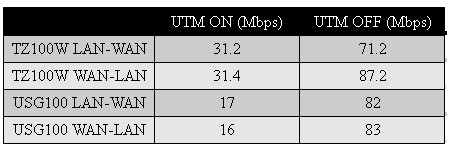
Table 1: Routing Throughput
Closing Thoughts
I asked SonicWall to name the main competitors to the TZ100W, and they listed the Fortinet 30B and Watchguard X55E. I haven’t had the opportunity to review these two devices, so I poked around their websites a bit.
Neither of these products appears to fully match up with the TZ100W. Fortinet’s website rates the 30B with only 10 Mbps of throughput for a key UTM feature, Anti-Virus filtering. The Watchguard X55E seems a bit more comparable to the TZ100W, but its wireless network only supports 802.11b/g, not 802.11b/g/n and its VPN throughput is rated for a maximum of 35 Mbps.
The previous UTM devices I’ve reviewed include the SonicWall’s TZ190W, the D-Link CPG310, and the Zyxel USG100. The TZ100W replaces the TZ180W, which was a step below the TZ190W. Still the TZ100W is a significant boost in performance over both the TZ180 and TZ190 as both were only rated for up to 10 Mbps UTM throughput.
Further, the TZ100W outclasses all three of these devices I’ve reviewed with a 3DES VPN throughput rating of 75 Mbps. Even the 11.9 Mbps 3DES VPN throughput I measured far outclasses the TZ190W, CPG310 and USG100’s 1-1.5 Mbps 3DES VPN throughput.
Conspicuously absent from Sonicwall’s list of competitive products is NETGEAR’s new UTM10, which is aiming squarely at the same market as the TZ100W is. I’ll be reviewing it shortly and it will be interesting to see how NETGEAR has approached the challenge of creating a low cost, high performance UTM.
The list price on the TZ100W is $295.00, which is a pretty amazing price point for all the features this router includes. Take a look at Table 2 showing the latest pricing information from Pricegrabber on the Fortinet, Watchguard and Zyxel routers. I didn’t list the CPG310, since that product reached end of life on 8/1/09.
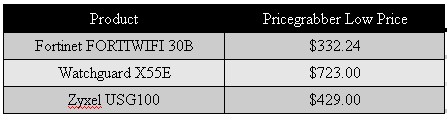
Table 2: Competitive pricing summary
The security and support services for the TZ100W are subscription based, so buying the router for $295 isn’t the final tally. Below are SonicWall’s list prices on 1 year subscriptions for the key features of the TZ100W. Longer term subscriptions and bundles provide discounts, but Table 3 below should give you a good understanding of the costs.
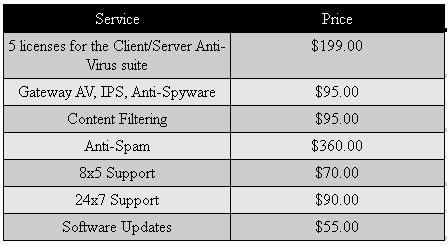
Table 3: TZ100W Option pricing
As you can see, the subscription fees for the key UTM features on the TZ100W add up to hundreds of dollars per year. But when you consider that network security has become a key priority for our government, and is a growing concern for all networks connected to the Internet, the cost becomes more palatable.
In a recent article from the Associated Press, former national intelligence director Michael McConnell stated the Internet “is the soft underbelly” of the U.S. today. Speaking at a new cybersecurity exhibit at the International Spy Museum in Washington, McConnell said the Internet has “introduced a level of vulnerability that is unprecedented.”
The article goes on to recommend several key security steps to protect against the threats our networks face every day. Those steps include Anti-Virus solutions, spam filters, parental controls or content filters, regular backups, and thinking twice before sending information over the Internet, “particularly when using wireless or unsecured public networks.”
I found the SonicWall TZ100W, along with SonicWall’s CDP 110 for regular backups, provides a nice solution for all these key security steps and I liked the TZ100W’s flexible port options and configuration capabilities. The TZ100W’s stability and performance are also significantly improved over SonicWall’s previous UTM products. And kudos to SonicWall for hitting their goal on performance numbers; the TZ100W has the best UTM and VPN performance levels of any router I’ve tested to date. In summary, for small networks looking for an affordable Unified Threat Management solution, the TZ100W has everything you need.