Introduction
Updated 5/23/2011 – RV220W info corrected. EPS AV feature clarified

| At a Glance | |
|---|---|
| Product | ZyXEL Unified Security Gateway (USG20) |
| Summary | Business class router with Gigabit ports, IPsec and SSL gateways, one-to-one NAT, bandwidth management and more |
| Pros | • Endpoint Security checking • Free Anomaly Detection • Flexible Network Options • Multiple information and report options |
| Cons | • Manual lacks examples • Limited number of VPN tunnels |
In this review, I’m going to cover Zyxel’s USG20 security router. This small network security device has quite a few networking and security options. Although the USG20 isn’t a full Unified Threat Management (UTM) device because it lacks anti-virus and intrusion detection and prevention, it provides some excellent security and networking features.
I looked at Zyxel’s USG100 UTM device a couple years ago, and the USG20 shares a lot of its functionality. So I’ll refer to that review periodically. The USG20 isn’t just a refresh of an older device, though. The USG20 introduces some new features. Note that Zyxel also offers the USG20W that includes a wireless AP.
Physically, the USG20 is a desktop device, measuring 8.25” (W) x 5.5” (D) x 1.25” (H). It does not have rack mounting options. There is an internal fan which is audible, but I didn’t find it any more offensive than the fan in my laptop.
The front of the device (Figure 1) has the device’s indicator lights.
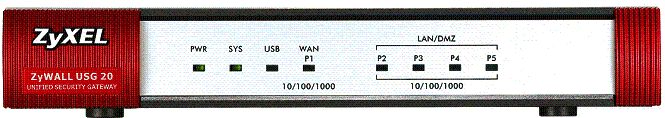
Figure 1: USG20 Front Panel
The rear of the device (Figure 2) has the physical Ethernet ports, a console port, USB port, reset button and power connector.
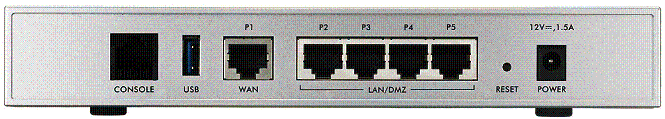
Figure 2: USG20 Rear Panel
As Tim covered recently, the USG20 is powered by a Cavium CN5010 CPU running at 400MHz paired with 256 MB of DDR2 RAM, 128 MB of Flash, and a Realtek RTL8367R Ethernet chip.
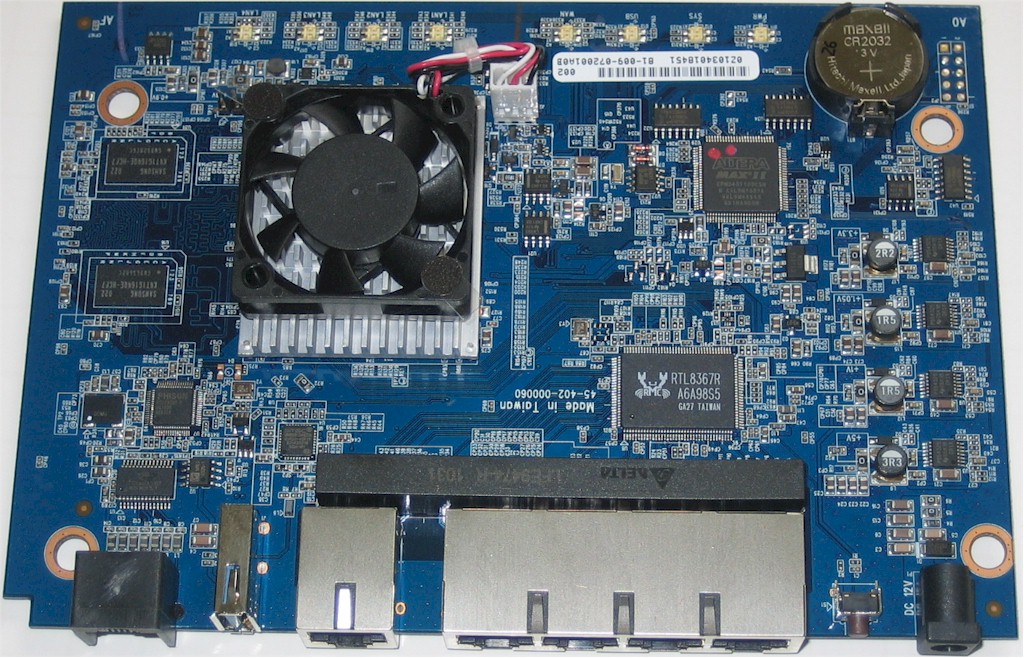
Figure 3: USG20 Board top
Configuration
One of the strengths of the USG20 is that it provides a good amount of information in various formats. Logging into the USG20 web GUI presents a useful dashboard of high level status indicators, shown in Figure 4.
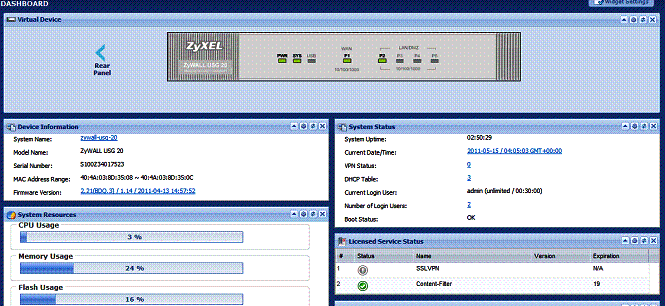
Figure 4: USG20 Status page
Configuration of the USG20 is object oriented, meaning you create an object, such as an IP address, a user, a schedule, an application, etc. and then apply it elsewhere in the configuration. As I mentioned in my review of the USG100, I like this form of configuration because it is very flexible. Once you get used to it, you can create numerous configuration options that are easy to select.
There are three main menus in the USG20. The first menu is labeled Monitor which has 13 different screens for viewing status of the hardware and network activity, statistics on various activities, and log messages.
The second menu is labeled Configuration. There are 40 different configuration screens available via this menu, many with multiple tabs. I like the layout of the menu; I found it intuitive to navigate and responsive.
The third menu is labeled Maintenance. The options here enable upgrading firmware, backing up and restoring configurations, rebooting and shutting down the device, as well as a useful packet capture tool. I used this menu to upgrade the USG20 to the latest firmware, as well as to restore it to factory default settings.
The USG20 supports SSH and Telnet access if you prefer to configure it via the command line (CLI). SSH is enabled by default, Telnet has to be enabled if you wish to use it. The USG20 also has a console port and comes with a console cable, enabling configuration if you can’t get into the device via the network. The USG20’s CLI commands follow a similar structure as other major network providers, such as Cisco and Juniper, and “?” is available to display command line configuration options. Zyxel also has a CLI reference guide in their on line download library.
The USG20’s manual is over 900 pages long but, quite frankly, not very useful. The manual is long on descriptions of the configuration options and short on basic configuration examples. It is a good thing the menus are intuitive!
Network
One of the things I liked about the USG100 was the number of options available for networking and interface configurations. The USG20 has 1 WAN port, 1 USB port, and 4 LAN ports compared to the USG100’s 2 WAN ports, 2 USB ports, and 5 LAN ports. But the USG20 still has the configuration flexibility I found valuable in the USG100.
All ports on the USG20 are Gigabit Ethernet, although the max MTU is 1500 bytes, ruling out Jumbo Frame support. The WAN port (port 1), which is the WAN interface, is used to connect to the Internet, and supports Static, DHCP, and PPPoE configuration.
The USB port is also a WAN port, used to connect to 3G wireless providers. This enables the USG20 to share a 3G connection if that is the primary Internet connection, or use a 3G connection as a back up to a wired connection.
3G modem support has been recently updated in firmware 2.21 (BDQ.3) and is listed in the Zyxel’s product 3G compatibility section. Supported modems include HuaWei’s E220, E270, E169, E800, and E180. Also newly supported are the Sierra Aircard USB 598, and Novatel Ovation MC760.
For North American customers, the supported modem list doesn’t provide many options, and doesn’t include 4G support. A quick web search showed that at one time, both Verizon Wireless and VirginMobile supported the MC760, and Sprint supported the Sierra Aircard. Check with your wireless provider if either are still supported (Ed. note: VirginMobile still supports the MC760). (An example of a router that has more extensive USB modem support is the Cradlepoint MBR900.)
The four physical LAN ports (ports 2-5) can be assigned to one of three interfaces: LAN1, LAN2 or DMZ. Each of these three interfaces has a separate subnet and DHCP server, and is configured as a separate zone in the firewall. By default, ports 2-3 are assigned to LAN1, port 4 to LAN2 and port 5 to the DMZ. Changing a port’s designation is point and click, as shown in Figure 5.
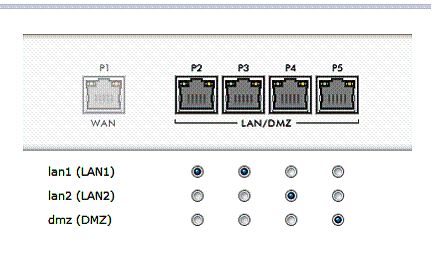
Figure 5: LAN port assignment
As with the USG100, the USG20 supports 802.1q VLAN tagging, enabling even greater network segmentation then available with the three interfaces. VLAN tags can be between 1-4094 and the USG20 can have up to 8 different active VLANs, each with its own DHCP server.
The USG20 provides the same powerful routing options as the USG100. The options include Policy Routes, Static Routes, RIP and OSPF. Policy Routes allow for defining traffic paths based on incoming interface, source and destination subnets, service (protocol), and a next-hop destinations such as an interface or IP. I covered an example of a Policy Route configuration in my review of the USG100.
For a router designed for a small office with five users or less, you might wonder why an advanced routing protocol like OSPF would be supported in the USG20. However, a remote office may connect to a main corporate office that uses OSPF and need to learn network destinations from that main router. The USG20 can be configured as an OSPF stub router, meaning it could learn default and summary routes from the more powerful router without the high memory and processor requirements.
A useful feature on the USG20 is the ability to measure and manage bandwidth utilization. AT&T recently announced it is going to cap Internet delivery service for broadband and DSL customers. I hope they don’t, but I wouldn’t be surprised if other ISPs follow suit. With the USG20, you can collect traffic statistics and measure your utilization by user or service. Figure 6 shows my utilization by service. As you can see, most of my traffic (94 MBytes) is web traffic.
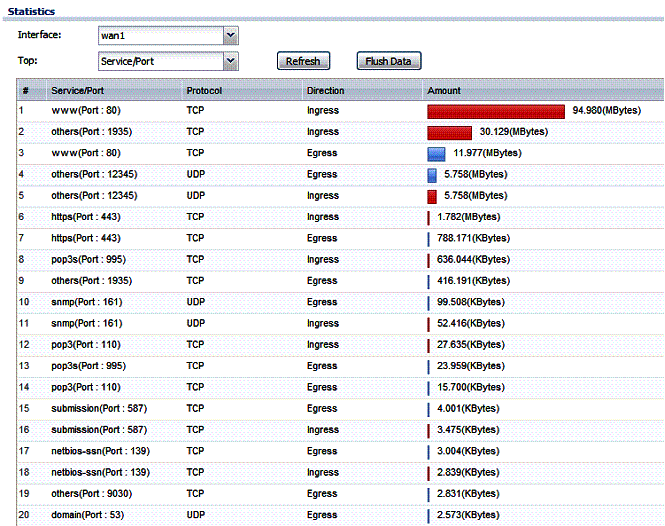
Figure 6: Traffic statistics
To further manage utilization, the Bandwidth Management (BWM) feature of the USG20 can be used to limit throughput for a specific service, such as FTP or HTTP. There are 73 defined services and more can be added as needed. BWM can also be applied globally between zones based on protocol (TCP or UDP).
In addition to limiting traffic by service or between zones, session limits can be applied by user or address, restricting the number of simultaneous flows generated by end devices. Of course, with the USG20 Firewall, specific traffic flows can be blocked entirely, which I’ll discuss next.
Security
The Firewall on the USG20 uses similar object oriented configuration options as the USG100. Firewall rules are created to allow, deny, or reject traffic based on user, source, destination, or service between zones. The difference between denying and rejecting traffic is that denied traffic is simply dropped. When traffic is rejected by a Firewall Rule, a TCP reset message is sent to the source.
For example, I created a simple rule to reject all FTP traffic through the USG20 (Figure 7). I could have made this rule more detailed and blocked FTP traffic only for a specific schedule or for a specific user, or between specific source and destinations as desired.
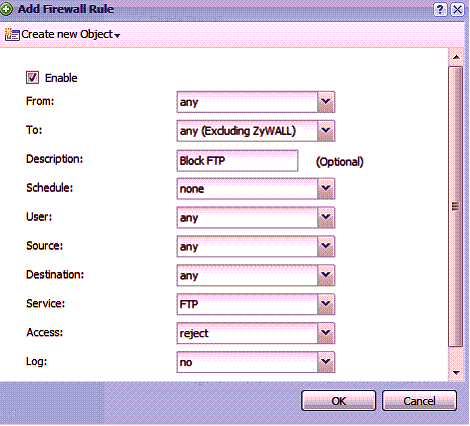
Figure 7: Block FTP firewall rule
A neat feature of the USG20 is Endpoint Security (EPS). An EPS profile can be set up to allow PCs to connect to the USG20 only if they meet certain criteria. When a user first tries to access the network they will have to authenticate with a valid user name and password. Their PC will then be checked to see if it meets programmed security criteria. Those criteria examine the PC’s Operating System (OS), Firewall software, and Anti-Virus (AV) software as depicted in the below diagram.
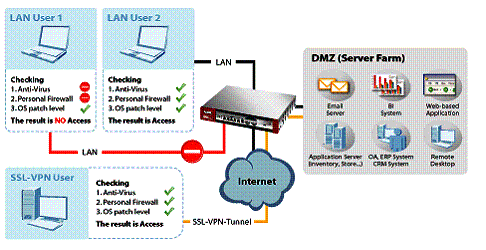
Figure 8: Endpoint Security block diagram
EPS allowed OSes include Windows, Linux and Mac OSX. If Windows is permitted, you can choose the versions allowed, including Windows 2000, XP, Vista, and 7, as well as Server 2003 and Server 2008. Further, you can require certain OS patches are applied to devices that connect to the USG20.
EPS allowed firewalls include Windows, Kaspersky, and Trend Micro. EPS allowed AV software includes Avira, Kaspersky, Norton, Trend Micro and Microsoft’s Security Center.
As a test, I set up an EPS profile to only allow PCs with Norton AV software. I do not use Norton AV Software, so I expected to be blocked. Indeed, with this EPS profile loaded, I was blocked from connecting to the USG20 with the message shown in Figure 9.
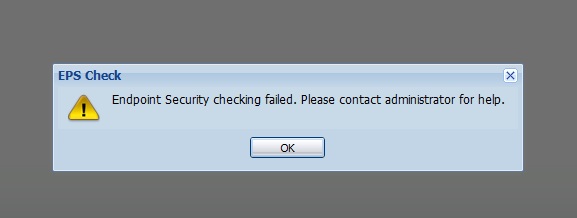
Figure 9: EPS block message
I modified my EPS profile to accept connections from a PC with Microsoft Security Essentials AV software, and was then able to connect to the Internet. Note, if you’re using a different OS, Firewall, or AV software than those supported by the USG20 EPS feature, you can disable the appropriate check in the EPS profile.
Updated 5/23/2011
I ran another test to see if EPS detected whether the AV software was up to date or even running by turning real time protection off on the Microsoft Security Essentials. But my PC still passed the EPS check. This was certainly disappointing because EPS could give users a false sense of security about the status of AV software running on machines that it allows network access to.
I found the EPS functionality a nice enhancement to network security. Network security is improved by ensuring all PCs using the network through the USG20 LAN have required security software, especially in a small network where users may use personal devices.
ADP
Key security features of the USG20 are configured in the Anti-X menu. These features are Anomaly Detection and Prevention (ADP), Content Filtering, and Anti-Spam protection.
Zyxel’s ADP seems to be a poor man’s version of Intrusion Detection System (IDS) and Intrusion Detection and Prevention (IDP). The USG20’s ADP feature protects against network threats such as port scans, DoS (Denial of Service) attacks, and protocol based attacks via http, tcp, udp and icmp.
Zyxel’s ADP, like an IDS/IDP system, relies on signature databases for detecting unsafe traffic types. A signature is a traffic pattern or characteristic that is considered potentially malicious. The firewall compares incoming and outgoing traffic against its database of patterns, and blocks those that match the patterns it holds in its database. The USG20 updates its ADP database from Zyxel which has a partnership with Lionic for current signature files.
ADP is enabled by default. Enabling and disabling ADP is a simple check box. Options for customizing ADP includes defining which zones (LAN1, LAN2, DMZ) are to be protected by ADP and selecting traffic types (port scans and floods) and protocols (http, tcp, udp, icmp) to be scanned.
Running a port scan on the USG20 triggered dozens of messages in the log, all alerting of unsafe traffic hitting the firewall and blocked. As you can see in the log output in Figure 10, the USG20 successfully detected the traffic anomaly and blocked it. (A port scan is both a useful tool for a network administrator, as well as for a hacker. It scans a device for possible open ports that can be used for unauthorized access.)
Figure 10: Log messages from port scan
The USG20’s ADP functionality isn’t as comprehensive as an IDS/IDP solution, but it has a key advantage in that it is free!
Content Filtering
The USG20 comes with a 30 day trial for Content Filtering, with a suggested retail price of $77 annually. Content Filtering on the USG20 is facilitated through a partnership with BlueCoat.
Configuration of Content Filtering is pretty straightforward and consistent with the object oriented methods found in other menus. First, a Filter Profile is created. Within the Filter Profile, you define whether a web page will generate a warning, be blocked or passed, and/or whether it will trigger a log report.
There are 66 different managed web site categories, shown in Figure 11, plus three categories for filtering sites known to be risky for Phishing, Spyware/Malware, and Spyware/Privacy.
Figure 11: Web filter categories
Web features such as ActiveX, Java, Cookies, and Web Proxies can also be blocked. A white list and a black list of web sites, as well as key words found in URLs can also be defined as part of the Filter Profile.
Once the Filter Profile is created, it is applied to a Policy where the schedule, zones, and users that will be subject to the Filter Profile are specified. In addition, a custom message and URL to redirect end users can be applied.
I looked up smallnetbuilder.com in the Profile tool, it is listed as a Computers/Internet site, so I created and applied a simple Profile to block Computers/Internet sites. Upon browsing to smallnetbuilder.com, I was presented with the below default message.
The web access is restricted. Please contact with administrator.(Computers/Internet)
It’s a good thing the default message can be edited! Nevertheless, filtering seemed to work as expected. Selecting all categories for filtering is a bit excessive, you can’t even go to Google, but the USG20 certainly provides plenty of filtering options.
Anti-Spam
The USG20’s Anti-Spam feature is based on do-it-yourself lists of black lists, white lists, and domain names. This is not a very comprehensive solution, as it leaves the blocking definitions up to the network administrator instead of leveraging a database of known spammers. On the other hand, it is cost effective because there isn’t a monthly or annual subscription cost.
Emails matching a black list or domain list can be blocked, or tagged with a specific text string and forwarded. The default tag is [SPAM], which can be customized. Figure 12 is a screen shot of a simple domain list I set up to tag all emails from yahoo.com. Once tagged, I set up a rule in my email program (Outlook) to delete emails with the [SPAM] tag.
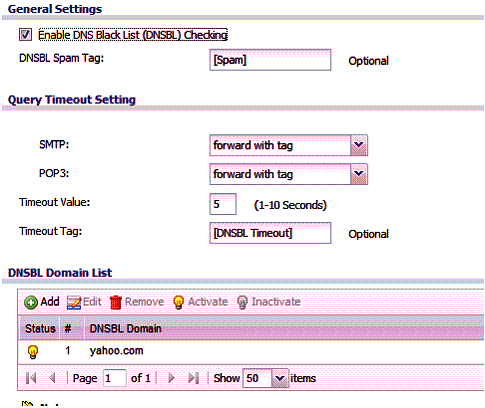
Figure 12: Anti-spam setup
VPN
The USG20 supports both SSL VPN tunnels and IPSec VPN tunnels, although the number of tunnels is very limited. The USG20 supports one SSL VPN tunnel and two concurrent IPSec VPN tunnels.
I had a bit of a challenge setting up the SSL VPN tunnel. The key to the USG20’s SSL VPN tunnel is to decide whether to allow full remote access to the USG20 LAN, or restrict remote access to specific applications including RDP, VNC, and Web Servers.
Full remote access to the USG20 LAN involves building an SSL VPN Access Policy, creating a user name and password, specifying the subnets accessible on via the remote tunnel, and defining a range of IPs for the remote PC. I overlooked the last step because it is labeled optional in the configuration menu. It turns out defining a range of IPs for the remote PC is an optional step only if you choose application restricted remote access. Interestingly. there is a wizard for setting up IPSec VPN tunnels, but not for SSL VPN tunnels.
Once the above set up was completed, I was able to remotely connect to the USG20 from my 64 bit Windows 7 laptop. Zyxel uses the SecuExtender client for remote SSL access, which has a Java applet for managing the tunnel. Figure 13 shows my PC has an IP of 10.10.10.100, which is an IP from the range created for remote PCs. Further, you can see I have access to the USG20 default 192.168.1.0/24 subnet. Up to four USG20’s LANs can be accessible remotely over an SSL VPN tunnel.
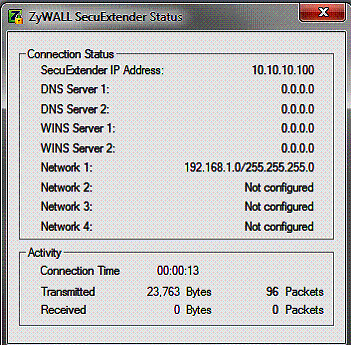
Figure 13: SecuExtender SSL client status
As discussed in the Security section, the USG20 has a feature for checking device’s security software called EPS. The EPS feature can be employed along with SSL VPN tunnels to ensure remote PCs accessing the network meet required security specifications. However, EPS applies to only SSL VPN tunnels and is not available for IPSec tunnels.
I usually find IPSec more challenging than SSL to configure. But I had no problem manually setting up the USG20 to support both Client-Gateway IPSec tunnels and Site-Site IPSec tunnels. For all IPSec tunnels, I set up both sides to use 3DES for encryption and SHA-1 for authentication. I manually set up my tunnels entering IPSec Phase 1 configurations on the USG20’s VPN Gateway tab and IPSec Phase 2 configurations on the VPN Tunnel tab.
I successfully created an IPSec Client-Gateway tunnel with Zywall’s IPSec VPN Client (which is from GreenBow) and IPSec Site-Site tunnels with both a Cisco RV220W and Netgear SRX5308. Figure 14 shows my active IPSec VPN Client tunnel to the USG20.
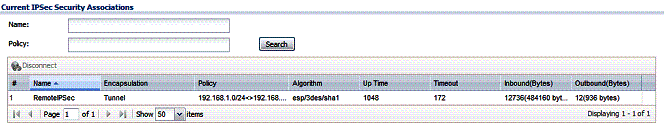
Figure 14: VPN tunnel status
I measured the USG20’s VPN throughput with iperf using default TCP settings, with a TCP window size of 8KB and no other options. I ran iperf on two PCs running 64-bit Windows 7 with their software firewall disabled. All tests were done over a Gigabit network. (Running a simple iperf throughput test between two PCs uses the command iperf -s on one PC and iperf -c (ip) on the other PC.)
Zyxel rates the USG20 at 30 Mbps for 3DES IPSec VPN throughput,but doesn’t provide a throughput rating for SSL VPN tunnels. Table 1 shows the results of my throughput tests.
| WAN > LAN | LAN > WAN | |
|---|---|---|
| SSL | 4.51 | 4.78 |
| IPsec | 17.6 | 27.8 |
Table 1: VPN throughput (Mbps)
The USG20’s SSL VPN throughput is more symmetrical than I’ve seen recently, at 4.51 Mbps from the remote client to router (WAN-LAN) and 4.78 Mbps from the router to remote client (LAN-WAN). In comparison, both the RV220W and SRX5308 support SSL VPN tunnels, but their throughput is much more asymmetrical, with <1 Mbps throughput from the remote client to router (WAN-LAN) and 12-13 Mbps from the router to remote client (LAN-WAN).
The USG20’s IPSec VPN throughput is a bit more asymmetrical than the SSL throughput and significantly faster. I measured 17.6 Mbps from the remote client to router (WAN-LAN) and 27.8 Mbps from the router to remote client (LAN-WAN).
The more important number in remote tunnels is throughput from from the router to remote client (LAN-WAN), as remote clients are typically downloading more data than uploading, so it was good to see my measured throughput (27.8 Mbps) is relatively close to Zyxel’s rating (30 Mbps).
Reporting
The USG20 provides a significant amount of information on network activity, performance, and security. The left side of the Monitoring menu is the launch point to access all this data, as shown in Figure 15.
Figure 15: Monitoring – port statistics
Via the Monitoring menu, you have access to data on port activity, interface status, traffic stats, active sessions, DDNS status, IP/MAC binding, logged in users, 3G connections, IPSec and SSL activity, Content Filter and Anti-Spam activity, and the general USG20 log.
In addition to the information available via the USG20’s menus, log messages can be emailed on regular intervals, as well as a daily report. The USG20’s daily report provides a summary of all the above data options, delivered conveniently to your inbox. A section of the Daily Report shows WAN utilization by hour, shown in Figure 16.
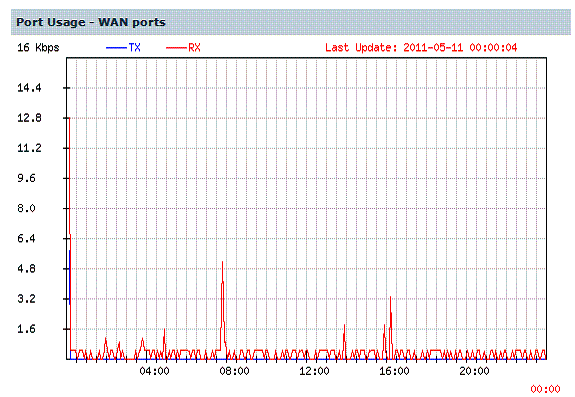
Figure 16: WAN usage plot
Performance
Tim previously reported the maximum sessions capability on the USG20 at only 8, even though Zyxel rating states the device will support up to 6000 sessions. Subsequently, he asked me to repeat the tests to validate. Using the same tool, I couldn’t get a result greater than 8 either, until I changed some of the USG20 settings.
I found the ADP functionality was intercepting our maximum sessions tests. Our tool for measuring maximum sessions is a UDP based tool, which must be triggering one of the ADP signatures. With ADP disabled, our tool indicated the maximum session capability was 29,986. So the Router Chart data has been updated to reflect this.
I don’t think the USG20’s ADP feature actually limits sessions as our tool indicates. I was able to open numerous browser sessions at once, and could see over 30 sessions active in the USG20’s session monitor, even with ADP enabled.
The USG20 sits between a couple of other devices I’ve previously reviewed. SonicWall’s TZ100W is a UTM device with more security features than the USG20 and Cisco’s RV220W is a VPN/Firewall device with fewer security features. All three devices are targeted at the same network size, though, so it is interesting to see how they stack up.
Table 2 compares the throughput capabilities of all three devices, and Table 3 shows price and some key capability/capacity information.
| Router | IPsec | SSL | |
|---|---|---|---|
| USG20 | 58 | 27.8 | 4.78 |
| TZ100W | 31.4 | 17.2 | 1.2 |
| RV220W | 728 | 49.3 | 12.5 |
Table 2: Performance comparison (Mbps)
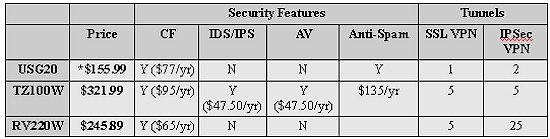
Table 3: Competitive comparison
*As I mentioned in the beginning of this article, the USG20 is also offered with a wireless radio. The USG20W can be found on line for $214.09.
Although these comparisons are not apples to apples, I think it helps provide a good idea of the value of the USG20.
The TZ100W is a UTM device with more security features that you’ll pay for with a higher device cost ($321.99) and annual subscriptions of $95/yr for Content Filtering, an additional $95/yr for IDS/IPS and AV protection, and $135/yr for Anti-Spam.
Updated 5/23/2011
In contrast, the RV220W is not a UTM device at all, has greater routing and VPN capability and throughput, but you’ll pay a higher device cost ($245.89). It does have a subscription content filtering option (Cisco ProtectLink Web Service) for $65/yr or $194 for 3 years.
Conclusion
The biggest weakness of the USG20 is the limited number of VPN tunnels, but if that is a problem, Zyxel offers the USG50 that supports up to 5 SSL VPN tunnels.
I look at the USG20 as a “UTM-light” device as it provides the security functions of a UTM at a lower level and cost:
- Content filtering comes in at a reasonable $77/yr compared to SonicWall’s $95/yr.
- The USG20’s ADP functionality is a tool that provides subscription free signature based network security, although not as in depth as a full blown IDS/IPS.
- The USG20 does not provide AV software, but its EPS feature can ensure all clients are running firewall and AV software. With Microsoft giving away AV software, why pay for it?
- The USG20’s Anti-Spam functionality is also bit light, as it relies entirely on your configurations for detecting and blocking spam, but it is subscription free.
Overall, I think the USG20 is a good security device. It was stable and configuration was quick and relatively easy. The EPS feature, in particular, is a nice way to ensure endpoint security without adding cost. Finally, from a technical standpoint, the USG20 has an incredible amount of network options and provides plenty of details and information about the health and performance of your network.
