
| At a glance | |
|---|---|
| Product | CUJO Smart Internet Security Firewall () [Website] |
| Summary | Subscription-based “smart” firewall for protecting home networks. |
| Pros | • Protects all devices on network including PCs, tablets, handhelds • Pushes threat alerts to iOS & Android apps • Can disable misbehaving IoT devices |
| Cons | • Does not support user profiles • Access / parental control features are work in progress. |
Typical Price: $249
Introduction
Network security is a major issue for everyone. Most home networks are particularly vulnerable to network security threats and depend on a Wi-Fi router’s firewall to secure our network. In this review, I’m going to look at a device called CUJO, which is a firewall for home users “designed to bring business-level security to the home network”.
CUJO got its start as an Indiegogo project that met 763% of its funding goal. CEO Einaras Gravrock’s background is mostly in fashion e-tailing. But Technology VP Robert Beatty has security background, most recently with senior software and systems engineer gigs at Prolexic Technologies and then Akamai (which acquired Prolexic).
CUJO’s website says “CUJO is a smart firewall that keeps your connected home and business safe from cyber threats so that you can stay secure and private online”. CUJO’s website warns that hackers may be able to access your personal finances by exploiting security flaws in connected devices, tamper with a Wi-Fi router, hack a smart phone or plant malicious malware in a network enabled device.
CUJO is a local firewall that leverages cloud-based intelligence. This CUJO FAQ best describes how CUJO works:
Once the CUJO is logically or physically in the middle [between your internet connection and LAN], we sample metadata from your network’s connections (using NetFlow). The metadata is strictly src/dest IPs and ports, bandwidth, packet count and connection states. We do NOT perform Deep Packet Inspection as it is too intrusive and has a pretty big performance penalty for us. These samples are hashed and sent to the CUJO cloud over an encrypted channel. In the cloud is where we do the heavy lifting.
CUJO engineering explained that its cloud runs a “behavioral analysis engine” to detect security threats. Similar to an Intrusion Prevention System (IPS) firewall (but without using deep packet inspection), CUJO’s cloud detects threats by analyzing traffic statistics. CUJO detects and protects against malware and can determine whether a device on your network has been compromised and is possibly participating in a “botnet.”
When a threat or suspicious activity is detected by CUJO’s cloud service on a specific network, the cloud service instructs the CUJO firewall to create a rule to block that traffic. The cloud then sends a notification of the blocked traffic to the customer’s mobile app. If the customer wants to permit the blocked traffic, this can be done via the CUJO app.
Note that because CUJO looks only at packet metadata, it can’t block phishing email unless it comes from a known bad domain or IP address. Nor can it tell whether an email attachment or downloaded file contains ransomware, unless, again, it comes from somewhere known as a source of bad stuff. You’ll still need automatically updated virus and malware protection on all devices that can run it.
The CUJO firewall has an interesting shape for a network device. As shown in the product photo above, it’s an egg-shaped device with a flat top. There are two 10/100/1000 Ethernet ports and an AC power port on its backside. CUJO’s FAQ page lists the device having a 1.2 GHz 64-bit MIPS Cavium Octeon Dual Core Processor with 1 GB RAM and two Gigabit Ethernet ports.
The only lights on the device are a pair of “eyes” on the front that indicate status. The eyes are two half circles. In normal operation, just the upper half of the eyes should be lit. If both the upper half and lower half circles are lit, a threat has been detected. If just the lower half of the eyes are lit, it means the CUJO is offline or disconnected.

CUJO Eye Status
Setup
In larger networks, a firewall is typically installed in front of your network so it can see all traffic going in and out of your network. In home networks with only a single network device, usually a Wi-Fi router connected to the Internet, this can be challenging. The CUJO firewall does not connect directly to the Internet; it needs a router in front of it.
CUJO’s three installation modes (described here) are Direct/Automatic, Direct/DHCP, and Bridge mode. Each have their pros and cons.
Direct/Automatic mode is designed to automatically configure your router, so that all you have to do is connect the CUJO device to your router. This mode works with only some routers, however. For example, it didn’t work with my Linksys LRT224 router. The CUJO folks told me they are phasing out Direct/Automatic mode.
The Direct/DHCP mode requires a few manual steps on the end user’s part, described here. In this mode, CUJO is connected with a single Ethernet cable (the bottom Ethernet port on the CUJO) to a LAN port on your router, as shown below.
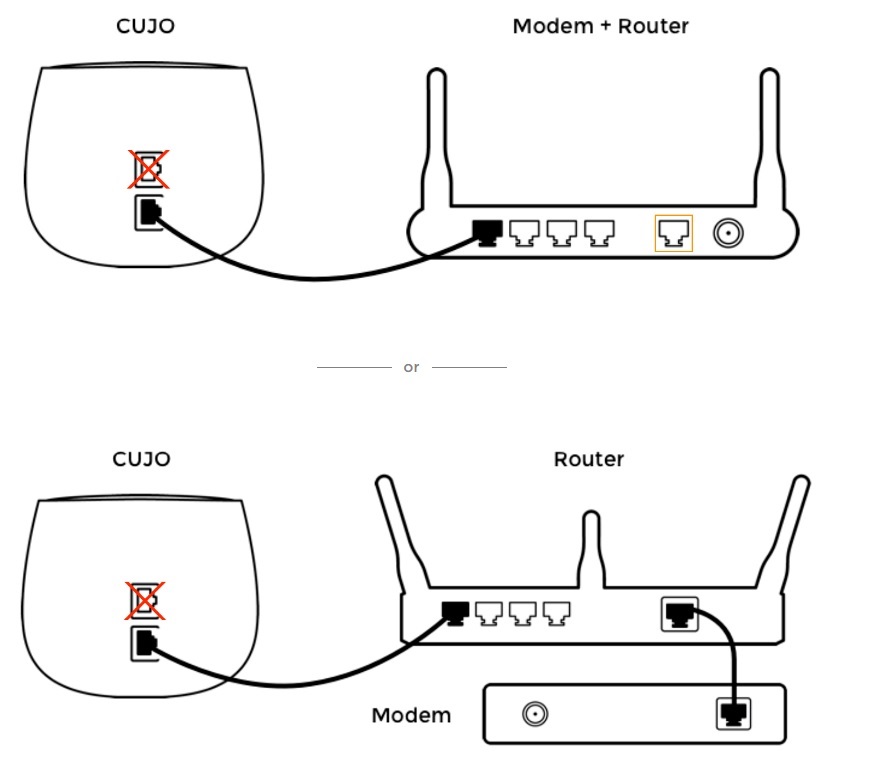
Connecting CUJO in DHCP Mode
The manual steps are to disable the DHCP server on your router and configure your router’s LAN IP address as 10.0.0.1/24. You then enable Direct/DHCP mode on CUJO, via the app, which I’ll discuss shortly, and reboot both your router and CUJO.
Once these steps are complete, CUJO becomes the DHCP server for your network as depicted in the below network diagram.
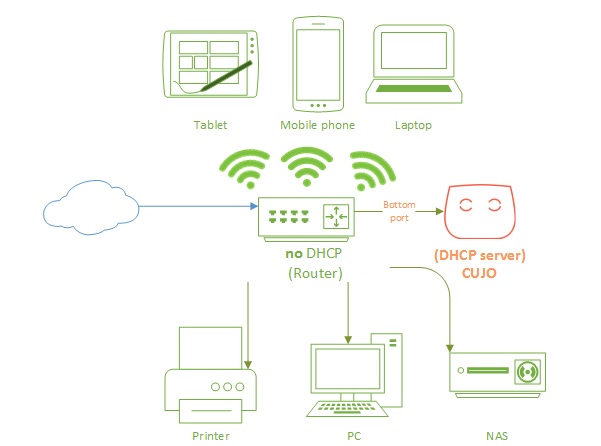
CUJO DHCP Network Diagram
Interestingly, CUJO forwards and receives traffic to/from your router via the 10.0.0.0/24 network and communicates to all your end devices via the 192.168.0.0/24 network through the same physical interface. Your end devices see the CUJO as their default gateway at 192.168.0.1. To communicate on two different networks with the same physical interface, the CUJO firewall uses two different MAC addresses and two different IP address on one physical interface.
This solution has its pros and cons. The pros are installation is simplified by just connecting a single Ethernet cable and making a few small changes. Further, all DHCP enabled devices will automatically communicate through the CUJO and be protected by the CUJO. Also, it requires the least amount of network equipment.
One of the cons to Direct/DHCP mode is that CUJO is also performing Network Address Translation (NAT). This means your network is now double-NATed, since your router already is performing NAT. Technically, this isn’t a big deal for most traffic, but it can cause problems with VoIP, gaming, and other connection-sensitive traffic.
Another con to Direct/DHCP mode is all traffic on your network is going first to your router’s built-in switch, then to the CUJO, and then from CUJO back to your router, which may reduce overall network throughput.
Two more cons to Direct/DHCP mode are devices with static IPs on your network will stop working. And if you’re using the VPN option on your router to remotely access your network, VPN will no longer work. Statically addressed devices can be re-enabled by configuring them for DHCP or giving them a static IP on the 192.168.0.0/24 subnet.
Bridge mode is the third installation method. In this mode, CUJO sits between your router and another network device such as a second router or Ethernet switch. In this scenario, the bottom Ethernet port on the CUJO is connected to your first router, and the top Ethernet port on the CUJO is connected to a LAN port on the second router or to a port on your Ethernet switch, as shown below.
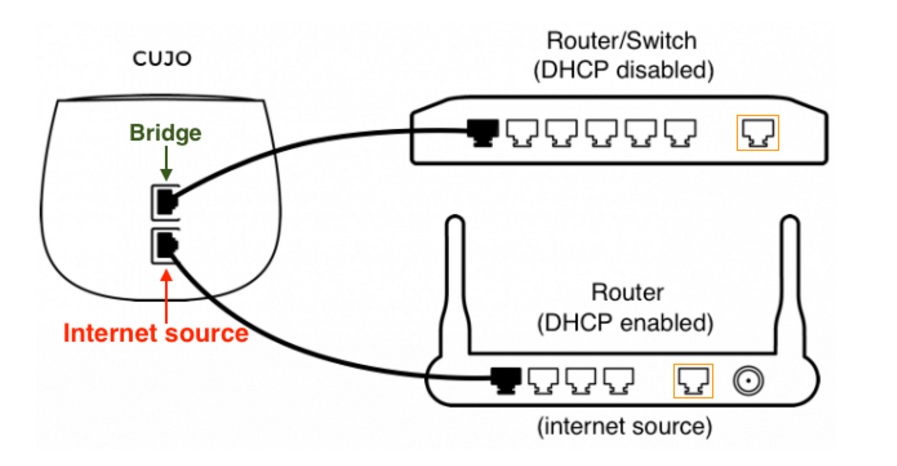
Connecting CUJO in Bridge Mode
No configuration is required on the CUJO, it automatically goes into bridge mode after a reboot when the upper Ethernet port is active. This mode is the best performance option, as it eliminates double-NAT and the issue of traffic going to and from your router twice.
The Cons for bridge mode is you need additional network equipment, you have to hook it up correctly and you have to configure it correctly. Typically, you’ll use two routers with CUJO’s bridge mode. The first router is your connection the Internet. Any devices connected to the first router will bypass CUJO. Wi-Fi needs to be disabled on the first router. The second router provides Wi-Fi and Ethernet ports to devices downstream of the CUJO. Wi-Fi should be enabled and DHCP disabled on the second router. CUJO bridge mode is depicted in the below network diagram.
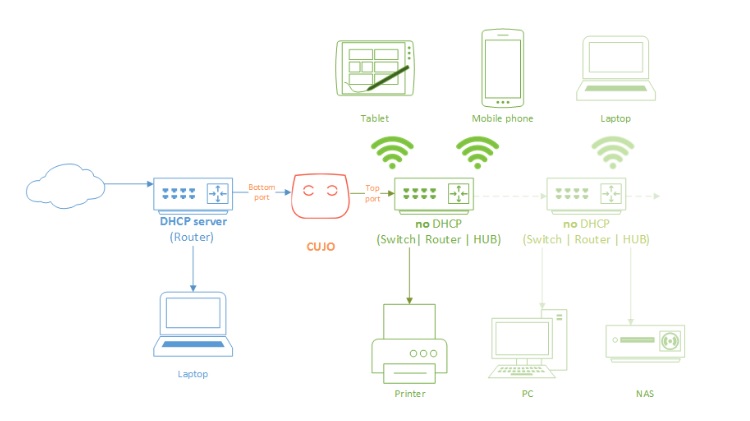
CUJO Bridge Network Diagram
It’s interesting to note, and as you can see in the two network diagrams, the CUJO is behind an existing router/firewall. Thus, installing CUJO on your network is adding a second firewall in addition to the router/firewall you’re already using.
Per CUJO engineering, they are planning a possible future Routed Mode where the CUJO will act very much like a standalone router. CUJO is also exploring embedding its firewall protection in other models of routers at some point in the future.
As mentioned, CUJO lists Bridge mode as the best performance option, so I ran a test to measure throughput. I used two PCs running 64-bit Windows with their software firewall disabled. I used TotuSoft’s LAN Speed Test client and server application, with a file size of 100MB to measure throughput. I ran baseline and CUJO throughput tests multiple times to ensure my results were consistent.
To baseline my PCs, I ran a test with my two PCs connected to a switch without CUJO connected. As you can see in the below screen shot, I could write and read data directly between my two PCs at over 400Mbps.
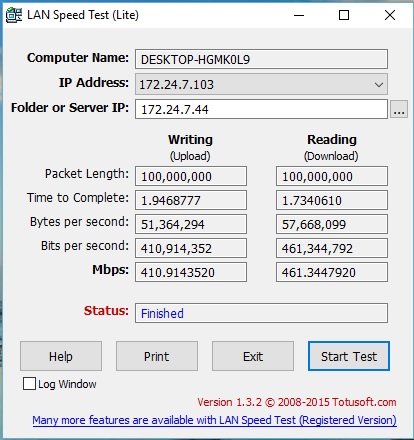
Throughput Baseline
To test CUJO’s firewall throughput while in bridge mode, I then connected one PC in front of the CUJO and the other behind the CUJO so the throughput test would be through the CUJO firewall. As you can see in the screenshot below, my upload throughput with the CUJO was reduced to 252 Mbps, while download throughput remained over 400 Mbps.
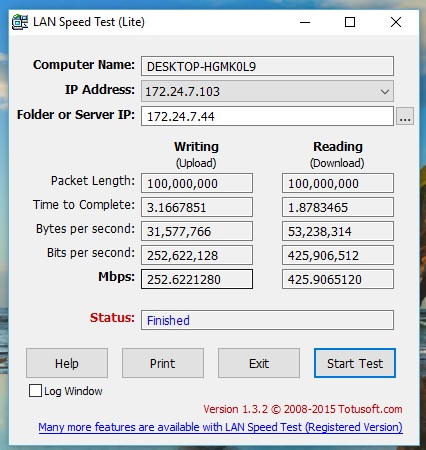
CUJO Throughput
Clearly, CUJO is slowing upload throughput, enough to be worth mentioning. However, most home users are primarily concerned with download throughput. For those concerned with upload, unless your ISP connection is higher than 250 Mbps, you shouldn’t have a throughput issue with CUJO in bridge mode.
As a final comment on CUJO installation, it is interesting to reference our review of a parental control device called Circle With Disney. The Circle device is focused primarily on providing parental controls on a network, a feature CUJO plans to roll out in the future. However, to provide parental control, the Circle Device has to be in position to filter all traffic going in and out of your network, just like CUJO.
As Craig discussed in the Circle review, the Circle device uses “ARP spoofing” so all devices on your network think the Circle device is the router and send their traffic to the Circle device. Circle doesn’t require any reconfiguring of your network or router for it to work. CUJO’s Direct/DHCP mode and Bridge mode both require a bit more effort from the end user.
In Use
You monitor and control CUJO with an iPhone or Android app; CUJO does not have a web-based administration interface. I loaded the app on an iPhone. The app has menus for Account Setup, Settings, Threats, and Devices as shown below.
CUJO Menus
The Account menu is a simple menu for entering your email address, cell phone number, and password.
The Settings menu allows you to change modes (Direct/DHCP or Bridge), to enable or disable Push Notifications for security threats, set a PIN code, activate or deactivate the firewall, enable the display of flow details and a menu option called Eyes On. I assume the Eyes On option is intended to turn on/off the eye ball indicators on the firewall, but it didn’t seem to work. CUJO’s eyes stayed on whether I checked or unchecked Eyes On.
The Device menu shows all the devices CUJO has discovered on your network. With this menu, you can see a list of discovered devices on your network as shown below.
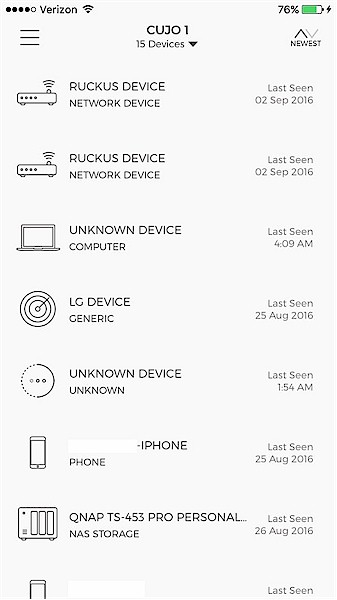
Device List
Further, you can specify whether the device should have access to the Internet and whether it should be monitored and/or protected by the CUJO. The default is for all discovered devices to have Internet access and be monitored and protected. I tested the Internet connectivity feature by running a continuous ping to Google from a laptop behind the CUJO, then used the CUJO app to disable Internet access to my PC. It worked as expected, the pings from my PC to Google failed until I re-enabled Internet access on the CUJO app.
An interesting feature in the Device menu is being able to see “flow data” on each monitored device. This option allows you to see on your smart phone what each device has connected to and the packet counts and bandwidth (in bytes) used by that device in the last 24 hours. As you can see below, one of my devices has sent / received a total of 48,273 packets and used 7,708,268 bytes of bandwidth in the past 24 hours.
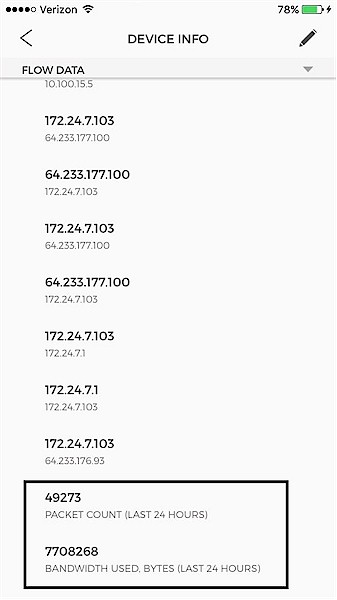
Device Flow Data
Missing from the Device menu are tools to edit device names or delete devices that are no longer on the network. It would be nice to be able to assign custom names to devices as desired. Further, once a device is no longer on the network, it would be nice to be able to delete it to reduce the number of devices in the device list.
The Threats menu allows you to see the last 7 or 30 days of threats. You can filter the view of threats by just looking at All threats, Critical threats, Blocked threats, or Unblocked threats. Note that CUJO documentation does not provide definitions of these threat categories. The screenshot shows the threats detected on my test network.
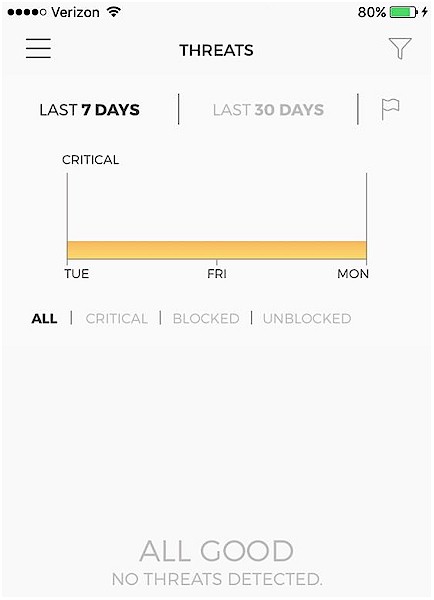
Device Threats
I ran CUJO on a small network with my PC and iPhone actively monitored by CUJO. In two weeks of general Internet and email use, neither my PC or iPhone triggered a CUJO alert or push notification. But that’s not really a good test. So I reached out to CUJO engineering for advice on how to see if CUJO blocked actual threats. They directed me to ianfette.org, a non-malicious site for testing malware detection. Sure enough, browsing to this site from a PC behind the CUJO resulted in this browser screen on my computer…
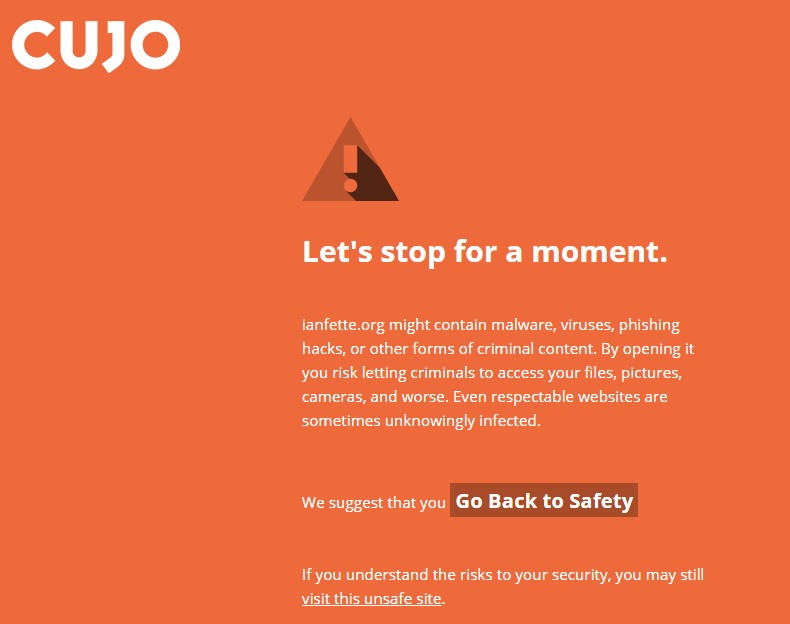
Blocked Webpage
…and this threat message on the CUJO app.
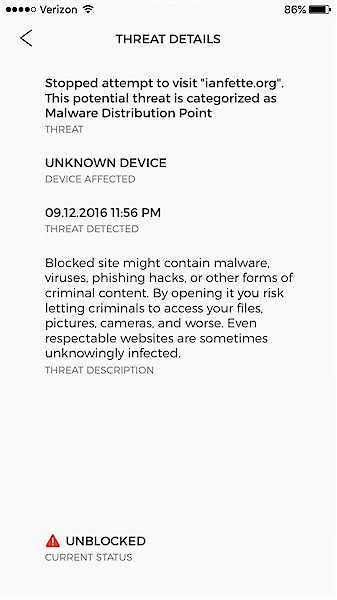
Threat Details
But Firefox 48.0.2 also blocked the site without using CUJO
Firefox ianfette.org block
…as did Chrome Version 52.0.2743.116 m (64-bit).
Chrome ianfette.org block
Only Internet Explorer 11.0.9600.18015 failed to block the site, but showed only "Nothing here" on an otherwise blank page.
To test CUJO on actual malicious websites, I did a Google search on known malware domains. I tried browsing to a listed attack site, ksdiy.com and a phishing site, spaceconstruction.com.au. (I don’t recommend browsing to these sites unprotected.) Both resulted in the CUJO messages shown above, indicating the CUJO firewall detected and blocked actual malicious websites.
As a final point on using the CUJO firewall, it appears to me CUJO is designed to be easy to use with minimal amount of controls. As such, there are no traditional small network firewall menu options for port triggering or port forwarding. There also isn’t a menu option for creating firewall rules to permit or deny specific types of traffic, although you can override a blocked device using the CUJO app. There also isn’t an option to put a device in the firewall’s Demilitarized Zone (DMZ), although you can disable CUJO monitoring of a specific device. CUJO engineering mentioned they are working on a possible advanced User Interface to provide these levels of functionality.
Additional future functionality planned for the CUJO are parental controls including content filtering and the ability to schedule Internet use. These features are planned in fall 2016, in other words, within a few months of this review. Other planned CUJO features without a rough release date are URL blacklists and whitelists and VPN capability. CUJO is also planning an additional security checkup service to provide anti-virus protection.
Closing Thoughts
I like CUJO’s innovation and focus on home network security. It appears they have met their goal of making a friendly and simple to use firewall. The handheld app is certainly easy to use.
CUJO costs $99, which includes a 180 day trial license. After that, you need to pony up $8.99 / month, $26 for three months, $49 for six months or $80 for a year of service. If you’re a true CUJO believer, you can opt for a lifetime subscription for $800.
My main concern is with installation. It’s nice to have options, but this runs counter to CUJO’s goal of being easy to use. One installation method is easiest, which is what CUJO should have, just like Circle With Disney already has.
Unless all you’re doing on your network is web surfing, email, and streaming Netflix, I wouldn’t use CUJO’s DHCP mode because it creates a double-NAT situation. This will break remote VPN capability and could hinder VoIP or gaming traffic. Bridge mode is the better mode from a network standpoint, but it requires additional equipment. Both DHCP mode and Bridge mode on the CUJO are going to require the end user make changes to their network, which can be a daunting task for the non-technical. In my experience, if a network device isn’t plug and play for home users, it’s going to be a hard sell.
As I’ve noted throughout the review, CUJO has big plans to enhance the product’s capabilities. But buying a product based on future plans from a young company trying to get established is not recommended. Either buy CUJO based on what it does today, or wait until it has the features you want.
CUJO is not going to be for everyone, particularly those uncomfortable with any cloud service looking at any part of their internet traffic. But for home users who want to protect all devices on their network, whether they run anti-virus / malware apps or not, CUJO could be worth a try.
