
| At a glance | |
|---|---|
| Product | CUJO Smart Internet Security Firewall () [Website] |
| Summary | Subscription-based “smart” firewall for protecting home networks. |
| Pros | • Protects all devices on network including PCs, tablets, handhelds • Pushes threat alerts to iOS & Android apps • Can disable misbehaving IoT devices |
| Cons | • Does not support user profiles • Access / parental control features are work in progress. |
Typical Price: $249
Introduction
My original review of the CUJO Smart Internet Security Firewall found its installation was a little rough around the edges. But the device met its goal of being easy to use, albeit with limited features. The CUJO folks recently reached out to tell us they had delivered on many of the promised enhancements with their V6 firmware. So with internet privacy and security becoming more front-of-mind to many of us at least here in the U.S., we agreed to take another look. I’ll specifically be testing CUJO’s promised performance improvements and looking at their new access (parental) control feature.
Setup
CUJO’s three installation methods have been streamlined down to the Direct and Bridge methods shown below. You can get details about the difference between these methods in the original review. I still prefer the Bridge method, even though it requires adding a switch, because it avoids the double-NAT complication of DHCP mode.
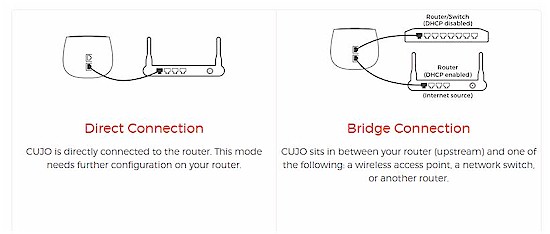
CUJO setup options
Many buyers must prefer DHCP mode, however, since CUJO has added lots of Setup FAQ that describe how to configure many popular routers to operate with CUJO in DHCP mode. There is also a FAQ explaining the difference between the modes.
Performance
CUJO’s hardware remains unchanged. It still uses a dual core 1.2 GHz 64-bit MIPS Cavium Octeon processor, 1 GB of RAM and 4 GB Flash storage. CUJO says the hardware “is fairly over-provisioned for most networks”, meaning it should have more than enough computing power to protect most small networks without impeding performance.
CUJO tracks CPU utilization of its devices in the field and has found them running at only 5-8%. Further, per CUJO, “because we use algorithms that are not inspecting every single packet based on signatures, we have a lot less utilization of CPU then other IDS/IPS (Intrusion Detection System/Intrusion Prevention System) approaches”.
CUJO said its latest firmware improves throughput to 750 Mbps,with all security measures enabled, so, of course I had to check.
To test CUJO’s improved throughput, I used two PCs running 64-bit Windows with their software firewall disabled. I used TotuSoft’s LAN Speed Test client and server application, with a file size of 100 MB to measure throughput. I ran baseline and CUJO throughput tests multiple times to ensure my results were consistent. To baseline my PCs, I ran a test with my two PCs connected to a switch without the CUJO firewall connected. In my baseline test, the max throughput I measured was over 927 Mbps, shown below.
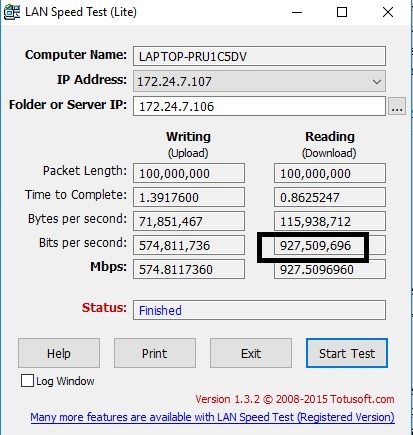
Performance Baseline
To test the CUJO firewall throughput in Bridge mode, I connected one PC in front of the CUJO and the other behind the CUJO so the throughput test would be through the CUJO firewall. The below screenshot shows my best result, with a peak throughput of 667 Mbps. 667 Mbps isn’t quite the 750 Mbps reported by CUJO, but much better than the peak of 425 Mbps I measured in my initial review.
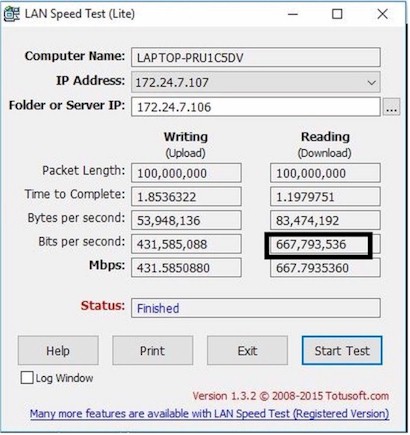
Measured Performance
How It Works Recap
Before we look at the new access control feature, let’s first review how CUJO works. CUJO inspects packets as they come and go from your network. CUJO does not look at actual packet content as more expensive IDS/IPS appliances do. Instead, CUJO looks at packet metadata including Layer 3 (IP addresses) and Layer 4 (port numbers, such as port 80 for web traffic) information, connection protocol (TCP, UDP, ICMP) and any security certificates exchanged. Although CUJO now "inspects" HTTPS traffic, only the unencrypted portions of the packet header are inspected.
The heart of CUJO’s protection mechanism is based on knowing two things: "bad" IP addresses and "normal" device behavior. CUJO’s cloud keeps track of "bad" IP addresses, which can potentially harm your system.
CUJO checks “every site that is accessed over HTTP/HTTPS against a CUJO threat database (in realtime)”. CUJO looks at the website you’re trying to browse, talks to the CUJO cloud to see if this website is safe, then allows or blocks the traffic based on the information it receives from the CUJO database. As sites are accessed, they are cached locally, so CUJO cloud lookups can be minimized. The local cache also lets CUJO keep working if its connection to CUJO cloud is temporarily interrupted.
Phishing, malware, virus and other malicious sites are blocked by matching the destination IP address against CUJO’s treat reputation database of known malicious sites. The CUJO threat reputation database is built on data compiled from commercial and open source databases, CUJO security partners, and data learned from their base of “tens of thousands” of CUJO devices in the world.
If you browse to an unsafe website, CUJO will present a block screen on your browser.
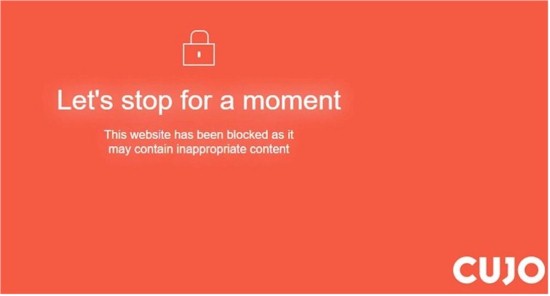
Safe Browsing
This CUJO basic function is mostly unchanged from my original review except it now handles HTTPS traffic and its speed has been improved. Because CUJO looks only at the packet header, its primary detection tools are IP addresses and web domains. But CUJO also looks at packet rate—helpful for determining whether a device has been hijacked to participate in a DDOS&mdashand behavior patterns.
CUJO says they learn "normal" behavior patterns for devices, so can remove internet access if they break pattern. The video below describes an example of this process.When traffic is blocked, a message will be shown on the CUJO app, allowing you to leave that traffic blocked, or to manually permit it if it is known good traffic.
CUJO said they currently consider more than 250 SYNs a minute to be a sign of a device participating in a DDOS attack. (SYN is part of TCP’s three-way handshake.) This traffic level doesn’t have to be to / from a known bad site; it can be to any IP address or domain. But when I ran my my own tests using nping as a packet generator, I wasn’t able to trigger a block from CUJO. CUJO explained that DDOS protection has not been enabled in my CUJO because "we tend to not enable it globally for now, as we are shaping/fine tuning the thresholds with our beta users”.
How It Works – more
One of CUJO’s base protection mechanisms is to block remote access to all devices behind by the CUJO firewall. In this respect, CUJO is just like your router’s NAT firewall, which also blocks all inbound traffic by default. But since CUJO sits in front of your router, you now get an additional layer of protection. Conversely, if you want to enable an inbound service, you need to both forward a port in your router’s firewall and configure CUJO appropriately.
I tested this by enabling remote access on my PC, then enabling port forwarding on my router to pass external Remote Desktop Protocol (port 3389) traffic to my PC. My first attempt to access my PC was blocked and I saw the warning below, meaning that CUJO blocked the remote access as designed.
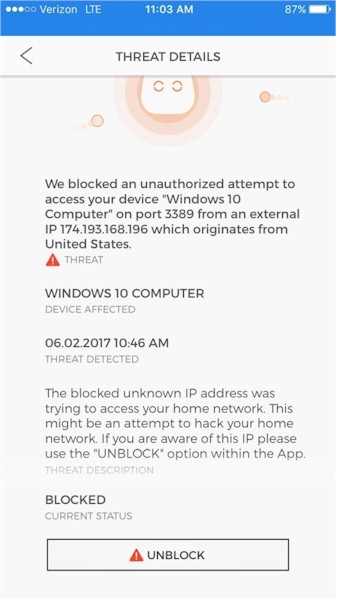
Remote Access Protection
I then selected UNBLOCK on the CUJO app, and after a few attempts to remotely access my PC, it worked. CUJO engineering told me that there can be a delay of up to 30 seconds after selecting unblock since CUJO needs to coordinate with CUJO cloud to make this happen.
A common network device is an IP camera, which often has remote access enabled so you can remotely view it. Moreover, that IP camera may just have simple user name and password protection, which can be breached through a simple brute force attack. A brute force attack is where an attacker either manually or with a simple program keeps trying to login with combinations of user names and passwords.
Once the hacker succeeds in guessing the user name and password (which can be really easy if the user name and password was left at default settings), the hacker can now view the camera feed. The video below discusses vulnerabilities and CUJO’s protection capabilities for IP cameras.
Another vulnerable network device is a network printer. This video shows how a hacker can install a program to capture print jobs from your printer and send them off your network. If your printer is compromised, documents you send to your printer can also be sent to the hacker’s network, where they can print and view your document without you ever knowing it!
CUJO remote access protection protects your printer from remote access and subsequently having a print capture program installed. Further, CUJO device profiling will block your printer from talking to devices outside your network and block your printer from sending your documents outside your network.
CUJO applies network malware protection by blocking access to / from known bad IP addresses and domains. See CUJO’s malware video here. I inadvertently experienced CUJO’s anti-malware protection in action while casually surfing Yahoo. CUJO detected, blocked and alerted me via its app of multiple attempts to access the site shown below, which it considers a malware site.
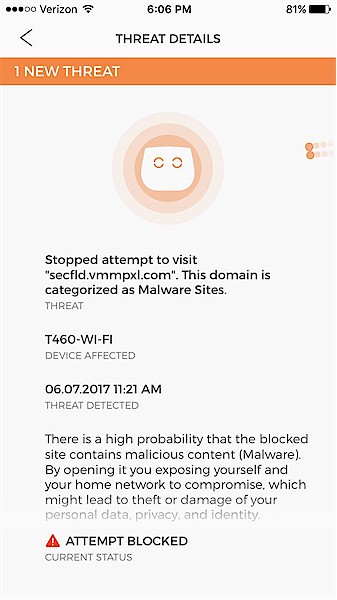
Malware alert
Access Control
Access is a new feature that allows restricting access to websites by device. This feature is available in the latest version of the app, but it is labeled beta, so still in development and being tweaked.
New CUJO menu with Access feature
The CUJO Access feature is a basic parental control / internet filter that filters website access by device. While this is a step forward, CUJO doesn’t support user profiles like Circle with Disney and many other parental control products. So you can’t assign devices to users and set appropriate filtering profiles at that level.
Devices are automatically discovered by CUJO when they connect to your network, so you select the device(s) to restrict from the list of discovered devices. The devices are listed by a network name that CUJO thinks matches the device, such as "Windows PC" or "Apple" device. To make devices easier to manage, you can rename them to something more intuitive, such as "Bob’s PC," "Mom’s iPhone," etc..
CUJO Access has 12 different website categories including News, Religion, Others, Shopping, Social, Streaming, Gaming, Rated R, Web Mail, Advertising, Adult, and Entertainment. The app has a brief description of each category, but no age ratings. Some of the category descriptions are shown in the screenshot below.
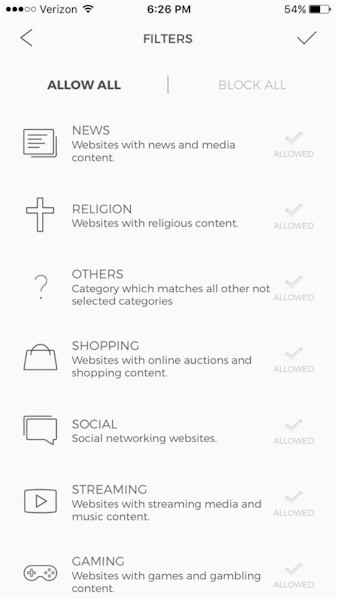
Access control categories
Other features in the app include a whitelist function to permit websites you don’t want blocked, plus the ability to view the names of websites that have been blocked by device over the past 24 hours.
A basic feature supported by many routers that CUJO lacks is internet access scheduling. So there is no option to control when or how long a device can access the Internet. CUJO said this feature will be added as Access moves out of Beta.
To test Access, I created a profile to block access to all categories for one of my network devices. I got inconsistent results, where I could access some sites, but not others. The sites I couldn’t access sometimes timed out, and other times presented CUJO’s orange block page. In my opinion, the Access feature appears to need more work, so is appropriately labeled beta.
Closing Thoughts
So, does CUJO make your network safer than just your current router? It depends on the router you have. Some routers, like ASUS’ ROG Rapture GT-AC5300 and TP-Link’s Deco Wi-Fi mesh system have Trend Micro IPS and malware protection built in. Luma‘s Wi-Fi mesh system also has the ability to detect when your network’s devices are up to no good and also provides basic internet access schedules, which CUJO doesn’t (yet) support. And none of these alternatives are charging a subscription fee for these services (at least not yet).
CUJO is now available at Best Buy in addition to Amazon and its own webstore. But Amazon and Best Buy sell only the $249 bundle of device and "free" subscription. So CUJO is trying to raise its ASP to boost revenue. You can only buy the device ($99) and monthly ($8.99) or yearly ($59) subscription, direct from CUJO.
But assuming CUJO to be as good or better than these other options, the more relevant question is whether CUJO will be here for the long term. Distributed / mesh Wi-Fi system newbies like eero, Luma and their ilk gave established consumer networking giants like NETGEAR and Linksys a wake-up call and are being reduced to single digit market share as a result.
Bitdefender is supposed to be shipping its upgraded Box sometime this year. Bullguard’s Dojo has just started to ship and Domotz’ Fingbox isn’t far behind. And don’t forget Circle with Disney, which supports more user-friendly user profiles. The real challenge, however, is likely to come from Comcast and other service providers who are already busily hawking physical home security systems to their customers. With the right partner, network home security is just a minor step and could be integrated right into the set-top box. This article by CE Pro’s Julie Jacobson shows how home security players are eyeing this market.
CUJO continues to work on improving the product. In addition to the beta Access feature, CUJO is also working on version 2.2 of the CUJO app that may be available by the end of this month. The company shared that it is working on machine learning algorithms that can detect “Zero-day” phishing threats, but has no firm timeframe for rolling out that capability. CUJO said it is also working to integrate their software into an unnamed partner’s router firmware.
The bottom line is that CUJO continues to evolve and today provides more protection from both inbound threats and surreptitious outbound traffic from compromised devices than it did nine months ago. The key question, if you decide to plunk down your $249, is whether CUJO will be around long enough to return enough of that investment.
