
| At a glance | |
|---|---|
| Product | Cisco Integrated Security Appliance (ISA550W) [Website] |
| Summary | Cisco’s entry-level but powerful Integrated Services router combining IPsec & SSL VPN, gateway anti-virus, intrusion protection and content filters. |
| Pros | • High VPN Throughput • High UTM Throughput • Cisco’s SIO Security Center |
| Cons | • Long boot time • Sluggish menu performance • Remote VPN Client tunnels are tough to set up |
Typical Price: $1027 Buy From Amazon
Introduction
Unified Threat Management (UTM) devices are all-in-one devices that provide networking, firewall, and security solutions for small-to-medium sized networks. UTM devices typically provide a wide array of security features including anti-virus, web filtering, anti-spyware, spam controls and intrusion prevention.
UTM devices also commonly support VPN services, a rules based firewall and flexible network options. The Cisco ISA500 series are Cisco’s UTM devices with all of these features, targeted at small businesses.
There are four models in the ISA500 series, the ISA550, ISA550W, ISA570 and ISA570W. The “W” denotes the wireless versions of each platform. Cisco recommends the ISA550/ISA550W for networks with up to 25 users and the ISA570/ISA570W for networks with 25-100 users. In this review, I’m going to look at the ISA550W.
The ISA550W is housed in a gray metal case with a black plastic front and external power brick. It measures 12.1”W x 7.1”D x 1.9”H, is mountable in a 19” rack and comes with mounting brackets. The ISA550W is passively cooled, so runs silently.

Cisco ISA550W front panel
Indicator and status lights are on the front and the Ethernet ports are on the back. In addition to the Ethernet ports, the wireless antennas, a power switch, power port, Kensington security port, and a single USB 2.0 port are on the back. (The USB port is used for loading or saving various files.)

Cisco ISA550W rear panel
Inside
The ISA550W runs on a 1.6 GHz Marvell 88F6282 CPU, with 1 GB RAM and 256 MB of flash. Other key components include a Marvell 88E6171R 7-Port Gigabit Ethernet Switch and a 2.4 GHz N300 Ralink wireless SoC, hidden under the RF shield at the bottom of the mainboard picture below.
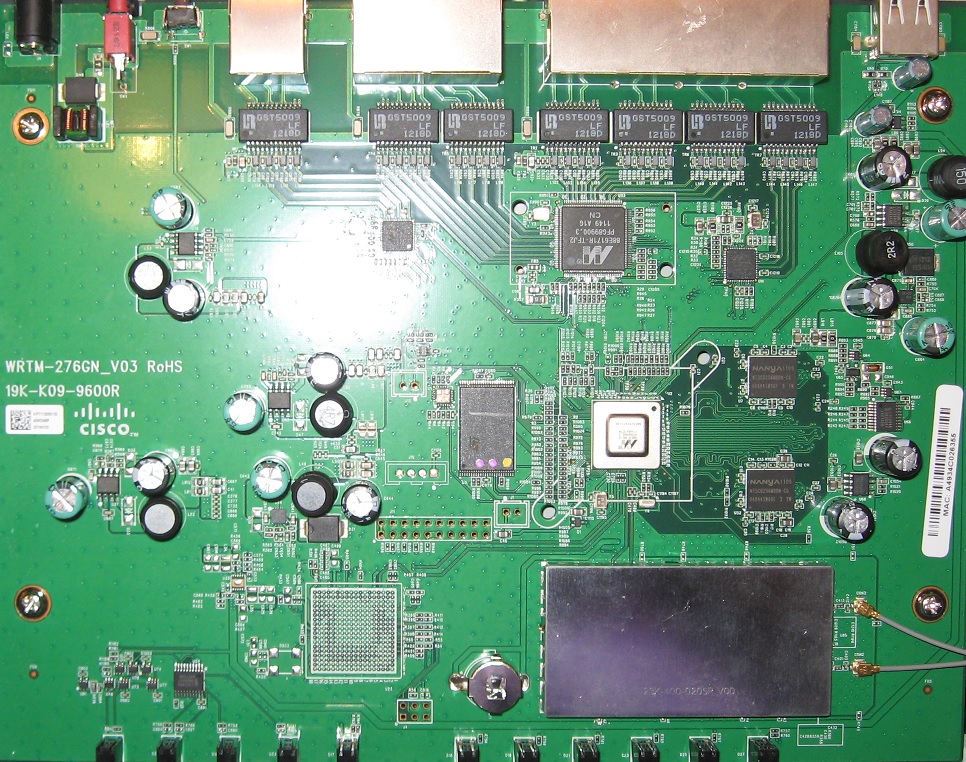
Cisco ISA550W board
Configuration
The ISA550W is managed via a web GUI, which Cisco refers to as the “embedded Configuration Utility.” If you were to deploy the ISA500 series in your business and rely on a third party to manage it for you, Cisco recommends deploying an ISA500 with the Cisco OnPlus service, which provides additional remote access to the device and monitoring options.
When you log into the ISA550W, you’re presented with a useful dashboard, shown below. This dashboard provides a quick summary of device utilization, log counts, VPN status, port status, interface status, and wireless status.
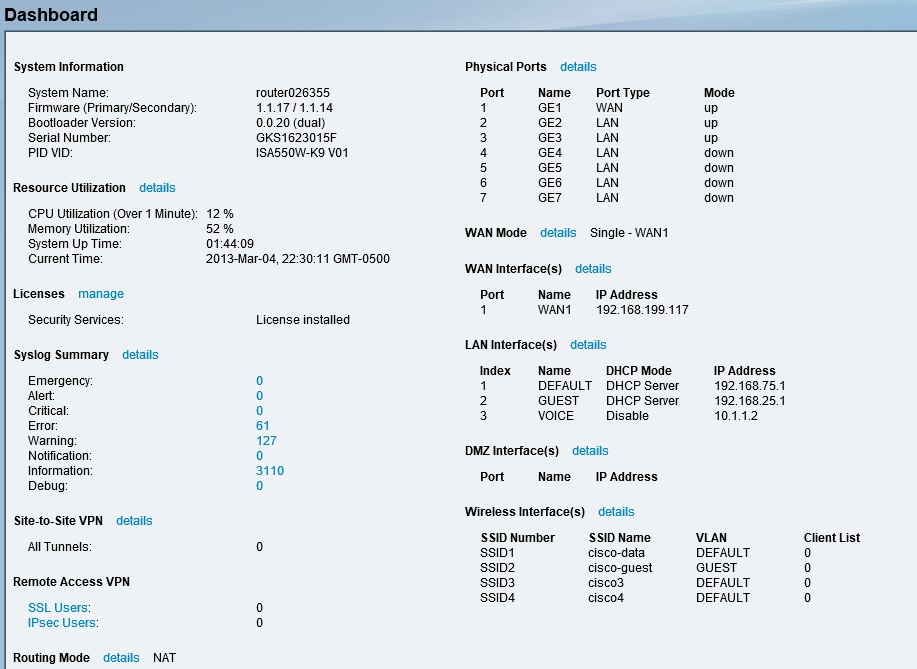
Cisco ISA550W dashboard
To make things easy, there are six different configuration wizards. There is a basic setup wizard, dual WAN wizard, remote access VPN wizard for both IPsec and SSL, a site-to-site VPN wizard, a DMZ wizard, and a wireless wizard. I found the VPN wizards helpful.
As would be expected in a UTM, the ISA550 has quite a few configuration options. However, I found the layout of the menus easy to navigate. Main menus are listed along a panel on the left side, which can be expanded to reveal further options. Clicking on an option brings up a page with one or more tabs of configuration screens.
There are 9 different main menus, each with 4-15 submenus, some of which have additional submenus. I often put together a chart in my reviews listing the menu headers of a device, but in this case there are simply too many. Suffice it to say, the ISA550W is highly configurable.
The ISA500 series’ 432 page manual covers the configurations of the ISA500 relatively well. In addition, there is a help button in the ISA550W configuration utility that brings up an online version of the manual, which is quite handy. As I’ll cover in the VPN section, a few more configuration examples would be useful, though.
On the downside, boot time and menu response time on the ISA550W are very slow. It takes about three minutes for the router to boot and the ISA550W’s screen response is sluggish when applying configurations. Waiting to apply configurations or to navigate from screen to screen can make configuration and administration of a device a drag. Unfortunately, I’ve seen menu lag on other Cisco small business devices, such as the SG500-28P switch.
Feature Summary
I put together this feature summary from the ISA500 series data sheet.
Zone Based Firewall
Security
VPN
Throughput
|
Networking
Wireless
Other
|
Networking
The ISA550W has seven 10/100/1000 Ethernet ports. One of the ports must be a WAN port and two ports must be LAN ports. The other four ports are configurable as either LAN, WAN, or DMZ ports.
The four configurable ports default as LAN ports. As a LAN port, they can be configured as an access or trunk port. As an access port, they can be assigned to a single VLAN. As a trunk port, they support 802.1q VLAN tagging. Up to 16 VLANs are supported on the ISA550W. Further, a unique DHCP server can be created for each VLAN.
As a test, I added VLAN33 on the ISA550W and enabled the DHCP server for that VLAN to provide addresses in the 192.168.33.0/24 subnet. I configured port 6 on the ISA550W as an 802.1q trunk port as a member of VLAN1 and VLAN33, and connected port 6 to a similarly configured 802.1q trunk port on a NETGEAR GS108T switch. The test was successful. PCs on VLAN1 access ports got IP addresses from VLAN1 and PCs on VLAN33 access ports got IP addresses from VLAN33.
The networking status screen below shows port 6 is configured as a trunk and is a member of VLAN 1 and 33.
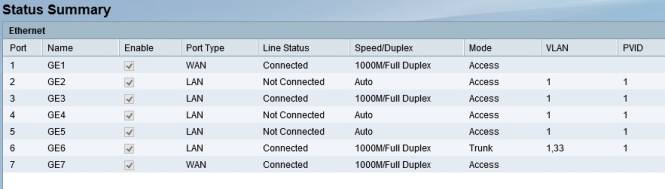
Cisco ISA550W dashboard showing VLAN and Trunking
Any one (but only one) of the four configurable ports can be configured as an additional WAN port, making the ISA550W a dual WAN router. The screenshot above shows port 1 and port 7 are configured as WAN ports.
The default dual WAN configuration is a 50-50 traffic distribution between the two WAN ports. Load balancing over dual WAN ports on the ISA550W can be adjusted by allocating different percentages of traffic to each port, distributing traffic based on link bandwidth, by setting one interface as primary and the other secondary, or by policy based routing. Traffic can also be metered on each WAN port if you’re connected to an ISP that limits bandwidth consumption.
I tested dual WAN functionality by making port 1 primary and port 7 secondary and left all other settings at default. I then set up a continuous ping to the Internet and disconnected port 1. With the default settings, it took the ISA550W about 45 seconds to failover to port 7. After setting the failover timers to their lowest values, it took the ISA550W only about 10 seconds to failover to port 7. Failback to port 1 in both cases was within 10 seconds.
Policy-based routing is a neat way to distribute traffic over dual WAN ports. For example, SIP based VoIP traffic could be routed over one WAN port, while all other traffic could be routed over the other WAN port to minimize bandwidth congestion for VoIP traffic.
Quality of Service (QoS) options are available for the WAN, LAN, and Wireless interfaces and can be applied to both uplink and downlink traffic. On the WAN interfaces, traffic can be queued using strict priority (SP), weighted round robin (WRR), or low latency queuing (LLQ) methods. Both source and destination traffic types can be classified with either a DSCP or CoS value, and then assigned to one of the priority queues. The screenshot below shows where you enable QoS by interface.
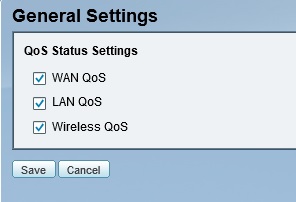
Cisco ISA550W QoS enables
WAN QoS configuration is a multi-step process. The steps include setting the uplink bandwidth of your WAN interface(s) and choosing a queuing method. SP queuing is good for voice, but may delay (“starve”) data traffic too much. WRR queuing is good for data, but may not provide enough priority for voice. LLQ queuing allows you to reserve bandwidth for a specific traffic type and specify queue priorities for remaining traffic.
With bandwidth and queuing selected, the remaining steps are 1) to create traffic classification selectors to identify which traffic is to be prioritized; 2) create a policy and rule to apply the priority to specific uplink or downlink traffic; and 3) apply that rule to a WAN interface. There are 53 predefined traffic types, more can be added based on protocol and port. One rule can be applied to each WAN interface in both the uplink and downlink direction. The ISA manual provides a nice example on how to configure Voice QoS for both uplink and downlink traffic.
On the LAN interfaces, traffic can be queued using strict priority, weighted round robin, or both. On both the LAN and Wireless interfaces, traffic can be classified with either CoS or DSCP markings. QoS for LAN traffic is then applied by queuing egress (outbound) traffic to either the wired or wireless interfaces.
Additional network options to mention include support for IPv6, port mirroring, port-based access control, IGMP, and VRRP. Finally, there are numerous network reporting options, including reports on traffic statistics, usage, and WAN bandwidth utilization. The screenshot below shows traffic statistics by port on the ISA550W.
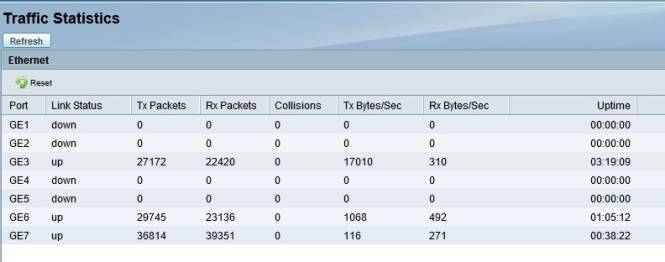
Cisco ISA550W Traffic Statistics
Wireless
Wireless options on the ISA550W are straightforward. I had no problem connecting to the ISA550W’s 2.4 GHz 802.11n wireless network with a Windows 8 laptop and an iPhone.
The ISA550W can operate in 802.11b/g, g/n, b/g/n, or n-only modes. The wireless channel can be set to auto or channel 1-11. Bandwidth can be set to 20 MHz or Auto. Wireless security options include Open, RADIUS, WEP, WPA , WPA/WPA2 and WPA2. WPA and WPA2 support either a shared secret key or enterprise (RADIUS) authentication.
Up to 4 different SSIDs can be broadcast, with each SSID mapped to a different VLAN. Up to 16 MAC addresses can be permitted or denied by SSID. A neat feature is that SSIDs can be enabled and disabled automatically by schedule. Below, I’ve set the guest SSID to be active from 9 AM to 6 PM daily.
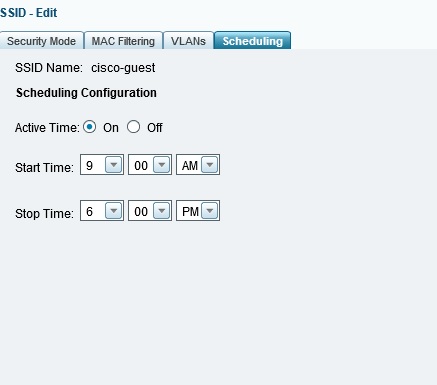
Scheduled SSID enable
Additional wireless options on the ISA550W include support for Wi-Fi Protected Setup (WPS), Rogue AP Detection, and Captive Portal. WPS is a bit unusual to support on a router intended for business, but there it is. Rogue AP Detection on the ISA550W will display detected wireless networks and allow you to simply mark them as authorized. The ISA550W does not restrict unauthorized access points.
The Captive Portal feature redirects wireless users to a web page to enter a user name and password, shown below, forcing them to authenticate before they are allowed to access your network.
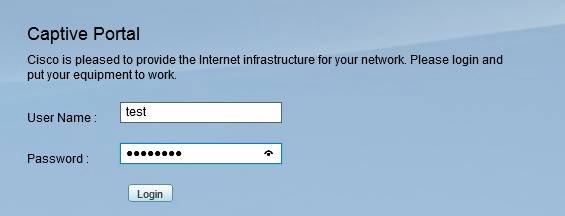
Cisco ISA550W Captive Portal
VPN
The ISA550W supports multiple VPN options with capacity for up to 25 site-to-site IPsec tunnels, 10 remote access IPsec tunnels, 10 remote access SSL tunnels, plus 10 remote access L2TP tunnels. PPTP tunnels are not supported.
An additional VPN option on the ISA550W is called Teleworker VPN Client. This option simplifies setting up an IPsec tunnel between two Cisco endpoints. In Teleworker VPN Client mode, the ISA550W will act as a VPN client and automatically set up a tunnel to another Cisco device. This would be useful for a remote office lacking the technical ability to configure and support VPN tunnels as this mode eliminates the need to install software on PCs and simplifies configurations on the ISA550W. Using this feature, however, disables traditional IPsec site-to-site and remote access functionality on the ISA550W.
I started by evaluating IPsec site-to-site tunnels. The ISA550W supports all standard IPsec options, including 3DES and AES encryption, as well as MD5 and SHA-1 authentication. Manual configuration of a site-to-site tunnel on the ISA550W is a bit detailed as it involves creating a transform set, an IKE policy, and an IPsec policy selecting your tunnel options.
Cisco simplifies the configuration of IPsec site-to-site tunnels with a wizard that walks you through the options. I used the ISA550W VPN configuration wizard to set up a site-to-site IPsec tunnel between the ISA550W and a NETGEAR SRX5308. I used 3DES encryption and SHA-1 authentication. Below is a screenshot of the ISA550W showing the status of my site-to-site IPsec tunnel.
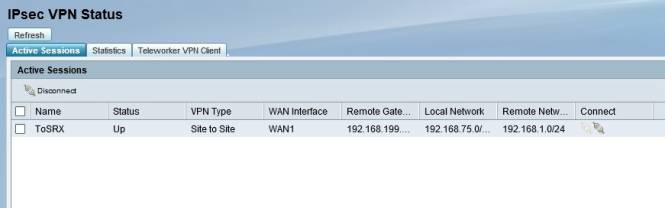
Cisco ISA550W IPsec status
Site-to-site VPN configurations were relatively easy, but I ran into a few hurdles getting remote VPN tunnels to work. In the end, however, I was able to remotely access the ISA550W via IPsec, SSL, and L2TP tunnels using a Windows 7 Pro PC.
For remote access IPsec tunnels, there is a wizard for configuring the ISA550W, which made the router configs easy. Cisco includes the IPsec client software on a disk that comes with the router. The part that threw me is the remote IPsec wizard has you create a group name and pre-shared key (PSK), plus a user name and password. The trick is to configure the IPsec client software with the group name and PSK, not the user name and password, circled below in the screenshot from the VPN client software.
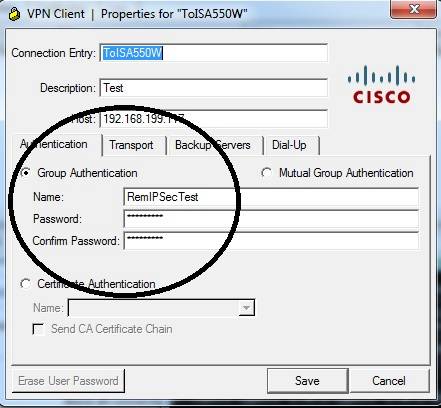
IPsec Remote tunnel configuration tip
Once I had my confusion sorted out (via a few emails with Cisco) and the configuration correct, the client successfully connected to the ISA550W. Note to Cisco: it would have been nice to get a few screenshots of both the client and router configs in the manual to make this easier. Below is a screenshot showing both my IPsec site-to-site and remote tunnels are up.
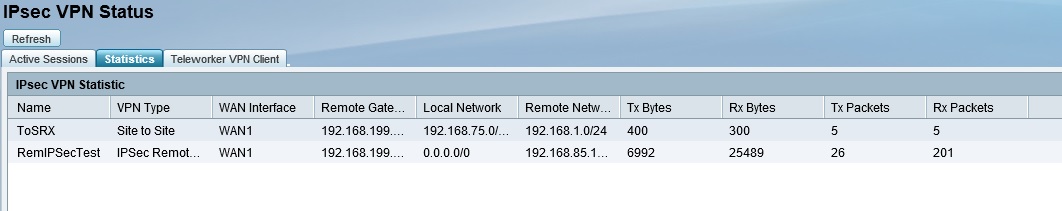
IPsec Site-to-Site & Remote tunnels up
The ISA550W also supports remote SSL tunnels and there is a wizard for configuring them. However, software needs to be installed on the PC for remote SSL access. On some VPN routers I’ve tested, such as the NETGEAR SRX5308, no separate software installation is required for SSL VPN tunnels—it is automatically installed during the connection process.
SSL VPN software is included on the disk that comes with the ISA550W. But for some reason, the software on the disk is in an image file (.iso) file that must be extracted using a utility such as 7-Zip before you can install it. I’m not sure why the software had to be packaged into an image file when the CD has only 90 MB of files on it!
Once I extracted and installed the software, I was again able to remotely connect to the ISA550W, this time via an SSL VPN tunnel. Below is a screenshot of a useful status page, showing the number of active SSL users along with various network statistics.
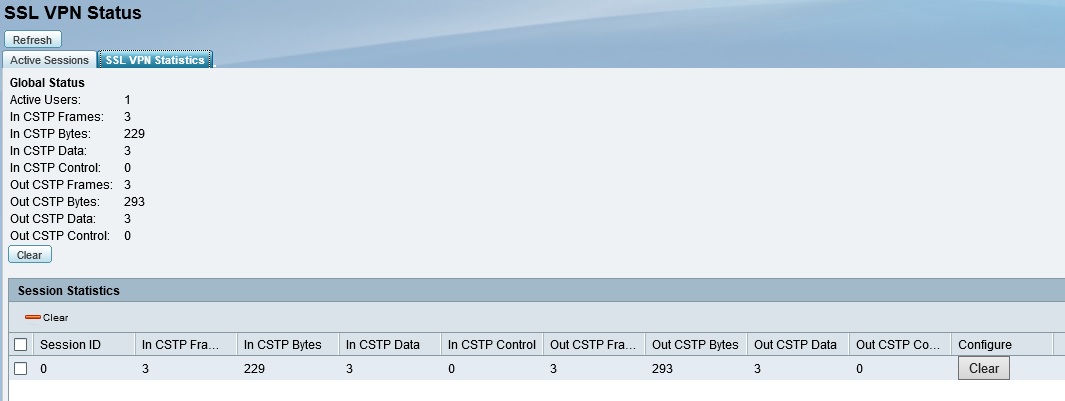
SSL tunnel Status
Lastly, the ISA550W supports remote access via L2TP tunnels. In this case, there is no wizard for configuring the router, so you have to manually enable the L2TP server and configure firewall rules on the ISA550W to allow access. L2TP software is included in Windows, so thankfully there were no client software challenges. Once L2TP was enabled on the ISA550W and configured on my Windows 7 PC, I was able to remotely connect to the ISA550W via an L2TP VPN tunnel.
I tested the ISA550W’s VPN performance with iperf using default TCP settings, with a TCP window size of 8KB and no other options. I ran iperf on two PCs running 64-bit Windows 7 with their software firewall disabled. (Running a simple iperf throughput test between two PCs uses the command iperf -s on one PC and iperf -c [ip] on the other PC.)
Cisco rates the ISA550W at 75 Mbps for IPsec throughput. (Note, NETGEAR rates the SRX5308 at 180 Mbps for IPsec throughput, thus the SRX5308 shouldn’t limit throughput on the site-to-site tunnel to the ISA550W.) Table 1 shows my VPN throughput measurements over the four tunnel types on the ISA550W.
| Tunnel Type | Client > Gateway | Gateway > Client |
|---|---|---|
| SSL | 0.67 | 14.3 |
| L2TP | 6.5 | 18.4 |
| IPsec | 91.6 | 91.6 |
| IPsec site-to-site | 67.8 | 107 |
Table 1: VPN Throughput (Mbps)
Notice in Table 1 the IPsec performance numbers at 91.6 Mbps in both directions using the IPsec client, and 67.8 Mbps / 107 Mbps in a site-to-site tunnel with the NETGEAR SRX5308. It is interesting the ISA550W exceeds the Cisco 75 Mbps rating on both client and site-to-site tunnels. In my experience, it is more common for a device to fall short of manufacturer ratings than exceed them.
Table 2 shows a VPN throughput table comparing IPsec client performance on the ISA550W to several VPN routers I’ve reviewed. Clearly, the ISA550W is head and shoulders above other devices in this table. (Note, you can click on the model number listed in the table to go to the review for each device.)
| Product | Client > Gateway | Gateway > Client |
|---|---|---|
| ISA550W | 91.6 | 91.6 |
| TL-ER6020 | 41.9 | 40.0 |
| Cisco RV180 | 39.7 | 50.9 |
| Cisco RV120W | 23.1 | 21.2 |
| Cisco RV220W | 38.3 | 49.3 |
| Cisco RV042 | 37.1 | 47.5 |
| Draytek 2920 | 17.8 | 17.8 |
| NETGEAR SRX5308 | 31.8 | 42.6 |
| NETGEAR FVS318N | 33.1 | 45.8 |
| Zyxel VFG6005 | 5.9 | 5.6 |
| TrendNet TW100 | 3.32 | 2.85 |
Table 2: IPsec Throughput (Mbps)
To wrap up my VPN discussion, the ISA550W has numerous VPN connection options and impressive IPsec throughput numbers, the fastest I’ve tested. If Cisco adds a few configuration examples showing both router and client configuration examples to the manual, the ISA550W’s VPN options will be even better.
Security
Security is an essential component of a UTM device. The Cisco ISA550W provides six key types of network protection, including spam-filtering, anti-virus protection, application controls, Intrusion Prevention (IPS), web filtering and network blocking based on IP. To use these six features, an annual license must be purchased from Cisco. I’ll cover the costs of that license at the end of this review.
The ISA550W leverages information from Cisco’s Security Intelligence Operations (SIO) to provide these security features. Cisco claims they have over 1.6 million security devices around the world communicating information about threats to the SIO daily. The information from these 1.6m devices produces up to 75 TB of new data daily to be filtered and added to a massive security database. Updates from this data are streamed back to the same devices, allowing Cisco security devices to learn from each other and block network threats that may have been experienced elsewhere across the globe.
Some of the security features update a database on the ISA550W from the SIO, others query the SIO in real time to filter traffic. As you can see in the screenshot, spam filtering and web filtering perform real time checks while anti-virus, network reputation, application control, and IPS update local databases from the SIO.
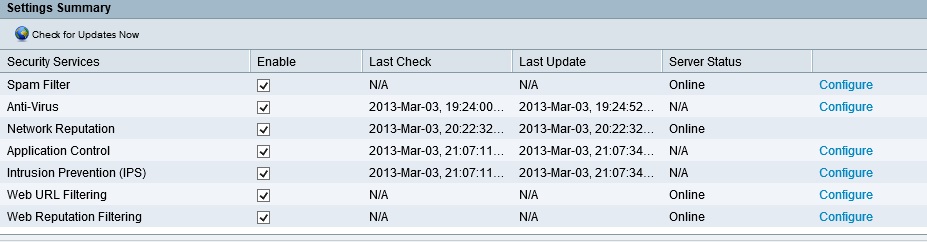
Security Service Status Summary
Spam filtering options on the ISA550W includes tagging or blocking known or suspected spam email based on reputation. Reputation is based on the email sender’s IP address “score.” Cisco’s SIO scores email IP addresses on a scale of -10 (bad) to +10 (good). You can set the ISA550W to filter email with a Low (-4), Medium (-3) or High (-2) reputation/score. You can customize it to filter spam at a higher or lower value as you choose. Known good email senders can be entered into an Allowed Senders list, bypassing the spam filter if needed.
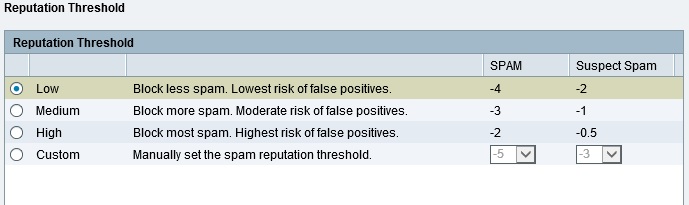
Spam Reputation Threshold
I did not test the ISA550W’s spam filter, but Cisco filled me in on how it works. The ISA550W filters for spam sent or received via SMTP ( = port 25). Thus, if you’re running your own email server which uses SMTP to send and receive email, the ISA550W will filter spam before it gets to your server, thus preventing it from getting to your clients. If you’re not running your own email server and your client email software uses POP3 (= port 110) to receive email, the ISA550W may not filter incoming spam.
A UTM device isn’t a replacement for host-based anti-virus software, but it can be a nice complement to your overall security plan. The ISA550W filters for viruses by comparing traffic to its virus database. The ISA550W gets its virus database from the SIO, which leverages Kaspersky’s database for virus scanning and Cisco’s SIO database to identify web sites containing viruses and malware. The ISA550W will scan HTTP, FTP, SMTP, POP3, IMAP, and NETBIOS traffic for virus signatures and either notify or block the traffic as desired.
An email notification can also be sent in the event a virus was detected. Below is the content of an email sent when I tried to download the eicar test file, a file that is useful for triggering anti-virus detection.
Alert – AntiVirus – Virus was detected in the file “eicar_com.zip” over a HTTP session.
Application control on the ISA550W is very configurable. Application signatures are downloaded from the SIO and are classified in 22 different categories. Each category has numerous listed applications.
Application policies can be created to permit or deny traffic based on category and application. Policies can then be applied based on network zone. The default policy is to permit all applications, so you have to either edit the default policy or create a policy and apply it to a zone to filter specific applications. I modified the default policy to block traffic to Facebook and received a “This page can’t be displayed” message when I tried to access the site. A screenshot of the application control policy edit page is below.
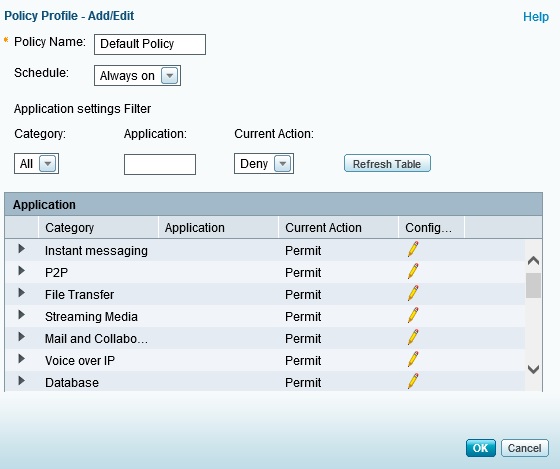
Application Control Policies
Intrusion Prevention Systems (IPS) inspect network traffic for threats like worms, spyware, and other undesirable traffic by comparing packets to a database of network threat characteristics, called signatures. The ISA550W will automatically update its intrusion prevention signature database from Cisco’s SIO on a regular basis. You can enable/disable IPS on the ISA550W, define which zones IPS will inspect, as well as enable or disable IPS blocking on any of the IPS signatures stored in the database. At the time of this writing, the ISA550W IPS feature recognized 1912 IPS signatures.
Web filtering is performed by reputation and URL. As stated in the ISA550W manual, “Web Reputation Filtering prevents client devices from accessing dangerous websites containing viruses, spyware, malware, or phishing links.” URL filtering is based on web site categories. Both filtering types are performed by real time checking the SIO database with each web site accessed.
Web site reputation filtering functions similar to spam filtering, with web sites being assessed a score from -10 (bad) to +10 (good). Web sites can be blocked based on settings of Low (-8), Medium (-6) or High (-4), or a custom level. Up to 16 websites can be omitted from web reputation filtering.
Website URL filtering is similar to Application Control, relying on policies and zones. There are 65 different web site categories that can be blocked or permitted. Up to 32 exceptions can be added to each policy to permit or block specific websites.
I modified the default policy to block traffic to URLs in the Computer and Internet category, which blocked access to the SmallNetBuilder website with the message shown below.
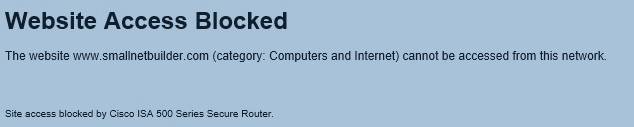
URL Blocked message
Per the ISA550W’s manual, the “Network Reputation filter blocks incoming traffic from IP addresses that are known to initiate attacks throughout the Internet.” This feature isn’t adjustable, it can only be enabled or disabled.
The ISA550W provides a Security Services Report, showing activity levels and actions for each of the six types of network protection. Specific incidents can be examined more closely to see action has been taken. Below is a screenshot showing the activity where traffic to Facebook was blocked by the application control feature.
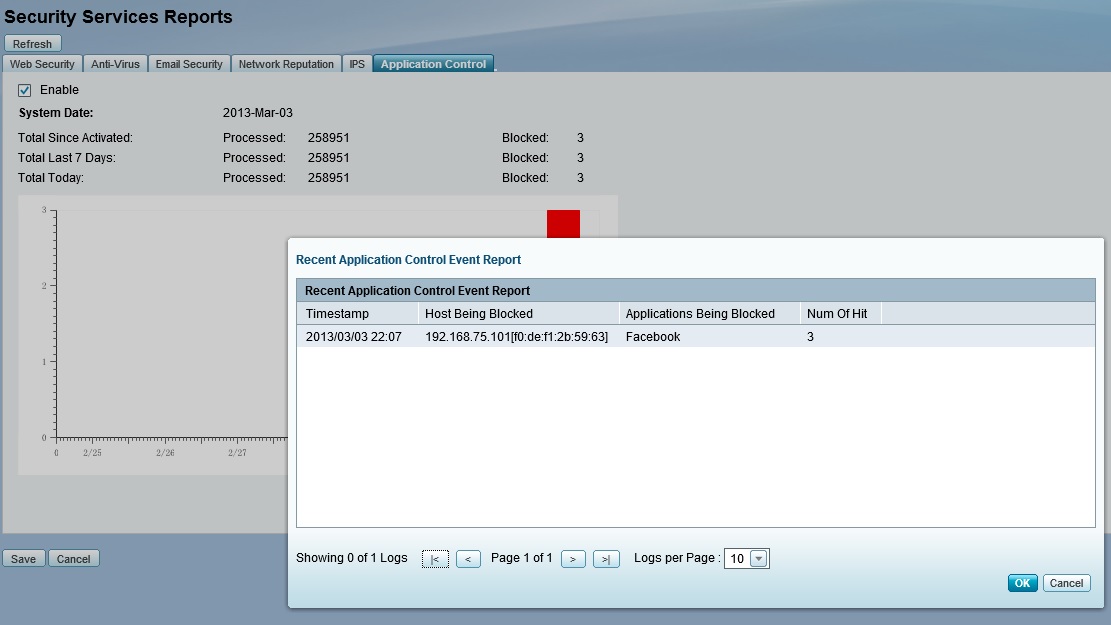
Security Services Report
Firewall
The ISA550W has a zone-based firewall. Note that the firewall functions in the ISA550W do not require the annual license as discussed in the security section.
Predefined zones include the LAN, WAN, DMZ, VPN, SSLVPN, GUEST, and VOICE zones. Additional zones can be created in the Networking menu. Each zone is assigned a trust level from 0 (Untrusted) to 100 (Trusted). Interfaces or VLANs are then assigned to a zone.
Firewall rules, or Access Control Lists, can be created to permit or deny traffic based on source and destination zone, traffic type, source and destination IP or MAC addresses. In the below example, I created a simple rule to deny all HTTP traffic going through the ISA550W. It worked as expected, no one was able to access web sites while this rule was in place.
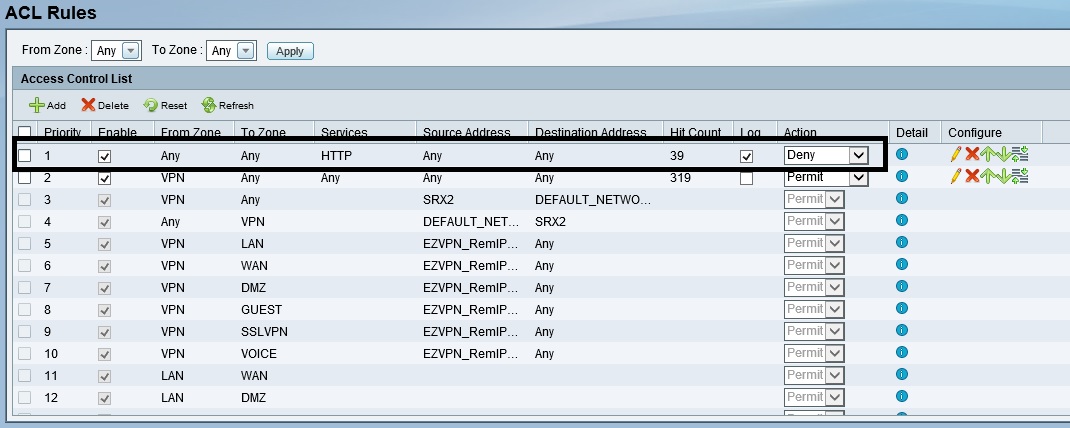
Firewall ACL Rules
Multiple options exist for Network Address Translation as well. By default, the ISA550W will perform Dynamic PAT (Port Address Translation) out the WAN interfaces. PAT is what most of us think of when we think of NAT. Static NAT rules, Port Forwarding, Port Triggering, and complex NAT rules can also be created to manage traffic source and destination addresses as traffic passes through the router.
If you’re not going to use the Web Reputation and URL Filtering feature, you can set up simple firewall rules to block up to 32 websites or keywords and apply them by zone. You can also enable an Application Layer Gateway feature to manipulate traffic headers on SIP, H.323, and FTP traffic.
Other protections in the ISA550W firewall include protection against TCP and UDP flooding and DoS attacks. Session limits can be set to limit the total number of traffic flows on the router, with a maximum limit of 60,000 connections.
Routing Performance
Routing performance for the ISA550W, loaded with 1.1.1.17 firmware and using our standard test method, is summarized in Table 3. We had to create Advanced NAT and firewall rules to allow all services from WAN to LAN test clients and disable Firewall > Attack Protection > Block UDP Flood to run Max Session test.
With just the firewall enabled, Cisco rates the ISA550W at 200 Mbps. As you can see from Table 3, the ISA550W meets or exceeds that rating.
| Test Description | ISA550W |
|---|---|
| WAN – LAN | 200.2 |
| LAN – WAN | 255.0 |
| Total Simultaneous | 252.2 |
| Maximum Simultaneous Connections | 34925 |
| Firmware Version | 1.1.1.17 |
Table 3: Routing throughput
The above measurements were performed with only the firewall on the ISA550W enabled. UTM security features such as IPS and anti-virus reduce throughput significantly. With IPS enabled, Cisco rates the ISA550W as capable of 60 Mbps throughput. With all UTM features enabled, Cisco rates the ISA550W at 45 Mbps.
Using the same Iperf methodology I described in the VPN section, I measured the ISA550W throughput with its security features disabled and enabled. Average throughput on the ISA550W with all UTM features disabled was 153 Mbps. Average throughput on the ISA550W with IPS enabled was 47.3 Mpbs. Average throughput on the ISA550W with all UTM features enabled was 44.5Mpbs.
In Table 4, I’ve compared the Cisco ISA550W throughput with the UTM features on and off to previous UTM devices I’ve reviewed, including the SonicWall TZ100W and the Zyxel USG100. As you can see, the Cisco ISA550 produces much higher throughput.
| Router | UTM On (Mbps) | UTM Off (Mbps) |
|---|---|---|
| Cisco ISA550W | 44.5 | 153 |
| SonicWall TZ100W | 31.3 | 78.2 |
| Zyxel USG100 | 16.5 | 82.5 |
Table 4: UTM On / Off Throughput Comparison
Wireless Performance
All testing was performed with 1.1.1.17 firmware using our standard test process, which uses Channel 1 for 2.4 GHz tests. The test client was our standard Intel Centrino Ultimate-N 6300 with Win7 13.5.0.6 driver.
The ISA550W is Wi-Fi Certified and defaults to auto channel selection and auto 20/40Mhz mode on startup. It also defaults to no wireless security set and WPS disabled. After setting WPA2/AES security and enabling WPS, the client did not prompt for WPS session upon first association, however. So we manually set up WPA2/AES for our test client for all wireless testing.
We did not test to see if the ISA550W obeyed 40 MHz coexistence rules or Fat Channel Intolerant bit enable.
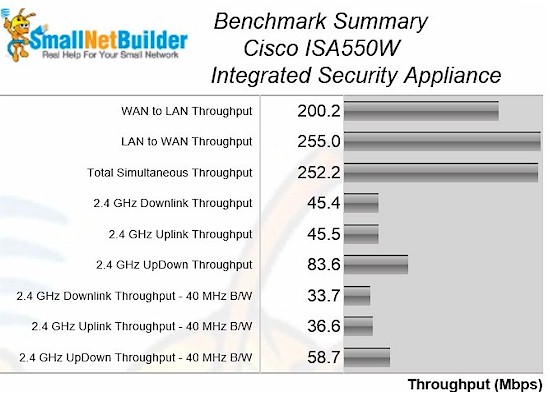
Benchmark Summary
I ran a simple comparison of overall average performance by filtering the charts for single-band routers only for the 20 MHz mode wireless benchmark. (The charts have been trimmed for space reasons.)
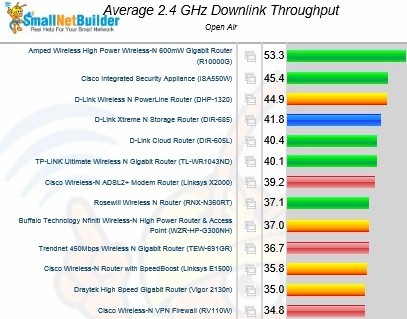
Overall 2.4 GHz downlink performance comparison
The charts above for downlink and below for uplink show the ISA550W in second and third place, respectively. This is impressive, especially considering that the wireless integrated into many security-focused appliances usually seems like an afterthought with middling performance.
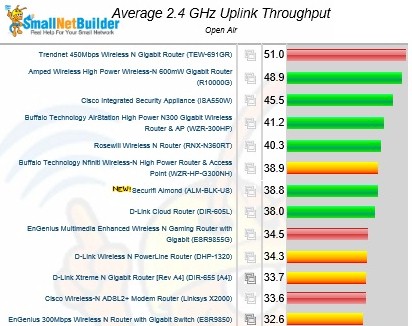
Overall 2.4 GHz uplink performance comparison
Closing Thoughts
Cisco ISA500 series devices can be purchased on line with a 1 or 3 year warranty, support and UTM license. Table 5 shows pricing as listed on Pricegrabber.com as I write this.
| Model | 1 year | 3 year |
|---|---|---|
| ISA550 | $272 | $398 |
| ISA550W | $323 | $434 |
| ISA570 | $485 | $742 |
| ISA570W | $578 | $794 |
Table 5: Cost comparison, 1 and 3 year licenses
Specifically for the ISA550W, if you purchase it with a 1 year contract, you can extend just the support contract to 3 years for $69, which covers technical support and firmware upgrades. Extending the license for the UTM security features will run $187 for a 1 year term or $352 for a 3 year term. Similar pricing applies to the other models.
I tested a SonicWall TZ100W UTM device back in 2009, and was impressed with its throughput at the time. However, the TZ100W I tested in 2009 doesn’t have the speed of today’s ISA550W. Based on specs, SonicWall’s TZ200W is a more apples-apples competitor for the ISA550W. The TZ200W and ISA550W have very similar VPN and UTM specs, but the ISA550W has a higher firewall throughput rating (200 Mbps vs. 100 Mbps). Moreover, Pricegrabber.com shows the TZ200W at $459, over $125 more than the ISA550W.
From a performance standpoint, the ISA550W is quite impressive. VPN, routing and wireless throughput on the ISA550W are all quite respectable. It would be nice if configuration performance were a little faster. But it’s better to have fast network throughput than a quick configuration menu.
From a security standpoint, the ISA550W has Cisco’s SIO team and 1.6 million other devices around the world providing it with the latest protections and updates. Alltogether, the Cisco ISA550W makes a pretty solid argument to be your Unified Threat Management device.
