Introduction

| Tritton Advanced Server Appliance with WebServer | |
|---|---|
| Summary | SPI-based router with IPsec and PPTP VPN endpoints and 120GB NAS. Also supports Web and FTP serving. |
| Update | 4/14/2004 – Corrected NAS throughput result observations (again).
3/5/2004 – New firmware released by ioGEAR and Tritton. ASAP has new packaging. Corrected NAS throughput observations. Other miscellaneous changes. |
| Pros | • Fast routing speed • Supports two WAN IP addresses (Multi-NAT) • Priced comparably to separate solutions |
| Cons | • File sharing is exposed to WAN • No DMZ • No port range forwarding • Limited file sharing privilege control • Admin requires Internet Explorer |
In their search for ways to differentiate themselves (and improve their miserably thin margins), networking product manufacturers are once again venturing into bundling network storage capability into their routing offerings. This idea of a combination router / file server isn’t new, given that SMC and Linksys both fielded very similar products (OEM’d from Sercomm) back in 2001.
But if I remember correctly, the first-generation product – I tested SMC’s SMC7208SBR Broadband Storage Server – was expensive, insecure, large, noisy and didn’t really take off. U.S. Robotics’ USR8200 Secure Storage Router Pro recently attempted to re-establish the router / storage combo category but requires you to bring your own storage – in the form of a USB2.0 hard drive.
Tritton’s All in One Server Appliance (ASAP) and ioGEAR’s Broadband Office Storage Server (BOSS) represent the latest incarnation of this product category, which now has the intended-to-be-less-scary “appliance” moniker. Unfortunately, though drive sizes have increased from 20GB to 120GB over three years, little else seems to have changed…
Basic Features
The BOSS and ASAP are internally twins (except for a few minor differences in indicators), but have slightly different plastic exteriors. Both have a footprint slightly larger than a typical computer language programming book but are considerably heavier – thanks to their internal 3.5 inch 120GB hard drives.
Both products have similar front panels with PWR, HD (activity), Link/Activity 10/100 for all four switched 10/100 LAN ports and single 10/100 WAN port indicators in common. The products differ in that the BOSS has four System Activity lights – which aside from continuously sequencing back and forth, perform no useful function as far as I can tell – and the ASAP has a single continuously blinking HB light. The BOSS’ indicators also seemed to be brighter and viewable from a wider angle than the ASAP’s.
The ASAP also has two banks of four lights marked Incoming and Outgoing over where the BOSS’ System Activity lights are. These apparently are intended to indicate download and upload Internet speed, but that conclusion is from observation, since neither their existance nor function is described in the hardcopy “Server Appliance User Guide” included with the ASAP.
The rear panel on both products is almost identical containing Power jack and switch, single 10/100 Ethernet WAN port, WAN port MDI / MDI-X switch, four 10/100 Ethernet LAN ports and Reset (to factory defaults) switch. The reason I say “almost” is that the WAN port MDI / MDI-X switch positions are reversed from product to product. Also note that, contrary to what the User Guides say, the LAN ports do not have auto MDI / MDI-X capability.
The products present very different first impressions, by the way. The BOSS’s box has attractive, informative graphics and text on the outside, and the product is safely nestled in a molded plastic box liner under a clear plastic cover. The ASAP’s packaging is much plainer, with no product pictures or graphics on the outside and the product loosely sitting in a cardboard box liner, which isn’t strong enough to hold it securely during shipping – judging from the tears on all four corners of the liner.
Update 3/5/2004 – Tritton says they have improved their packaging which now uses a white form fit plastic insert that secures the product with a plastic see through window that encloses the product. This now makes it the same as the BOSS’ packaging.
Both products come with power and Ethernet cables, but the BOSS opts for a printed Quick Start Guide poster and PDF User Manual on CD, while the ASAP comes only with a printed User Guide, which apparently was done by the product’s OEM, since it lacks any refererence to Tritton whatsoever.
Internal Details
Removing the plastic top cover reveals the hard drive, which is suspended above the main board on a sheet metal frame (Figure 1). Both products use 3.5 inch 120GB 7200RPM drives with my ASAP sample sporting an IBM/Hitachi IC35L120AVV207 while my BOSS review unit came with a Samsung SP1230N.

Figure 1: Tritton ASAP with cover removed
Removing the hard drive frame reveals the main board (Figure 2), which is based on a Toshiba TMPR3927CF 32 bit RISC-based CPU, with 8MB of RAM and 1MB of Flash.
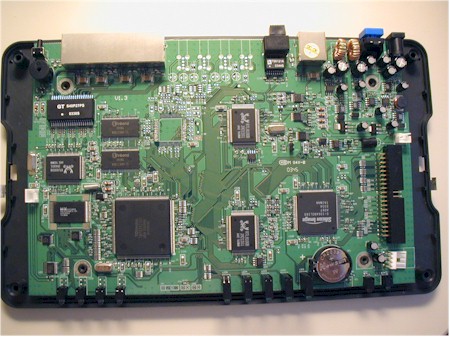
Figure 2: ioGEAR BOSS with hard drive assembly removed
A Silicon Image SiI 0649 Ultra ATA/100 host controller, two Realtek RTL8100B 10/100 Ethernet controllers and RTL8305SB 5-Port 10/100M Ethernet Switch make up the rest of the major board components.
One missing component bears special mention, by the way. Neither the ASAP or BOSS have a cooling fan, and as a result, run very quietly. This is a big plus in my book!
Update 3/5/2004 – More information about what makes the ASAP / BOSS tick and who really makes it can be found here.
Setup and Administration
Aside from cosmetic differences (including the absence of Tritton branding in the ASAP’s interface), default IP (BOSS = 192.168.2.1 / ASAP = 172.16.1.1) and the inclusion of web server capbilities on the ASAP, the user interfaces of both products are identical. So as I run through the admin capabilities, you can assume that the screen shots you see are the same on both products unless otherwise noted.
The internal DHCP server comes enabled, so if you know how to do a DHCP release / renew (or where the XP Repair button is) you should be able to grab a suitable IP address and log in with the same default password. If you’re using Internet Explorer 6.0 or higher with Windows (or IE 5.2 or higher with MacOS) you should be directed to the System Information page shown in Figure 3 upon login. If you use any other browser (I tried Mozilla 1.6b), you’ll get a 403 Forbidden screen with “Current version only supports “Internet Explore 5.0″ or above” message.

Figure 3: ASAP System Information page
Even when I used the required browser, the ASAP refused to send me directly to the System Info page once I logged in – instead presenting me with IE’s dreaded “This page cannot be displayed” page. After some futzing around, I found that clicking the Detect Network Settings link on that page finally coughed up the System Information page about 10 seconds later. This problem seems to be client system specific (probably due to IE’s version) and doesn’t happen on the BOSS, which came with newer firmware (1.42) than the ASAP. When I told Tritton about the problem, they offered to send me the same rev firmware as the BOSS had, but don’t post that firmware for download from their website.
Attempts to access the admin server from multiple computers revealed that once you’re logged in, admin access attempts from any other clients will be met with a “403 Forbidden” response. I couldn’t find an admin logout button, so had to wait out the non-adjustable admin timeout (which I think is 5 minutes) or resort to rebooting the product in order to allow a different client to access the admin server.
On a more positive note, remote admin worked ok (except as noted above) and you can set the port it operates on, but can’t restrict access to specific IP addresses. The admin interface also responded quickly and most changes were accepted without requiring a long reboot cycle.
Moving on, Figure 4 shows that PPPoE, PPTP, DHCP and Fixed IP address WAN connection types are supported.
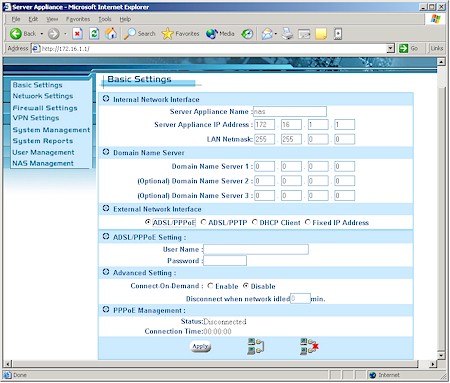
Figure 4: ASAP Basic settings
This will probably handle most users’ needs, but note that Domain and Host name authentication options aren’t supported and WAN MAC address spoofing is supported only when using the DHCP client connection type. There’s also no way to adjust MTU, which could present problems for PPPoE / PPTP users or VPN connections.
Firewall Features
Given the premium price that ioGEAR and Tritton are asking for their products, I was surprised to find the products’ firewalls both missing important capabilities and buggy in the features they did have. But in the interest of trying to stay positive, I’ll cover the better stuff first.
The ASAP / BOSS has two capabilities not typically included in consumer routers – Multiple NAT and IP Alias. Multiple NAT allows users that have multiple public IP address from their ISP to assign specific LAN clients to share a particular public IP address. This is mostly useful for business users and most useful for distributing server load.
The IP Alias feature – a first for me – lets you have LAN clients in up to three IP address ranges in addition to the 172.16.1.X or 192.168.2.X supported by the ASAP and BOSS’ default settings. This could be handy for larger networks, or those with statically assigned IP addresses.
You also get to control some of the Stateful Packet Inspection (SPI) aspects of the firewall via the Denial of Service page (Figure 5).
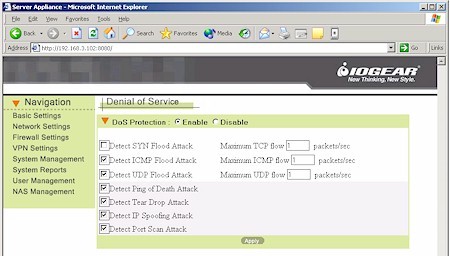
Figure 5: BOSS Denial of Service settings
Access to Internet services is controlled by the IP Filter capability, which provides five sets of IP address ranges that can each have four single ports and one port range blocked (Figure 6). But since the IP Filter Group must be specified in “slash” notation (example 172.16.1.0 / 24), you’re pretty much limited to having the filters apply to all clients on your LAN – not very helpful.
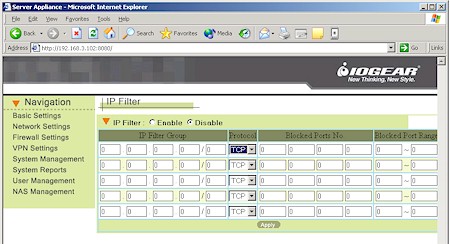
Figure 6: BOSS IP filter settings
From these high points, however, the firewall feature set heads steadily downhill. First, you can forward only ten, single, static IP addresses via the Virtual Server feature, and neither port ranges, nor triggered mapping nor “loopback” is supported. You currently can’t even make up for the miserly number of forwarded ports by using DMZ, since it’s not available either. When I asked about these missing features, ioGEAR said they will be added in a future firmware release, while Tritton would say only that they’ll “look into” adding the features.
Next, though you get ten URL filters, they aren’t very robust. You can’t enter keywords and instead must enter URLs with a.com,.net, etc. (i.e. “yahoo.com” not just “yahoo”). I found that sub-domains (i.e. mail.yahoo.com) are not automatically handled and you can’t enter a sub-domain wildcard (i.e. *.yahoo.com) either. By the way, note that the URL filters, IP filters and Virtual Servers aren’t schedulable, a feature found on routers costing far less.
The worst “feature”, however, is the major security hole opened as soon as you enable the ASAP / BOSS’ file sharing features. I’ll describe that later in the File Sharing section, but for now, let’s move on to the VPN features and performance.
VPN
The PPTP and IPsec capabilities are not a strong point of the ASAP / BOSS duo. Figure 7 shows the simple setup screen for the PPTP server, which users experienced with PPTP setup should be able to figure out.
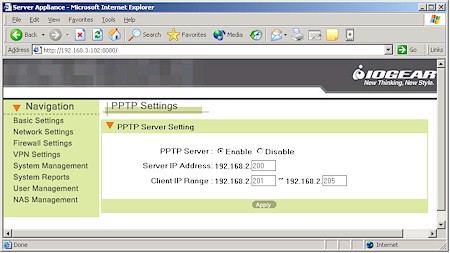
Figure 7: BOSS PPTP Settings
Since I’m not in that category, however, I needed more help, which I didn’t find in either User manual. Fortunately, ioGEAR has a Support Note that, though flawed, gave me the clues that I needed to get my WinXP client successfully connected via a PPTP tunnel.
Once you set up the PPTP server, you’ll also need to make a visit to the Users page (more later) to set up an account for each user who’ll be using the PPTP server. Once you do connect, note that since NetBIOS broadcast isn’t supported, you’ll need to find your way around the remote network by using the IP address of the computers that you wish to connect to.
I hope purchasers looking to use more secure IPsec VPN capabilities of the ASAP / BOSS have more luck than I did. Figure 8 shows the very limited IPsec configuration options, which provide no indication of either encryption or authentication options.
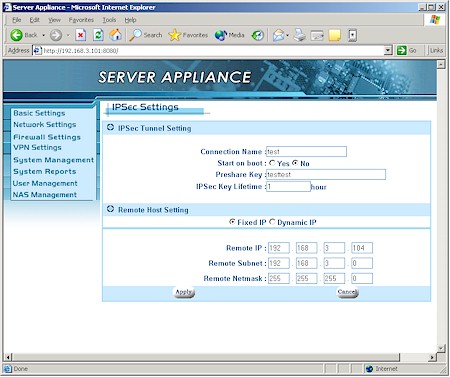
Figure 9: ASAP IPsec Settings
The manual was useless, and requests to both Tritton and ioGEAR for a detailed IPsec setup example were fruitless (I did learn that Perfect Forward Secrecy isn’t supported, however). And if you decide to try to figure it out yourself, the IPsec client you use better give you any debugging information you need since tunnel setup logging isn’t available for either PPTP or IPsec!
If you need to connect to a remote VPN gateway through the router, PPTP and IPsec pass through are supported, but not L2TP. Both companies say there is no hard limit on the number of pass through sessions, and that they can connect to multiple remote gateways. Forget planning on setting up your own PPTP or IPsec gateways behind the product, however, since the Virtual Server feature won’t support the protocols required for either VPN method.
VPN Performance
Figure 10 shows a composite Chariot plot of PPTP throughput test results in both Local-to-Remote and Remote-to-Local directions that I took using the BOSS.
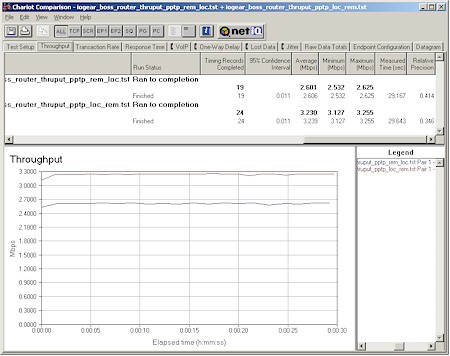
Figure 10: BOSS PPTP throughput
The PPTP client was a 1GHz Celeron-based notebook running WinXP home and using Microsoft’s built-in PPTP client. Note that these results were obtained with no other traffic running through the router and no other active applications besides Chariot and its endpoint running on the test pair machines. The 3.2Mbps best-case throughput is enough to keep up with most broadband connections, but less than half what I measured for the USR8200. Streaming performance wasn’t as good, however, with the 500kbps test stream rate cut just about in half and about half the data lost.
Though I couldn’t test IPsec tunnel performance, it’s sure to be considerably lower than PPTP throughput, due to the increased compute requirements of IPsec’s stronger encryption and the lack of any hardware encryption capability in the ASAP / BOSS’ design. Both products say they support up to 20 IPsec tunnels, but I doubt most users would be happy with the tunnel throughput with even half that many running simultaneously.
IPsec VPN Performance Test Results
| Test Description | Transfer Rate (Mbps) [1 MByte data size] |
Response Time (msec) [10 iterations 100 Byte data size] |
UDP stream [10s @ 500kbps] |
|
|---|---|---|---|---|
| Actual throughput (kbps) | Lost data (%) | |||
| Local to Remote | 3.2 | 4 (avg) 5 (max) |
259 | 47 |
| Remote to Local | 2.6 | 3 (avg) 5 (max) |
266 | 46 |
| Firmware Version | 1.39 | |||
See details of how we test.
Logging and Other Stuff
I’m not going to spend much time describing logging capabilities because, frankly, they look mostly broken to me. All the System Log shows is Startup and some DHCP lease info, the URL Log shows one URL per client IP address and I never heard a peep from the email Event Report capability even when I port-scanned the crap out of both products. The DHCP Lease report appears to be the only logging feature that works correctly.
Besides the Multi-NAT and IP Alias features I mentioned above, there are a few other miscellaneous features:
- you can set five static routes
- dynamic DNS is supported for dys, dynDNS, dyns, easydns, justlinux, ods, pgpow and TZO service providers
- SNMP management is supported
- there’s a real-time clock, but it doesn’t appear to automatically set itself from an NTP server
Routing Performance
Straight routing performance was in line with current-generation products at around 16Mbps and LAN-WAN UDP streaming was slightly lower than the 500kbps stream rate.
WAN-LAN streaming results are missing since I couldn’t run the test due to interaction between Qcheck and the ASAP / BOSS SPI-based firewall – a common side-effect of SPI+NAT routers.
Routing Performance Test Results
| Test Description | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
|---|---|---|---|---|
| Throughput (kbps) | Lost data (%) | |||
| WAN – LAN | 16.3 | 1 (avg) 2 (max) |
||
| LAN – WAN | 15.3 | 1 (avg) 1 (max) |
497 | 1 |
| Firmware Version | 1.39 | |||
See details of how we test.
Storage and File Serving
I hoped the file sharing side of the ASAP / BOSS twins would offset the weaker routing side. But instead I found file sharing to be just as problematic.
Figure 11 shows the first NAS Management screen, which allows you enable file sharing, adjust the drive idle power down time, intialize the disk and monitor the total available space. There’s no ability to set quotas or have a warning issued when disk capacity is running low.
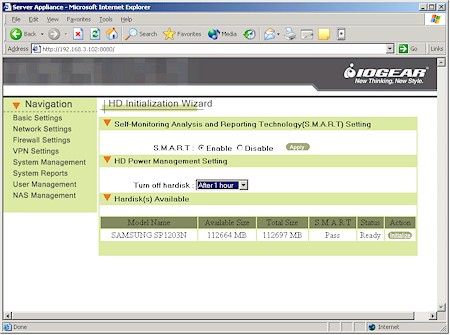
Figure 11: BOSS HD Initialization
The Advanced Settings (Figure 12) consist of enables for the supported file sharing protocols (NetBIOS, AppleShare over IP and NFS) and the built-in FTP server.
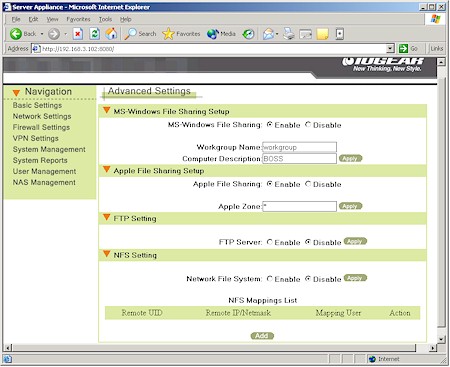
Figure 12: BOSS NAS Advanced Settings
But I was shocked to learn when I port-scanned both products that enabling each of these services also exposes those ports on the WAN side of the router! This is totally unacceptable from an Internet security viewpoint, since exposing any of these well-known ports virtually guarantees that your network will be come a target for a variety of unwelcome attention.
Update 3/5/2004 – Tritton and ioGEAR have released firmware updates that they say fix these security problems. I have not verified that they work.
Once the ports are exposed, only your username / password combination stands between the Internet and your LAN’s security, which is a position I certainly wouldn’t want to be in. Forget using the IP Filter capability as a patch, since I tried it and it doesn’t appear to apply to any of these services.
It’s also important to note that user / group permissions apply to all services. I found this out when I enabled FTP and found that anonymous read / write access was turned on! It turned out that the default guest user account that I was using to enable file sharing access without a password also left my files wide open to the Internet via FTP.
When I pointed out this problem to both vendors, ioGEAR said the open file sharing ports were “needed for file sharing via SAMBA” and Tritton didn’t answer the question. Tritton also didn’t respond to my query regarding anonymous FTP access and ioGEAR’s response said, in part, “This is not a security type product”. I found this a curious response, given that the product has the security features of both PPTP and IPsec endpoints built in.
To ioGEAR’s credit, however, they also said they’d work on improving security and would issue a TIL (applications note) and product insert that would describe the issue. Since I suspect this issue will be passed back to the OEM / ODM that actually makes the product, I can only hope that any security improvements will appear in both products.
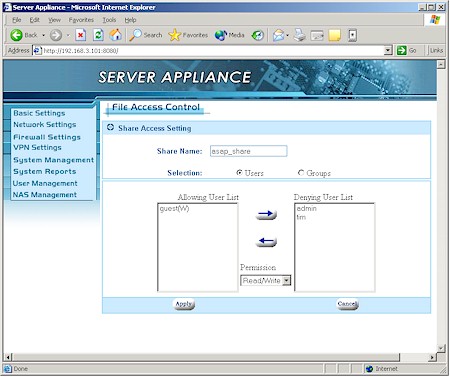
Figure 13: ASAP NAS File Access Control
Figure 13 shows the extent of the Access Control you have over files stored on the ASAP / BOSS. Only folder (directory) level permission can be set, though you can define Group level privileges for groups of users. As I mentioned before, these privileges apply to all protocols.
The ASAP recently added webserving capability (Figure 14) to its feature set, but the BOSS hasn’t.
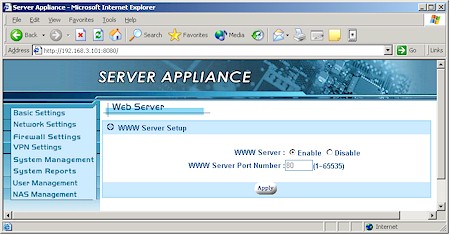
Figure 14: ASAP Web Server setup
Enabling the webserver and setting a port number automatically creates a “www” folder assigns it “guest” (i.e. no password) permissions, and opens the selected port in the ASAP’s firewall to allow access from the Internet. But since permissions can’t be set by service, the “guest” permissions also allow anonymous FTP access – another very insecure default setting.
Removing “guest” permission shut off anonymous FTP, but left the webpages accessible by anyone. Anyone, that is, using Internet Explorer. When I tried hitting the index.html page that I uploaded, Mozilla presented me with the actual HTML for the page instead of the rendered HTML! Neither IE nor Mozilla automatically displayed the “index.html” page when I entered the ASAP’s WAN IP address into my browser, contrary to what the printed web server instruction sheet that came with the ASAP said.
File Sharing Performance
Since I’ll be testing more NAS devices, I figured it was time to come up with a better performance method than the Windows drag-and-drop that I’d been using. After evaluating a number of tools, I settled on IOzone, which I’ll be using until something better comes along. The full testing setup and methodology are described on this page, so I’ll just concentrate on the results here.
IOzone runs a series of read and write tests using different record and file sizes. But to keep the comparison plots simple, I use only the results from writing and reading a 4MByte file – which are representitive of performance with other file sizes. Note that the plots’ Y axis has a logarithmic scale, for reasons you’ll see shortly.
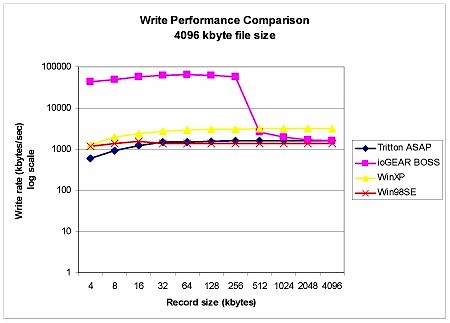
Figure 15: Write performance comparison – 4MByte file size
Figure 15 shows that the ASAP’s write performance is similar to writing to a shared Win98SE folder – around 1.5MBytes/sec – but with very different results for the BOSS! I ran this test three times and each time the BOSS’s write performance for record sizes smaller than 512 kBytes was a phenomenal 43 – 65MBytes/sec! My only explanation for this is that there must be a significant difference in caching between the ASAP’s Hitachi / IBM and BOSS’ Samsung drives.
Update 3/5/2004 – Helpful reader Roy Franz pointed out my math error in that it’s not possible to get the 43-64MBytes/sec I measured from a 100Mbps Ethernet connection. So I can only conclude that IOzone’s results for the BOSS write tests are incorrect and should not be used.
Update 4/15/2004 – Don Capps, the current maintainer of iozone set me straight with some very helpful and useful information about iozone. The gist of it is that the >50MByte/sec speed that I got from the BOSS’ test run is due to Windows file caching effects and not an IOzone error.
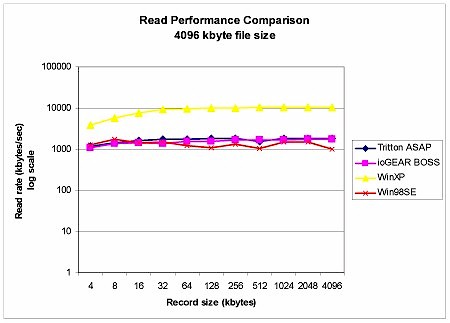
Figure 16: Read performance comparison – 4MByte file size
Read performance (Figure 16) was more consistent, with both the ASAP and BOSS ranging between 1.1 – 1.8MBytes/sec. This was slightly better than a Win98SE shared folder, but not as good as the shared WinXP folder, which averaged almost 9MBytes/sec.
Since this is my first use of a new NAS evaluation tool, I can’t compare these results to any previously tested NAS devices. But suffice it to say that if you’ve been sharing files using shared folders on a Windows machine, in most cases you probably won’t notice any performance difference – for better or worse – when using the ASAP or BOSS.
Wrap Up
As you can probably tell, I wasn’t impressed with either the ASAP or BOSS, because:
- the firewall features are meager and are harder to configure than stand-alone routers costing much less
- PPTP VPN throughput is ok for light use, but IPsec will be marginal – if you can get it to work
- you can’t restrict file sharing, FTP or webserving (ASAP only) to LAN-side only, and worse, these services are exposed by default to the Internet when enabled
The most positive thing I can say is that it pricing isn’t out of line. The lowest street prices I found (at the time of review) for the ASAP and BOSS were $360 and $328 respectively. Most current 120GB NAS devices are street-priced around $300, and an IPsec endpoint router is going to run you at least $50. Since you also get an FTP server and PPTP VPN endpoint with the ASAP and BOSS, you could argue that these products even have a pricing advantage over what you could assemble yourself from off-the-shelf networking gear. (Yes, I know you could do all this cheaper by rolling your own with Linux, so hold the emails, please.)
Maybe it’s just me, but I just can’t get past the gaping Internet security hole unsuspecting users will expose as soon as they turn on the file sharing features that compelled them to buy the ASAP / BOSS in the first place. Until these are fixed, I’d just say “No” to either product.
