Introduction

| At a Glance | |
|---|---|
| Product | D-Link DAP-2555 AirPremier N Dual Band, PoE Access Point powered by CloudCommand (Visit Website) |
| Summary | Cloud-managed single radio 2.4 / 5 GHz 802.11n access point for the small businesses. |
| Pros | • Easy setup • Inexpensive compared to competition • Works through NAT firewalls without port mapping • Can still use as normal AP after one-year initial service bundle expires. |
| Cons | • No WEP or WPA / TKIP support • Can’t control channel bandwidth mode • Doesn’t default to 20 MHz bandwidth in 2.4 GHz • Reporting might be inadequate for larger networks |
Anyone who has tried to install and manage a multi-AP wireless network using browser-managed gear understands the value of centrally-managed WLANs. Unfortunately, the pricing of systems from Cisco, Meraki, Ruckus, etc. puts managed Wi-Fi systems beyond the reach of most small businesses that could benefit the most from them.
Part of the high cost is in the access points themselves, although in some cases this more a reflection of what the market will bear rather than higher cost of material of the APs themselves. But another piece of the cost is the hardware controller(s) required to manage the APs.
What D-Link’s partner PowerCloud Systems has done is develop a cloud-based system for managing network equipment. PowerCloud’s technology, called CloudCommand, isn’t limited to managing wireless networks. But it’s PowerCloud’s first application with D-Link as their first equipment customer.
Meraki also uses a cloud-based management system for its rather pricey access points that I reviewed last year. So I’ll be making some comparisons to Meraki as we go along.
The first comparison is that D-Link is aiming at smaller networks than Meraki. D-Link’s sales material describes the target customer as having 5 to 300 employees and / or 10 to 100 computers, where Meraki has a broader target of 50 to 5000 users.
D-Link and PowerCloud are focusing on penny-pinching businesses that have little or no IT support, but need multiple access points to get the job done. D-Link is also pitching to VARs, who might be responsible for multiple networks, some of which could be multi-site.
Because the system controller is in the cloud, CloudCommand is designed to handle networks with multiple APs in multiple locations, and even on multiple networks, as easily as those at a single site (Figure 1).
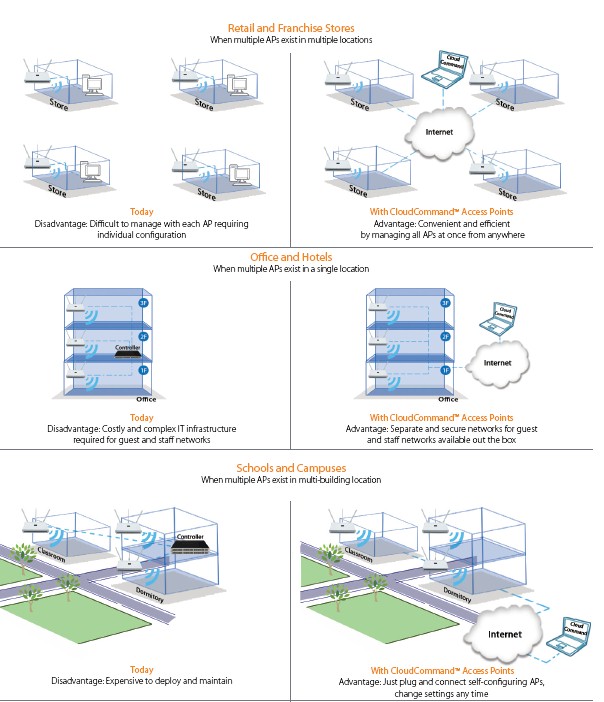
Figure 1: Multi-site networks are easy with CloudCommand
I’ve already covered the DAP-2555 hardware and wireless performance in the SmallNetBuilder review. So this review will focus strictly on the CloudCommand management features. Note that this review is based on the latest CloudCommand firmware v110rc010.
Setup
In keeping with its target customer, setup is very easy and adequately described by the printed Quick Install Guide. Each AP comes with a yellow label on its bottom that contains a Unit Identification Code (UIC), which has to be entered on the CloudCommand website before the AP is connected and powered up (Figure 2).
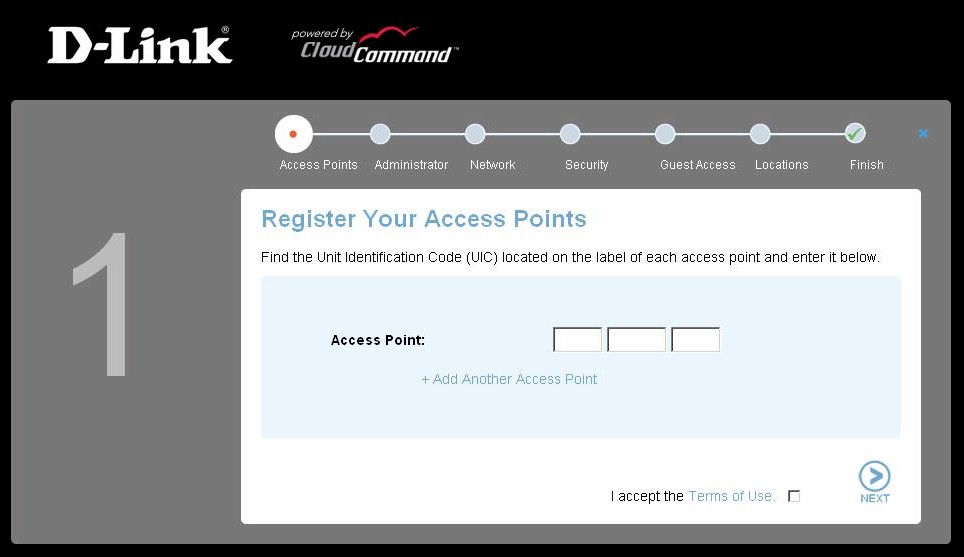
Figure 2: Registering an AP
After you enter the AP UICs and complete the registration and setup process, you attach the DAP-2555’s three dual-band antennas and plug it in either via its DC wall-wart or to a 802.3af PoE-enabled switch. Of course, the switch must provide access to the Internet!
The Gallery below steps you through the setup process, which is easy enough and sets up SSIDs for your main and Guest networks.

After first log in to http://dlink.cloudcommand.com you are greeted by this screen. I chose the first option.

You then register access points by entering each one’s Unit Identification Code.

Registering an Administrator also establishes your account
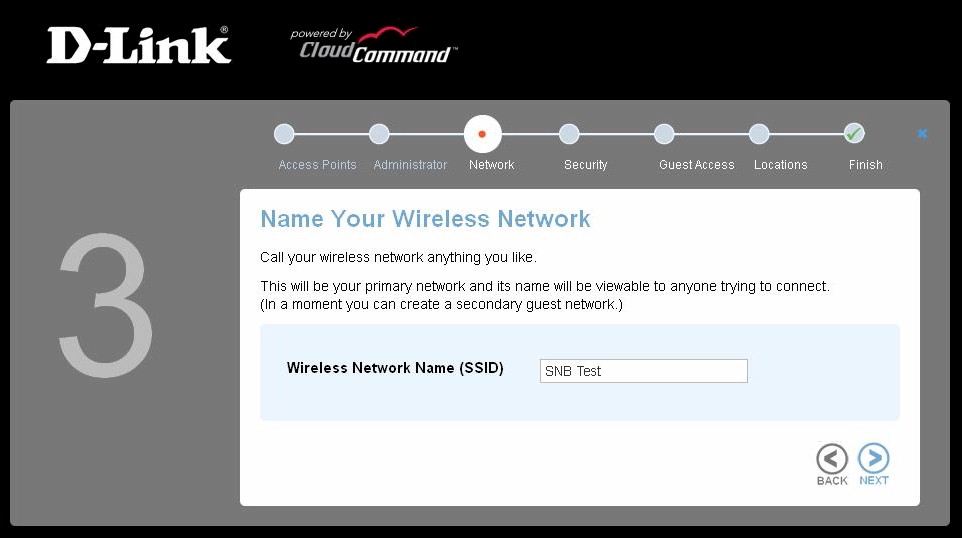
You then create a network SSID. You get only one primary and one guest SSID
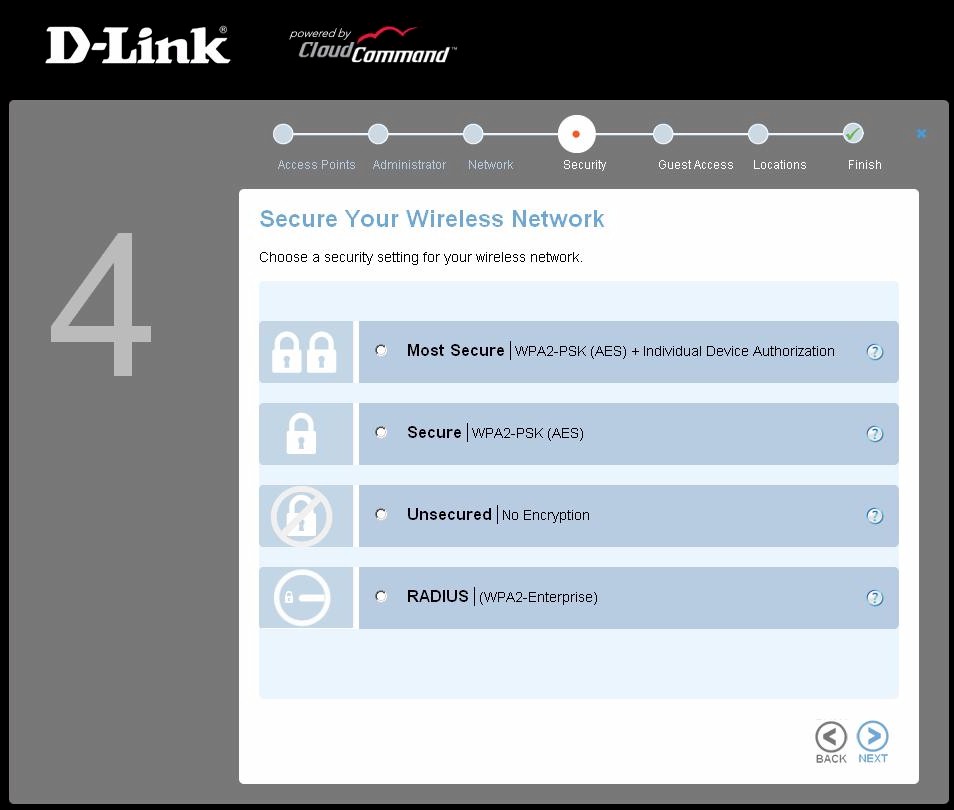
Your wireless security choices are somewhat limited. There is neither WEP nor WPA/TKIP support
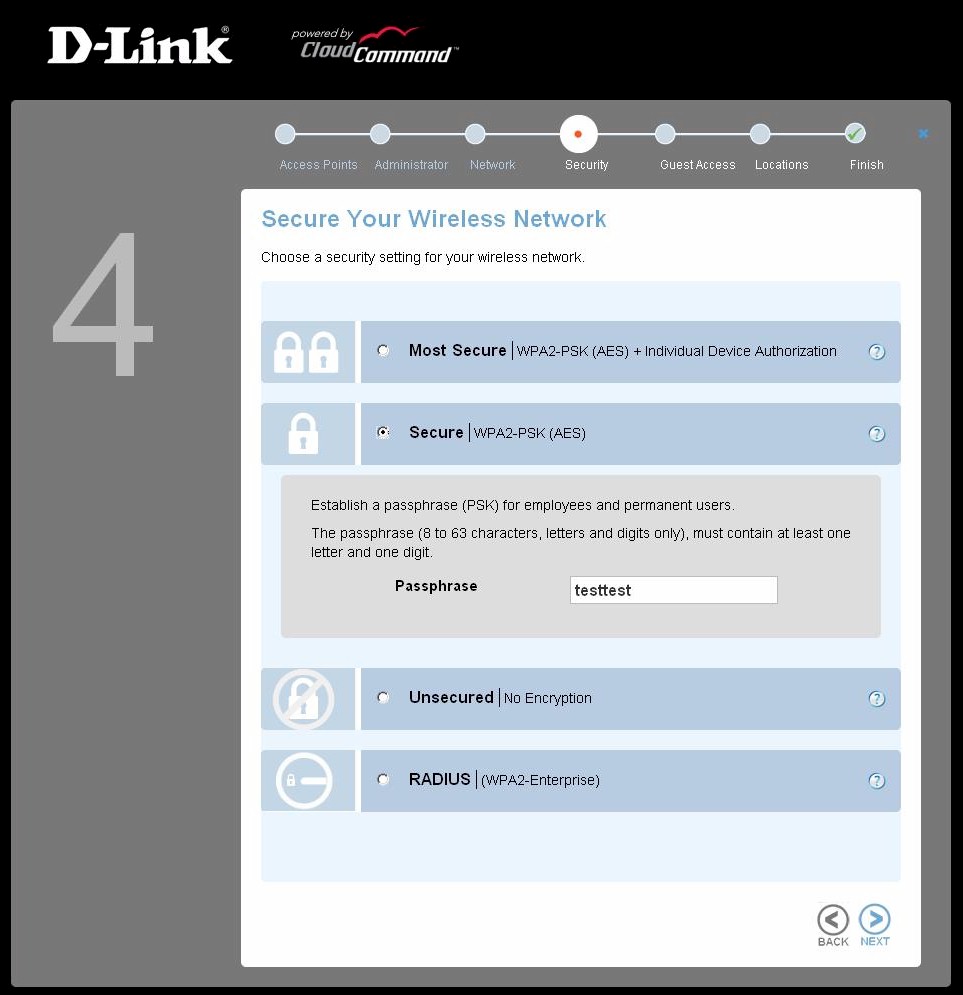
This passphrase is not a good one to use
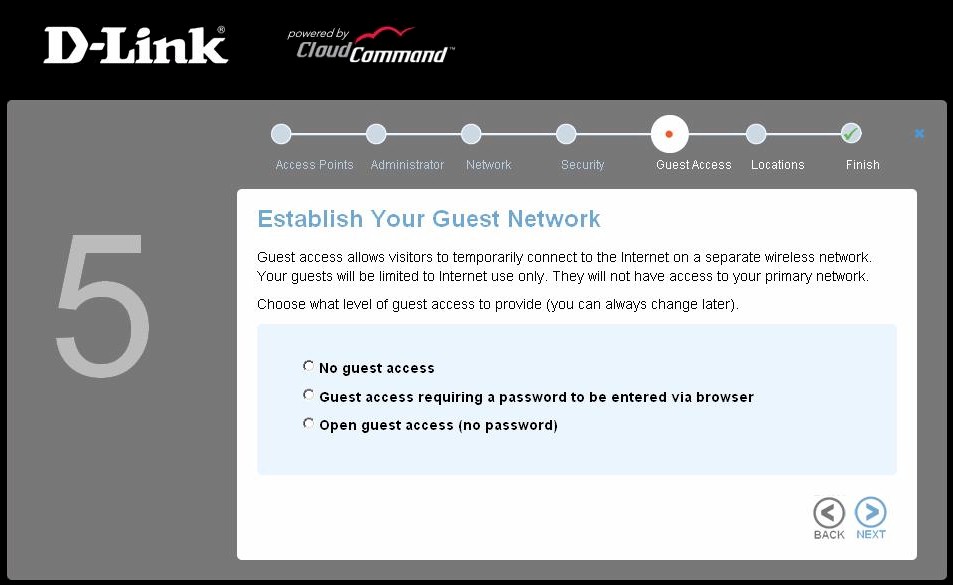
These are the only options for guest networks
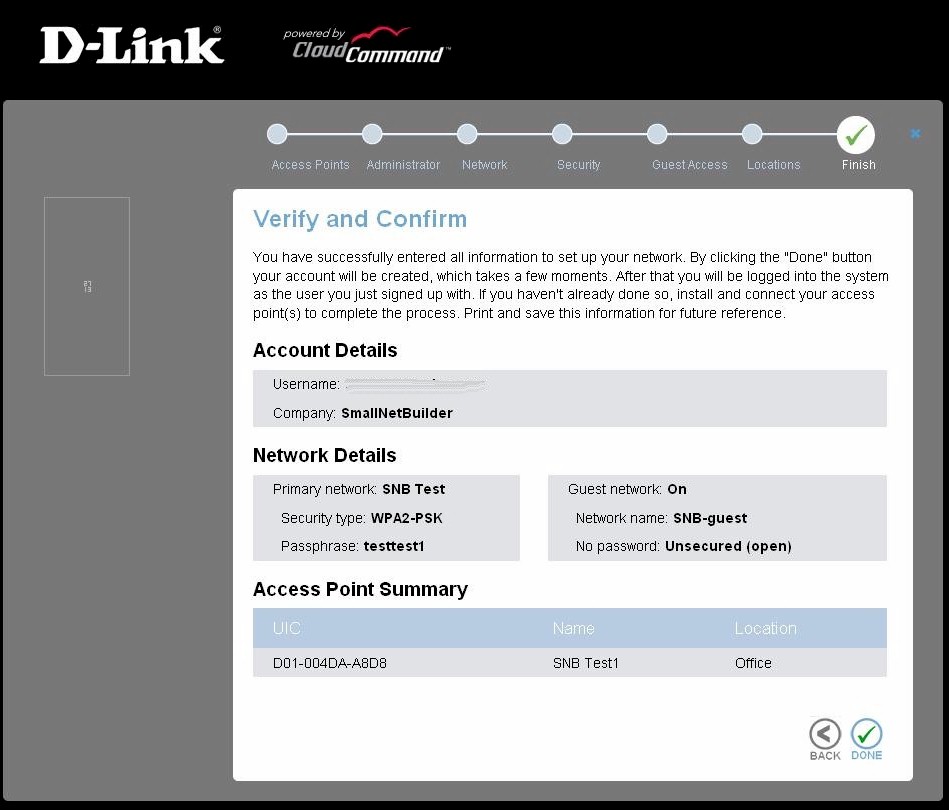
A summary of what you entered is presented for verification
If all goes well, you’ll see your access points and network when you log into the web console at http://dlink.cloudcommand.com.
In Use
Figure 3 shows the default Dashboard view that shows an overview of network status. The left column remains constant, providing access to Alerts, adding new Access Points, other management functions and a Support section.
Integrated help is accessed by clicking on the ? icons in the various panels and via the FAQ link in the Support section. PowerCloud is also working on an online CloudCommand Knowledgebase that is supposed to come online next month (April 2011). But the look I got at it told me PowerCloud has some work to do; most of the information there looked like it came from the online FAQ.
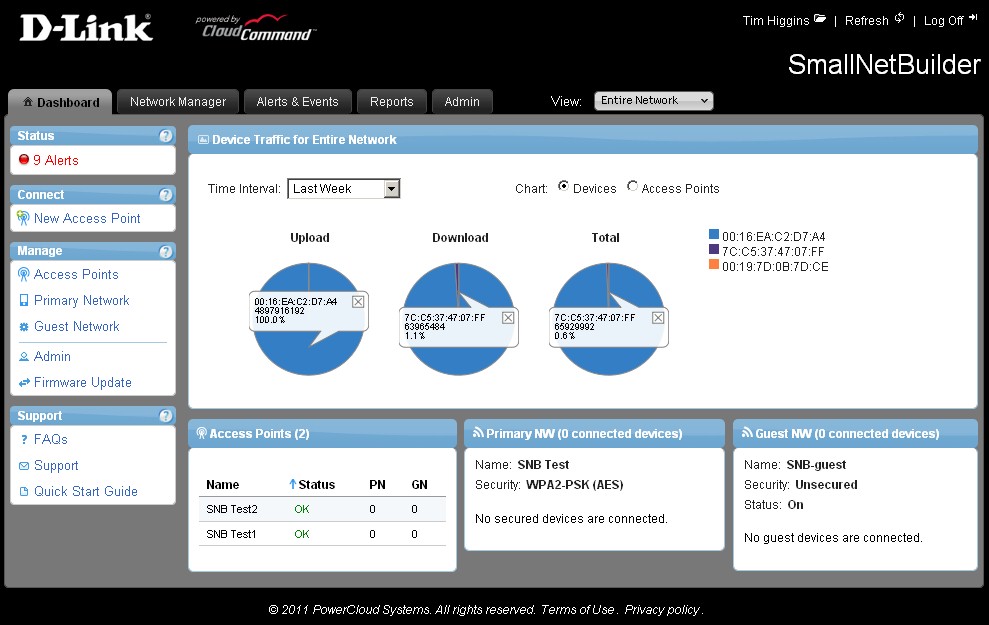
Figure 3: CloudCommand Dashboard showing a two AP network
Figure 3 shows two access points that D-Link provided, up and running. The default Dashboard view actually shows device traffic for the last hour. But I changed it to Last Week for the screenshot, because the network hasn’t been in constant use. The furthest back you can go in either this or the Reports tab is one week.
This top level view provides a percentage view of total network traffic by either device (client) or access point. I had to click on the pie chart slices to pop up the data shown in the boxes overlaid on the pies. You can’t drill down into traffic data from here. For that, you need to go to the Reports tab, which I’ll get to in a bit.
To test D-Link’s claim of easy multi-site installation, one of the APs was installed at my home office and the other at my colleague Matt Smollinger’s office. Matt and I are on two different ISPs in two different states and have different LAN network IP structures as you can see in the Network Manager tab (Figure 4). But all that was completely transparent and there was no router port forwarding or futzing with dynamic DNS required.
The default Network Manager Standard view provides an overview of AP status and connected clients on the Primary (PN) and Guest Networks (GN). Note that you can opt in the Global Settings to let CloudCommand select channels and adjust AP transmit power automatically. I can see where the auto transmit power adjustment might be good to have. But without the ability to control the band that APs use, I think auto channel selection could be a risky choice unless you have all dual-band clients.
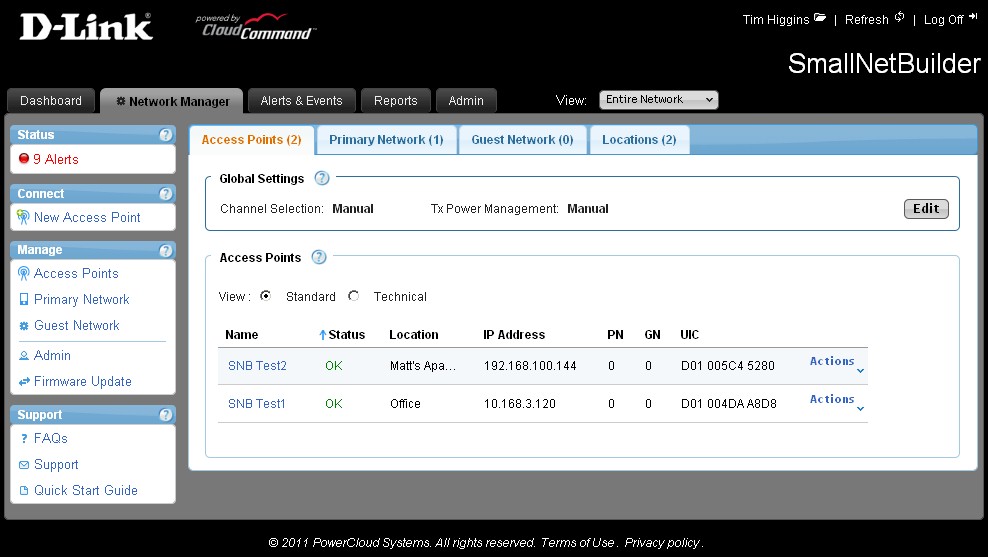
Figure 4: CloudCommand Network Manager Standard view
In Use – more
There is a bit more access point information that you can see by selecting the Technical view shown in Figure 5, including Channel (CH), Transmit power (TX) and VLAN assignment (VLAN). The Actions menu you see pulled down is available in either Standard or Technical view.
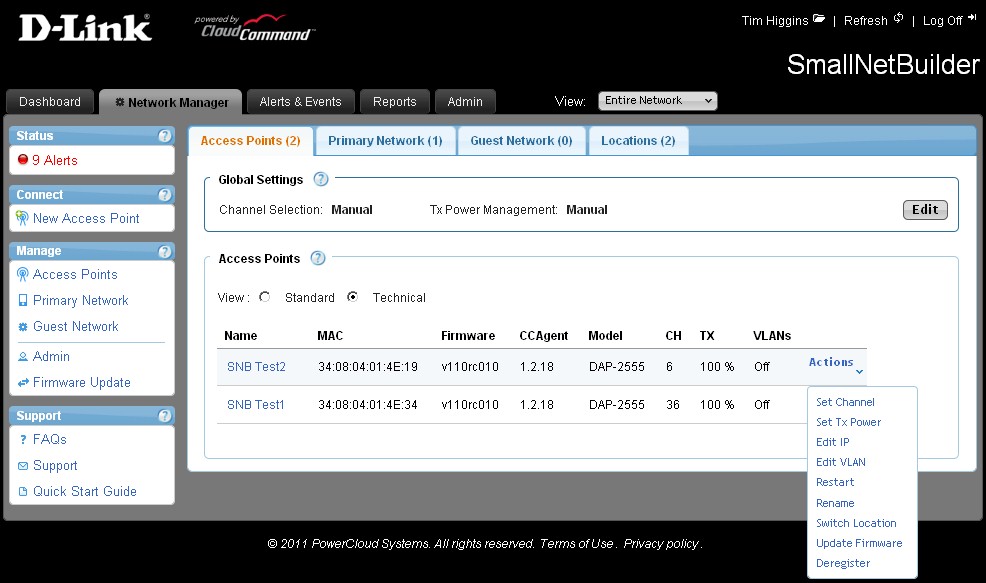
Figure 5: CloudCommand Network Manager Technical view
Selecting each item overlays a small window with the appropriate settings. Since there is only one radio, channel assigment is presented as one list with Channels 1-11 for 2.4 GHz and 36, 40, 44, 48, 149, 153, 157, 161 and 165 for 5 GHz. There are only four power settings (100, 50, 25 and 12.5%).
VLAN support was added in the most recent firmware. As Figure 6 shows, you can assign separate VLAN ID tags to Primary and Guest traffic. Of course, you’ll need a managed or smart switch that supports 802.1q VLAN tagging.
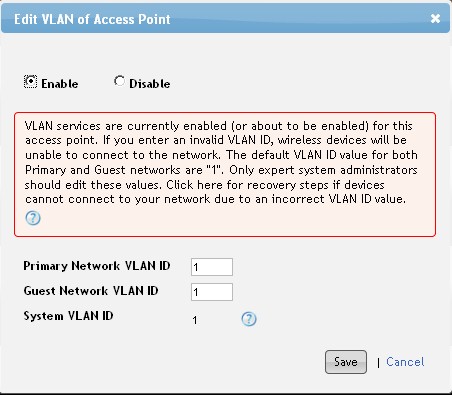
Figure 6: CloudCommand Network Manager VLAN setting
If you don’t want to hassle with VLANs, you’ll want to know what the story is with client separation on the primary and Guest networks. Here’s what D-Link told me:
The Guest Network is by default configured with client isolation and Internet only access. Clients on the Guest network cannot see each other, nor any of the resources connected to the Primary newtwork. A built-in firewall provides traffic segreagtion between Primary and Guest network.
Clients on the Primary network behave as if they were "wired", having access to all LAN resources or according to local domain policies if a local domain controller is available (i.e access privileges controlled by the domain controller as set by IT policies).
I ran a quick test to verify these rules and found them as described.
Although the 2555 uses the same hardware as the DAP-2553 that I reviewed about a year ago, it doesn’t have all the 2553’s features. Here’s a quick rundown of what the 2555 dropped from the 2553 feature set:
- Transmit data rate control
- Client connection limiting (D-Link couldn’t tell me the maximum clients the 2555 supports)
- Four SSID support
- Scheduled AP enable / disable
- Priority-based QoS
The biggie not listed above, but noted in the hardware review is that the 2555’s radio is set to Auto 20/40 MHz channel mode in both the 2.4 and 5 GHz bands. This is not in keeping with the Wi-Fi Certification requirements and seems in conflict with the DAP-2555’s Wi-Fi Certification. It could also put a serious crimp in plans to be a good wireless neighbor by not hogging 2.4 GHz spectrum.
Primary Network
Although CloudCommand can handle networks with far-flung pieces, all those pieces are joined into only two networks. As noted earlier, the Primary Network (Figure 7) has a single SSID and one security setting. The only things you can change are the Network Name (SSID), whether to disable network broadcast (Hide Network Name), and security mode.
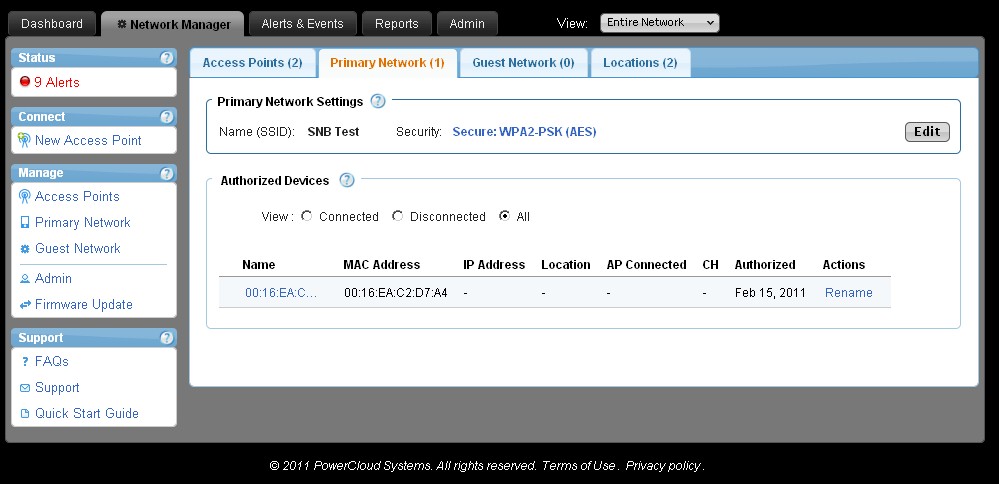
Figure 7: CloudCommand Primary Network
The security mode options are Unsecured, WPA2-AES PSK and WPA2-AES PSK with Individual Device Authorization. You also get the option of using WPA2-Enterprise. But you need to provide the RADIUS server. This seems odd to me, given CloudCommand’s target market. If a customer can’t install a multi-AP network, how the heck are they going to install and configure a RADIUS server? I’d like to see PowerCloud offer cloud-based RADIUS at some point.
In the meantime, you have the Individual Device Authorization (IDA) option. Here’s PowerCloud’s explanation of IDA.
IDA, or Individual Device Authorization, is an enhanced security mode. Like many secure environments, it requires a shared passphrase. But in addition, this mode requires all wireless devices to be individually approved ("whitelisted") by the network administrator.
There are two methods. An administrator may send a unique, one-time PIN to the device’s operator, who then uses it with the passphrase to access the network. Or, the administrator may whitelist a device using its unique Media Access Control address (often called "MAC address" or "Wi-Fi address").
I tried the one-time PIN method and had my code sent via email (the other option is SMS). When I attempted to connect to the Primary Network, my browser was redirected to a CloudCommand page that instructed me to enter the PIN. Once I did, I was good to go. I forced the client to disconnect, then reconnect and didn’t have to re-enter the code. I also tried to connect with a different client using the same code and was rejected.
Two things threw me in this process. One was the Device Name field in the Automated Authorization window. I wasn’t sure whether to enter a MAC address (the only device / client information shown in the CloudCommand GUI) or my notebook’s Windows Host name. So I just entered a few letters for the name so that I could complete the Automated Authorization transaction. It turned out this was fine. Because I was able to connect using just the emailed PIN and found that my authorized device now was named with what I had entered for the device name.
The other puzzler was the Send instructions via email or SMS shown when I chose the Manual Authorization method. If this really is a MAC address filter, then why would any emailed instructions be necessary? As it turns out, no instructions are necessary. The emailed instructions do provide the network name, wireless security method (WPA2-AES) and passphrase, however.
Note that the CloudCommand GUI doesn’t make it easy to copy / paste MAC addresses or even look them up in the main window to manually enter it. You can see the problem in Figure 8.
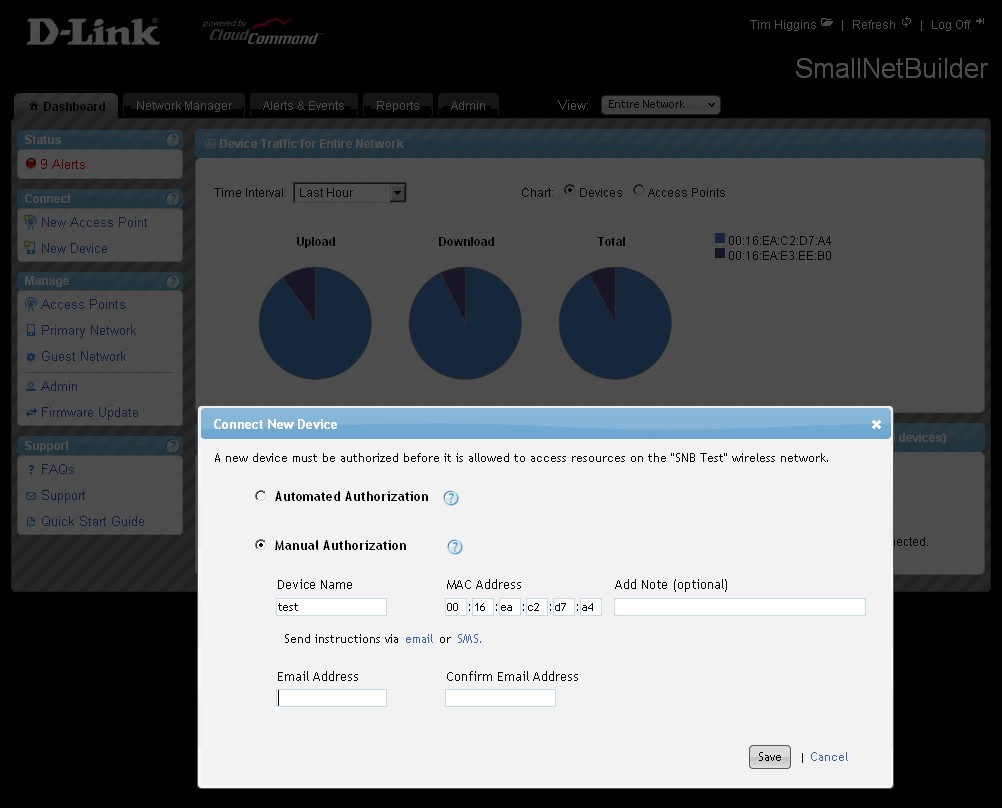
Figure 8: It’s not easy to enter MAC addresses
The screenshot actually shows the obscured MAC addresses more clearly than they looked on my monitor! It would be really helpful if the GUI provided a pick list of known MAC addresses to choose from, too.
Guest Network
As noted earlier, the single Guest network keeps connected client traffic separate from each other, the Primary network and the wired LAN. Anything connecting to the Guest network gets only Internet access. Nevertheless, some may want the same security options provide on the Primary network, especially the IDA option.
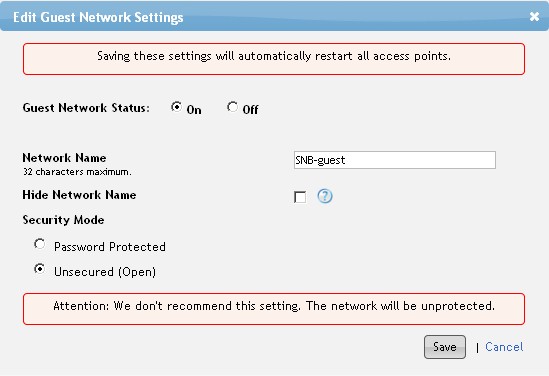
Figure 9: Guest Network security options
Unfortunately, PowerCloud doesn’t see it that way, at least not in CloudCommand’s current incarnation. What you see above in Figure 9 are the only connection options you get. Upon connection and first access all clients get sent to a captive portal where they have to check a box to accept Terms of Use. You can’t change the text or layout of this page, nor can you modify the Terms of Use.
Alerts
Folks with simple reporting needs may find CloudCommand’s reports and logs adequate. But more advanced users may find them lacking. The Alerts and Events tab has Alerts, Events and Notifications sub-tabs.
Alerts "identify unexpected issues with the network", which mainly consist of AP connects and disconnects. The Notifications sub-tab contains enables for emailing and SMSing alerts only about AP connection status and failed firmware updates. You can dismiss alerts, but you can’t save or delete them. You can view dismissed Alerts, however.
Figure 10 shows the Alerts page, which should make better use of all the blank space on the right so that you don’t have to mouse over each alert to pop up a tooltip with the full alert text.
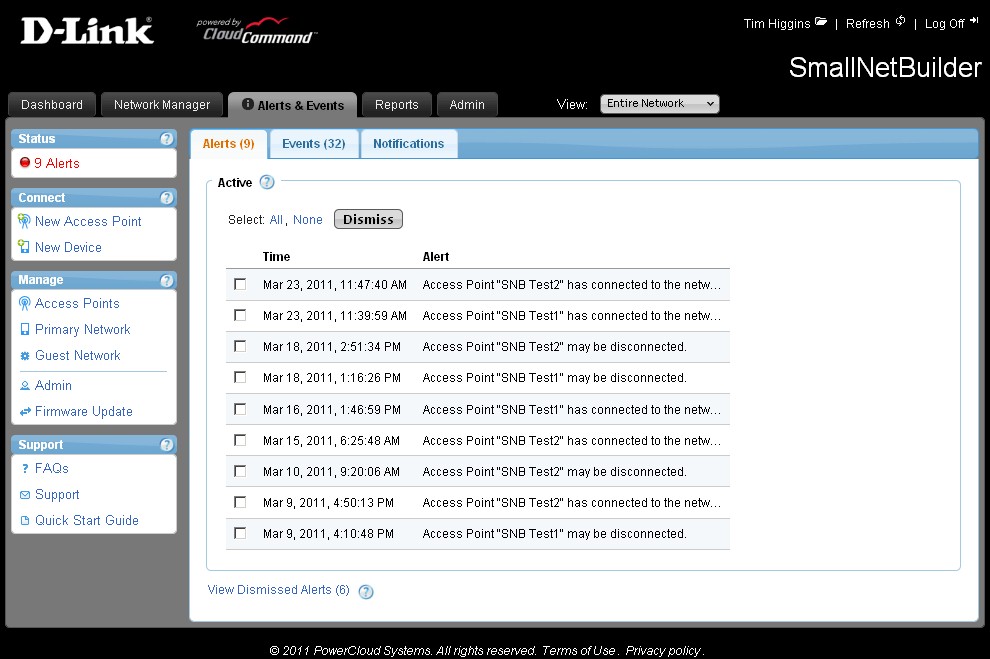
Figure 10: CloudCommand Alerts page
Events
The Events tab is basically the AP log, which seems quite comprehensive. I was able to pull up all the events from the point where I first fired up the network, over two weeks ago. Figure 11 shows you can filter by date and a wide selection of event types and High / Medium / Low / Alert severity levels. But you can’t filter by individual AP or Network. You can export the Events to a CSV, but can’t delete more than one event at a time or email them on schedule.
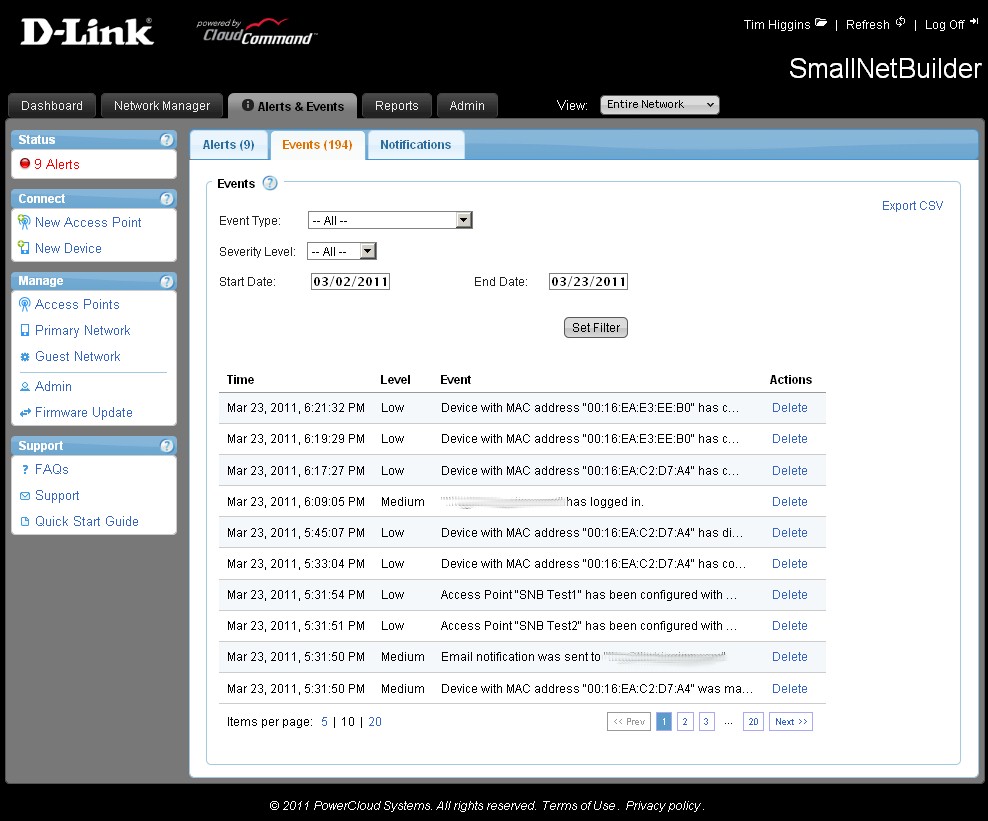
Figure 11: CloudCommand Events page
Reports
Reports are where network performance junkies and managers may really get frustrated. The Devices view (Figure 12) scaling made it impossible to see everything without scrolling up and down. You can filter by network and location, but not by AP and there is no way to remove clients from the view.
Time periods can be set for the last hour, 6 hours, 12 hours, day, 3 days and week. Data beyond the past week is saved in the CloudCommand, er, cloud but can’t be accessed at the present time.
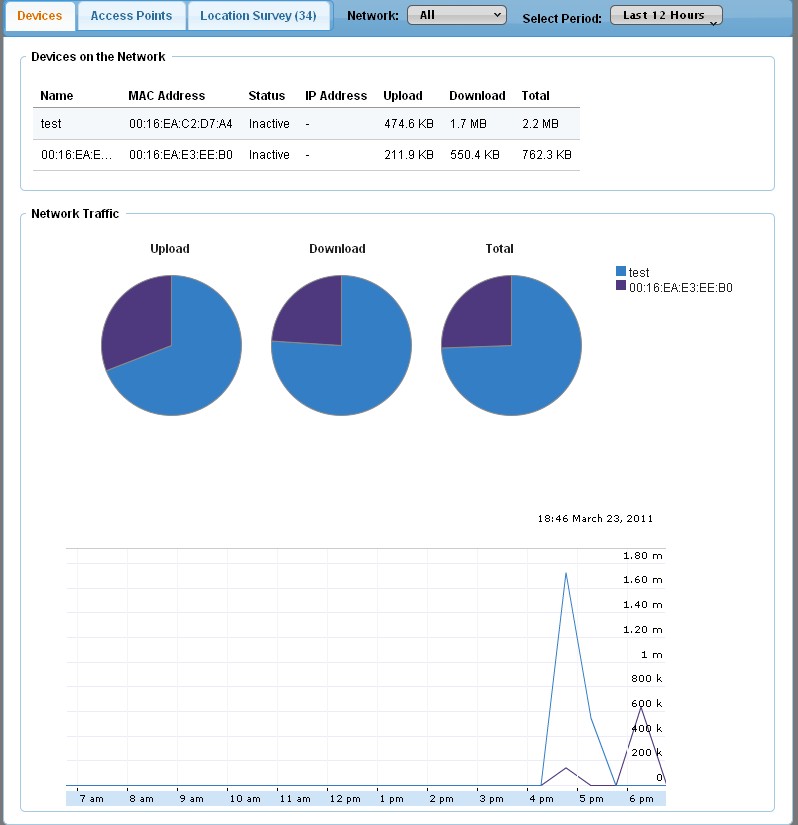
Figure 12: CloudCommand Reports Devices page
The Access Points tab offers a similar view but for APs. In addition to the filters in the Devices view, you can select Active, Inactive or All APs. This view could really benefit from information on number of clients connected and the ability to click on a pie chart or piece to drill down into its client data.
The last Reporting option is the Location Survey or Rogue AP detection (Figure 13). This view lets you filter by Network location and by Active / Inactive APs. But you can’t determine the AP that detected the rogue and there is no signal level information provided. So tracking down the rogue’s physical location would be pretty much impossible from this data.
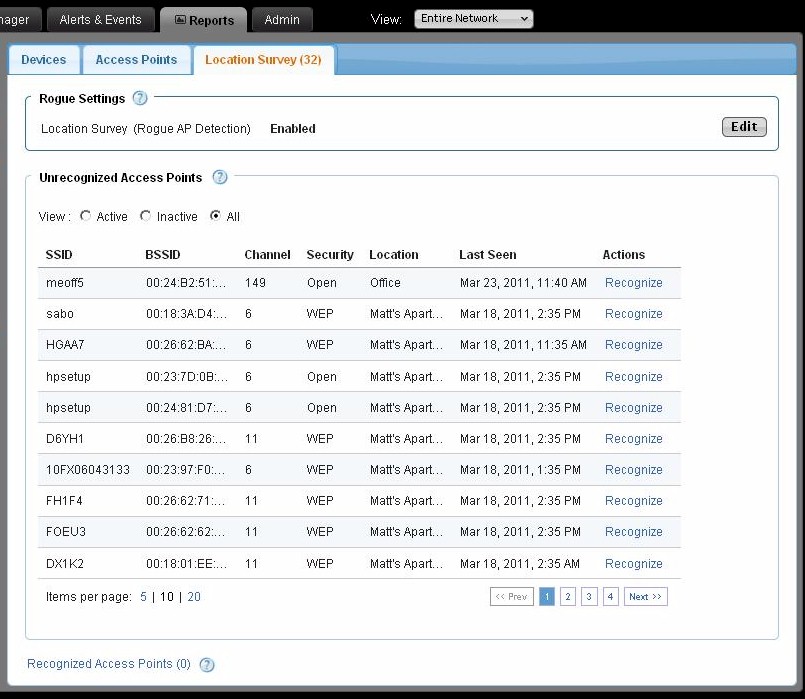
Figure 13: CloudCommand Reports Location Survey page
This report looks like a filter of the main AP log but only went back a week. You can Recognize the data to dismiss it from the view and recall it. But you can’t email or save the report and there are no email or SMS alert options for it. The only setup options are to enable / disable and set the scan frequency for hourly or daily.
Closing Thoughts
Despite its reporting and configuration omissions, the DAP-2555 could be an attractive alternative for those looking for a cost-effective way to get a business-class multi-AP wireless LAN up and running in a hurry. Installation is dead simple and configuration options are limited so that inexperienced users won’t get confused.
D-Link has also made the DAP-2555 easy to buy and relatively affordable. They’ve worked out a deal with PowerCloud to bundle the first year of CloudCommand service into the price of each AP. The first year of bundled CloudCommand service looks like around $150 ($281 – $132 based on lowest current prices of the DAP-2555 and DAP-2553 at time of review). Fortunately, yearly renewal after the first year is $99.
If you change your mind after the first year and decide not to renew, D-Link also provides the option of converting the 2555 back into an independently-managed AP. So if you decide that cloud-managed WLANs aren’t your thing, your hardware investment doesn’t turn into a doorstop.
Figure 14 shows an web admin that will be very familiar to DAP-2553 owners. You just hit the AP’s IP address, login as admin (no password), uncheck the Enable Cloud Manager box on the Cloud Manager page and reboot.
Figure 14: DAP-2555 with CloudCommand disabled
It looks like all the DAP-2553’s features are intact, which means that CloudCommand could enable them through its interface, should it choose to.
But the DAP-2555 also has some serious limitations that could keep it on companies’ no-buy lists. The most serious is the inability to implement separate 2.4 and 5 GHz networks with unique SSIDs. You get only one Primary and one Guest network, which is at least one network short. And even if you decided to limp along by splitting the Primary and Guest networks by band, you’d have to manually assign channels.
Companies with mixed N and A/G clients may also find CloudCommand’s lack of controls for legacy (A, B, G) support troubling, if not a show-stopper. There are still clients around that don’t like to talk to N APs running auto 20/40 mode. So the inability to accomodate those clients by setting up a legacy-only network isn’t good.
Finally, the reports and tools need work. CloudCommand does an excellent job of geting APs up and working. But figuring out where to place them for best coverage and performance will require the services of an experienced installer, who will find no help in CloudCommand’s reporting, which lacks any client signal level reporting.
If you can live with CloudCommand’s limitations, you’d be hard pressed to find another solution at this price point for building an easy to manage multi-AP network. It will be interesting to see if PowerCloud can get more hardware vendors signed up to provide a wider equipment selection and the revenue stream they’ll need to not only survive, but grow and continue to enhance CloudCommand. That, in the end, is the key question.
