Introduction
I don’t get the opportunity to do much virus, spyware or malware fighting here at SmallNetBuilder HQ. There are no kids downloading and "exploring" the Internet, my wife and I seldom (if ever) copy in files from off-network computers and both of us are well-versed in safe Internet practices (and follow them).
But my neighbors and family members are not so fortunate. My holiday-time trips home usually involve a half-day session with one of my sister’s computers to make it stop "running slow", although that has ceased to be a regular thing now that all of her kids have moved to places (and computers) of their own.
Her problems usually haven’t been bad, however. Removing some adware that came along with Party Poker and a general cleanout of temp and unused applications were enough to get her back to a nicely responsive system.
This weekend, however, one of my neighbors was not so lucky when they got hit with a variant of the Zlob trojan. Fortunately, they didn’t complicate the problem and fall prey to Zlob’s multiple exhortations to download and install fake malware fix tools that would have further complicated the problem. As it was, Zlob was perfectly capable of installing enough malware on its own.
In the end, I took the safe route of doing a clean reinstall of XP after spending an afternoon making several unsuccessful attempts at removal. But I learned a few things along the way that I thought might be useful to pass along.
Lesson #1: Know Your Anti-Virus Program
The most important thing in preventing a malware, virus or adware infection, besides observing good Internet hygiene, is to know the state of your anti-virus program. If you are running an Internet-connected system without good, automatically-updated anti-virus protection at a minimum, you’re not just exposing yourself to risk, but you’re also potentially part of the world-wide epidemic of infected computers.
AVG continues to provide its free Anti-Virus edition for "private" use, i.e. individuals, not businesses. So there is no excuse for not having effective anti-virus on every system that you own. Of course, AVG would also appreciate it if you would buy either the Pro or Internet Security versions, which add rootkit and additional protection features.
In my neighbors’ case, they had a different anti-virus program installed. But they didn’t know that it wasn’t providing any protection, because it had expired months ago. The problem was that the program looked like it was running because it was spinning its little logo continuously down in the System Tray. But what my neighbor thought was the program’s way of showing that it was working, turned out to be its way of saying it needed attention!
The fault here is shared between the program’s designers and my neighbors’ complacency and lack of curiousity. The program designers should have provided continuous non-ambiguous indications that the program was not doing its intended job.
With AVG, the tray icon changes to superimpose an international alert symbol on top of its normal icon when it is not running or hasn’t been able to perform its daily update (Figure 1). It would be even better, however, if it also provided a pop-up or other obvious indication of what the problem is that is causing the alert.
![]()
Figure 1: AVG problem indication
But my neighbors are also at fault. Just as you must know what your car’s dashboard trouble lights mean (if you want to avoid expensive repairs…or worse!), so must you know the status of your anti-virus. If they had known what their previous anti-virus program was trying to tell them, they would have saved themselves (and me) a lot of time.
Lesson #2: Know When You’re Being Scammed
The most important thing in surviving a malware infection is knowing that you have one. Fortunately, zlob isn’t shy about announcing itself. But the way it announces its presence can panic unknowledgeable users into doing things that they shouldn’t
Zlob changes your desktop wallpaper to display a warning similar to that in Figure 1 and pops up a warning balloon in your Windows System Tray / Notification Area similar to those in Figure 2.
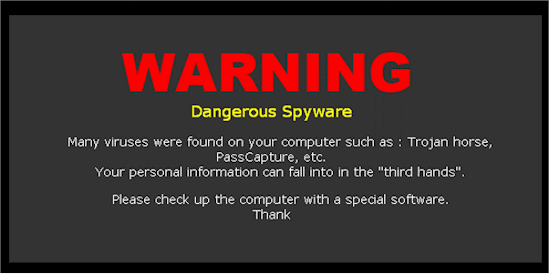
Figure 2: Zlob desktop wallpaper warning
From community.ca.com
The wallpaper change is a good tipoff, since there is no normal Windows behavior that I know of that causes Windows to change your desktop wallpaper and prevents you from changing it back. But the tray popup is much more subtle and easier to fall prey to. Windows frequently uses Tray popups to provide warnings and alerts and allows you to take action by clicking on the alert balloon.
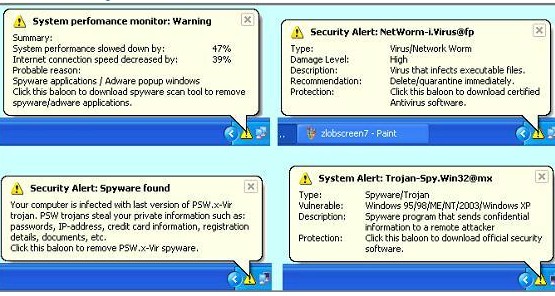
Figure 2: Zlob tray popups
From spynomore.com
Fortunately, the desktop wallpaper change was enough to raise suspicion that something was wrong and caused him to call for help.
Lesson #3: Isolate and Shut Down
The first thing I told my neighbor to do was to pull the computer’s network connection. This was both to prevent it from downloading anything further and to prevent whatever he had from spreading to other networked computers.
It turns out that zlob doesn’t spread by copying itself to networked shares. But I didn’t know what I was dealing with and it could have been a worm, which are very good at distributing themselves via networks.
I should also have told my neighbor to shut down the system since the longer zlob is left running, the deeper it seems to bury itself into a system. Zlob’s ongoing efforts to burrow into the system were clear once I was able to get AVG installed. It seemed that as fast as I was able to track down and delete infected files and kill processes, zlob produced more bogus infected driver files and launched more bad processes.
Lesson #4: Be Ready For A Clean Install
The best way to rid yourself of something like zlob is to do a clean system reinstall, which includes a wipe and reformat of your hard drive. It seems that every time that I face a messed-up Windows system and try to manually fix it, I always spend way more time than it would have taken me to just do a clean install from the get-go.
Of course, doing a clean install assumes that you have everything you need to do so. If you’re really organized, you already have a "bare metal" restore backup ready to go using Acronis True Image Home or another solution that can create and restore a full image of your system.
But even if you are that well-prepared, the restore image will bring everything back, including a registry full of outdated and unused entries and probably plenty of other stuff that Windows collects over time that sucks the speed out of you daily computing.
That’s why I prefer a clean install, which means that I need to have the following items collected and ready to go:
- Windows install or System recovery CD: Unless you purchased a retail copy of Windows, your computer came with a collection of CDs, including a System Recovery CD that is used to restore Windows. The good news is that it’s easy to use. The bad is that it also reinstalls the crapware that most vendors include in order to improve profit margins. So you’ll need to spend some time uninstalling the stuff that you don’t need or want.
- Drivers: If you’re installing from a retail Windows CD, you’ll need drivers for hardware that isn’t handled by the Windows install CD. You’ll need to have collected these from the appropriate vendor websites.
- Application CDs: Of course you have all the CDs for programs that you’ve installed over the months and years collected in a safe place, right? If not, write yourself a note to collect everything this weekend and put them all in an envelope or desk drawer where you can’t miss them. And be sure that you have a copy of the installers for any downloaded applications.
I make it a practice to copy the contents of my installed application CDs to a folder on my NAS. This saves the hunt and also allows me to install to systems that don’t have an optical drive. This also means that they are backed up to my backup NAS. - Data backup: This is the trickiest and scariest part of the whole clean install / recovery exercise. The stuff in the My Documents (or whatever folder you use for document files) folder is easy to do. It’s the other things like application settings, browser bookmarks, address books, etc. that Windows and applications scatter around the system that are the pieces that you’re most likely to miss.
The Windows File and Settings Transfer Wizard isn’t much help because it has a definite Windows-centric view of the world and collects only the settings for Windows itself and Internet Explorer. It also provides the option of adding file types and folders to the stuff that it collects. But since you need to know enough about where stuff is stored to add the proper settings folders, this approach isn’t very wizardly. The wizard also stores the settings in a DAT file that doesn’t let you see what it actually collected. So I think I’ll pass on the wizard.
My approach is to make sure that all applications store my data files in the same place. Some apps default to a folder in My Documents, while others default to storing data files somewhere in their Program Files folder. Your job is to check all of your applications and if possible point them to a common place to store the files you create. If you can’t change the location where an application stores its data files, at least make a shortcut to the folder and put it on your desktop to remind you and be sure to add the appropriate folder to your backup.
Once this is done, my scheduled backups copy these data file folders and also copy my folder in the Documents and Settings folder. If you copy the entire Documents and Settings folder, you get a lot of stuff you probably don’t need. But at least you should have the stuff you do need to get your apps set up the way you want them.
Tracking down all the data files is the toughest part of the preparation for a clean install. Even with the above checklist, I still missed the location of my neighbor’s Palm desktop address book database files.
Lesson #5: Isolate During Download
Until you know that the infected system is clean, you need to keep it isolated from other networked machines. This is not a problem during the initial reinstall, which is done from a CD or DVD drive. But once you get the base system installed, you’ll need to connect to the Internet to download and install the many updates needed to bring the system up to snuff.
This is where having a managed switch with VLAN capability came in handy. Before I plugged the restored, but yet untrusted machine into my LAN, I first set up a port-based VLAN on a NETGEAR GS108T that allowed the system to connect only to the Internet and isolated it from the rest of my LAN. I then plugged in another known-good system into the VLAN’d port to verify that it was indeed isolated from the LAN, but could connect to the Internet. Only then did I connect the system under reconstruction into the VLAN’d port.
If I had not had the GS108T, I would have had to either unplug all my other systems, including NASes, or rewire them into a separate switch. I wouldn’t have been able to maintain an Internet connection for them, however, not at least while the "bad" system was connected.
Lesson #6: Scan and Scan Again
Because my neighbor had not kept backups, I had no choice but to take the risk of copying files from the infected system. But I took the precaution of scanning the flash drive with a fully-updated AVG anti-virus to ensure that no files were infected.
So imagine my surprise when I plugged the flash drive into one of my own systems—with updated and running anti-virus—to scan it again before copying the data back to the freshly restored (and fully-scanned) system and saw the telltale zlob desktop and popup!
I eventually found an infected file in the $RECYCLE folder of the flash drive that somehow got missed during the initial scan, probably through some AVG setting that I missed. The lesson here is to make sure every file and folder is scanned on whatever backup you are going to use for restore.
Lesson #7: Disable Autorun
I still don’t know exactly how my own system got infected from the backup flash drive. But I think at least part of the cause was that the flash drive had the U3 system installed. And when the U3 Launchpad installer was launched via Windows Autorun when the flash drive was plugged in, the infected file (in the $RECYCLE folder no less) somehow was able to come along for the ride.
I had, of course, seen the warnings to disable Autorun many times, but never saw how it could cause problems. Well, now I do see! So before I plugged that key in again, I disabled autorun on all drives using the instructions in this Microsoft KB article.
Once I did that (and uninstalled the U3 launchpad), I was able to safely plug in the drive and not have it launch anything. It was then after I rescanned the drive with AVG that I found the infected zlob file in the $RECYCLE folder and was finally able to bid farewell to zlob, which I hope to never meet up with again.
