Introduction

The splendors of travel are many. As are the dangers
Whether for business or for pleasure, traveling can be one of the best experiences of a person’s life. The chance to broaden the mind and get a sense of different peoples and cultures is a priceless one, and has the potential to vastly transform a person for the better. Unfortunately, alongside this potential for great good also comes the potential for great ill. Strange diseases, crime, dangerous public transportation and tacky popular culture are a few of the maladies that can plague a traveler, but perhaps the most overlooked pitfall of travel is identity theft.
Travelers are even more open to identity theft than normal users, being at the mercy of questionable Internet cafes, shady wireless access points, and tempted by all manner of pirated forbidden fruits on the street corners. But few take the time to take precautions to safeguard their personal information while traveling. The silver lining to this cloud is that, with a combination of not-so-common sense and a knowledge of the threats that are out there, it is relatively easy to prevent identity theft while on the road.
This article is intended to provide a basic introduction to the potentials for identity theft that face the road warrior, though it should not be taken as a substitute for one’s own judgment in different situations. Above all it is a guide, and like all guides should be taken with a grain of salt to better suit the tastes of its reader.
The Basics
It is no surprise that the same basic guidelines for protecting personal information at home also apply when traveling: use strong passwords, don’t open funny attachments, and don’t reveal sensitive information such as PIN numbers to anyone. The third guideline applies even more when traveling, as some places around the world boast police that will ask for your credit card and PIN number for ‘record keeping purposes’ when responding to an incident.
The basic guidelines for safe travel also apply to protecting your identity: carry a money belt (people may laugh when you reach into your pants for money, but it is a whole lot better than having them laugh when a car and plane tickets are purchased with your credit card!), carry a photocopy of your passport, and be extra cautious when changing money or accessing ATMs. Above all, it is a good idea to treat every computer that is not your own with extra suspicion. Not all of them will be Pandora’s boxes of identity-stealing nightmares, but a little bit of paranoia can go a long way.
TIP: More travel tips for preventing identity theft outside of the digital realm can be found in the Identity Theft Resource Center’s handy consumer guide on travel identity theft.
Internet Café Dangers
One of the more interesting vectors of identity theft is the Internet café. Over the past several years, more and more viruses and worms have appeared that target the end user’s computer automatically (such as the Sasser and Blaster worm families). This, coupled with the loosely-controlled nature of Internet café machines (which could potentially hide a keylogger, a rootkit, or worse), the difficulties in patching a large number of computers, and the lack of incentives for many café operators to patch their machines, make Internet cafes a gamble when it comes to personal information.
Certainly it is always a possibility to take the time to run anti-virus and -spyware utilities and install all of the latest patches and critical updates in an attempt to sanitize a café machine. But as I learned from an experience at an Internet café in Laos, doing this is quite time-consuming and can eat through your time at the Internet café. Not to mention the fact that patching and updating is a horrible way to spend your vacation.
The solution to this situation mainly relies on finding a reputable Internet café. Oftentimes these may prove to be more costly than other Internet cafes, but this cost is still far less than the cost of recovering from a stolen identity. Sometimes a reputable Internet café cannot be found. In this case, it is a good idea to bring along a copy of a Linux LiveCD such as Knoppix in order to provide a safe desktop environment (Figure 1).
Figure 1: Startup screen for the Knoppix LiveCD (Click to enlarge)
These CDs allow you to run a distribution of Linux directly from the CD, without modifying the contents of the hard drive at all. This will allow you to safely and securely browse the Internet, check your email, and do everything that you would normally do at an Internet café, without worrying about your activities being recorded by that computer or worrying about leaving anything behind that could damage the machine.
Laptop Liabilities
Sometimes the information you need is too much to be accessed remotely (especially in an Internet café with a shared broadband connection). In this case, it may be desirable to bring along your own laptop to use. Aside from the obvious dangers of the laptop being damaged during travel, there are also several potentials for identity theft involved in bringing a laptop with you.
The most obvious danger is the laptop being stolen. This not only provides the obvious hassle of having to replace the laptop, but also carries the potential of having vital information – both business and personal – fall into the wrong hands. Laptop theft can be prevented by a good lock and keeping a watchful eye over the laptop and other portable digital devices that you take with you. But even a lock cannot deter a determined thief, and you will have much better things to do than keep a constant eye on your laptop while traveling. So it is always a good idea to keep safeguards in place in the event that you do become a victim of laptop theft.
Regular backups of vital information (such as any projects or documents that you are working on, email, etc) will help you recover in the case of lost data. Investing in strong disk encryption will also help prevent laptop thieves from accessing and using critical information on your laptop. Apple laptops running Mac OS X 10.3 or later have access to FileVault, a disk encryption mechanism that can encrypt a user’s home directory with 128-bit AES encryption and is provided within the operating system itself (Figure 2).
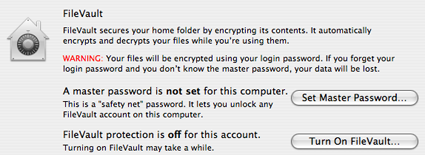
Figure 2: FileVault in action on Mac OS X
Windows users must rely on third-party software for disk encryption (though the forthcoming Windows Vista will include BitLocker encryption). PGP’s Whole Disk Encryption provides a way to encrypt an entire disk, and is available in either Enterprise (for organizations that want to implement a centralized encryption solution) or Professional (for individual users) flavors. FreeOTFE is a free (as-in-beer) disk encryption program for Windows that allows for a variety of different encryption algorithms and ciphers to be used in encrypting the disk.
On the Linux side of things, kernel 2.6.4 contains native support for dm-crypt, an update of the venerable and vulnerable Cryptoloop. For extra security when running Linux, the root plug module may be used. This module can be used to prevent a thief from running processes as the root user, since it blocks processes from running as root if a specific USB device is not present in the machine.
VPNs For Secure Networking
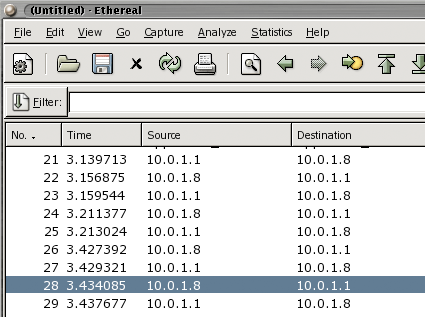
Even when a laptop is safe in your hands, there is still the problem of what happens to your data in when it hits a network. Unencrypted wireless access points (and even access points using weak encryption) can broadcast your information to anyone and everyone who is listening. It’s then a simple process to use a network sniffer such as Ethereal (recently rebranded as WireShark) or OmniPeek Personal to capture traffic that includes unencrypted login and password information (Figure 3).
Figure 3: The packet-sniffing utility Ethereal (Click to enlarge)
Malicious users can also set up fake access points that can mimic legitimate sites, perpetrating what is commonly known as a ‘man-in-the-middle’ attack and relieving you of your personal information. It’s all enough to drive a person mad.
Fortunately, virtual private networking technology (VPN) allows users to ‘tunnel’ into a server via an encrypted connection, providing a great deal of communication security even when making use of an insecure connection. VPNs vary in speed and security depending on the implementation. The most common VPN technologies available are IP Security (IPsec), Point-to-Point Tunneling Protocol (PPTP), and Layer 2 Transport Protocol (L2TP).
L2TP and IPsec are commonly combined together (as they operate on layers 2 and 3, respectively), with L2TP providing security on the datalink layer and IPsec providing secure authentication on the network layer, though IPsec may be used by itself. PPTP is another available standard, and is significantly easier to set up than IPsec, though it may be broken if a user selects a poor password.
Figure 4: VPN connected notifications in Windows and Mac OS X
Many companies and universities make use of VPNs for their users and certain ISPs and Web hosting providers also offer VPN services to customers. So be sure to look into whether or not your organization or ISP provides VPN access before you depart, as it can save a great deal of heartache along the road.
If you want a cheaper VPN solution, and don’t mind a bit of elbow grease and setup time, OpenVPN provides a free way of deploying a VPN on your home network. For an even easier solution, consider setting up your own SSL-based VPN using the “Community” (free) version of SSL Explorer.
Lock Down Your Email
Another way to stay secure in your communications while on the road is email encryption. A good idea even while at home, encrypted email becomes all the more useful when accessing the Internet through an insecure access point or in an untrusted computing environment.
As with disk encryption and VPNs, there are a variety of different ways available to encrypt email. The most common email encryption mechanism is Pretty Good Privacy (PGP), which can be found in a variety of implementations ranging from standalone command-line tools to plugins for email clients.
The competing (and incompatible) standard is Secure/Multipurpose Internet Mail Extensions (S/MIME), which requires a valid security certificate from a reputable certifying authority. Both standards are endorsed by the National Institute of Standards and Technology as security standards, and are both secure enough for everyday use. However, the two standards cannot decrypt one another, so it is important to know which email encryption mechanism the person you are communicating with uses before sending a message (or even if they are using encryption at all!), to avoid a mess of garbage text from reaching your recipient.
PGP is officially available through the PGP Corporation, which also offers the PGP Universal solution for encrypting emails in an enterprise environment. For a free option, Gnu Privacy Guard (GPG) is a free/open-source solution that can be used from the command line or even plugged into an email client for even easier encryption.
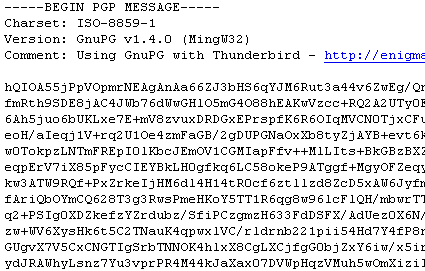
The Enigmail plugin for Mozilla Thunderbird (Figure 5) allows GPG email encryption directly from the client. In the large version of the figure below, the message on the left has been encrypted, while the message on the left has been decrypted.
Figure 5: Enigmail plugin for Mozilla Thunderbird
S/MIME support is included with many e-mail clients, so using it is as easy as selecting the ‘Encrypt Email’ option within the client. The difficult part, however, comes with obtaining a certificate from a CA. Many organizations provide their own CA’s, but certificates are also available through trusted third-party CA’s. Thawte is the most popular third-party CA, and can issue free S/MIME certificates (Figure 6), while VeriSign provides certificates for a fee.
Figure 6: An S/MIME certificate issued by Thawte and viewed in Mozilla Firefox. (Click to enlarge)
A word of caution/paranoia: Though the cryptographic algorithms behind mechanisms such as PGP and S/MIME are secure, it should be noted that their greatest weak points come in their implementations. An improperly-implemented version of one of these algorithms can provide a false sense of security – which can be even worse than having no security at all! – so take care to update to the latest versions of whichever implementation you choose. Or, for the truly paranoid, just use the time-tested command-line versions of each tool.
A final concern when bringing your laptop on the road is file sharing. For security’s sake, unless you absolutely trust the network you are plugged into, disable file sharing on your laptop’s network adapter when connecting to a network. This will prevent other machines from viewing and accessing the files on your laptop, and may even save you the pain of having to remove a worm from your machine if file sharing permissions are improperly configured.
Piracy Predicaments
(Note: While we at Tom’s Networking do not endorse illegal activity of any kind – even victimless crimes such as jaywalking and the tearing of tags from mattresses – we do realize that pirated software and movies are a real part of traveling, and provide this advice to help you protect yourself from technical and legal problems when dealing with such software.)
In many places throughout the world, the forbidden fruits of pirated software sit ripe for the plucking by travelers and locals alike (Figure 7). These generally carry an incredibly low price, and can often seem like too good of a deal to resist. While most are benign from a security standpoint, they all come with the potential for Trojans and backdoors that can turn your computer into a slavish zombie. Keep in mind that the pirated software market is truly ‘buyer beware’, and that even Sony’s rootkit efforts pale in comparison to some of the malware that may be present in pirated software.

Figure 7: A rack of pirated software on a street corner.
Customs and immigration presents another potential issue to users wishing to purchase pirated software abroad. In recent years, customs officials have become more vigilant in cracking down on the importation of pirated software. So you may not only have your cheap software confiscated by Customs, but also potentially find yourself slapped with a fine or jail time, depending on how much software you have purchased.
The bottom line is this: if you wish to purchase pirated software abroad, know and accept the risks. It is illegal and may prove harmful to the computer that it is installed on, but it’s also cheaper than a hot dog and almost as readily available. For good or ill, you are on your own when it comes to pirated software, and don’t expect anyone else to go to bat for you if you find yourself with a broken computer, a stiff fine or worse!
Conclusion
While this article may sound like it’s full of doom and gloom, it is not. The benefits of traveling far outweigh the identity theft dangers, and 90% of the time you will find yourself with all your personal information intact even over the most insecure connection. However, “an ounce of prevention is worth a pound of cure” is almost a mantra in the security industry, and it is even more relevant when traveling. Simply being aware the things that may happen in an untrusted computing environment can go a long way towards keeping you safe and secure while traveling, and taking a few cautionary steps to help protect yourself can help ensure a safe trip.
So go forth and travel the world. Wine, dine, and have a good time. Go on adventures that would make Gulliver jealous. Just keep in mind these few precautions so that you can come home to your own identity once the voyage ends.