
| At a glance | |
|---|---|
| Product | Norton by Symantec Core Router (517) [Website] |
| Summary | Qualcomm-based 4 stream AC2600 class router focused on network security |
| Pros | • Good value for parental control and per-device anti-virus/anti-malware |
| Cons | • Low routing throughput • Poor wireless performance • No USB storage sharing, only printer • Can’t administer router with internet connection down |
Typical Price: $99 Buy From Amazon
Introduction
Updated 10/12/17 – Corrected alternate DNS error, double NAT comments
I have no idea why companies with no previous experience in Wi-Fi routers still want to enter the market. Product cycles are getting shorter with new shiny routers hitting store shelves to entice people to spend their hard-earned cash every six months or so. And the going is particularly tough if part of your product is based on a recurring subscription.
Despite increasing threats from malware, drive-by downloads, poisoned websites, phishing emails, ransomware and all the other crap coming at us from the internet, tech buyers balk at add-on router services. The same people who easily cough up 10 bucks or so a month for Hulu, Netflix or other OTT services suddenly get alligator arms when it comes time to pony up for a subscription security service.
Which brings us to Norton by Symantec’s Core Router. It’s a four-stream AC2600 class router that has Norton’s parental control and security technology baked into an easy to use package. In an attempt to stand out on store shelves and perhaps wow naive buyers, Norton/Symantec chose to go with a geodesic dome format with internal antennas. This makes for perhaps higher WAF, but limits space for the ports necessary to power and connect the beastie. As a result, you get only a three-port LAN switch vs. the usual four. But at least all ports, including the single WAN, are gigabit. The power switch could have been left off, given its inconvenient location, and so could one of the two USB 3.0 ports, since only printer sharing is supported.

Core rear panel
There are neither wireless on/off, nor WPS switches, either hardware or software.
Inside
Symantec/Norton has not released the FCC internal pictures, so I opened the router after testing was done for a look. After finding 3 hidden screws and with some patient prying, the top came off to reveal the photo below. The plastic antenna tower holds four dual-band bent-metal antennas. The heatsink below it has a small fan at its center and is coupled via thermal pads to the RF can tops covering the processor/ RAM and 5 GHz radio sections.
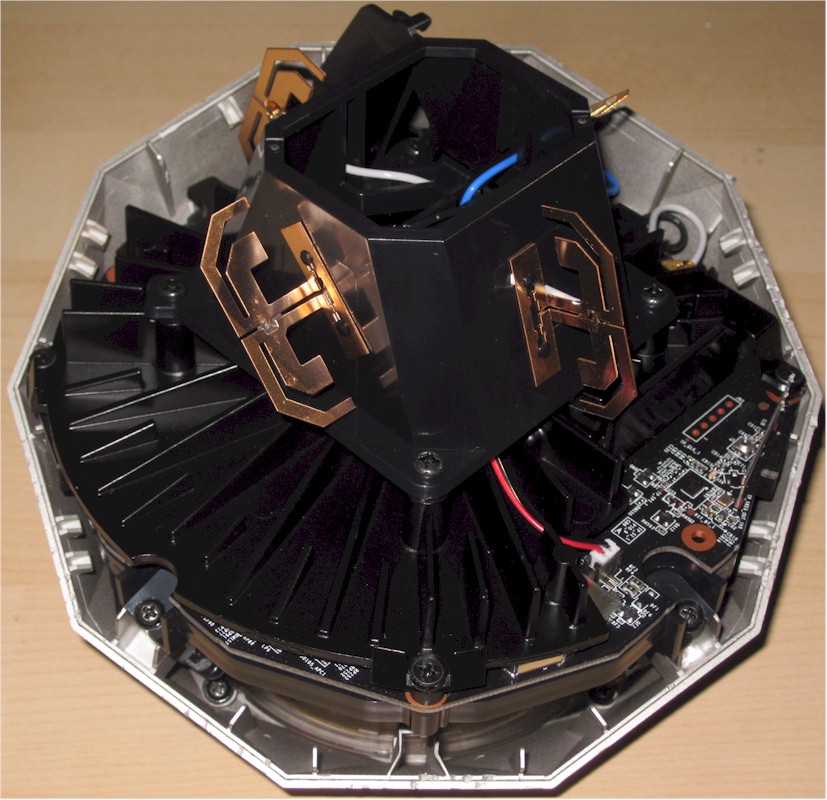
Norton Core inside
The connector board must be removed from the main assembly to get the guts out of the geodesic dome shell.
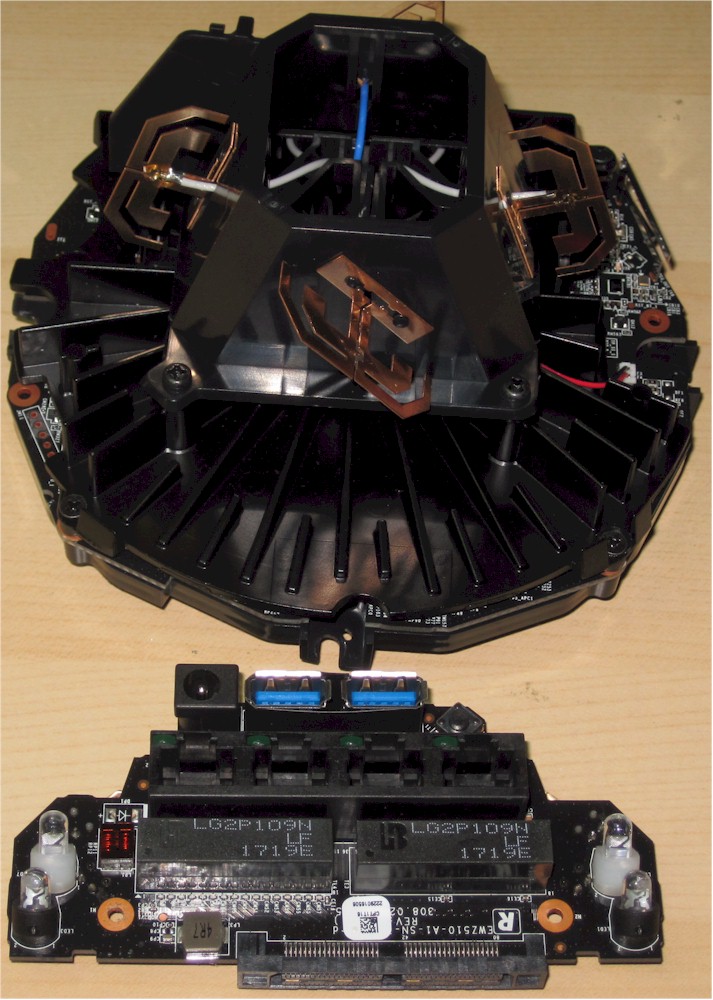
Norton Core two assemblies
Stripping off all the RF can tops shows the CPU / switch and RAM section at top and 5 GHz radios at bottom. It’s pretty clear Core is yet another Qualcomm-based design. Both radios are on plug-in modules connected via mini PCI-e. The 2.4 GHz radio connects to the 5 GHz radio board, which contains switching circuitry to feed both radios to the single set of dual-band antennas.
The Bluetooth 4.1 radio and its bent metal antenna are tucked into the lower left corner.
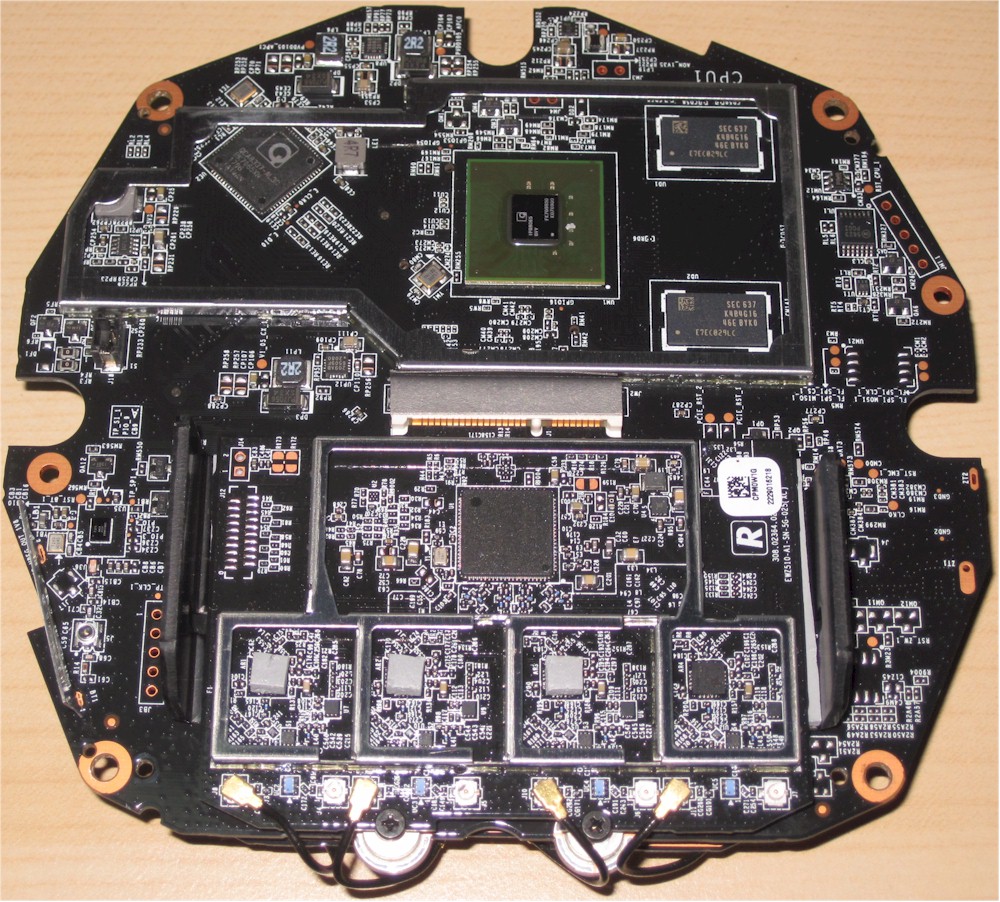
Norton Core board processor side
The other board side holds the 2.4 GHz radio module and eMMC flash to its left.
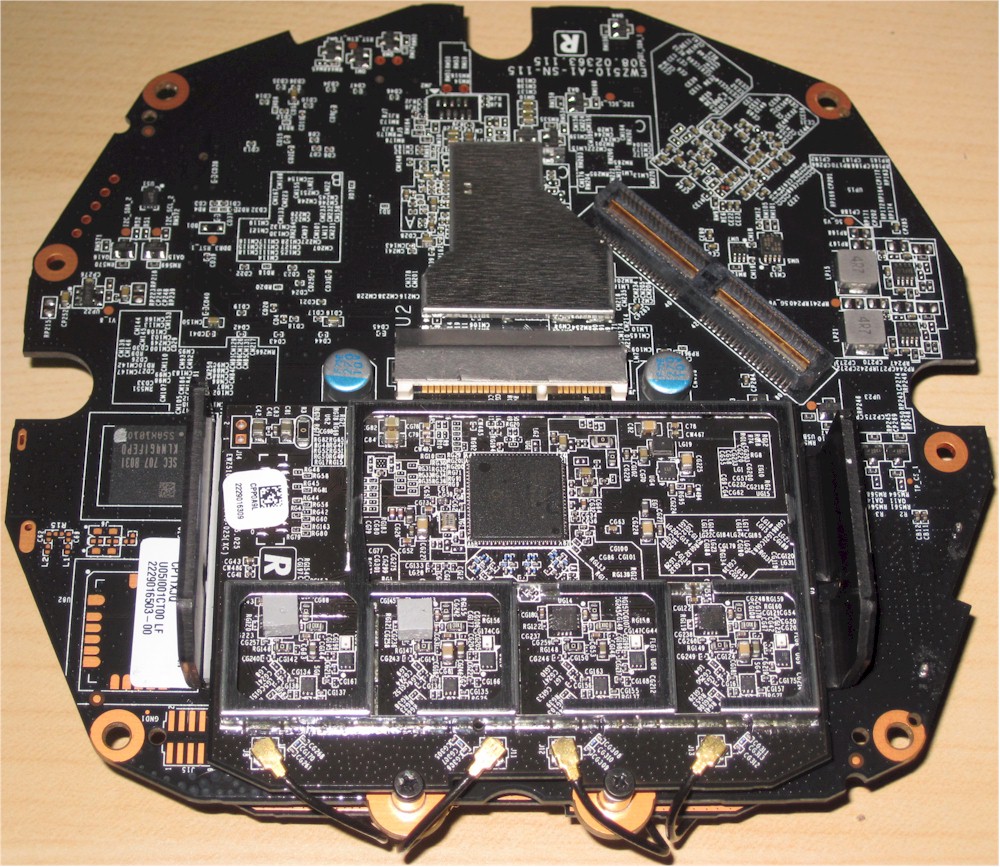
Norton Core board 2.4 GHz radio side
Key components are summaried below along side NETGEAR’s R7800 Nighthawk X4S AC2600 router. The designs are very similar, component-wise except for RAM and flash capacities and the Core’s Bluetooth radio.
| Norton Core | NETGEAR R7800 | |
|---|---|---|
| CPU | Qualcomm dual-core IPQ8065 Internet Processor @ 1.7 GHz | Qualcomm dual-core IPQ8065 Internet Processor @ 1.7 GHz |
| Switch | Qualcomm Atheros QCA8337 | Qualcomm Atheros QCA8337 |
| RAM | 1 GB | 512 MB |
| Flash | 4 GB eMMC | 128 MB |
| 2.4 GHz Radio | – QCA9984 4×4 MU-MIMO 802.11ac radio – MSC5533(?) 2.4 GHz power amp (x4) |
– QCA9984 4×4 MU-MIMO 802.11ac radio – Skyworks SE2623L 2.4 GHz power amp (x4) |
| 5 GHz radio | – QCA9984 4×4 MU-MIMO 802.11ac radio – RFMD RFPA5542 5 GHz PA module (x4) |
– QCA9984 4×4 MU-MIMO 802.11ac radio – RFMD RFPA5542 5 GHz PA module (x4) |
| Bluetooth | CSR8811 Bluetooth 4.1 SoC | N/A |
Table 1: Component summary and comparison
Features
Core requires a subscription to Norton Core Security Plus, which provides all security features. Symantec/Norton bundles a one-year subscription that starts when you activate the router. After that, you’ll pay $9.99/mo. to continue to have all security features. There is no yearly billing option. If you opt to not continue, the router will function, but without any of the security features.
Symantec/Norton chose to go with app-only administration and setup for the Core. If you try to hit the Core’s 172.16.0.1 LAN address, you’ll just get a 403-Forbidden for your trouble. Speaking of addresses, the Core uses a subnet mask of 255.255.0.0 (aka Class B) vs. the usual 255.255.255.0 (aka Class C). So instead of seeing devices all in the 172.16.0.0/24 subnet, you’ll see 172.16.X.2 where X runs from 2 on up.
The "onboarding" experience is more similar to setting up a Wi-Fi System than your typical router. You download iOS or Android apps onto a device that has a Bluetooth radio, which is used for initial connection to the Core. As the screenshot below from the User Guide shows, you have no choice in setting up a Norton account to get the router going. At least you don’t have to surrender a credit card number during sign-up. With the bundled year subscription, Symantec has plenty of time to pry that out of you.
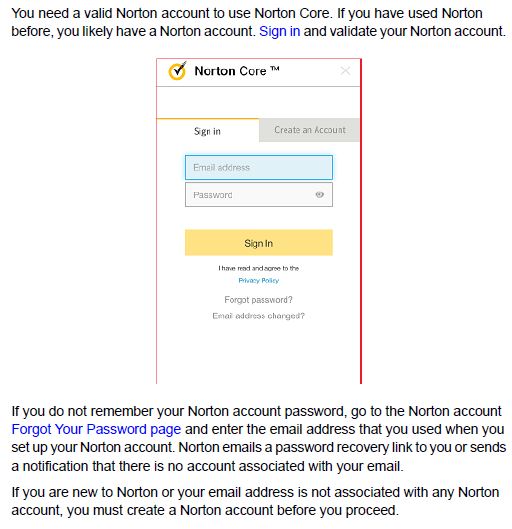
Norton account required
I also found that you need a working internet connection for the app to access the router at all. So if you have internet problems, there is no way you can log into the Core to see what’s up. I hope Symantec changes this to allow local administration. But it’s unlikely, since when I questioned Symantec/Norton about this, they said a connection not secured by its cloud would be another attack surface, which it is trying to minimize.
Core’s focus is security, so the router feature set is more like eero (with eero plus) than a typical ASUS RT-AC series router. The app Home page obviously emphasizes security by putting the Security Score front and center. The screenshot also shows the hamburger menu extended.
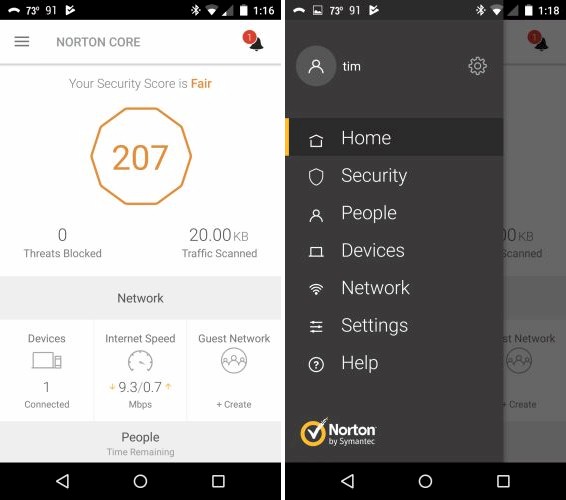
Core Home and menu
Tapping on the little bell on the Home screen brings up the Alerts/Notifications screen (left). The Security menu provides details behind your Security Score with suggested fixes. My relatively low score was due to running Core behind another router, my weak Wi-Fi password (11111111) used for testing and the single port I opened for testing.
Updated 10/12/17
I don’t didn’t agree with the ding for running double-NAT. Since all devices are connected to Core, all traffic will end up passing through it anyway. Most users are forced into double-NAT when they want to use a different router than their ISP-provided modem/router combo and the ISP won’t let them bridge the router portion. So they wouldn’t intentionally connect anything to the ISP router since all those devices would be on a separate network.
But Symantec is trying to address all potential security risks. So since it would still be possible to have devices connected to the ISP router—like when that router’s Wi-Fi isn’t shut off—I now agree it’s fair for double-NAT to lower the Security Score.
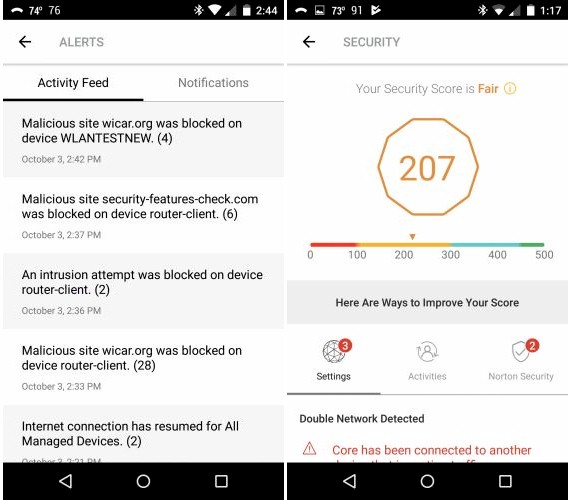
Core Alerts and Security
You also get security demerits if you aren’t running Norton Security on all Windows, MacOS, iOS and Android devices. You get an unlimited number of licenses for Norton Security Premium with the Core subscription, so you might as well use them because Core does not run an anti-virus engine.
Since products like Core, Bitdefender Box, Luma, etc. depend on a combination of local and cloud services for their protection features, I asked the company what runs where. This was their response:
"The DPI/IPS (Deep Packet Inspection/Intrusion Prevention System) detects malware, network attacks, and protocol anomalies and is done entirely on the router, driven by signatures that are updated regularly – it’s the same network security technology that is responsible for blocking 50%+ of threats blocked on our endpoint security products. Our reputation technologies (URL, executable files, and mobile applications) are cloud based lookups which won’t be available without cloud access. However, no traffic gets “passed to the cloud” and the reputation technologies are mostly useful against threats present in the cloud itself."
I’ll come back to this later when I present the results of our security feature testing.
Many people will buy Core for its Parental Controls, which are found under the People menu. Core supports User-based security, with the ability to assign devices to users. Web filtering and internet use time limits can be set for each user, as shown below.
Each user has a pause button that kills internet (but not local network) access instantly. You can kill internet access for all devices via a Pause internet for all devices button on the Devices menu. Note the Pause internet buttons don’t have selectable timeouts. So you’ll have to remember to re-enable access before you take that business trip or you’ll get the dreaded family tech support call.
The Shared category shown below is the default category for all devices that aren’t assigned to another People profile.
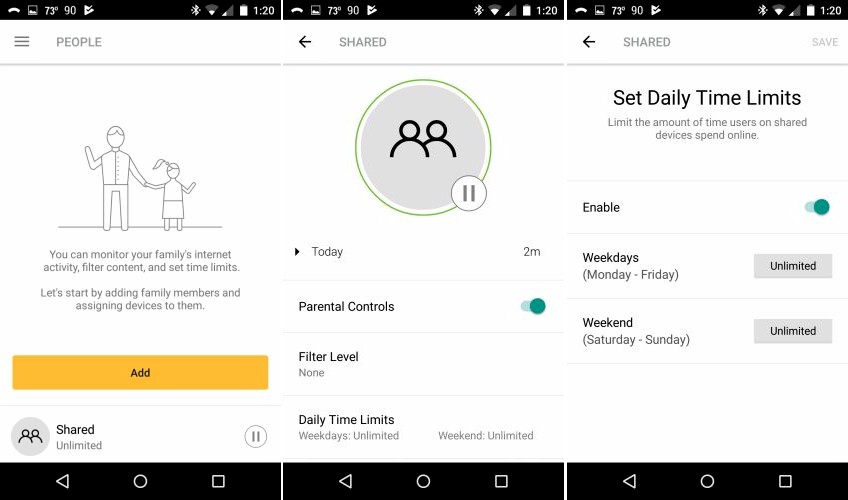
Core People menus
Web filters themselves use a familiar age-based model and include the ability to tweak blocked categories. You can also allow/block specific websites for each user profile that override the blocked categories. If you want to block all websites except those you list, I suppose you just block all categories and add your sites to the allowed sites list.
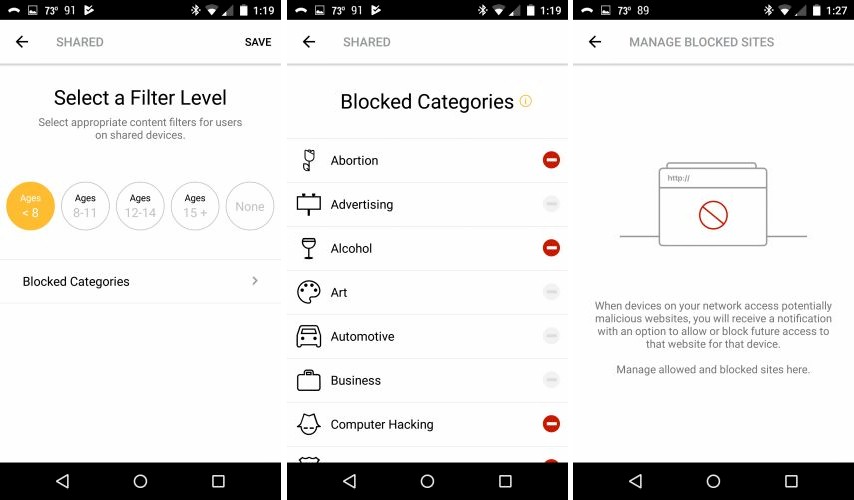
Core web filtering
Internet access controls are limited to domain blocking only; there is no ability to limit access to specific services either by name or port number. This may be beyond many users’ needs, but is a notable omission for a router touting itself as focused on security. This means you can’t block access to any apps that you don’t know the URL for or apps that require both URL and ports to be blocked.
Since this is a Wi-Fi router, I suppose we should look at those controls. These are located under the Settings menu, not the Network menu, as you might properly assume from the wireless icon…
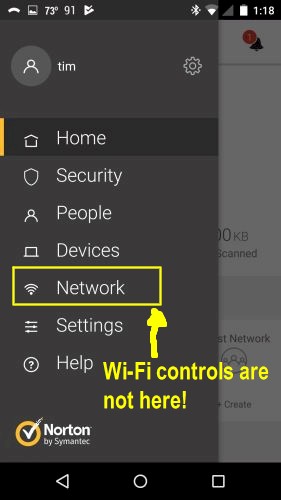
Core Wi-Fi controls are not here
Core defaults to a single SSID, which can be changed to separate ones for each band for the main and Guest SSIDs. Aside from that, there isn’t anything else you can do to control Wi-Fi. There are no controls for channel, bandwidth or client isolation. There is also no MU-MIMO or beamforming disable. I think the app should at least tell you the channel and bandwidth Core is using.
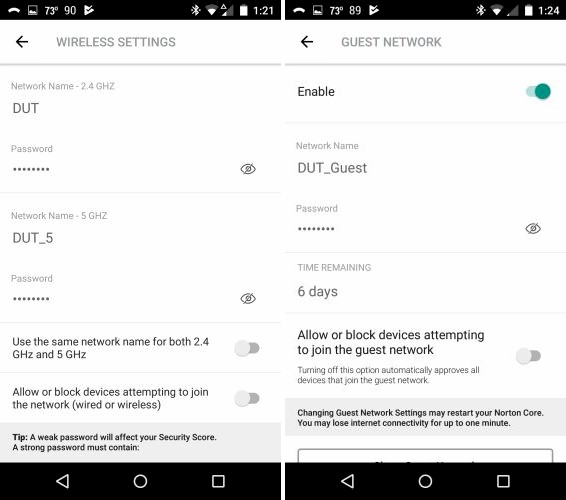
Core Wi-Fi controls
A few other features are worth mention. UPnP is supported, but disabled by default due to security risks. If you enable it, Core will alert you when it gets a UPnP request to open firewall ports. I tested this and was able to block my smartphone when Skype tried to open ports via UPnP. But when I changed the block to allow or even forgot the UPnP device, I wasn’t able to get Core to show the phone again when I reconnected it and relaunched Skype.
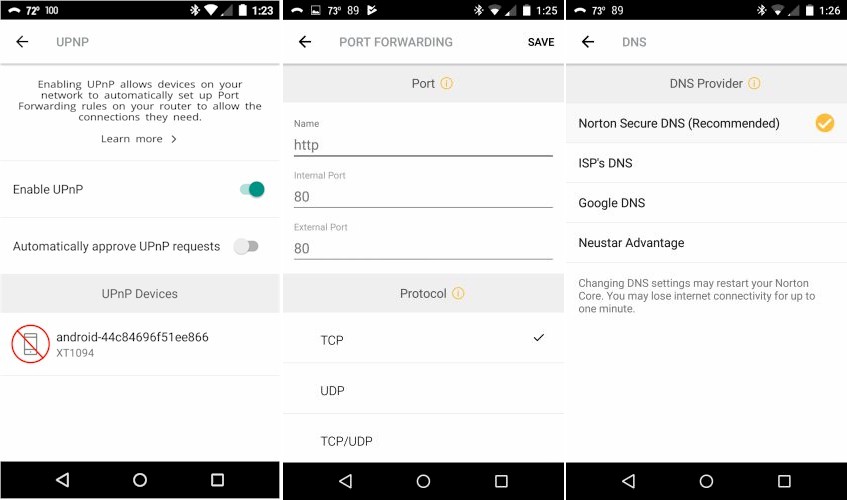
Core UPnP, Forward, DNS controls
Updated 10/12/17
Port forwarding is single port only and does not support triggered port forwards. You can select from the three alternate DNSSEC DNS providers shown and still get all security features. but I don’t know why you would. You must use Norton’s DNS to get parental control content filtering.
In case I forgot something, here’s a summary of supported and not supported router features. The supported list is fairly limited, but should be sufficient for many people whose only exposure to router administration screens is during setup.
Supported:
- DHCP reservations
- Single port forwarding
- Internet pause (all or individual devices)
- User-based parental controls with assignable devices
- Content filters
- URL blocking
- Internet time limits
- Internet speed test
- Priority device
- Guest Wi-Fi network
- MU-MIMO
- UPnP (default disabled) with allow/deny alerts when enabled
- DNS service selection
- Secure remote administration
Not supported:
- Any WAN type other than DHCP or Static
- Ability to set or see Wi-Fi channels or bandwidth. You can change the default of a single SSID to separate 2.4 and 5 GHz SSIDs, however.
- Wi-Fi Protected Setup (WPS)
- WEP wireless security
- DMZ
- MAC address filtering
- Triggered port forwarding
- Port range forwarding
- Service (port) filtering
- IPv6
- VPN server
- Dynamic DNS
- App pass-through controls (VPN, SIP, etc.)
- Band steering
- MU-MIMO disable
The gallery has additional (Android) app screenshots with commentary.
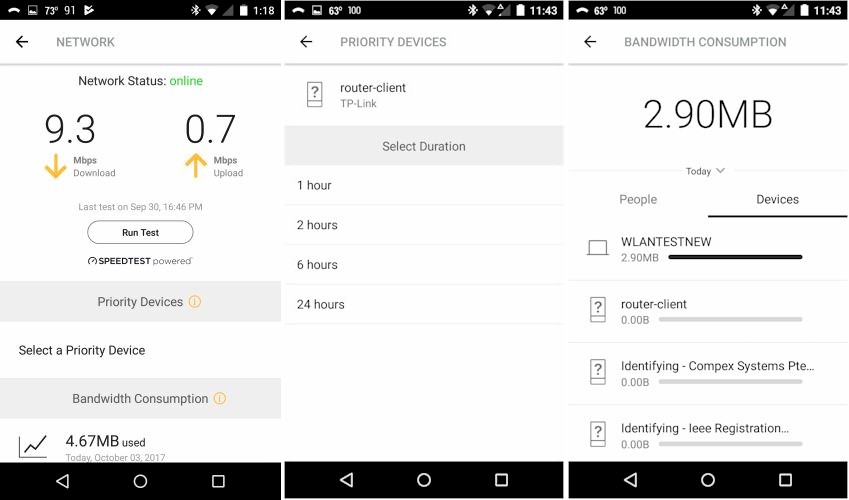
You run a internet up/download speed test, set priority devices and check bandwidth use on these screens
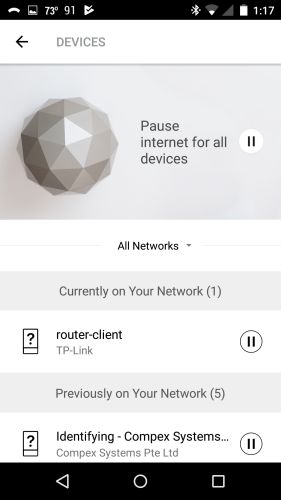
This is where you pause internet for all devices.
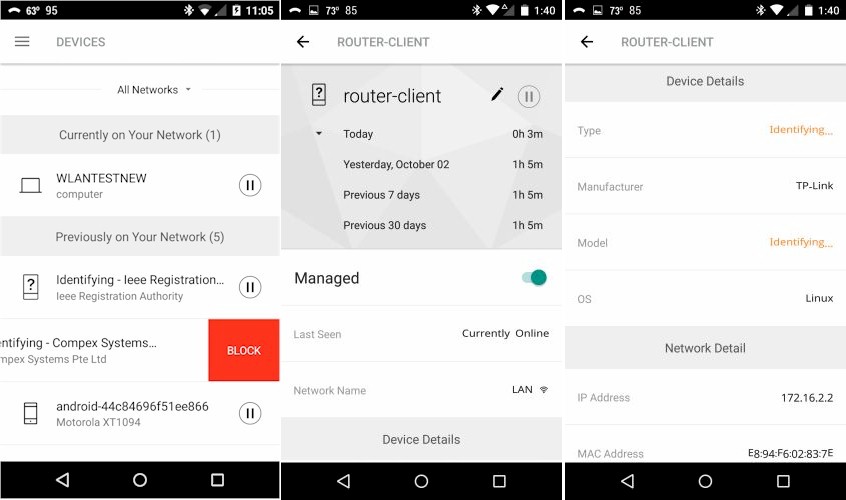
You can block and get more information on specific devices.
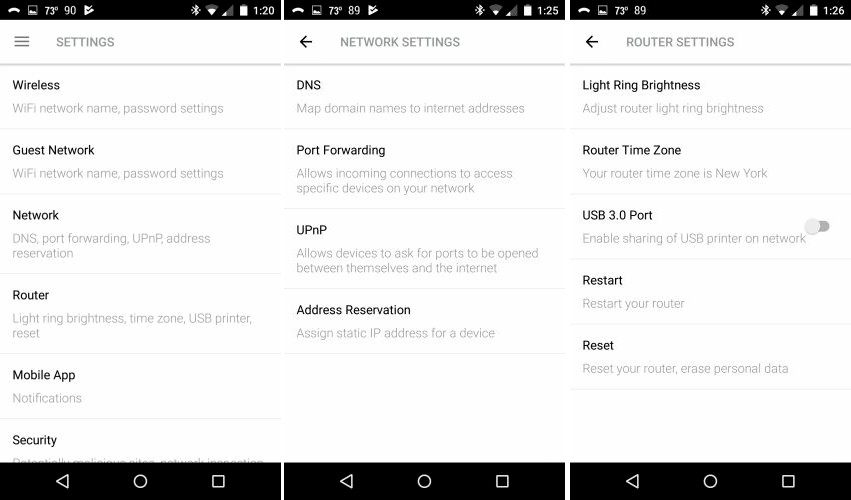
The Settings menu also includes an About sub-menu not shown.
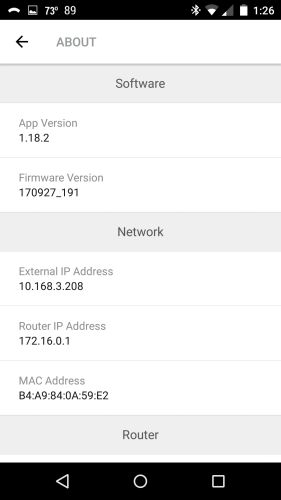
You need to dig deep into the Settings > About menu to find WAN and LAN IP addresses. You can’t release/renew the WAN DHCP lease.
Security Test
Doing a proper check of security products requires tools and knowledge beyond my expertise. So I stuck to a rather small set of tests. I confirmed that devices could be blocked and paused, which produced the block messages below when I tried to browse. If I stopped then restarted the block, however, I could not get the messages to reappear.
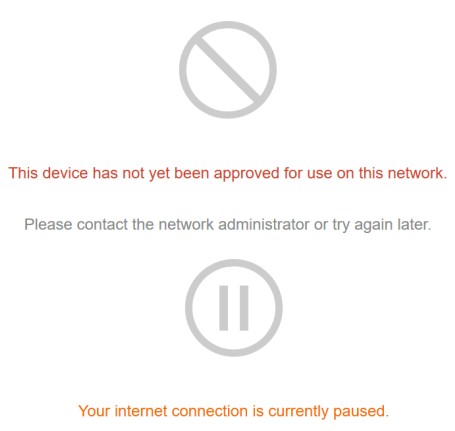
Core device block messages
I did a quick check of web filtering by setting the Filter Level to Ages < 8 for the default shared category. I then went to Google and entered "porn" in the search bar and got plenty of search results, both listings and images. This is typical of any web filtering "solution" I’ve tried, which is why I don’t spend much time testing web filtering.
I was more interested in testing Core’s DPI/IPS/IDS features that are supposed to protect against bad things other than naughty websites. Despite the awesome power implied by these acronyms, packet inspection features on consumer routers, even those with multi-core processors, are pretty limited. They generally are limited to blocking access to internet servers known to host malware or other nasty stuff designed to mess you up, bigly.
Since I don’t subscribe to AMTSO’s (Anti-Malware Testing Standards Organization) Real Time Threat List (RTTL), I settled for running all WICAR.org’s Malware tests. All 12 triggered the page shown below, once I bypassed the warning page Firefox first put up.
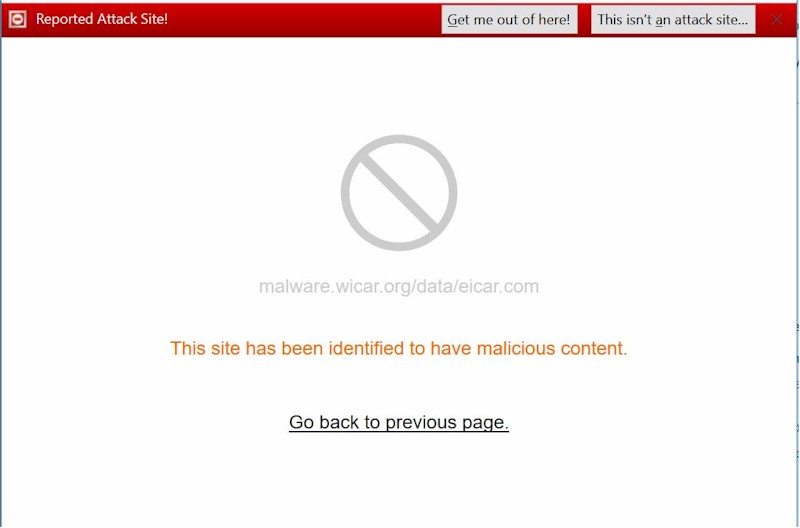
Core WICAR malware test result
My last security test attempted to verify Core’s claims to protect against rogue IoT devices. I did this by using nping to execute a SYN flood from a system on Core’s LAN to a machine on its WAN, i.e. nping -tcp -p 5000 –flags SYN -c 10000 –rate 1000 10.168.X.Y I ran this multiple times, with not a peep out of Core.
Thinking the attack might not be enough to be seen as a compromised machine acting as a zombie in a DDoS attack, I then tried hping3 and the command lines suggested in this article. Again, no matter what I tried, Core didn’t flag a thing. So if you’re expecting Core to let you know if something on your network has been zombified and is being used to DDoS someone, that’s not going to happen.
Routing Performance
The Core was tested with our new V10 router test process, loaded with 170927_191 firmware. It didn’t do very well. Core has three levels of network inspection, which the app warns affect routing performance. I tested ran the test suite in all three modes, but the results posted in the Router Charts and used for ranking are with the Default setting.
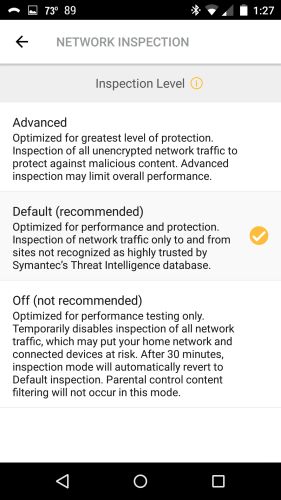
Core Network Inspection Levels
The table shows results for all three Core modes and includes results for the current top-ranked ASUS GT-AC5300. Yes, I know it’s not a fair comparison, but it does show that Core’s routing will not keep up with higher bandwidth internet services. Even if you used the Off mode—which would be nuts since it disables all the security that you bought the Core for in the first place—the HTTP scores show Core won’t keep up with heavy traffic loads.
| Test Description | Norton Core (default) | Norton Core (Off) | Norton Core (Advanced) | ASUS GT-AC5300 |
|---|---|---|---|---|
| WAN – LAN Throughput (Mbps) | 62.7 | 934 | 66.9 | 719 |
| LAN – WAN Throughput (Mbps) | 58.4 | 940 | 59.9 | 713 |
| HTTP Score – WAN to LAN (%) | 4.4 | 4.5 | 3.2 | 68.1 |
| HTTP Score – LAN to WAN (%) | 4.9 | 4.7 | 4.9 | 68.4 |
| Bufferbloat Score- Down Avg. | 1282 | 266 | 1259 | 450 |
| Bufferbloat Score- Down Max. | 253 | 235 | 253 | 317 |
| Bufferbloat Score- Up Avg. | 1133 | 521 | 1311 | 227 |
| Bufferbloat Score- Up Max. | 70 | 375 | 775 | 162 |
| CTF Score (%) | 6.2 | – | – | 64.5 |
| Firmware Version | 170927_191 | 3.0.0.4.382_12184 | ||
Table 2: Routing throughput
I thought it odd that Bufferbloat increased in the Off mode. But even then, we’re talking latency of 3.7 ms average and 4.3 ms maximum for download and 1.9 average and 2.7 ms maximum. Default mode had average up and download latencies below 1 ms. The HTTP Score plots by filesize are below. Core never really gets out of the mud running in either direction.
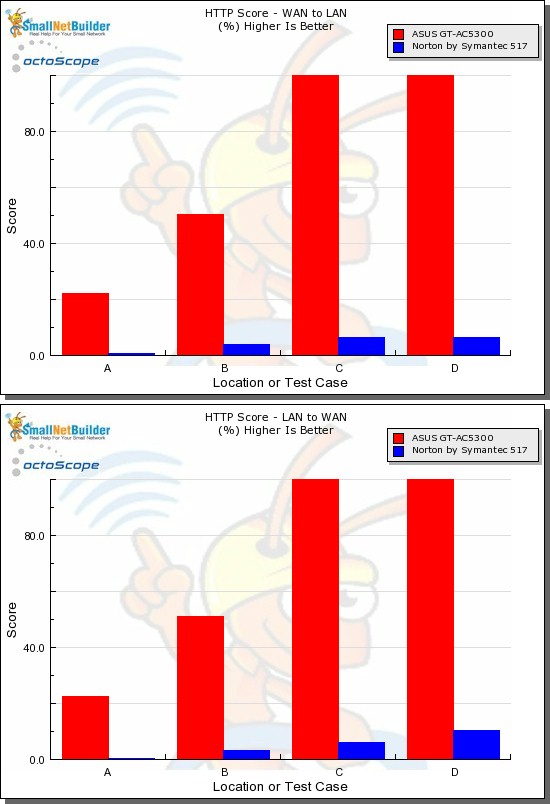
HTTP Score comparison
Plot key file size: [A] 2 KB, [B] 10 KB, [C] 108 KB and [D] 759 KB file
I based the Cut Through Forwarding score on the worst case difference between routing throughput in default mode and both Off and Advanced mode. Yep, Core ekes out only around 6% of the Off mode throughput when running in its Default mode.
Wireless Performance
The Core is not Wi-Fi Certified and was tested with the Revision 10 wireless test process loaded with 170927_191 firmware. Since the app provides no control over channel or bandwidth, I had to take what I got, which was Channel 1 / 40 MHz bandwidth for 2.4 GHz and Channel 36 / 80 MHz bandwidth for 5 GHz.
However, the Revision 10 process still uses 20 MHz bandwidth for 2.4 GHz tests for throughput vs. range, but uses 40 MHz for peak throughput tests. These settings are enforced by the octoScope Pal test client.
The router body was centered on the test chamber turntable as shown in the photo below. The 0° position for the router had the front facing the chamber antennas. Although you see four chamber antennas in the photo, only the center two are used for throughput vs. attenuation testing, which is done with the Pal set to operate as a 2×2 AC device.
Core in test chamber
I haven’t tested a lot of routers with the Revision 10 process due to concentrating on the more popular Wi-Fi Systems. So I have no other 4×4 routers to compare with. Instead I’ll put the Core up against two 3×3 routers, NETGEAR’s newer R7000P and original R7000 Nighthawk.
First comparing 2.4 GHz average throughput, we find Core coming in last for both down and uplink. At least it’s not alone, joined by the R700P.
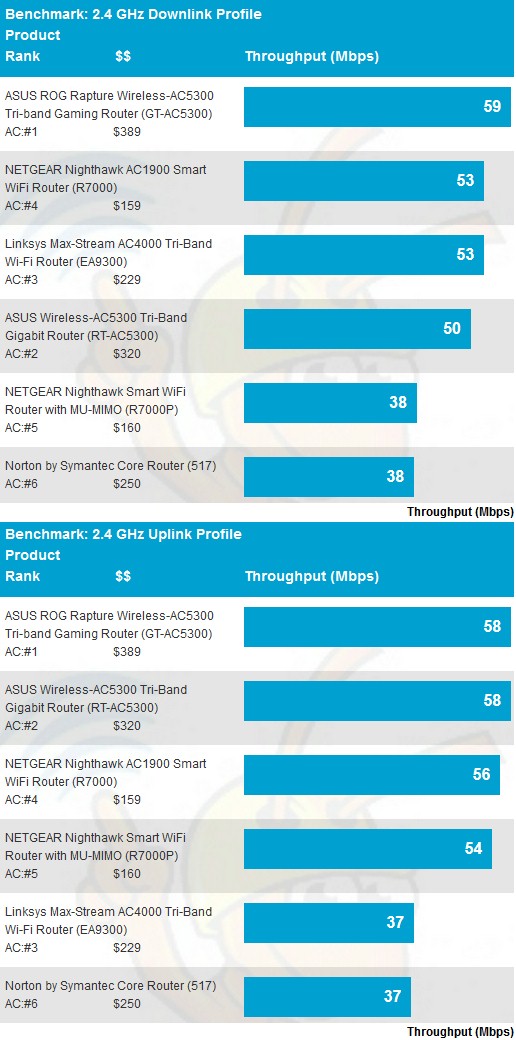
2.4 GHz average throughput comparison
Core fares better in the 5 GHz benchmarks for downlink, but coming in once again at the bottom of the chart for uplink.
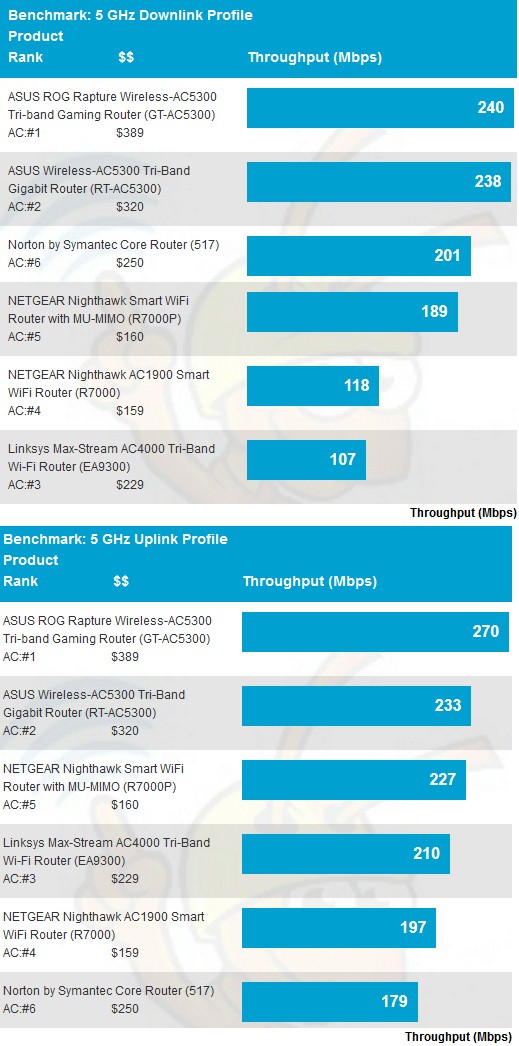
5 GHz average throughput comparison
The 2.4 GHz downlink profile shows why Core did so poorly, starting out lower than the NETGEAR R7000 and falling off faster than the R7000P. It was also the first to disconnect after the 39 dB attenuation test.
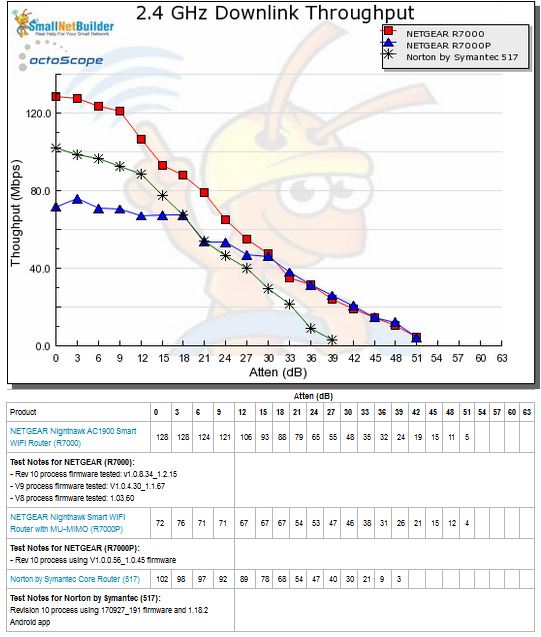
2.4 GHz Downlink Throughput vs. Attenuation
2.4 GHz uplink shows a similar pattern, although with higher starting throughput. But Core’s rapid throughput decline and early disconnect end it up at the bottom of this chart, too.
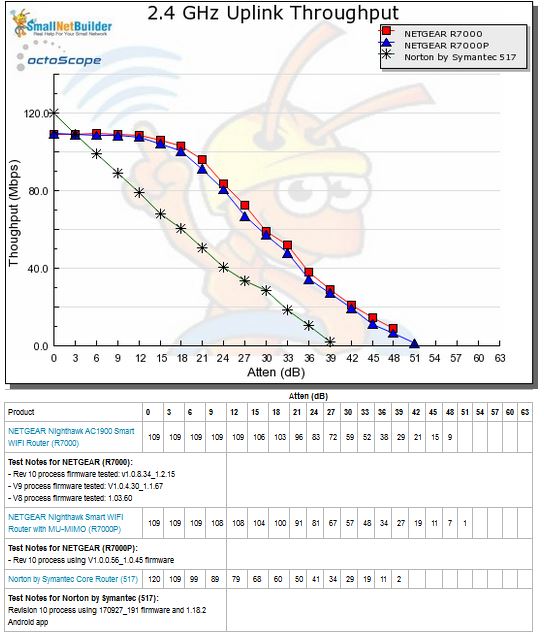
2.4 GHz Uplink Throughput vs. Attenuation
Core starts out strong for 5 GHz downlink and, for awhile, looks like it might go the distance. But throughput collapses after the 18 dB attenuation test. The plotted results are the average of two complete test runs, so this effect was repeatable.
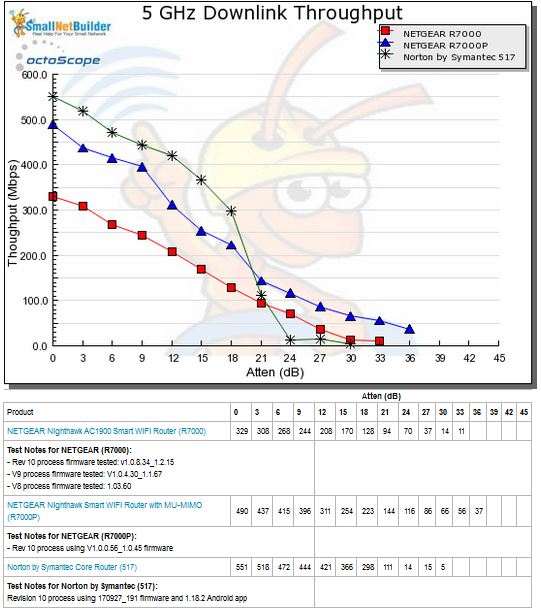
5 GHz Downlink Throughput vs. Attenuation
Looking at the stats from the octoScope Pal test client, it’s clear that TX rate went south pretty quickly after 21 dB, indicating a problem with MCS rate management.
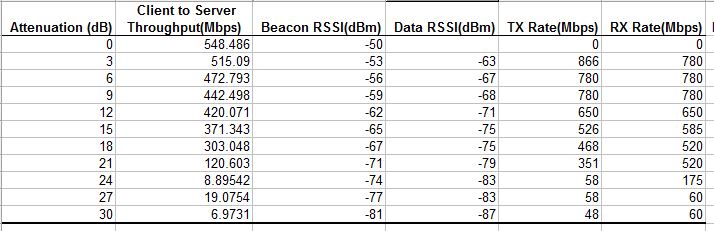
5 GHz Downlink octoScope Pal statistics
5 GHz uplink shows Core starting out at the same ~560 Mbps as NETGEAR’s R7000. But Core’s steeper decline again makes it disconnect earlier and push it down in the Chart ranking.
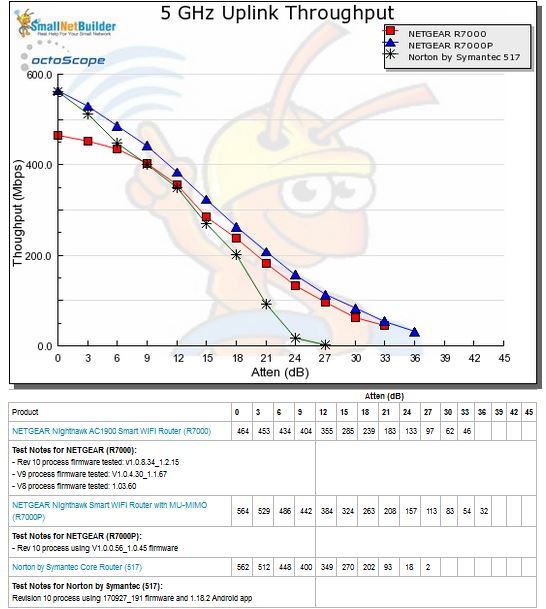
5 GHz Uplink Throughput vs. Attenuation
A look at the Pal uplink stats again shows a rapid decline in link rates.
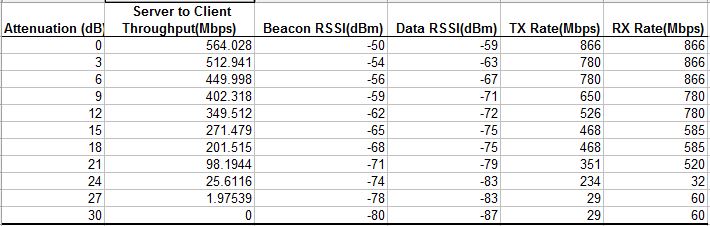
5 GHz Uplink octoScope Pal statistics
For our peak wireless performance tests, the octoPals are configured as 4×4 AC devices and left to negotiate their best connection, with 10 dB of attenuation applied on 2.4 GHz. The latter is necessary so the 2.4 GHz octoScope Pal isn’t overloaded.
The octoScope Pal test client reported 720 Mbps as the highest link rate vs. the 800 Mbps maximum possible using 256 QAM in the 2.4 GHz tests. The maximum possible 1300 Mbps was seen for the 5 GHz tests. The peak 2.4 GHz tests are the only two wireless benchmarks where Core outdid the two NETGEARs. However, Core also turned in respectable results in the 5 GHz peak throughput tests.
| Test Description | Norton Core | NETGEAR R7000P | NETGEAR R7000 |
|---|---|---|---|
| 2.4 GHz Peak Downlink (Mbps) | 472 | 221 | 220 |
| 2.4 GHz Peak Uplink (Mbps) | 500 | 134 | 116 |
| 5 GHz Peak Downlink (Mbps) | 884 | 940 | 929 |
| 5 GHz Peak Uplink (Mbps) | 931 | 940 | 842 |
Table 3: Peak Wireless throughput
I didn’t test MU-MIMO because it rarely provides significant benefit, if any at all.
Closing Thoughts
Many of us are looking for an reasonably-priced, easy-to-use solution to help protect us against the evils that lurk on today’s internet. And some of us are getting to the point where we won’t mind paying a reasonable monthly fee to ensure that safety.
Unfortunately, like most other internet security "solutions" we’ve looked at, Norton by Symantec’s Core Router doesn’t make the grade. It failed our very simple zombie machine check and has the usual weaknesses with its website content filtering.
If you use Core with devices protected by its companion Norton Security Premium Windows, MacOS, iOS and Android apps, you’ll be able to rest a little easier. But if you’re expecting it to detect all the nefarious activity your webcams, streamers, printers, etc. might be up to, it doesn’t look like it will.
Most of all, Core fails the minimum requirements for any router that hopes to make it today, specifically, the ability to keep up with 100 Mbps+ internet connections and decent Wi-Fi performance. No matter how good Core’s security features may be, if it has worse Wi-Fi performance than the router it replaces, it will probably go right back to the store. Since Core’s performance landed it at the bottom of our Router Ranker, I can’t even recommend Core as a plain ol’ Wi-Fi router.
