
| At a glance | |
|---|---|
| Product | Zyxel Next-Gen Unified Security Gateway-Performance Series (USG40) [Website] |
| Summary | Dual WAN UTM router with Gigabit ports, IPsec and SSL gateways, one-to-one NAT, bandwidth management and more |
| Pros | • Big performance gain over USG20 • VPN solutions for IPSec, SSL, and L2TP • Powerful application management features |
| Cons | • L2TP configuration is challenging • More than 10 IPsec & 2 SSL tunnels cost extra • IPsec client not bundled • UTM bundle license renewal is very expensive |
Typical Price: $463 Buy From Amazon
Introduction
Updated 12/11/14: Various updates & corrections
In June, ZyXEL introduced its new Performance and Advanced series Unified Threat Management (UTM) devices. The Performance series includes the USG40, USG40W, USG60, and USG60W. The Advanced series includes the USG110, USG210, and USG310.
The Performance series models with “W” indicate Wi-Fi. The USG40W has an integrated N300 class 2.4 GHz only access point and the USG60W has an integrated dual-band N600 class AP. ZyXEL recommends the USG40/USG40W for networks with 1-10 users, and the USG60/USG60W for networks with 10-25 users.
ZyXEL refers to the Performance series devices as “all-in-one Next Generation Firewalls.” In this review, I’m going to take a look at the ZyXEL USG40, which is a significant update to the ZyXEL USG20 I reviewed awhile back.
Inside
The USG40 is housed in a gray metal case with red trim, similar to ZyXEL’s styling for the USG20 and ZyWALL 110. The USG40 measures 9.53″W x 6.89″H x 1.42″ H. The power supply is external. Unlike the USG20 and ZyWALL 110, the USG40 has passive cooling, thus it runs silent which is nice if the router is located near humans. The USG40 has adhesive rubber feet for desktop use.
The front of the USG40, as shown in the diagram below, presents the status and port LEDs.
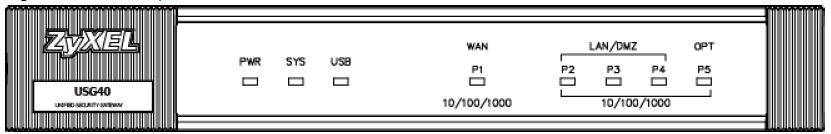
Front
The rear of the USG40, as shown in the diagram below, is where you’ll find the RJ45 ports and USB port.
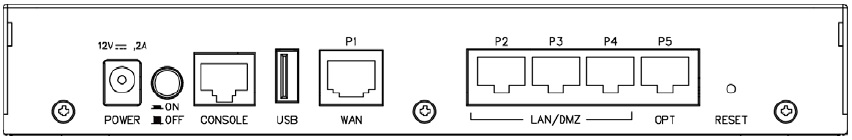
Rear
Internally, the USG40 has a single-core Cavium CN6010 CPU, 1 GB DDR3 RAM, 4 GB Flash and a Qualcomm Atheros AR8327-BL1A 7 port Gigabit Ethernet switch. A shot of the USG40 mainboard is below. The USG60 has the same RAM and flash but swaps in a dual-core Cavium CN6020 and adds a Qualcomm Atheros AR8033-AL1A Gigabit Ethernet PHY.

USG 40 Main Board
Features
The USG40 is a feature-rich device as you can see in the below list compiled from ZyXEL’s data sheet and website.
Hardware
Performance Ratings
Networking
IPv6
WLAN
IPsec and L2TP VPN
SSL VPN
Security/Firewall
|
Intrusion Detection and Prevention (IDP)
Application Intelligence and Optimization
Anti-Virus
Anti-Spam
Content Filtering
Authentication
System Management
Logging and Monitoring
|
Configuration
The USG40 has a similar menu structure and GUI to the USG20 and ZyWALL 110. In addition to the GUI, the USG40 can be managed from the command line via Telnet, SSH and direct console connection. A virtual console connection is also accessible via the GUI.
When you log in, you’re presented with a useful dashboard that displays Device Information, Security Service and License Status, System Status, System Resource utilization and statistics for Content Filtering, Viruses, Intrusions, and Security Policies. Below is a screenshot of the dashboard.
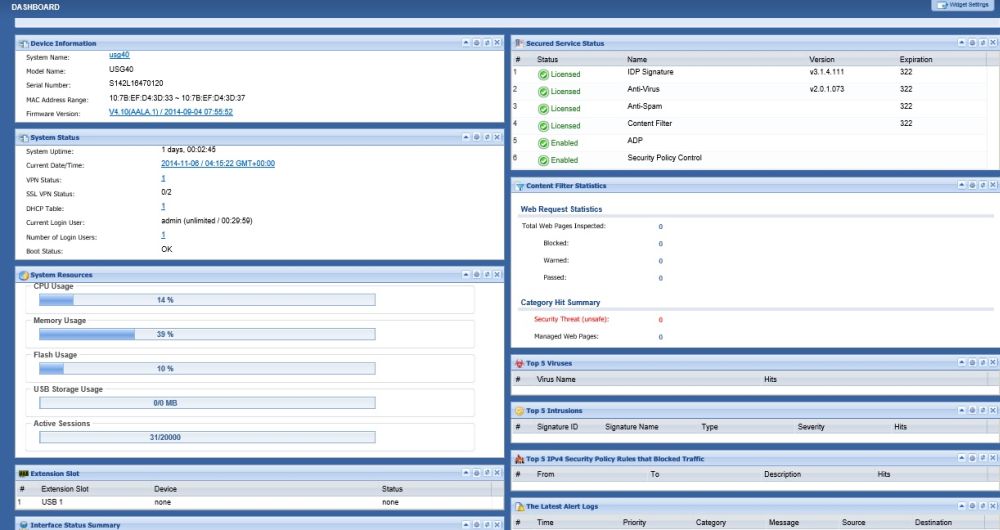
Dashboard
At the top of the dashboard, you can see virtual images providing a real-time view of the front (shown below) and rear of the device.
Virtual Front Panel
The USG40 uses an object oriented configuration model. Objects are created for interface zones, user management, access points, application control, IPv4 addresses, network services, manageable schedules, authentication servers, authentication methods, certificates, WAN profiles, ISP authentication and SSL applications. Creating an object is a common first step in configuring the USG40. Once an object is created, you apply it in a profile and then attach that profile to a rule to manage network traffic.
For example, to configure an IPsec tunnel, first you create an IPv4 address object matching the subnet of the far end router’s LAN. You then use that object in the Policy section of the VPN Connection configuration.
ZyXEL has done a good job organizing the USG40’s configuration screens. This is critical, as the device literally has hundred of configuration options. Menus for configuring the USG40 include Licensing, Wireless, Network, Web Authentication, Security Policy, VPN, Bandwidth Management (BWM), UTM Profiles, Objects, System, and Logging/Reporting Options. Within each of these menus are submenus, each with one or more tabs where configurations are entered. ZyXEL further simplified WAN, IPsec and L2TP setup by providing useful step by step configuration wizards.
The 741 page manual for the USG40 provides an overview of configuration options. I’ve struggled with some of the configuration options on ZyXEL devices in the past, but I’ve found ZyXEL’s growing support library to provide useful configuration examples. Keyword searches on ZyXEL’s Support Document site returns a good number of step by step guides.
Network
There are five 10/100/1000 RJ45 Ethernet ports on the USG40 while the USG60 has six. An image of the USG40 port configuration screen is shown below.
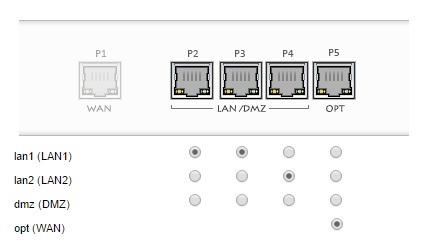
Interfaces
Updated 12/11/14
The physical ports (P1-P5) can be assigned to a port type (WAN1, LAN1, LAN2, DMZ, and OPT). Each port type can be enabled or disabled, plus ingress/egress bandwidth and MTU can be changed.
One interface is dedicated as the WAN1 interface. Three interfaces can be configured as members of the LAN1, LAN2 or DMZ internal zones. The last interface can be configured as a member of the LAN1, LAN2, DMZ or WAN zone. Thus, the USG40 has the flexibility of being a dual WAN router if you have dual WAN connections. If you don’t have dual WAN connections, you can still use the last interface as a member of an internal zone.
In addition to dual WAN connections via Ethernet ports, the USG40 has a single USB port where a 3G / 4G WWAN network connection can be used as a WAN connection. The USG60 has two USB ports. ZyXEL lists support for 151 USB 3G devices here in the download library for the USG40. The USB port on the USG40 can also be used to store the USG40’s sys logs and diagnostic information. It can’t be used for shared network storage, though.
The USG40 also supports 802.1q VLAN tagging, enabling even greater network segmentation then available with the physical interfaces. VLAN tags can be between 1-4094 and the USG40 can have up to 8 different active VLANs, each with its own DHCP server.
The USG40 supports policy based routing, routing protocols including RIP and OSPF, as well as Static routes. Additional networking options include dynamic DNS from multiple suppliers, configurable network address translations, and VoIP and FTP application layer gateway (ALG).
Wireless networking is supported in two ways by the Performance series devices. As mentioned previously, two models (USG40W and USG60W) have integrated access points. All four models of the Performance series can function as WLAN controllers for specific models of ZyXEL access points.
Out of the box, the Performance series devices can manage two access points, but that can be increased to ten access points with a license upgrade. Supported access points are the ZyXEL NWA3000-N, NWA5000-N, and NWA5120-N series devices. (Specific model numbers are listed on the Wi-Fi compatibility tab on the ZyXEL product page.)
VPN
The USG40 supports IPsec, SSL and L2TP VPN connections in much the same manner as the ZyWALL 110. Up to 20 concurrent IPsec tunnels and 12 concurrent SSL tunnels are supported. L2TP tunnels, which use IPsec encryption, count as part of the 20 concurrent IPsec tunnel limit.
I had no problem setting up a site-to-site IPsec VPN tunnel between the USG40 and a ZyWALL 110. Phase 1 and Phase 2 IPsec tunnel options include DES, 3DES, AES128, AES192 and AES256 encryption; plus MD5, SHA1, SHA256, and SHA512 authentication. I set up my tunnel using AES256 encryption and SHA1 authentication.
For IPsec peer authentication, the USG40 supports pre-shared key and certificate authentication. I was able to set up an IPsec tunnel on the USG40 with both methods. Note, IPsec throughput is not affected by the peer authentication method, which I verified in my IPsec throughput tests, which I’ll cover shortly.
Pre-shared key authentication is easier to configure, just enter a common key on both IPsec routers. Certificate authentication between two ZyXEL routers isn’t much more difficult and is more secure than pre-shared key authentication. Certificate authentication involves clicking the certificate option in the VPN menu instead of the pre-shared key option and exchanging certificates.
Exchanging certificates is done with the export and import options in the Object-Certificate menu. I exported the default self-signed certificate from the USG40, saved it on my PC, then imported it into the ZyWALL 110 as a trusted certificate. Then, I exported the default self-signed certificate from the ZyWALL 110, saved it on my PC, then imported it into the USG40 as a trusted certificate. In the screenshot below from the USG40, you can see the imported certificate from the ZyWALL 110.
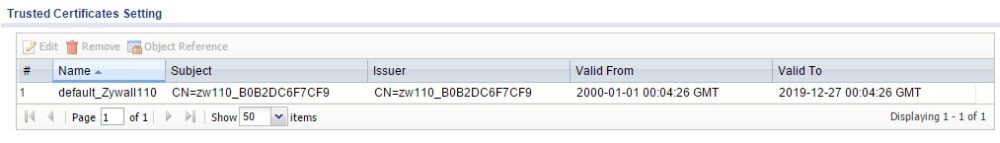
Certificate
Below is a screenshot from the USG40 showing my active IPsec tunnel to the ZyWALL 110 using certificate authentication.
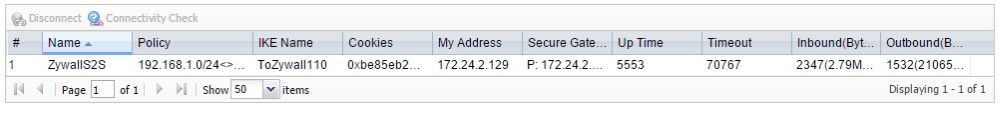
IPsec
Updated 12/11/14
The ZyWALL IPsec VPN Client, which is based on software from Greenbow, provides remote IPsec VPN connectivity. I had a few challenges getting remote IPsec VPN connectivity to work.
There are configuration wizards in the router and client software, but the values don’t match and require editing. The router wizard configures Phase 1 with DES, MD5, and DH1 and Phase 2 with DES, SHA-1 and PFS=none. In contrast, the client software wizard configures Phase 1 with 3DES, SHA-1, and DH2 and Phase 2 with 3DES, SHA-1 and PFS=DH2.
I edited the router to match the client software settings for both Phase 1 and Phase 2. Below is a screenshot showing Phase 1 (gateway) settings on the client software.
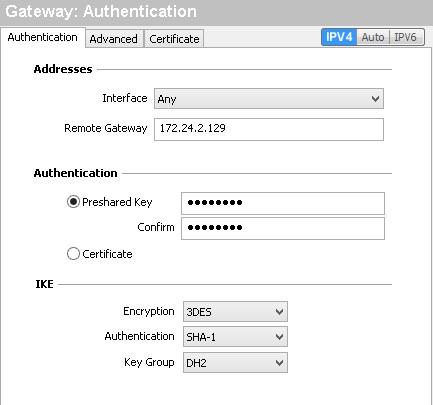
Phase 1 Config
Further, I found you need to edit the VPN Client address in the client software Phase 2 (tunnel)config screen. The client software wizard configures
the VPN Client address = 0.0.0.0. I observed
the tunnel passes two-way traffic with 0.0.0.0, but encryption
was one-way. Traffic appeared to be encyrpted from the
client to the router, but not from the router to the client.
The below
screenshot shows the Phase 2 (tunnel) settings on the client
software that enabled two-way encryption. Note, the highlighted area
where I changed the VPN Client address to 192.168.33.3.
You can enter any IP address in this field that doesn’t
overlap with address ranges or specific addresses already in use on the client or the USG40.
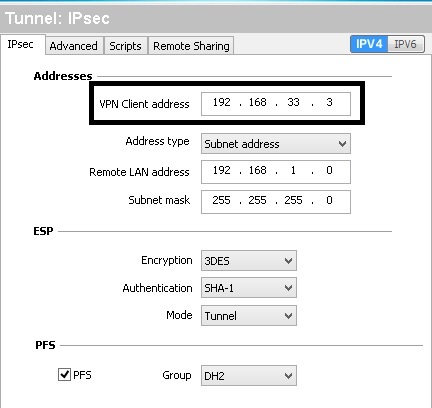
Phase 2 Config
SSL and L2TP VPN connectivity are supported for remote devices. For PCs, I prefer using SSL tunnels for remote access. ZyXEL’s SSL VPN solution uses their SecuExtender software which supports Windows 8, 7, Vista, 2003, XP and MacOS 10.7 or later. The SecuExtender software is installed on a Windows PC when you first connect to the USG. You can download SecuExtender for the MAC here.
I followed the same configs on the USG40 that I used on the ZyWALL 110 to setup an SSL connection, so I’ll refer you to my ZyWALL 110 review for those steps. Below is a screenshot showing an active SSL VPN connection to the USG40.
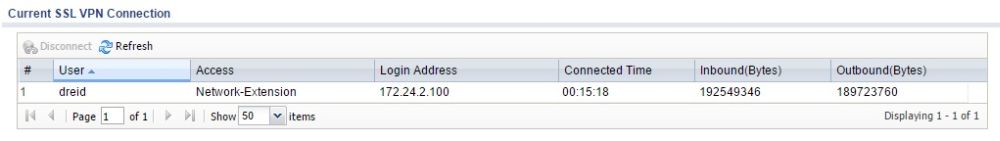
SSL
For handheld devices, L2TP is a useful remote solution as the L2TP client is built into the iPhone and Android operating systems. However, configuring an L2TP tunnel manually on the USG40 is no picnic. Thankfully, there is an L2TP configuration wizard to set up L2TP on the USG40, which enabled me to get it working with an iPhone and a Windows 8 laptop. Below is a screenshot showing my active L2TP VPN connection to the USG40.
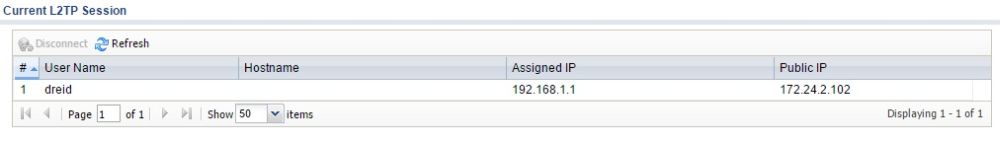
L2TP
To measure VPN throughput on the USG40, I used two PCs running 64-bit Windows with their software firewall disabled. Using TotuSoft’s LAN Speed Test client and server application, with a file size of 100MB, I measured throughput over an IPsec, SSL, and L2TP tunnel. Below are my throughput measurements.
Updated 12/11/14: Throughput column headings have been swapped
| Throughput (Mbps) | ||
|---|---|---|
| VPN_Tunnel_Type | Client-Gateway | Gateway-Client |
| IPsec Site-Site | 49.5 | 53.8 |
| IPsec Client to Site | 47.8 | 52.1 |
| L2TP Client | 49.9 | 56.0 |
| SSL Client | 10.3 | 19.7 |
Table 1: VPN throughput
VPN throughput on the USG40 is significantly improved over the USG20. On the USG20, I measured peak IPsec throughput at 27.9 Mbps and peak SSL throughput at 4.79 Mbps. On the USG40, I measured peak IPsec throughput at 53.8 Mbps and peak SSL throughput at 19.7 Mbps. L2TP throughput on the USG40 maxed at 56 Mbps.
Note 1: IPsec throughput was the same with pre-shared key and certificate authentication. I tried both peer authentication methods in response to a SmallNetBuilder forum question about whether certificate authentication could improve IPsec performance.
Note 2: I used ZyXEL’s ZyWALL 110 to measure IPsec throughput with the USG40. The ZyWALL 110 is rated at 300 Mbps IPsec VPN throughput, which is much higher than the USG40’s 100 Mbps rating. Thus, the ZyWALL 110 wouldn’t be the bottleneck.
Note 3: ZyXEL uses a UDP based test to rate throughput on their devices. The TotuSoft test uses TCP. UDP has a lower overhead than TCP, so ZyXEL’s ratings are typically higher than my measurements.
Security Features
The USG40 is a very capable VPN router, but its main selling point is network security. The USG40’s firewall allows you to control traffic based on source and destination zone, source and destination IP addresses, services, users, and schedules. There are 106 pre-defined services and you can add more.
Traffic can also be controlled on the USG40 using security features that include Anomaly Detection and Prevention (ADP), Application Patrol, Content Filtering, Intrusion Detection and Prevention (IDP), Anti-Virus and Anti-Spam.
Anomaly protection, when enabled, will look for scans or flooding events, as well as incorrect TCP, UDP, and ICMP sequences.
Application Control
The USG40’s Application Control feature can filter or throttle traffic to and from over 3,000 social, gaming, productivity and other web applications. ZyXEL states that with this application control feature, bandwidth consumed by unproductive applications can be controlled.
As with other functionality on the USG40, application control is object based. ZyXEL has defined 20 application categories, such as Social Networking, Instant Messaging, Games, P2P, Business, etc. Within each category, there are dozens of specific applications that you can select.
In my test, I created an Application object, shown below, to match all of ZyXEL’s 103 defined Social Network applications. I then created an App Patrol profile to reject all matched traffic in Application object. Finally, I applied the App Patrol profile as a security policy to the USG40’s main outgoing security policy, which controls outgoing traffic from the LAN1 interface.
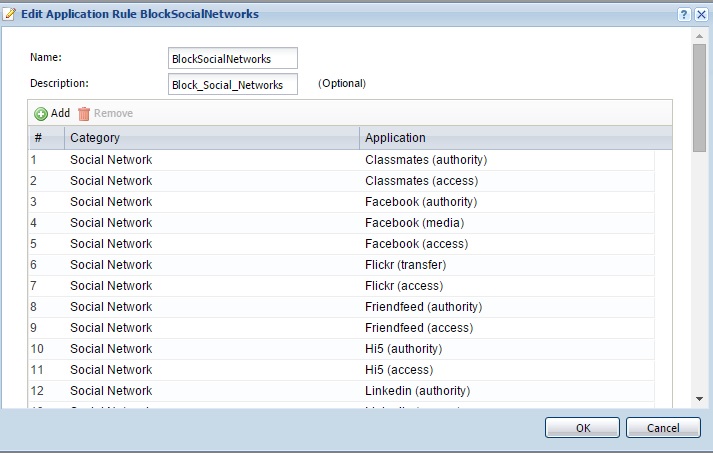
App Control Object
Validation of application control functionality on the USG40 was clear. Prior to applying these configurations, I could surf Facebook. Once the configurations were applied and I attempted to surf to Facebook, my browser showed “This webpage is not available” (Chrome) and “This page can’t be displayed” (IE). Once the configurations were removed, I was again able to surf Facebook.
Content Filtering
Content filtering on the USG40 can be controlled by security threat type including anonymizers, botnets, compromised, malware, network errors, parked domains, phishing and fraud, and spam sites. Content filtering can also be applied by category. There are 56 pre-defined website categories. ZyXEL claims they have over 140 billion URLs in their cloud-based database. Finally, content filtering can be applied by creating lists of trusted websites, forbidden web sites, and blocked URL keywords.
The content filter configuration has a useful tool to input a website and see what category it matches. I used the tool to determine that SmallNetBuilder.com is in the Computers & Technology category. I then created and applied a profile to block Computers & Technology websites. With my profile in place, I got the below message when surfing to smallnetbuilder.com. This message can be customized, or you can redirect users to a specific URL.
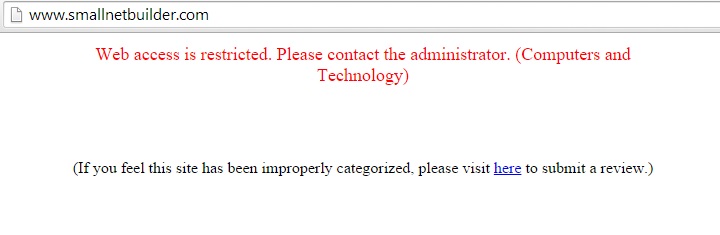
Content Filter
Intrusion Detection and Prevention (IDP)
IDP performs packet inspection by looking for specific data “signatures” indicative of malicious data. The USG40 has several base profiles (none, all, wan, lan, dmz) for applying IDP protection. These profiles define which service signatures will trigger an action (alert, log, drop, no action), plus you can create custom signature rules. Each profile is a set of packet inspection signatures. You create different profiles using one or more of the base profiles, then apply the profile(s) to a firewall policy.
In the screenshot below, you can see icons for UTM profiles I’ve applied to the default firewall rule that filters traffic involving the LAN interfaces.
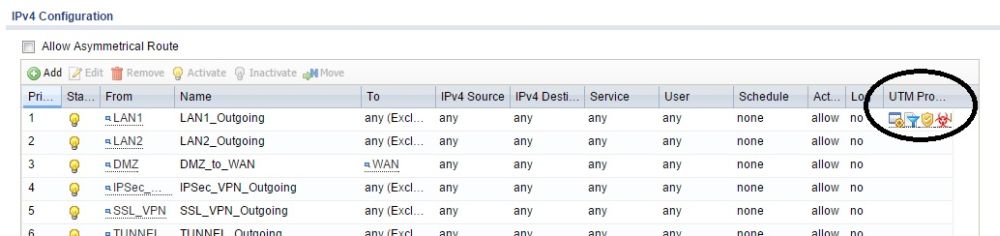
UTM Profiles
Anti-Virus and Anti-Spam
Anti-virus signature files are from Kaspersky’s anti-virus signature engine. The USG40 scans traffic using the common ports for SMTP, POP3, IMAP4, HTTP and FTP and compares them to the database of anti-virus signatures. Gateway anti-virus solutions, such as this solution on the USG40, provide a nice complement to software based anti-virus solutions, especially if end users bring their own devices (BYOD) and it isn’t known what type of anti-virus software they’re using.
Anti-spam filtering uses ZyXEL’s cloud-based IP reputation system for identifying domains and IP addresses that are sources of spam. Spam scanning options include checking the IP reputation of email domains, comparing domains to a white list and/or black lists, checking mail content, checking for a virus outbreak, and checking DNS black lists (lists of IP addresses known for sending or forwarding spam).
Reporting
There are a massive number of reporting options on the USG40. The Monitor menu has statistic screens for port, interface, traffic, session, IGMP, DDNS, IP/MAC, user, cellular, and UPnP statistics. UTM statistics can be collected for application controls, content filtering, IDP, anti-virus and anti-spam.
The USG40 can be configured to email a daily report showing CPU usage, memory usage, session and port usage, a threat report, and interface traffic statistics. Email alerts to two addresses are also supported. Below is a snippet of the daily report showing port usage on the WAN interface.
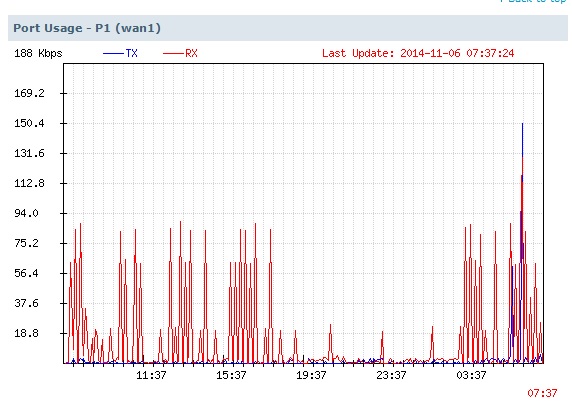
Daily Report Port Usage
Performance
We tested router performance using our standard test method with firmware V4.10(AALA.1). Measurements were made with the router in its default state, which has ADP and Security policy control enabled. A security policy was added to forward all WAN ports to LAN so IxChariot WAN to LAN tests were not blocked. For the Maximum Simultaneous Connection test, we disabled session limits (default=1000) and disabled ADP.
The results below compare the ZyXEL USG40 to the USG20. It’s pretty clear that the USG40 is about 4x faster than the USG20 it replaces as the entry-level member of ZyXEL’s Security Gateway family.![]()
| Test Description | USG40 | USG20 |
|---|---|---|
| WAN – LAN | 234.5 | 58.1 |
| LAN – WAN | 242.1 | 41.9 |
| Total Simultaneous | 225.5 | 56.7 |
| Maximum Simultaneous Connections | 19,997 | 29,986 |
Table 2: Routing throughput summary
Unidirectional router throughput is shown in the plot below. We measured 234.5 Mbps for download and 242.1 Mbps for upload on the USG40.
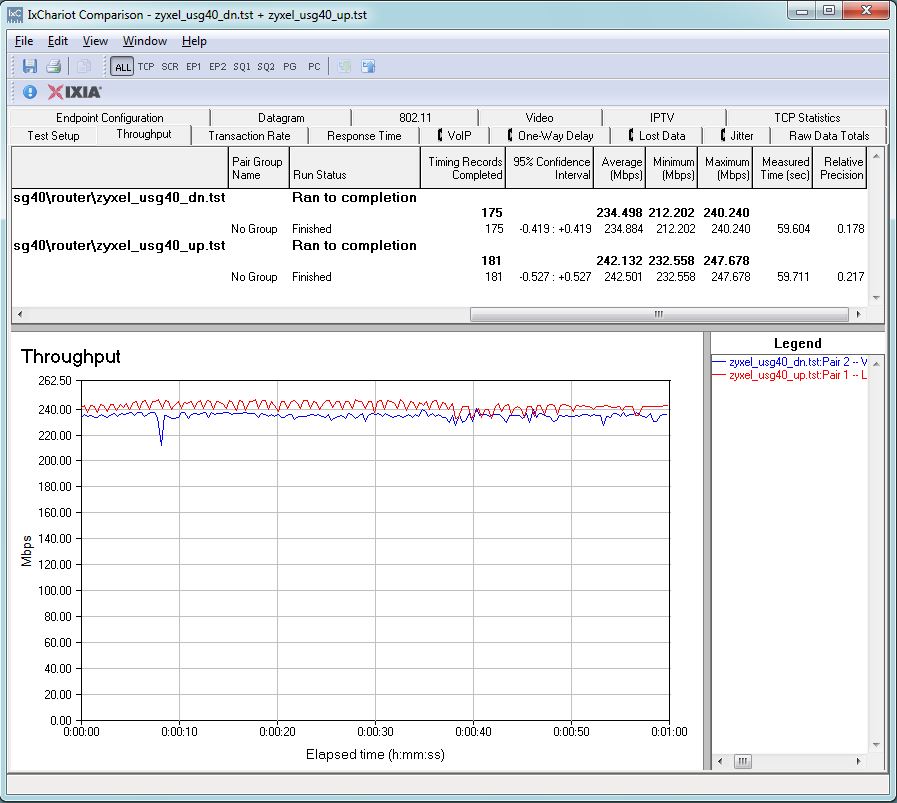
Unidirectional Throughput
Simultaneous up/downlink router throughput is shown in the plot below. We measured the USG40 at 225.5 Mbps, which is also over 4x faster than the USG20.
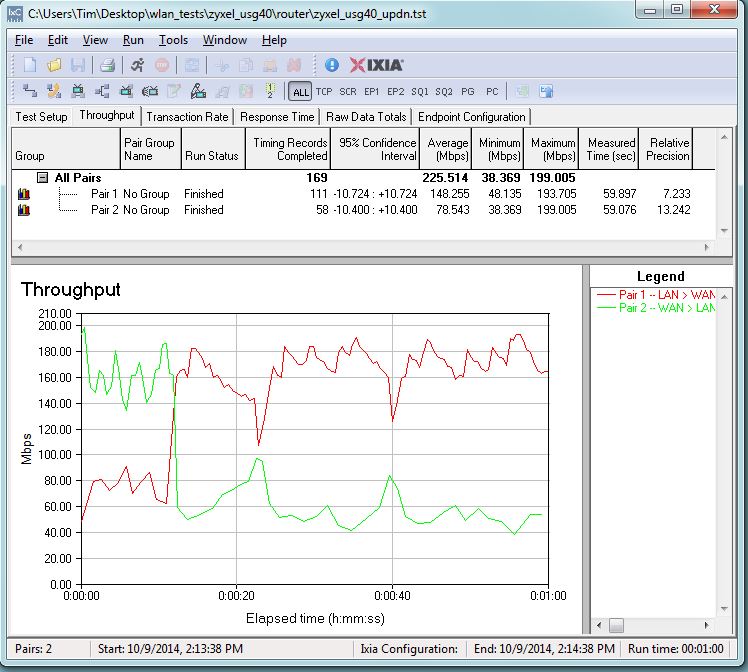
Bidirectional Throughput
Max connections on the USG40 is 19,997, which is less than the max connections of 29,986 on the USG20. However, ZyXEL spec’d the USG40 for 20,000 connections, so it is hitting that target exactly. 20,000 connections should be more than enough for the USG40’s target network of 1-10 users.
We did some quick checks to see if security services affected routing throughput. We found disabling ADP raised WAN to LAN throughput to 280 Mbps. Enabling all UTM services except App Patrol did not change down or up throughput from the default configuration results.
Closing Thoughts
ZyXEL told me that the list price for the USG40 with a 1 year license for all UTM features runs $420. But Amazon sells the USG40 with a 1 year license for all UTM features at around $212. That’s a pretty good deal. Not so good a deal is the UTM bundle renewal price of $230!
VPN tunnels can also run up your cost. Out of the box, you get support for 10 IPsec tunnels and 2 SSL tunnels. Support for only 2 SSL tunnels without buying additional licenses is a bit disappointing. An additional 10 IPsec licenses are $399 and an additional 5 SSL licenses run $135 as listed on ZyXEL’s licensing page. Also note ZyXEL doesn’t bundle any IPsec client licenses and they run $65 a pop.
If you haven’t dealt with a UTM class appliance before, be prepared for a steep learning curve. Even with the extensive manual, built-in configuration wizards and application note library, the USG40 is going to take some work to get up and running. Still, the USG40 offers a very compelling value proposition for small businesses or even individuals looking to step up their network’s security to a whole new level.
 Buy Next-Gen Unified Security Gateway-Performance Series from Amazon
Buy Next-Gen Unified Security Gateway-Performance Series from Amazon
