Introduction

| SMC Barricade Plus Cable/DSL Broadband router | |
|---|---|
| Summary | VPN version of popular Barricade router with SPI based firewall and PPTP / IPsec VPN endpoint, but no printserver or dialup WAN support. Will probably do better with PPTP vs. IPsec-based VPNs |
| Update | 10/24/02 – Updates for 2.03e firmware features, including TZO Dynamic DNS, UPnP, PPTP WAN type, and “loopback” support. |
| Pros | • Schedulable firewall rules & URL keyword blocking w/different time periods per day • Supports 10 WAN IP addresses • Supports PPTP & IPsec VPN endpoints • Supports NetBIOS broadcast (MS Network browsing) |
| Cons | • No Web traffic logging • No inbound port range mapping • 760kbps IPsec VPN performance • Poor IPsec VPN setup logging |
SMC’s Barricade Plus is the only one of the current crop of inexpensive VPN endpoint routers to support both IPsec and PPTP tunnels. I found it to be similar to its non-VPN sibling the SMC7004VBR [reviewed here], but with a few idiosyncracies of its own…
Basic Features
The Plus’ plastic package maintains SMC’s dark grey color scheme, and at first glance looks just like the original, homely little Barricade. The main differences are that the Plus is about half an inch wider and the indicators have been moved from the top to the front panel. The lights include Link/Activity, and 10/100 for each of the four LAN ports, Link/Activity for the WAN, and Power. All LED’s were bright and viewable from a wide angle.
The four switched 10/100 LAN ports are on the front panel, along with the Reset to Factory Defaults button. The 10/100 WAN port and power socket bring up the rear. Although you won’t find a Normal/Uplink switch or shared Uplink port, all the Plus’ ports are auto MDI / MDI-X. This means they’ll figure out how to connect to whatever you plug in whether you use a Normal or Crossover cable.
The Plus uses the Conexant CX82100 single-chip ARM940T-based processor, which is the same processor used in Linksys’ BEFSX41[reviewed here]. This processor has more oomph than the ADMtek 5106 Home Gateway Controller used in most current generation routers, and gave the Linksys some decent IPsec VPN throughput results. As we’ll see later, however, the Plus’ IPsec VPN results don’t come up to par.
NOTE! I learned a few weeks ago that ADMtek sold their 5106 Home Gateway Controller to Conexant, who has rebranded it the CX84200 Network Processor. So it looks like Conexant, not ADMtek, is winning most of the current generation router design-ins.
SMC includes a printed “EZ 3-Click Installation Guide”, Installation CD, and normal CAT5 patch cable. The CD contains:
- a PDF copy of the User Guide
- a copy of a Windows-executable for the 3-Click setup wizard
- a copy of the Adobe Acrobat Reader installer
 What’s not included (and what would have saved me some time) is a copy of the Barricade Plus VPN IPSEC & PPTP Configuration Guide. This PDF document is essential if you’re going to attempt to set up the Plus’ VPN features. You can download it from SMC’s support site. I think it should be included on the CD since it describes how to use a major feature set of the router… and one that customers will probably purchase the router to use!
What’s not included (and what would have saved me some time) is a copy of the Barricade Plus VPN IPSEC & PPTP Configuration Guide. This PDF document is essential if you’re going to attempt to set up the Plus’ VPN features. You can download it from SMC’s support site. I think it should be included on the CD since it describes how to use a major feature set of the router… and one that customers will probably purchase the router to use!
Setup and Administration
As you can see from Figure 1 below, the Plus’ browser-based admin interface is essentially the same as that on its non-VPN-endpoint cousins. So see the 7004VBR’s review for a detailed run-through on the feature set… I’ll just concentrate on the differences here.
Figure 1: Virtual Servers
(click on the image for a full-sized view)
The first difference is that the Plus doesn’t support PPTP authentication, which is used by some US and many European xDSL providers instead of PPPoE. Update 10/24/02 2.03e firmware adds PPTP support.
Both products are the same, however, in their lack of support for static IPs with PPPoE service.
A closer examination of Figure 1 shows two new menu items VPN and SNMP. I’ll cover the VPN features later, but take a quick look at the SNMP screens now.
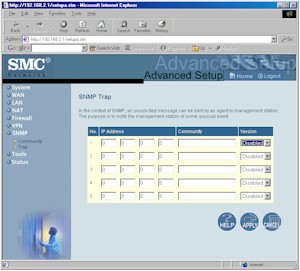
Figure 2: SNMP Trap
(click on the image for a full-sized view)
Figure 2 shows one of the two SNMP screens. The other is used to specify 5 different community strings, read or write access, and whether the community is enabled. No SNMP MIB is supplied, nor is there one available for download from SMC.
Firewall Features
Like the VBR, the Plus includes multi-NAT capability with the ability to take up to 10 WAN IP addresses and assign them to ranges of private LAN IP addresses. This lets you, for example, put more than one LAN client in DMZ (one for each WAN IP address you have), and also lets you have multiple virtual (mapped) servers of the same type (FTP servers for example) operating on the same port. Also like the VBR, you can define 8 different DMZ machines (if you have the WAN IP addresses to assign them to!).
What you won’t find is any sort of port range mapping. The VBR only allowed port range mapping through its “Special Applications” feature, which didn’t handle static inbound port ranges. Update 10/24/02 SMC confirmed that they deleted port range mapping on purpose because of the Plus’ small/medium business target market. They suggest using DMZ as a work-around.
The FW has only single-port “Virtual Servers” that don’t support server “loopback”. Update 10/24/02 Loopback support has been added by 2.03e firmware.
The FW’s Access Controls (Port Filters), and Scheduling Features are carbon copies of those on the VBR, with the scheduling among the most flexible that I’ve seen.
Again, if you need more details on the Plus’ firewall features, see the 7004VBR’s review.
VPN
As I said previously, the Plus is the only one of the under $100 VPN endpoint routers to support both PPTP and IPsec tunnels. I found the PPTP setup harder to figure out (although I have to admit I haven’t had to futz much with PPTP setups previously), but had better throughput than the IPsec. But let’s start with a walkthrough of the IPsec capabilities.
The big complaint about most of the inexpensive VPN endpoint routers is that people have a hard time connecting them to anything other than another of the same make and model router. In the first place, manufacturers don’t want to take on the support liability of saying that that their product will work with someone else’s. This costs them time and money in support calls, and at the prices that these products sell for (and the fact that support is not charged for), that gets to be a losing proposition pretty quickly. Add in the fact that the manufacturers would have to test the combinations that they say they support, and you can see why most steer clear of the subject.
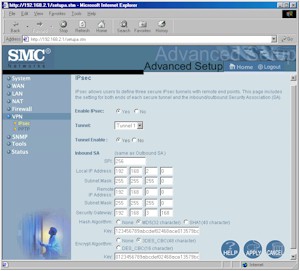
In the Plus’ case, a look at Figure 3 shows that the IPsec setup parameters are even more limited than those offered by competitive products, so you may have even a harder time doing anything other than connecting to another Plus to form a tunnel. On the other hand, connecting to other PPTP-based products may be fine, since it seems like SMC paid more attention to detail in the PPTP implementation, and since PPTP has fewer tunnel setup options than IPsec does.
Figure 3: IPsec setup
(click on the image for a full-sized view)
In addition, the IPsec setup instructions in the Barricade Plus VPN IPSEC & PPTP Configuration Guide describe only a router-to-router subnet-to-subnet configuration. Although you can probably configure a tunnel using single IP addresses, you can’t configure tunnels using ranges of IP addresses. You also can’t set the Plus to connect to a remote gateway (“Security Gateway”) using a domain name, or dynamic IP address.
Although you can choose between DES (56 bit), 3DES (168 bit), or disabling Encryption, and MD5, SHA, or disabling Authentication, your Key Management options are limited to setting the SPI (Security Parameter Index) value. This means no IKE, no Pre-shared Key, and no Key Lifetime parameters. PFS (Perfect Forward Secrecy) is not an option either, nor is the ability to control what happens in Phase 1 and 2 of the IPsec tunnel setup or handle Main and Aggressive mode settings.
Fortunately, it seems that NetBIOS broadcast (for Microsoft Network browsing) seems to be enabled by default for both IPsec and PPTP tunnels. This is something that I think all consumer VPN endpoint routers should do, since the “Can I see the guys on the other side of the tunnel?” test is the first thing most people try! It was nice to see machines on the other side of the tunnel in My Network Places / Network Neighborhood shortly after the tunnel was established without having to hunt for any additional settings.
I was lucky that I had done router-to-router IPsec setups before because my settings worked the first time. If they hadn’t, I would have been in trouble because there is no logging of IPsec tunnel setup, and no ability to connect or disconnect the tunnels! The only indication of tunnel operation you get is on the Status Screen (Figure 5). I guess the Plus is pretty tenacious in terms of maintaining tunnels, because there’s no setting allowing you to auto-reconnect or timeout a connection. The Plus automatically connected as soon as I enabled the tunnel on both ends and stayed connected until I disabled the Tunnel setting.
The bottom line is that the three IPsec tunnels that the Plus can handle will most likely be limited to connections between Pluses, with only the stout-of-Networking-heart attempting tunnels with individual VPN clients or other vendors’ products!
PPTP
You’d be well-advised to download the VPN Configuration guide before attempting to set up a PPTP tunnel, because some of the settings aren’t obvious.
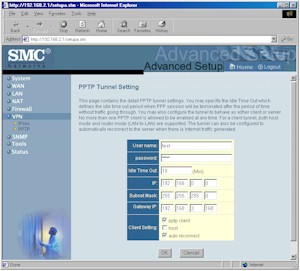
Figure 4: PPTP setup
(click on the image for a full-sized view)
Figure 4 shows the PPTP setup screen you reach after selecting from a list of 20 possible PPTP “accounts” on a previous screen. Folks who’ve set up a PPTP tunnel will know what to do with most of the entries, but the “host” checkbox isn’t what it seems (it’s checked only if you’re connecting to a Windows PPTP server), and setting up a PPTP server requires you to set the Gateway IP to 0.0.0.0. (all this is explained in the VPN Configuration guide). You’ll also have to scroll down and set the IP Address Pool on the page that lists the PPTP “accounts” if you’re setting up a PPTP server, something that I think should be done automatically based on the Plus’ DHCP settings.
Note that the 20 accounts doesn’t mean the Plus can handle 20 PPTP tunnels. Although I couldn’t find a spec for the number of PPTP tunnels in any of SMC’s documentation, the Status screen indicates that a Plus configured as a PPTP server can handle 2 client connections, and can handle one connection to a remote server when configured as a PPTP client.
Debugging and managing PPTP connections is also done through the Status screen as you can see in Figure 5.
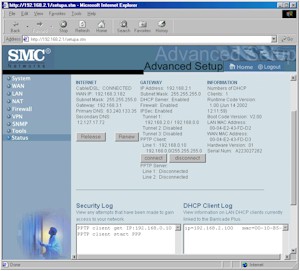
Figure 5: Status screen
(click on the image for a full-sized view)
But this time, it looks like there was more attention to design details because Connect and Disconnect buttons automatically appear for each client connection, along with a Disconnect button for each server. You also get PPTP connect and disconnect logging in the Security Log window which, although terse (and a pain to read due to the small, unsizable window), at least gives you some insight into what is happening during PPTP tunnel setup!
Tip: The PPTP VPN capability uses a Client / Server model, which automatically sets up a PPTP tunnel from client to server only. This probably isn’t a problem in real life, since the Plus seems to be pretty aggressive in setting up and keeping a tunnel running. So it’s likely that the tunnel will be up if a LAN client on the server side of the tunnel wanted to talk to a machine on the client side.
Tip: The Plus doesn’t automatically disable one flavor of VPN tunnel when another is disabled, or give you a Connect / Disconnect button for IPsec tunnels. You must disable the IPsec tunnel (or entire IPsec feature) in order to kill an IPsec tunnel.
VPN Performance
Because it uses the same chip as the Linksys BEFSX41, I expected to get at least 2Mbps throughput through an IPsec tunnel, and better through a PPTP tunnel, since it doesn’t require as much number-crunching for its encryption. But, try as I might, the best I was able to do was around 760kbps, more like what I got from other VPN-endpoint routers that don’t have an IPsec co-processor. I did find, however, that the Plus’ firewall settings affected throughput, as you can see from Figures 6 and 7 below.
I used Chariot to set up a test that ran the TCP throughput script simultaneously through the VPN tunnel and through the Plus’ normal non-VPN LAN-WAN direction. Four computers were used for the test – two for the VPN tunnel and two for the LAN-WAN connection. I set up the test so that the non-VPN test pair started first, then kicked in the VPN test pair for awhile, stopped it, then finally stopped the non-VPN test pair. This let me see how much the normal routing and VPN parts of the router interacted.
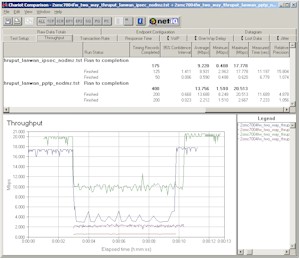
Figure 6: VPN throughput comparison – DMZ disabled
(click on the image for a full-sized view)
Figure 6 compares the results for runs with IPsec and PPTP tunnels. You can see that the non-VPN pair takes a significant throughput hit when either flavor of VPN tunnel is kicked in. But which part of the router gets hit the most? By using the data from the tables at the bottom of the page that contain data taken with only the VPN tunnel running, we can find the answer.
The data shows that when an IPsec tunnel is running , there’s about 80% throughput reduction for the non-VPN pair (17.8 to 3.5Mbps [interpolated]) and 22% reduction for the tunnel pair (0.77 to 0.60Mbps). The throughput hit is more evenly distributed when running a PPTP tunnel, with the non-VPN pair getting knocked down only 50% (20 to 10Mbps) and 56% (5.0 to 2.2Mbps) for the PPTP tunnel.
From my previous testing of SPI-based routers, I knew that enabling DMZ or port forwarding could cause routing throughput reduction, so I wanted to see if it would also affect VPN throughput. Figure 7 shows the same test run as in Figure 6, but this time with DMZ enabled on the router with the LAN-WAN traffic.
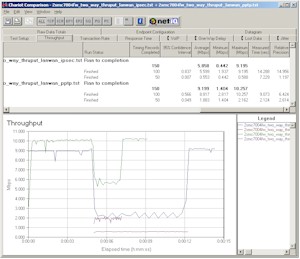
Figure 7: VPN throughput comparison – DMZ enabled
(click on the image for a full-sized view)
As expected, enabling DMZ knocked down the non-VPN throughput about 50% for both PPTP and IPsec cases with no tunnel running. But this time when the IPsec tunnel is kicked in, throughput changed 75% (9.0 to 2.2Mbps – both interpolated from the graph) for the non-VPN pair and 29% (0.77 to 0.55Mbps) for the tunnel. Making the same comparison for a PPTP tunnel running finds the throughput reduction a little less evenly distributed this time, with the non-VPN pair taking a 45% (10 to 5.5Mbps – interpolated) hit, and the PPTP tunnel extracting a 62% (5.0 to 1.9Mbps) penalty.
So what the heck is the bottom line out of all of this? My take-away is that the router does a better job of balancing normal routing and PPTP tunneling than it does with IPsec tunnels. You also probably won’t be happy with IPsec tunnel performance unless your data load is very light, and if you enable DMZ or have any ports forwarded, you may even see a noticeable speed reduction in your non-VPN traffic.
IPsec VPN Performance Test Results
| Test Description | Transfer Rate (Mbps) [1 MByte data size] |
Response Time (msec) [10 iterations 100 Byte data size] |
UDP stream [10s @ 500kbps] |
|
|---|---|---|---|---|
| Actual throughput (kbps) | Lost data (%) | |||
| Local to Remote | 0.77 | 9 (avg) 11 (max) |
293 | 36 |
| Remote to Local | 0.73 | 9 (avg) 10 (max) |
279 | 35 |
| Firmware Version | 1.0 (Jun 14 2002 12:11:59 | |||
See details of how we test.
Logging and Other Features
Logging on the Plus is the same as that on the VBR, including the fact that the Plus does not log or email alerts when probed (port scanned), but only when “serious attacks” (snork, smurf, etc.) are attempted. The syslog capability that SMC said was planned for a future VBR firmware update is not in the Plus either.
Update 10/24/02 The 2.03e firmware update adds Dynamic DNS support for both TZO.com and DynDNS.org, handy if you’d like to use a domain name instead of an IP address to reach any of your Plus’ Virtual Servers. Support for UPnP has also been added, but other than ON/OFF radio buttons, you get no view into what it’s doing, nor do you get to specify any services via UPnP’s Internet Gateway Properties settings.
Routing Performance
Testing Notes:
• WAN to LAN tests are all run with LAN endpoint in DMZ
• LAN to WAN tests are run with LAN endpoint not in DMZ, except UDP Stream
The VPN Performance results have given you a hint of what you’ll get for straight routing performance, and the chart above tells the rest of the tale. If you compare the Plus’ results with those of the VBR, it looks like SMC has tuned the Plus’ routing engine to cause less of a hit to WAN-LAN performance when all the SPI features are turned on. I didn’t test under all the conditions that I did for the VBR’s review, but the plots from the VPN testing show that disabling DMZ or not using any port forwarding will give you even higher performance. But all things considered, routing throughput will be faster than most broadband connections, even with ports forwarded or DMZ in use.
Routing Performance Test Results
| Test Description | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
|---|---|---|---|---|
| Throughput (kbps) | Lost data (%) | |||
| WAN – LAN | 4.7 | 169 (avg) 182 (max) |
500 | 0 |
| LAN – WAN | 9.1 | 88 (avg) 97 (max) |
499 | 0 |
| Firmware Version | 1.00 (Jun 14 2002 12:11: | |||
See details of how we test.
Wrap Up
The Plus is an interesting mix of pluses and minuses. On the downside is so-so IPsec tunnel performance, no IPsec setup logging, and lack of inbound port range forwarding. But the positives include decent routing performance, schedulable port filters, the ability to act as both a PPTP endpoint in both client and server modes (with decent throughput), and a street price under $100.
Which leaves prospective buyers with both port range forwarding and PPTP tunneling needs with a quandry.
My advice is to think of the Plus as a PPTP endpoint router that needs a firmware update to add the missing port range forwarding. Buyers in search of an inexpensive IPsec endpoint router should either keep their fingers crossed that the same firmware update will fix the IPsec negatives, or just move on to other choices.