Introduction

Cisco kicked over a pretty big hornet’s nest back in June when its Cisco Connect Cloud (CCC) service went live. In hindsight, the company made two key errors.
The first was failure to adequately notify users that a firmware update was going to completely change their router’s administration interface so that it required a working Internet connection (and authentication by a Cisco service) to access all admin features.
The second gaffe was a privacy policy that said Cisco was going to keep track of usage data, including Internet history.
After the uproar, Cisco quickly backed off from both, allowing users to downgrade their EA router firmware and opt-out of the CCC service. Cisco also changed the privacy terms. The revised Cisco Connect Cloud Supplement now does not detail the kind of data collected, saying instead just that Cisco "may collect and store detailed information regarding your network configuration and usage for the purpose of providing you technical networking support".
Despite the changes, there are some who are still convinced that Cisco is watching their every move on the Internet and profiting from it. So I decided to try to see what data actually flows between a CCC-enabled router and Cisco’s cloud.
The Approach
I set up a Cisco Linksys EA4500 running Ver.2.1.38.138880 firmware that supports CCC. The WAN port of the router was plugged into a NETGEAR GS108T smart switch with that port mirrored to a second port where I had a Windows machine running Wireshark for packet capture and analysis.
After doing some initial captures and getting way too much network chatter, I filtered the packet captures to grab only traffic to and from the router’s WAN IP.
The Results
The first thing I looked for was traffic going someplace other than the websites and services requested. This is harder than you might think, since most websites reach out and touch many servers other than their own for ad serving, Facebook, Twitter and other third-party widgets and traffic and page activity tracking. I ended up hitting Google’s relatively simple home page to simplify my search for the CCC cloud server.
I actually found a few, but they weren’t Cisco’s. Instead, CCC uses Amazon Web Services (AWS) Elastic Compute Cloud (EC2) servers. The ones my router contacted are listed below.
alt01.xmpp.ciscoconnectcloud.com (50.18.193.10) resolves to ec2-50-18-193-10.us-west-1.compute.amazonaws.com
cloud.ciscoconnectcloud.com (50.18.106.225) resolves to ec2-50-18-106-225.us-west-1.compute.amazonaws.com
cloud.ciscoconnectcloud.com (184.72.33.187) resolves to ec2-184-72-33-187.us-west-1.compute.amazonaws.com
The first server (alt01.xmpp.ciscoconnectcloud.com) appears to be used for "heartbeat" since the router sends and receives a few short messages about every minute. This happens whether or not you are logged into the router. I suspect this allows CCC to keep a path open through firewalls so that you can log into the router from the Internet side.
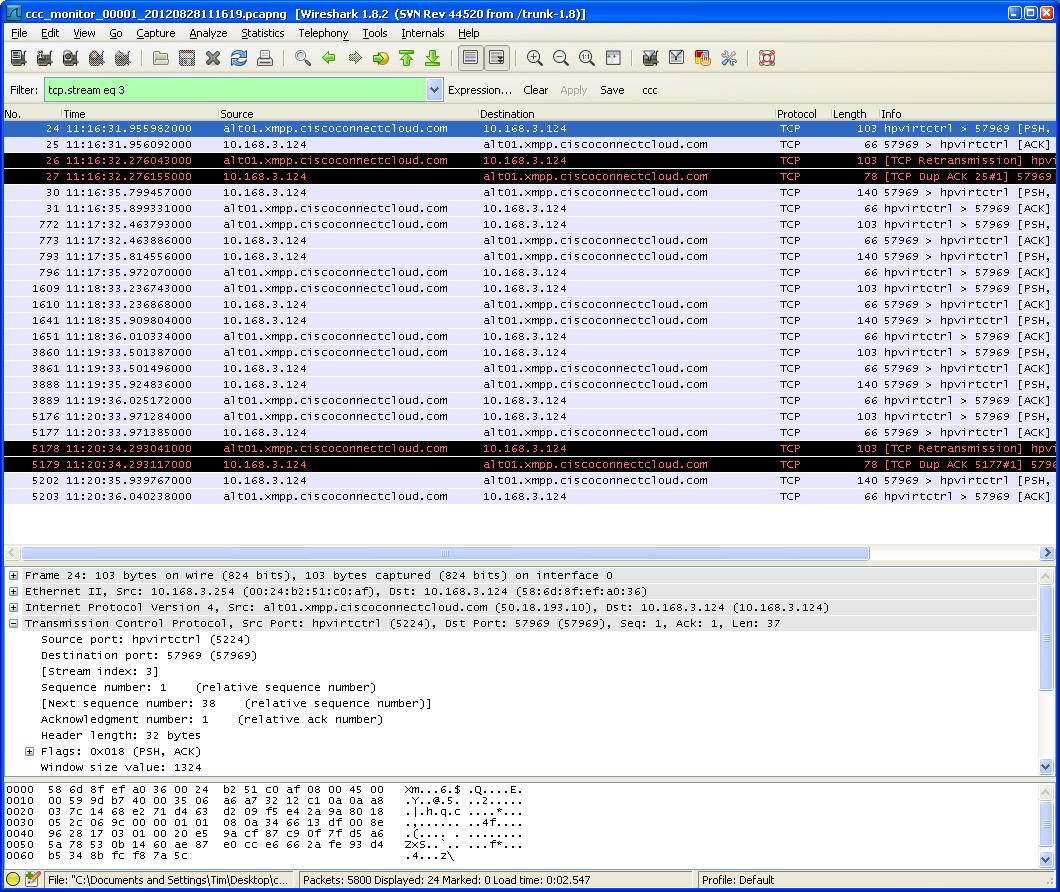
CCC “Heartbeat” Wireshark capture
I had Wireshark watch traffic for a few hours while I went about my normal business on another machine plugged into the EA4500. As long as I did not have a browser window open that was logged into the CCC router admin, the "heartbeat" packets were all that was sent to and from the CCC servers.
When I did log into the router admin, the cloud.ciscoconnectcloud.com servers came into play. As the capture below shows, all that traffic was encrypted, so I couldn’t tell what was sent.
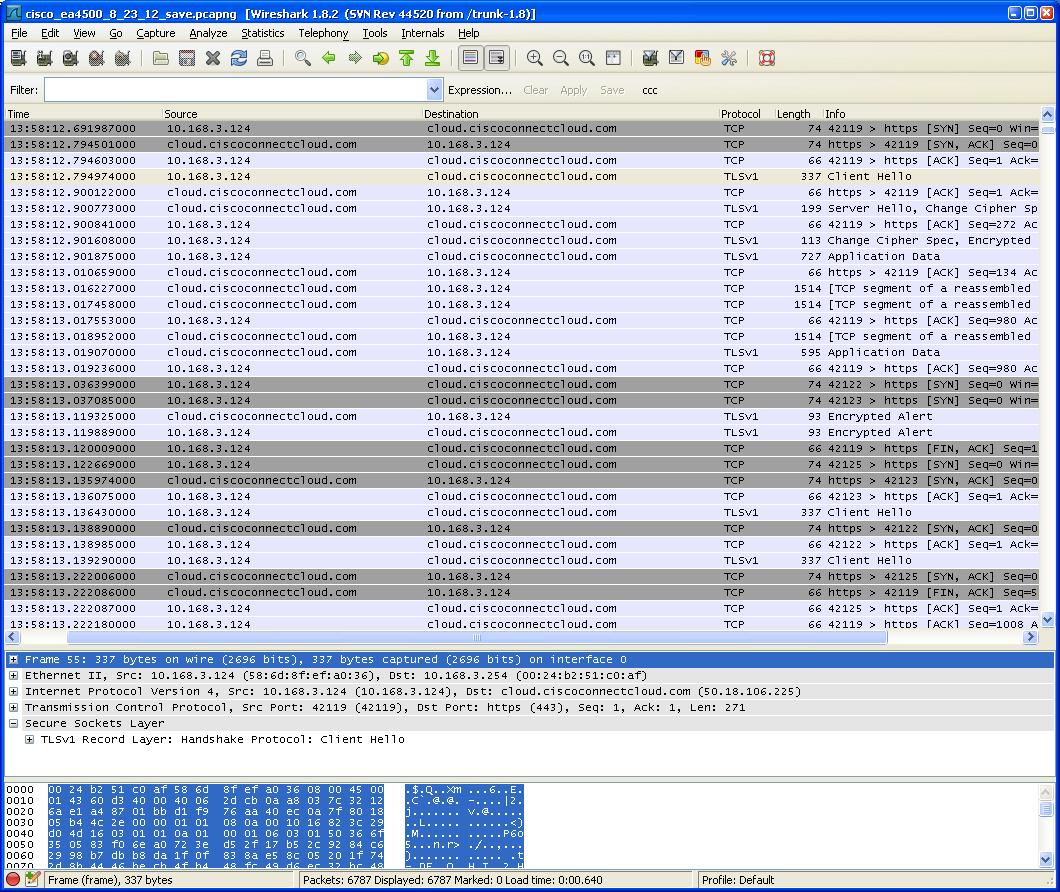
CCC logged in traffic Wireshark capture
However, I didn’t see any large exchanges that would indicate some sort of data dump. The encrypted traffic appears to be related to the operation of the CCC router admin GUI. Once the router admin browser window or tab is closed, this encrypted traffic stops and just the periodic "heartbeat" exchanges continue. You don’t even have to log out of CCC admin to have the encrypted traffic stop. All you have to do is close the browser window or tab.
Conclusion
I’m by no means a data security expert and I’ll admit my methods were very simplistic. But here is what I conclude from this investigation:
- Cisco is not redirecting all CCC router traffic through its servers or a proxy
- When you are not logged into a CCC router’s admin, the only data moving between your router and CCC servers is a once-per-minute "heartbeat"
- When you do log into the CCC router admin all traffic is encrypted.
- The length and timing of data exchanges while logged in indicates they are related to router administration
- There is no sign of large data dumps to the CCC cloud while you are logged into router admin
- Closing the browser admin window or tab stops the encrypted traffic. Logging out of the router is not required.
The bottom line is that there is no evidence to support claims that Cisco Connect Cloud is tracking your internet activity. So while there may be many reasons not to buy a Cisco Linksys App-Enabled router, data security and personal privacy don’t appear to be among them.
