Introduction
| NETGEAR Prosafe Dual Band Wireless VPN Firewall (FWAG114) | |
|---|---|
| Summary | First dual-band tri-mode wireless router with Atheros-based 11a, b, and g radios and 2 tunnel IPsec VPN endpoint |
| Update | None |
| Pros | • Excellent 11a performance • Separate b/g and a radios • Superior 11g throughput vs. range |
| Cons | • Does not play well with Broadcom 11g clients • Non-upgradable antennas • Wireless repeating and bridging not supported • WPA not supported |

I’ve waited a long time to get my hands on an Atheros-based 802.11g AP / router and NETGEAR finally obliged with the release of the FWAG114. I’ve always been impressed with Atheros’ client performance in NETGEAR’s WAB501 a/b [reviewed here] and WAG511 a/b/g [reviewed here] CardBus cards, and wanted to see if they could deliver the same goods on the AP end of things.
Basic Features
The FWAG is aimed at the “enterprise” crowd, so comes in NETGEAR’s sturdy blue metal box instead of the plastic “Platinum” line enclosure used for consumer networking products. The box is pretty compact – about the size of a 200 page hardcover book – and has slots on its bottom for wall mounting.
All indicator lights are on the front of the box and are bright and viewable from a wide angle. Indicators include Link/Activity and 100Mbps for the four 10/100 ports and one 10/100 Ethernet WAN connection. There are also separate Activity and lights for the 802.11a and b/g radios and Power, and Test general indicators.
Four 10/100 LAN ports, one 10/100 WAN port and power jack are on the rear panel, along with the Reset-to-Factory-Defaults switch. Note that all LAN ports are auto MDI / MDI-X which means they’ll figure out how to connect to whatever you plug into them, including switches or hubs if you decide to expand the number of ports.
Internal details
Figure 1 shows that each of the radios is hard-wired to two external dipole antennas so that they can support antenna diversity.

Figure 1: FWAG114 internal view
The unusual flat shape of the non-upgradeable antennas is explained by the detail photo in Figure 2 of the printed circuit board contained in each plastic housing.
Figure 2: Antenna detail
(click on the image for a full-sized view)
Although Atheros’ technology is used in the separate 802.11a and 802.11b/g radios, Figure 3 shows that Broadcom’s BCM4702 Wireless Network Processor handles the FWAG’s processing duties. LAN switching and Ethernet are handled by a Broadcom BCM5325 5 port switch/PHY and WAN port, and an Altima AC101 is used for the WAN port.

Figure 3: FWAG114 main board with radios removed
Setup
Even though the FWAG is based on an entirely different processor platform, its user interface is pretty much the same as its siblings the FR114P [reviewed here] and FM114P [reviewed here]. Opening the router’s default address of 192.168.0.1 for the first time brings you to the same Setup Wizard used on those products. The Wizard will auto-detect the type of connection you have and present you with the appropriate Internet connection configuration options.
If you’re a do-it-yourself kinda person, you can also set the WAN connection up manually. All the usual suspects for WAN connection types are supported, along with BigPond cable and PPTP. Note that static IPs are supported for PPTP, but not PPPoE.
During bootup the FWAG automatically checks a NTP server (you can specify the IP address of your favorite one, or just use the default one) for the correct time once it gets connected to the Internet. The only thing you have to do is set your Time Zone and whether your location observes Daylight Savings time.
The overall interface responsiveness was good with screens coming up quickly, but many changes required a 30-second-plus reboot cycle.
Remote Management can be enabled (it’s off by default), and you can set the port used and restrict access to a single IP address or range of addresses if you like. I especially liked that remote management sessions are automatically redirected to a secure (https) connection once you succefully login. The FWAG does not allow multiple administrator logins at a time and tells the second would-be administrator the IP address and computer name of the current admin. NETGEAR has thoughtfully provided both a admin log-out function and the ability to change the time for auto-logout of an inactive admin session from its default of 5 minutes.
Firewall
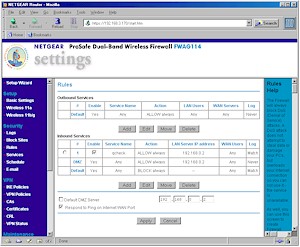
The FWAG borrows its Rules and Services firewall model from its sibling products to control all port usage in and out of the firewall. Figure 4 shows the Rule screen that summarizes both Inbound and Outbound Rules.
Figure 4: Firewall Rules
(click on the image for a full-sized view)
Outbound Service rules (commonly known as Port Filters), are used to specify a range of ports, i.e. a service, that are either allowed or blocked from a range of LAN IP addresses to a range of WAN (Internet) IP addresses. Figure 5 shows a rule that will block access to RealAudio streams for all LAN users.
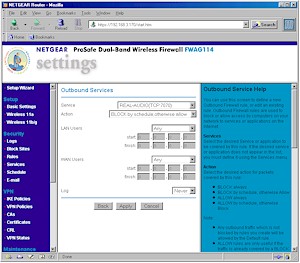
Figure 5: Outbound Service Rule
(click on the image for a full-sized view)
Inbound Services (usually known as Port Forwarding), have the same configuration features as Outbound Services, but are used to allow access to servers on your LAN that are behind the FWAG’s firewall. Note that server “loopback” is supported for Inbound Services.
The FWAG comes with service definitions for commonly used services such as HTTP (Web), FTP, and others, which you can pick from a drop-down list. When you need a service that’s not pre-defined, you can add it via the Custom Services screen, shown in Figure 6.
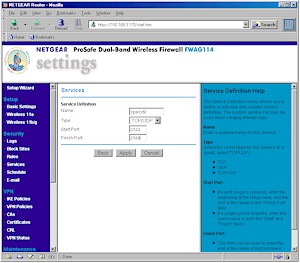
Figure 6: Custom Service
(click on the image for a full-sized view)
Rules have a few other tricks they can do. Both Inbound and Outbound rules are schedulable as shown in Figure 7, but there is only one schedule, which can be applied on a rule by rule basis.
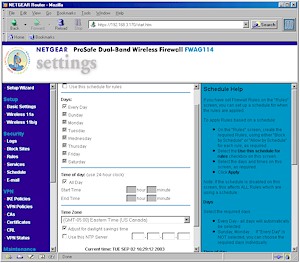
Figure 7: Rule Schedule
(click on the image for a full-sized view)
You can also control the logging of each rule with selections of Never and Match, as well as the order of precedence for rules in both directions. But note that there is no ability to set an outbound trigger port for the Inbound Services… the service mappings are static only. And contrary to the FWAG’s User Manual, UPnP is not supported, at least not yet.
You can exert finer control (than blocking all access with Outbound Services) over the websites and newsgroups that your users visit via the Block Sites feature. The feature is not schedulable, but you can enter one “Trusted” IP address that will get unfiltered Internet access.
VPN
Like its 802.11b FVM318 sibling, the FWAG has a built-in IPsec endpoint and also supports VPN passthrough for PPTP, IPsec and L2TP traffic. But unlike the FVM318, the endpoint is for tunnels originating or terminating on the WAN interface only. Protection for wireless LAN clients will need to be done via WEP or WPA (more on this later).
The IPsec endpoint has its good and bad points. On the plus side, it’s much more configurable than the endpoints found on Linksys’ popular BEFVP41 [reviewed here] and BEFSX41 [reviewed here] routers, and supports digital certificates (and a certificate revokation list) for IKE policy authentication in addition to pre-shared keys. NETGEAR also includes a couple of detailed setup examples for FWAG114-to-FWAG114 VPNs.
The main negatives are its logging and connection setup. VPN setup log messages are generally tough to decipher unless you’re an expert, but I found the FWAG’s tougher to decipher than those generated by Linksys’ BEFSX41. Since there’s no Connect button, NETGEAR suggests you try to ping a client on the opposite end of the tunnel to get things started. Once you’re up, there’s no way to terminate a connection (although this is more of a problem during testing than in real application).
Having recently figured out how to make WinXP’s built-in IPsec client work [see this ProblemSolver for the details], I figured I’d try to get it to work its magic with the FWAG. I eventually succeeded, but only could get the tunnel going from the FWAG end and after a router reboot. And although the tunnel appeared to be working, this message in the VPN Log didn’t exactly inspire confidence!
[2003-09-02 17:17:39]Something terribly wrong, trying to free alredy freed
IKE_QM_STATE block
However, I was impressed that the throughput through the tunnel averaged a respectable 1.6Mbps from the XP client to FWAG and 2.0Mbps in the reverse direction, which is well matched to most broadband connection speeds.
Tip: If you want to try your own luck at getting XP and the FWAG tunneling in harmony, here are my basic setup details:
| FWAG114 IKE Policy | |
| Direction Type | Both directions |
| Local Identity Type | WAN IP address |
| Remote Identity Type | Remote WAN IP |
| IKE SA Parameters |
Encryption algorithm: 3DES |
| FWAG114 VPN Auto Policy | |
| IKE policy | select the policy created |
| Remote VPN endpoint | IP address |
| IPsec PFS | selected, PFS Key Group 2 |
| Traffic Selector | Local IP: Subnet address Remote IP: Single address |
| ESP configuration | Enable encryption, 3DES Enable authentication, MD5 |
| XP Client | |
|
Basic approach is mirror the settings above. For both rules: For the “To” rule: For the “From” rule: |
|
Logging & Other Features
The Logging feature can selectively record the following events:
- Router admin (start up, get time etc)
- Connections to the Web-based interface of the router
- Known DoS attacks and Port Scans
- Attempted access to blocked sites
- All websites and newsgroups visited
- All local activity
- All incoming and outgoing traffic
You can view, clear, refresh, and immediately send the log to one designated email address, or schedule the emailing of the log on an hourly, daily, weekly, or “when full” basis. Immediate email alerts can also be sent which are triggered by three different types of events. Logging to a Syslog daemon is also supported and you can either specify an IP address or have the FWAG broadcast the syslog info to all LAN clients.
Finally, the FWAG has a few other features that I haven’t mentioned, such as:
- you can set the router’s MTU (Maximum Transmission Unit) value (useful in getting some PPPoE-based connections to work)
- you can set and view 8 static routes (useful in networks that have more than one subnet)
- dynamic routing protocols RIP1, and RIP 2B, and RIP 2M are supported
- you can enable the router to respond to WAN ping requests (this is disabled by default, which is good security practice)
- dynamic DNS support is built-in for using dyndns.org
Routing Performance
As you can see from the table above, the FWAG’s routing performance is more than enough to keep up with most broadband connections. The LAN-WAN UDP streaming test results are missing due to a problem with Qcheck’s newer endpoints and the FWAG’s NAT+SPI firewall, and not because of any problem with the FWAG’s routing itself.
Routing Performance Test Results
| Test Description | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
|---|---|---|---|---|
| Throughput (kbps) | Lost data (%) | |||
| WAN – LAN | 12.8 | 2 (avg) 4 (max) |
500 | 0 |
| LAN – WAN | 12.5 | 2 (avg) 2 (max) |
||
| Firmware Version | U12H00500_V1.0.20 | |||
See details of how we test.
Wireless Features
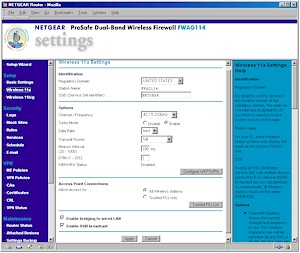
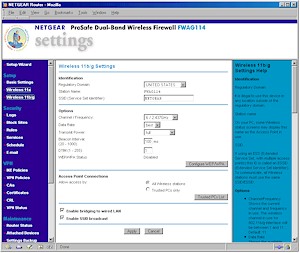
The FWAG’s wireless settings are separated into two pages – one for the 11a radio (Figure 8), the other for the 11b/g radio (Figure 9).
Figure 8: Wireless 11a settings
(click on the image for a full-sized view)
Figure 9: Wireless 11b/g settings
(click on the image for a full-sized view)
The settings are pretty much what you expect, but also include the ability to control the transmit power and disable SSID broadcast on both radios. You can’t, however, turn off the radios, a feature I think should be mandatory on all wireless routers.
Also note that there are no mode settings on the b/g radio – including no support for Atheros’ “Super-G / AG” throughput enhancement mechanism, and no way to disable 802.11g’s 11b protection mechanism.
Wireless Security
The FWAG has a decent set of wireless security features. I’ll start by noting one that’s not commonly available on competing products – the Enable Bridging to Wireless LAN checkbox near the bottom of each radio’s admin screen (which is checked by default). This feature keeps all wireless and Ethernet clients separated and is handy for folks who want to wirelessly share their broadband connection with anyone within range, but keep those users off their wired LAN. (The feature also works in reverse, keeping wired clients from reaching wireless users.)
The Trusted PC feature lets you enter MAC addresses of clients that will be allowed to connect to the FWAG. The feature doesn’t offer a “pick list” of currently associated wireless clients to ease the chore of creating the MAC Address Filter list, nor can you save or load the filter list – again for ease of configuration.
Only WEP encryption was supported in the firmware that shipped with the FWAG, but NETGEAR sent me Beta firmware that supports Wi-Fi Protected Access (WPA), which is why you see it in radio admin page screenshots. I’ve been nagging NETGEAR to get its act together on WPA support since they announced, but didn’t ship, it earlier this year. NETGEAR has told me that “all new builds” of their WAG511 CardBus client card will ship with WPA-enabled firmware, but the update still isn’t available for download from the WAG511’s support page. WPA support for the FWAG is supposed to ship this month (Sept 2003), but given NETGEAR’s past track record on WPA, if this feature is important to you – and it should be – I’d hold onto your money until you see the download actually available on the FWAG’s support page.
TIP: For more information about WPA, see our Wi-Fi Protected Access (WPA) NeedToKnow – Part II.
Moving back to WEP, you can enter 64 or 128 bit keys for 11b/g and 64, 128, and 152 bit keys for 11a directly in Hexadecimal. Both radios also support key entry using an alphanumeric passphrase. The passphrase method generates four different keys in 64 bit mode, four identical keys in 128 bit mode, and doesn’t work at all when the 11a 152 bit WEP mode is selected. Keys also can’t be saved to a file, which would make client entry a little easier.
Both WPA “enterprise” (RADIUS) and WPA-PSK modes are supported, but only with the mandatory TKIP encryption. NETGEAR appears to have chosen to not allow access to the stronger, optional AES encryption that Broadcom-based products provide, even though Atheros’ chipsets include an embedded hardware AES encryption co-processor.
Wireless Monitoring & Other Features
Wireless client monitoring is supported, but you have to work to find it. The Maintenance > Attached Devices link shows the FWAG’s DHCP client list, but offers no distinction between wired and wireless clients and shows only the Name, IP and MAC addresses of leases. If you’re using static IP addressing for your wireless clients, they won’t show up in this list.
The Maintenance > Router Status link shows the SSID, BSSIC (MAC address), Channel, and WEP status of each radio and includes a Show Statistics button that pops up a window showing aggregate transmit and receive stats for WAN, LAN and both radios. Better than nothin’, but not up to what I’d like to see.
Finally, you should know that Wireless Bridging features are not included in the FWAG. If you need this capability, you should check out Buffalo Tech’s WBRG54, which is the only 11g router so far to support this capability.
Wireless Performance 11a, g – Throughput vs. Range
NOTES:
• Testing was done with a NETGEAR WAG511 Cardbus client card in a WinXP Home Dell Inspiron 4100 laptop unless otherwise noted
Since the FWAG is the first Atheros-based 11g product I’ve tested, I gave it my full battery of tests. There’s a lot to go through, so let’s get started.
Throughput vs. Distance
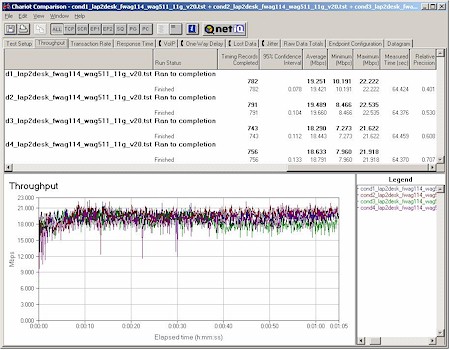
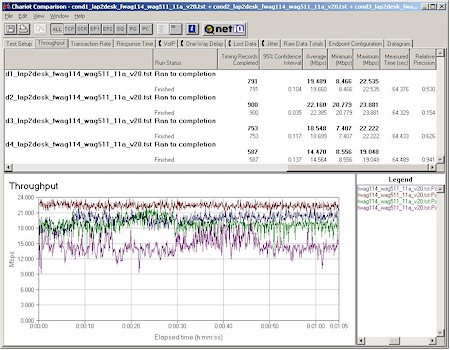
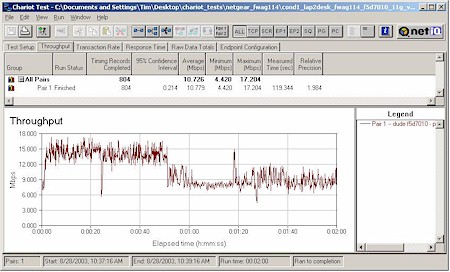
I ran my four-location throughput test using IXIA’s Chariot for 11a, 11a Turbo, and 11g operation. Figure 10 shows the 11g mode results.
Figure 10: Four Condition 11g Throughput test – FWAG114
(click on the image for a full-sized view)
For comparison, here’s the 11g plot from the Broadcom / Atheros based Linksys WRT55AG review.
Figure 11: Four Condition 11g Throughput test – WRT55AG
(click on the image for a full-sized view)
No comparison, eh? Granted the WRT55AG was tested with draft-11g firmware, but even if you use the throughput results from its 11g-only sibling, the WRT54G, the FWAG still has superior overall throughput vs. range, but is at a slight disadvantage for best-case average throughput.
Throughput vs. Distance, continued
Moving on to 11a performance, let’s once again compare the FWAG (Figure 12) to the WRT55AG (Figure 13).
Figure 12: Four Condition 11a Throughput test – FWAG114
(click on the image for a full-sized view)
Figure 13: Four Condition 11a Throughput test – WRT55AG
(click on the image for a full-sized view)
Although there are more similarities in 11a performance, the FWAG’s radio uses a newer Atheros chipset, which appears to give it an edge over the WRT55AG in low-signal conditions.
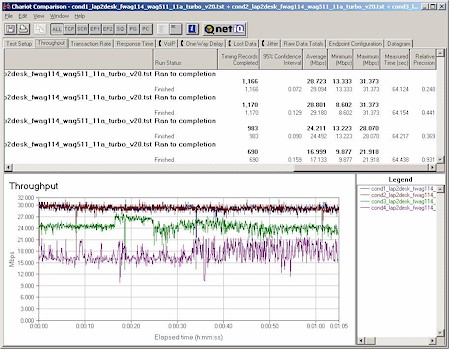
The best news, however, is the FWAG’s 11a Turbo performance shown in Figure 14.
Figure 13: Four Condition 11a Turbo Throughput test – FWAG114
(click on the image for a full-sized view)
There’s no Linksys comparison plot because the WRT55AG didn’t provide an 11a Turbo mode. This plot clearly shows that Atheros’ 802.11a technology can deliver high throughput under indoor test conditions and maximum throughput superior to 802.11g – with or without “packet-bursting” throughput enhancements.
802.11g Wireless Performance Test Results
| Test Conditions
– WEP encryption: DISABLED |
Firmware/Driver Versions
AP f/w: |
||||
|---|---|---|---|---|---|
| Test Description | Signal Strength (%) | Transfer Rate (Mbps) | Response Time (msec) | UDP stream | |
| Throughput (kbps) | Lost data (%) | ||||
| Client to AP – Condition 1 | 92 | 19.4 [No WEP] 19.1 [w/ WEP] |
1 (avg) 3 (max) |
499 | 0 |
| Client to AP – Condition 2 | 78 | 19.7 | 1 (avg) 2 (max) |
499 | 0 |
| Client to AP – Condition 3 | 52 | 18.4 | 1 (avg) 2 (max) |
499 | 0 |
| Client to AP – Condition 4 | 55 | 18.8 | 1 (avg) 3 (max) |
499 | 0 |
See details of how we test.
Wireless Perf. – Security
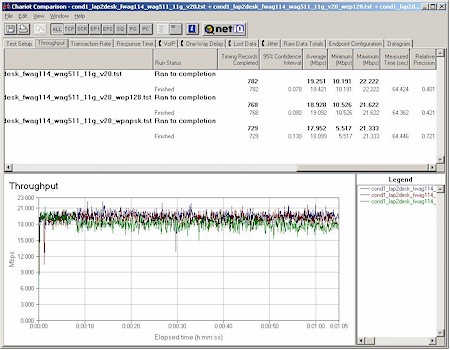
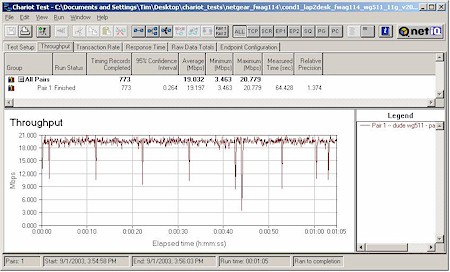
Although throughput loss with WEP enabled should be a thing of the past since all latest-generation wireless chipsets have hardware encryption co-processors, I still test for it because I still find throughput loss! Figure 14 shows a composite plot comparing Location 1 (best case) throughput for no encryption, WEP 128, and WPA-PSK modes.
Figure 14:11g security mode throughput comparison
(click on the image for a full-sized view)
Although it’s tough to call, there appears to be a 5-7% reduction in average throughput when WEP or WPA-PSK / TKIP is enabled for either the 11b/g radio. I ran the same tests with 11a Turbo mode enabled (not shown) and got similar results. Either way, this slight reduction is a small price to pay for WPA’s improved security – once NETGEAR finally releases it.
The real good news, however, is that when NETGEAR sent me the soon-to-be-released WPA-enabled driver for the WAG511 card, I found they’d integrated a WPA-supplicant into the client utility! Although it now takes up more screen space when you open it up, there are a number of feature enhancements in addition to the WPA supplicant. The supplicant, by the way, includes support for EAP-TLS and EAP-PEAP, 802.1x, and Cisco-LEAP authentication in addition to WPA and WPA-PSK. You can also use WPA and 802.1x certificates. See Figures 15 and 16 for the screen shots (click on either one for a larger view)
| Figure 15: WAG511 client utility | Figure 16: WAG511 client security |
Performance – 11g Interoperability
Since this is my first test of an 802.11g Atheros-based product, I checked to see if the FWAG played nicely with other 11g chipsets. The results are in Figures 17 – 19:
Figure 17: Condition 1 11g throughput – Belkin F5D7010 (Broadcom)
(click on the image for a full-sized view)
Figure 18: Condition 1 11g throughput – NETGEAR WG511 (Intersil PRISM GT)
(click on the image for a full-sized view)
Figure 19: Condition 1 11g throughput – USR5410 (TI TNETW1130)
(click on the image for a full-sized view)
The results for the Intersil and TI chipsets are lookin’ good, but the Broadcom-based Belkin card didn’t fare well at all. I ran the same test with a Linksys WPC54G and got similar poor results. Both Atheros and Broadcom said they’d uncovered a similar problem during early interoperability testing and both said it had been fixed. But NETGEAR was unable to confirm the problem, although they sent Beta firmware for me to try that had no effect.
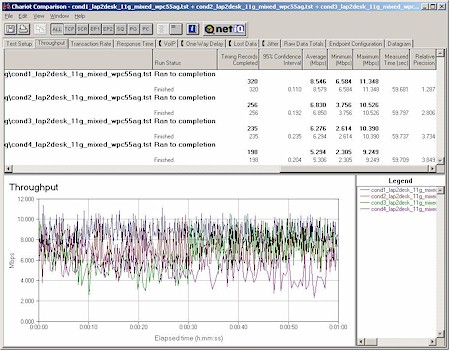
Wireless Perf. – Mixed mode
My last round of tests checked the handling of simultaneous 802.11b and 11g traffic. Again using Chariot, I set up a test using two client pairs. The reference 802.11g test pair for each test was a WinXP Home Dell Laptop with NETGEAR WAG511 Cardbus card to Win98SE Ethernet client. The second pair used a WinXP Home Compaq Presario 1650 Laptop with various 802.11b cards to a different Win98SE Ethernet client. I tested the following cards:
- Linksys WPC11 v3 (Intersil PRISM III)
- NETGEAR WAB501 (Atheros 5001X ) [forced to 11b mode]
- ORiNOCO Gold (Agere Systems)
- D-Link DWL-650+ (TI ACX100)
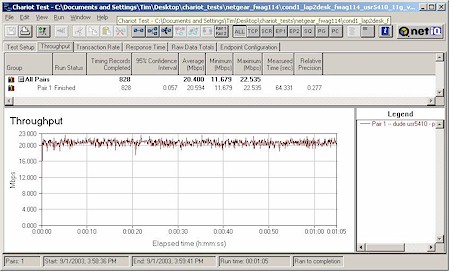
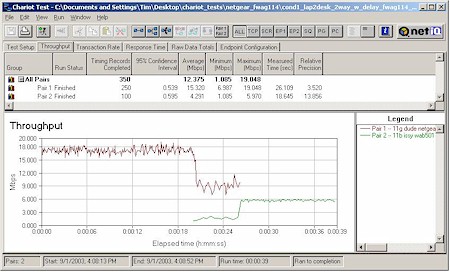
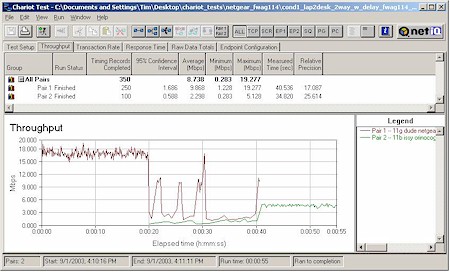
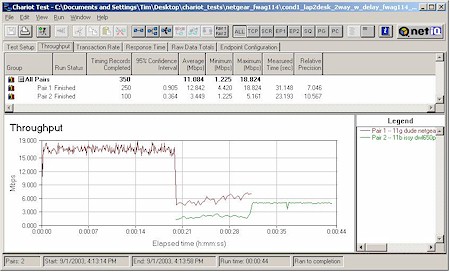
In each test, I started the 11g card first, then kicked in the 802.11b card. Both cards then run simultaneously for awhile, with the 11g card stopping first to let the 11b card finish by itself. The AP was set to its default mode for all tests. Figures 20-23 show the results.
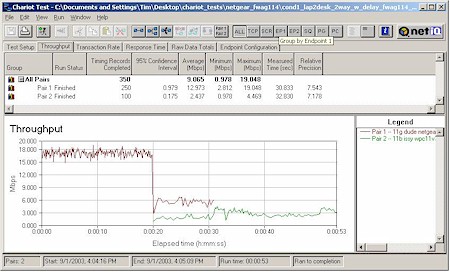
Figure 20: Mixed mode test – WAG511 & Linksys WPC11 v3
(click on the image for a full-sized view)
Figure 21: Mixed mode test – WAG511 & NETGEAR WAB501 ( forced to 11b)
(click on the image for a full-sized view)
Figure 22: Mixed mode test – WAG511 & ORiNOCO Gold
(click on the image for a full-sized view)
Figure 23: Mixed mode test – WAG511 & D-Link DWL-650+
(click on the image for a full-sized view)
As I’d expect, the two Atheros-based cards had the best cooperation, nicely sharing bandwidth. The ORiNOCO card (with the oldest 11b chipset) had the worst effect on 11g throughput, seriously knocking it down while both were running. But the card it looks like you don’t want to use with the FWAG is the Linksys WPC11 v3, based on the Intersil PRISM III chipset. As Figure 18 shows, its average throughput when running by itself tended to be around 3Mbps.
Take it to the max…
Since there are two radios, and given the throughput results above, I should be able to get a best case 29Mbps average throughput from the 11a radio in Turbo mode, plus 19Mbps from the 11g radio for a total of 48Mbps aggregate throughput, right? Check out Figure 24 to see what really happens when both radios are loaded to the max.

Figure 24: Maximim bandwidth test
(click on the image for a full-sized view)
This test took actually ran the WAG511 in 11g mode first, then kicked in the WAB501 set to 11a normal mode, ran both for awhile, then let the WAB501 finish by itself. Since four separate computers were used, any bottlenecks would have to come from the FWAG, since it’s the only common element in the test.
You can see that when the WAB501 kicks in, both cards average about 15Mbps, for an aggregate throughput of about 30Mbps – almost 40% below the 48Mbps that I calculated from individual tests. I’m not sure whether this will be able to be improved via a firmware update, or an upgrade to a processor with more oomph will be required. At any rate, if you see any “starbursts” on WLAN product boxes claiming “over 200Mbps speed!” (which I’d think someone would try on a dual-radio AP or router that supported both 11a Turbo and one of the 11g speed-boosting technologies) I’d treat it with a very skeptical eye!
Wrap Up
The FWAG took me on an roller-coaster ride, since I really wanted to see Atheros come out with kick-ass 11g performance to match their excellent next-generation 11a technology and give Broadcom some serious competition. But when I ran it through my intial tests, the poor performance with Broadcom 11g-based products, the lack of WPA support, and October availability of “Super-G” capability was a real disappointment.
But once I ran my throughput vs. distance tests, my attitude brightened. And when I found the speedy routing performance and decent 2Mbps IPsec tunnel throughput, my attitude adjustment was complete.
The FWAG114 certainly isn’t a perfect product, and NETGEAR’s track record on supporting WPA to date has been very disappointing. But if you want the fastest WLAN in your neighborhood, grab a FWAG114 and WAG511 for your notebook and enjoy the ride!